Being a security analyst tracking down threats can feel like being the Wile E. Coyote to an attacker’s Road Runner. You’re fast, but they’re faster. You set up alerts, but they still manage to get past your defenses. You’re monitoring systems, but they’re still able to hide their criminal activities.
Threat detection and incident response (TDIR) should help you create high-fidelity alerts that reduce false positives so you can focus on the malicious or abnormal activity that matters most. However, building detections yourself can be time-consuming or require additional experience you don’t have yet.
When you combine the MITRE ATT&CK knowledge base with vendor-agnostic Sigma rules, you can accelerate your TDIR maturity for faster detection and investigations.
What are the fundamental elements of threat detection and response (TDIR)?
Threat detection and incident response (TDIR) processes and platforms enable security teams to identify, assess, investigate, and respond to indicators of an attack. These platforms and tools enable the following related but distinct functions:
- Threat detection: collecting, correlating, and analyzing data generated by the company’s IT environment to identify threats to networks, endpoints, assets, and applications, including cloud-based technologies.
- Incident response: investigating and responding to threats that can lead to a data breach, including investigating alerts, isolating assets, remediating issues, and restoring impacted systems.
Historically, organizations implemented either a security information and event management (SIEM) or a security orchestration, automation, and response (SOAR) platform to manage these tasks. However, cloud technologies, like Software-as-a-Service (SaaS) applications, generate high volumes of data, making these traditional technologies expensive and inefficient.
As organizations seek to modernize their IT and cybersecurity infrastructures, they increasingly look for cost-effective, easy-to-navigate solutions that can manage the four steps of the TDIR lifecycle:
- Detection: Identifying a potential threat by monitoring the IT environment for abnormal activity and known threats
- Analysis: Reviewing alerts to assess potential impact and prioritize next steps
- Response: Mitigating and remediating the identified threat with containment activities, like taking systems offline, resetting passwords, or
- Recovery: Returning systems to their pre-incident state so the organization can resume operations
How does MITRE ATT&CK relate to TDIR?
The MITRE ATT&CK(R) knowledge base categorizes adversary behavior according to:
- Tactics: why an adversary performs an action
- Techniques: how an adversary achieves an objective
- Procedures: examples of tactics and techniques in the real world
These tactics, techniques, and procedures (TTPs) create a common language for security analysts so that they can build detections and analytics across three levels of security maturity. Additionally, the MITRE Cyber Analytics Repository (CAR) defines a data model for specific tools so you can use a validated analytics set.
Level 1
Organizations with limited resources are starting to build out their security operations and analytics programs.
At this early stage, you should work on collecting data from sources that can help identify as many techniques as possible, like data about:
- Process and process command line
- File and registry
- Authentication
- Packet capture
Once you start collecting this data, you can build detections to compare the data to known threats.
Level 2
After correlating and analyzing basic log data, you can mature your data strategy by incorporating automation and additional cybersecurity tools. For example, while Level 1 may be primarily IT log data and endpoint detection and response (EDR), Level 2 may include additional technologies like user and entity behavior analytics (UEBA) or monitoring Application Interface Programming (API) security.
Further, you can start building your own detections by combining ATT&CK’s knowledge base with threat intelligence. Once you understand how an attack works, you can test the detection against your system so you know what your log data would show you.
Level 3
At this security maturity level, you can start running tests against your systems regularly by having a red team that emulates adversary behaviors. Malicious actors try to hide their attacks and methods so that they can achieve their objectives.
Your defenders can create detections while your red team tries to execute an attack. The red team will think and act like an adversary rather than a formula, so that the defenders can see whether the alert works as intended.
How do Sigma rules relate to TDIR?
Sigma rules are vendor-agnostic detection rules that security teams can use to identify known threat activities. Where ATT&CK uses the word “analytics,” Sigma rules use the term “detection rules.” While the MITRE CASCADE research project attempts to automate investigation work and runs analytics, it only runs analytics against data stored in a limited number of proprietary locations.
The Sigma rule repository offers three types of rules:
- Generic detection: detect a behavior or implementation of a technique or procedures
- Threat hunting: look for a known suspicious or malicious activity
- Emerging threats: identify activity related to timely and relevant threats, like zero-day vulnerabilities or malware campaigns
As vendor-agnostic detections, Sigma rules give security teams a way to implement threat detection capabilities, even if they don’t have a traditional SIEM or SOAR tool.
