Graylog API Security
The Data Exfiltration Threat is Growing - Stop It Before It Happens
APIs are the backbone of modern digital ecosystems, integrating applications and enabling critical data exchanges. However, this convenience comes at a steep cost: APIs are now the #1 attack vector for cybercriminals. Sensitive Personally Identifiable Information (PII) such as emails, credit card information, and more constantly traverse APIs—making them prime targets for data exfiltration and compliance violations.
API breaches
10x
more leaked records than the average cybersecurity breach
Regulatory fines
>$1.7B
GDPR-related fines largely due to insufficient data protection
Reputation damage
45%
of customers stop doing business with a company after a data breach
Most security teams struggle with unknown API exposure, relying on Web Application Firewalls (WAFs) and API Gateways that only defend the perimeter and fail to detect API-specific threats. Without deep visibility into who is accessing your data and where it’s going, attackers can exfiltrate data undetected, leading to breaches, regulatory fines, and reputational damage.
Why Organizations Choose Graylog API Security: Empowering Your Entire Cybersecurity Organization with Cross-Functional Capabilities
CISOs & Security Executives
Without Graylog API Security: A lack of API visibility can lead to increased compliance risks and financial penalties.
With Graylog API Security: Gain full visibility into API security risks and ensure compliance with GDPR, CCPA, and HIPAA by tracking and securing PII across all APIs.
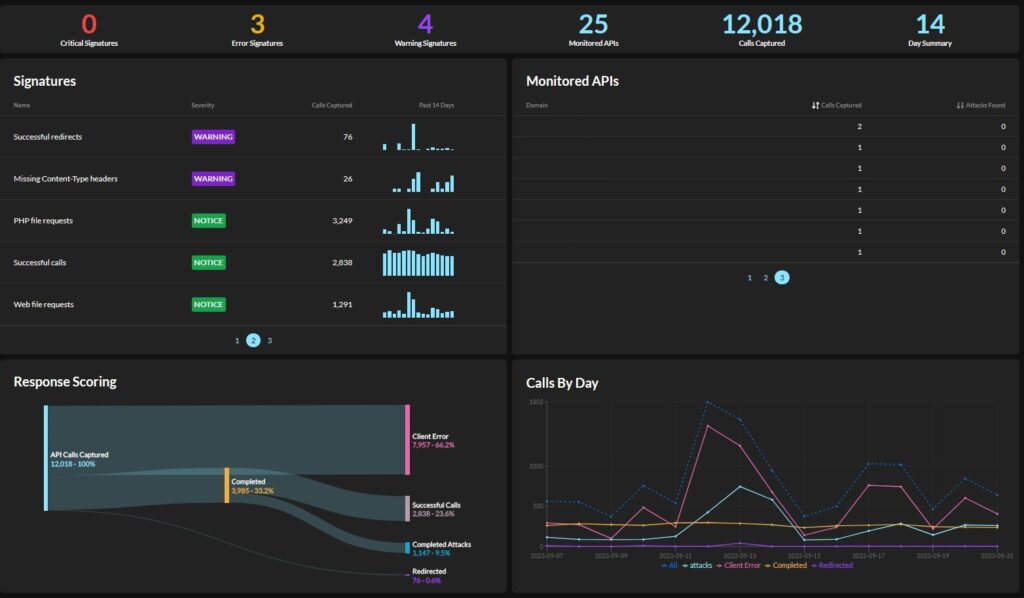
Security Analysts, Engineers, and DevOps Teams
Without Graylog API Security: No visibility into PII flows, making it nearly impossible to detect and triage exfiltration attempts before breaches occur.
With Graylog API Security: Discover APIs and PII flows in real time, going beyond headers and analyzing full API request and response payloads to identify potential exfiltration attempts faster.
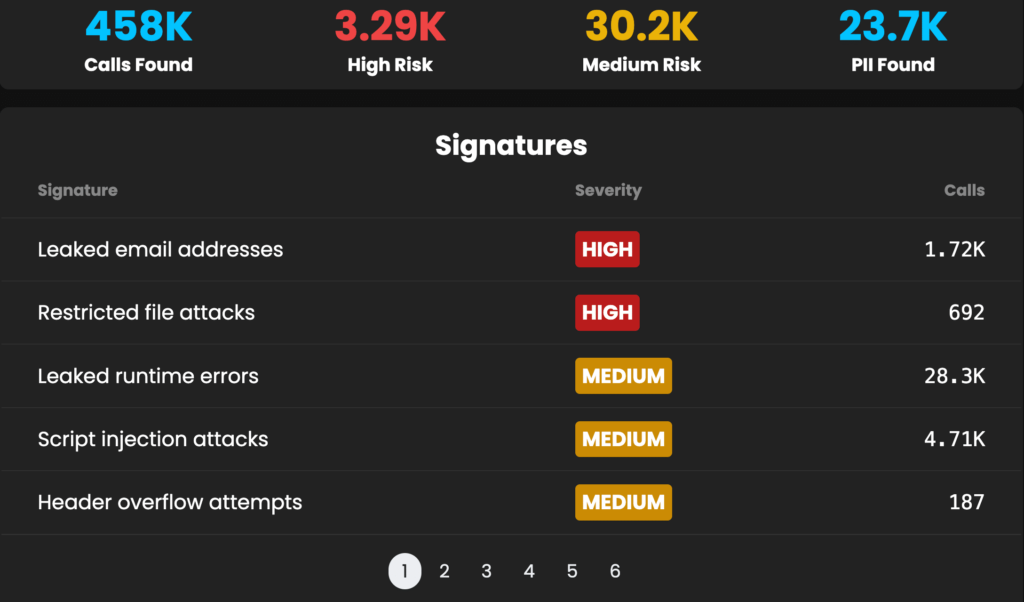
Without Graylog API Security: Manually sifting through API logs without a clear way to identify which APIs are handling sensitive PII, making it difficult to prioritize high-risk APIs, increasing incident response times, and leaving critical data exposure risks undetected.
