
Illicit streaming devices have become an unnoticed yet significant threat in many households and corporate environments. These devices, often advertised with wild promises of free

Imagine, for a moment, that your IT environment is the Death Star. You know the rebels will try to rescue Princess Leia. If you’re Darth
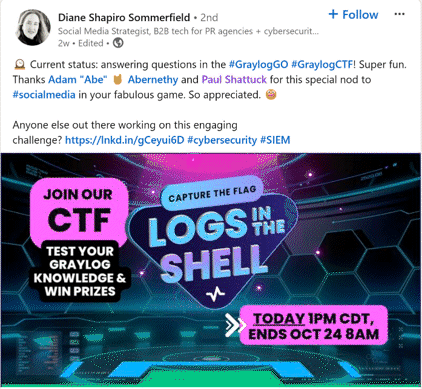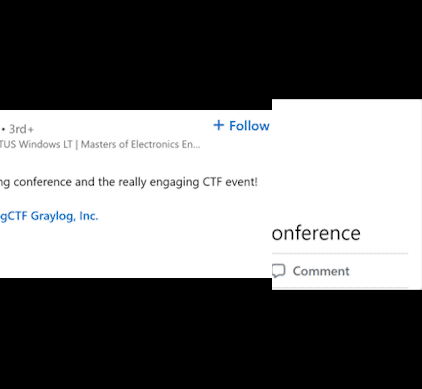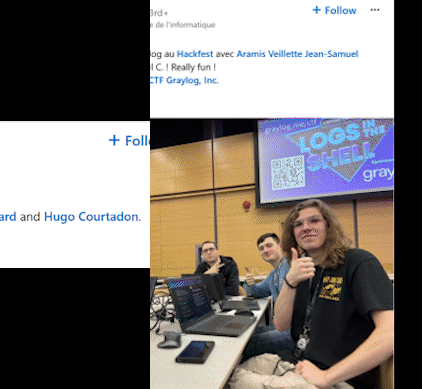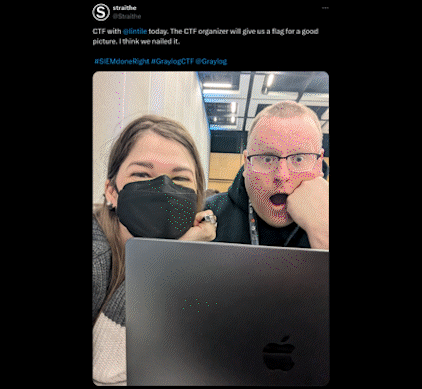
2024 was a thrilling year for Graylog Capture The Flag (CTF) events! Across major cybersecurity conferences, Graylog invited participants to test their skills in a