How combining ATT&CK and Sigma rules improves TDIR
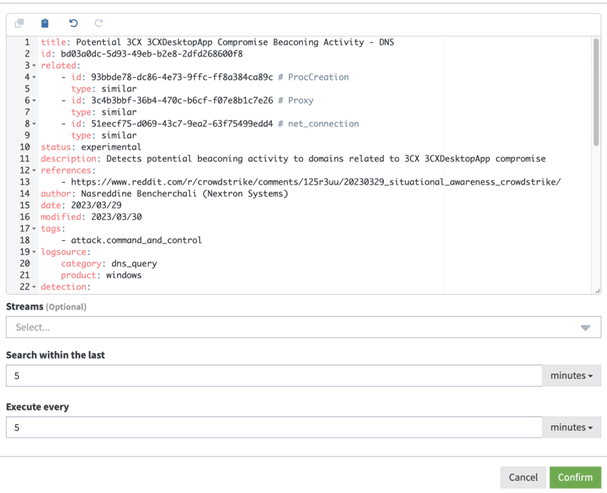
Many Sigma rules are directly mapped to ATT&CK tactics and techniques. For example, in a Sigma rule to look for indicators of compromise (IoCs) from a supply chain attack exploiting a vulnerability in the 3CX Desktop Application the tag indicates the ATT&CK tactic:
By combining ATT&CK knowledge base data with Sigma rules, you can mature your security program without having to invest in additional, expensive technologies.
Automation
By combining the Sigma rule with ATT&CK information, your security team can identify opportunities for removing repetitive tasks that lead to human error risk. For example, with detections mapped to TTPs, security teams can identify and rapidly implement analytics that enable two use cases:
- Tactical: getting alerts for known threats relevant to their IT environment
- Proactive threat hunting: using threat intelligence to proactively identify TTPs, like command and control or exfiltration, relevant to your risk tolerance
Instead of building the detections on your own, you should look for solutions that provide out-of-the-box content to support your needs, enabling you to automate the monitoring for faster detection and incident response.
Risk reduction
When choosing Sigma rules, you can focus on use cases earlier in the attack lifecycle. From a proactive standpoint, high-fidelity detections that capture activity during the Initial Access stage prevent malicious actors from gaining or maintaining unauthorized access, hopefully preventing them from getting to the Exfiltration stage. Since you can choose Sigma rules based on their ATT&CK tags, you can identify the ones that help you improve key security metrics like Mean Time to Detect (MTTD).
Faster investigations
The sooner you detect an incident, the faster you can investigate it. Malicious actors seek to hide their activities, so tracing an incident’s root cause can become time-consuming when you have multiple disconnected tools. By aggregating and correlating events, you can leverage Sigma rules and ATT&CK TTPs to identify likely attack paths, improving Mean Time to Investigate (MTTI).
Cost reduction
When you prevent attackers from running malicious code or maintaining a foothold, you also reduce the amount of time and money spent on incident response. Containing the attack before a threat actor can compromise a system means that you limit recovery costs. With fewer impacted systems, the organization also reduces business interruption costs.
Graylog Security: TDIR with Detection Chains
Using Graylog Security, you can rapidly mature your TDIR capabilities without the complexity and cost of traditional Security Information and Event Management (SIEM) technology. Graylog Security’s Illuminate bundles include subsets TruKno rulesets so that you have content that includes Sigma detections, enabling you to uplevel your TDIR with threat hunting capabilities and correlations to ATT&CK TTPs.
By leveraging our cloud-native capabilities and out-of-the-box content, you gain immediate value from your logs. Our anomaly detection ML improves over time without manual tuning, adapting rapidly to new data sets, organizational priorities, and custom use cases so that you can automate key user and entity access monitoring.
With our intuitive user interface, you can rapidly investigate alerts. Our lightning-fast search capabilities enable you to search terabytes of data in milliseconds, reducing dwell times and shrinking investigations by hours, days, and weeks.
To learn how Graylog Security can help you implement robust threat detection and response, contact us today.