With Graylog API Security: Prioritize threats based on PII exposure with automatic risk scoring so you can focus on securing high-risk APIs first.
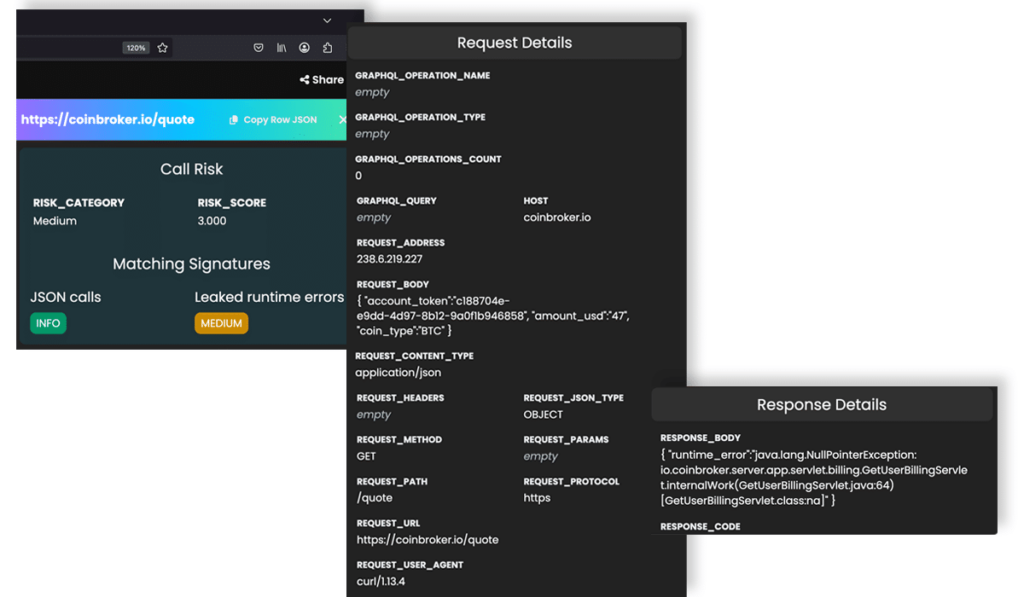
Security Analysts, Engineers, and DevOps Teams
Without Graylog API Security: No visibility into PII flows, making it nearly impossible to detect and triage exfiltration attempts before breaches occur.
With Graylog API Security: Discover APIs and PII flows in real time, going beyond headers and analyzing full API request and response payloads to identify potential exfiltration attempts faster.

Without Graylog API Security: Manually sifting through API logs without a clear way to identify which APIs are handling sensitive PII, making it difficult to prioritize high-risk APIs, increasing incident response times, and leaving critical data exposure risks undetected.
With Graylog API Security: Prioritize threats based on PII exposure with automatic risk scoring so you can focus on securing high-risk APIs first.

Incident Response Teams
Without Graylog API Security: Slow, reactive investigations due to incomplete API request and response data, leading to prolonged dwell time for attackers.
With Graylog API Security: Detect suspicious API behavior with customizable alerts and leverage triage guidance for faster forensic investigations, actionable recommendations, and rapid response.
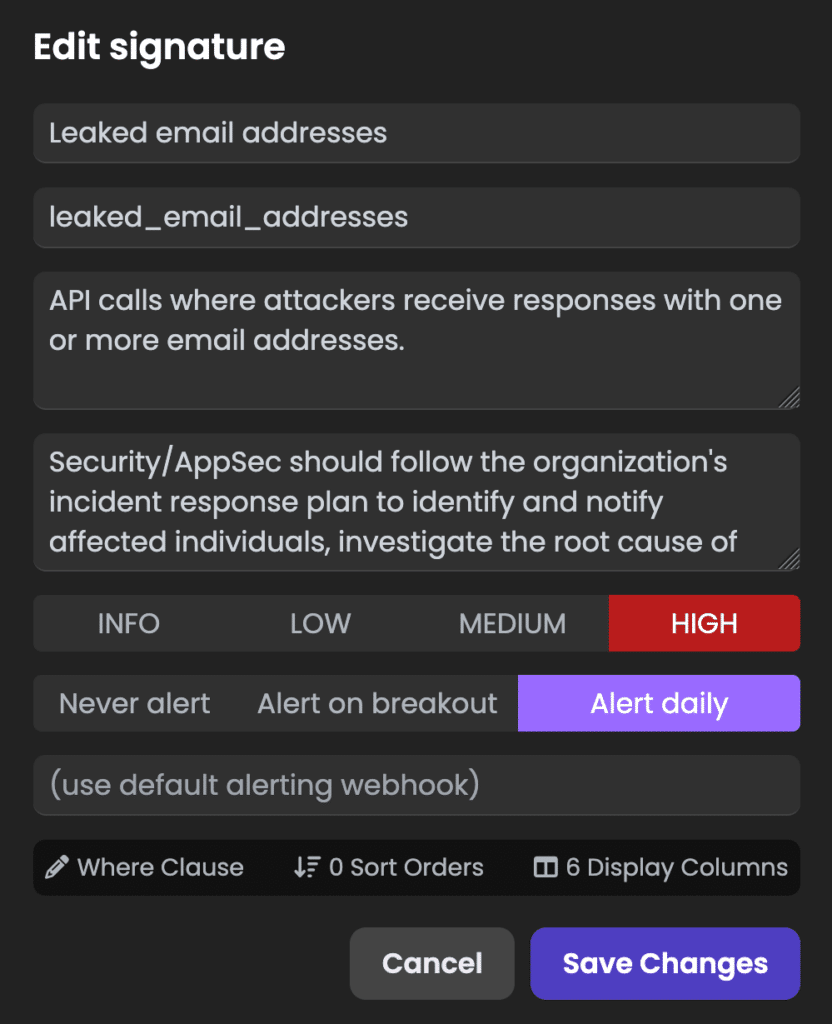
SecOps Teams
Without Graylog API Security: WAFs and API Gateways miss API-specific risks, preventing security teams from connecting API threats to broader attack patterns.
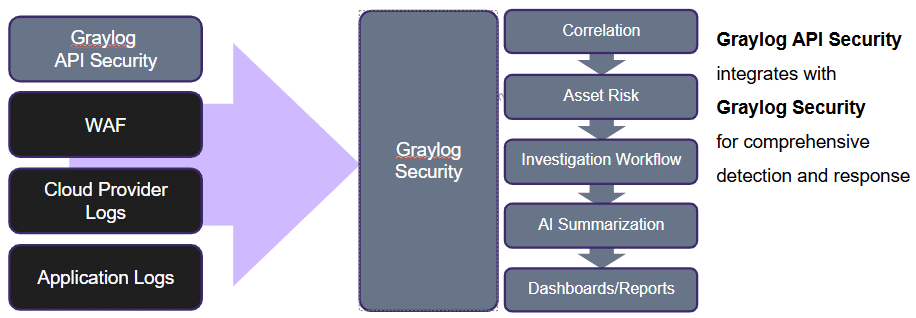
With Graylog API Security: Integrate API security insights into Graylog Security and augment centralized security operations with API-specific context.
Graylog API Security: Real-World Industry Use Cases
USE CASE
Banking & Insurance
Attackers exploit session token hijacking to impersonate authenticated users and extract financial data. Graylog API Security detects anomalies in session behavior and flags unauthorized API access before fraudulent transactions occur.
USE CASE
Healthcare
API misconfigurations expose electronic health records (EHRs), allowing unauthorized access to patient data. Graylog API Security automatically discovers APIs handling PII and alerts security teams to misconfigured endpoints before data leaks happen.
USE CASE
Public Sector
Attackers exploit session token hijacking to impersonate authenticated users and extract financial data. Graylog API Security detects anomalies in session behavior and flags unauthorized API access before fraudulent transactions occur.
USE CASE
Supply Chain
Cybercriminals exploit third-party API integrations to siphon supplier and logistics data. Graylog API Security continuously monitors API request patterns, detecting suspicious data transfers before they lead to operational disruptions.
USE CASE
Education
Unsecured student information APIs allow attackers to steal enrollment records and personally identifiable information. Graylog API Security pinpoints PII exposure points and enables schools to enforce stricter API access policies.
Get Ahead of API Threats Before They Become Breaches
Don’t wait for a security incident to expose your API blind spots. Talk to an expert and learn how we can help. Start discovering and securing PII within your APIs today with Graylog API Security.
Get the Monthly Tech Blog Roundup
Subscribe to the latest in log management, security, and all things Graylog blog delivered to your inbox once a month.



