As a kid, treasure hunts were fun. Someone gave you clues and a map so you could hunt down whatever hidden item they left for you. However, as a security analyst, your incident investigations often have clues but lack a map. An alert fires. You search through your vast collection of log data. You hope to find the next clue while trying to figure out the attacker’s next steps.
The MITRE ATT&CK framework gives you a map that helps you understand how attackers move from one point to another, even across complex systems and networks. Understanding how to use the MITRE ATT&CK Framework as part of your larger threat detection and incident response (TDIR) practices helps you reduce alert fatigue and improve key cybersecurity metrics.
What is the MITRE ATT&CK® framework?
Originally developed in 2013, the MITRE ATT&CK framework uses publicly available threat intelligence to document and categorize common threat actor tactics, techniques, and procedures (TTPs). The non-profit research center MITRE created the framework for an internally developed project, FMX, that would help identify advanced persistent threats (APTs) using endpoint security data and analytics.
Over time, the ATT&CK knowledge base has become a critical resource for threat hunters and security analysts, helping them understand attacks, investigate incidents, and implement appropriate risk mitigation controls.
Some common use cases include:
- Detections and analytics: building alerts for various adversary techniques
- Threat intelligence: creating a common language for structuring, comparing, and analyzing threat information
- Adversary emulation and red teaming: providing information that helps defenders re-create threats across various sophistication levels
- Assessment and engineering: reviewing and improving the organization’s security capabilities to make informed decisions about cybersecurity investments or logging
How is ATT&CK Organized?
Initially, ATT&CK can feel overwhelming because it drills down into details about adversary objectives and activities. However, once you understand the knowledge base’s organization, navigating the information becomes easier.

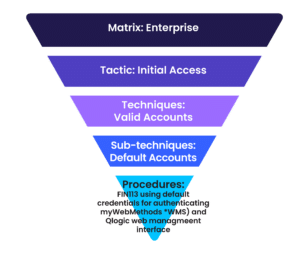
Matrices
The matrices focus on three environments or devices:
- Enterprise: typical corporate IT systems and networks, including Windows, MacOS, Linux, PRE, Azure AD, Office 365, Google Workspace, Software-as-a-Service (SaaS), Infrastructure-as-a-Service (IaaS), network, and containers
- Mobile: device access and non-device network-based threats for Android and iOS
- Industrial Control Systems (ICS): attack strategies specific to technologies like supervisory control and data acquisition (SCADA), distributed control systems (DCS), industrial automation and control system (IACS), programmable logic controllers (PLCs), programmable automation controllers (PACS), remote terminal units (RTUs, control servers, intelligence electronic devices (IEDs), and sensors
Tactics
The tactics describe the adversary’s reason for engaging in a technique or sub-technique. For example, the ATT&CK Enterprise Matrix outlines the following objectives:
- Reconnaissance: gathering information about systems and networks
- Resource development: creating, purchasing, or compromising/stealing resources to support activities
- Initial access: gaining unauthorized access to networks
- Execution: running malicious code on local or remote systems
- Persistence: maintaining access despite system restarts, updated credentials, or other interruptions
-
- Privilege escalation: gaining higher-level permissions
- Defense evasion: preventing defenders from detecting activity
- Credential access: using stolen account names and passwords
- Discovery: learning about the compromised environment
- Lateral movement: exploring networks by moving across various systems and accounts
- Collection: gathering interesting data
- Command and control: communicating with or taking over systems
- Exfiltration: stealing sensitive information
- Impact: manipulating, interrupting, or destroying systems and data
Techniques
Techniques focus on how malicious actors achieve their objectives and the action that enables this. For example, within the Initial Access tactic, ATT&CK outlines the following Techniques:
- Content injection
- Drive-by Compromise
- Exploit Public-Facing Application
- External Remote Services
- Hardware Additions
- Phishing
- Replication through Removable Media
- Supply Chain Compromise
- Trusted Relationship
- Valid Account
Sub-techniques
In some cases, a technique can include variations on the theme. For example, using Valid Accounts to gain Initial Access can be completed using:
- Default Accounts
- Domain Accounts
- Local Accounts
- Cloud Accounts
Procedures
Procedures are specific examples of adversaries using a sub-technique or technique to achieve an objective. For example, the following adversaries or malware have used Default Accounts as a sub-technique of Valid Accounts to gain Initial Access:
- FIN13
- HyperStack
- Magic Hound
- Stuxnet
Benefits of the ATT&CK Framework
Using the ATT&CK framework to help your security team offers various benefits and supports better outcomes.
Create a Shared Language
ATT&CK standardizes threat actors behaviors, giving everyone involved in security a shared language. By applying these categories to your system, you can more effectively identify adversary behaviors and predict potential attack paths.
Incorporate Threat Intelligence
ATT&CK uses publicly available threat intelligence and incident reporting to build out the TTPs. While individual attacks can look different, adversaries typically have similar objectives, like gaining unauthorized access to sensitive data. Further, while the way they gain that access may look different or use various attack vectors, the strategies and actions often use similar techniques. ATT&CK’s ability to identify these commonalities enables security teams to help understand new attack methodologies and know what to look for.
Complement Other Frameworks
Threat hunters use frameworks to achieve various outcomes. For example, the Lockheed Martin Cyber Kill Chain(R) focuses on the different phases of an attack. ATT&CK compliments the Cyber Kill Chain by providing details about the different actions adversaries can take to complete a particular phase of an attack and provides insight into malicious actors’ reasons for each phase.
Build Detections
Security monitoring tools use log data to document what’s happening in an environment. By building detections that include ATT&CK TTPs, security analysts can correlate the activities they see with potential attacker motivation or next steps. With this capability, they can prioritize alerts more effectively and respond more efficiently.
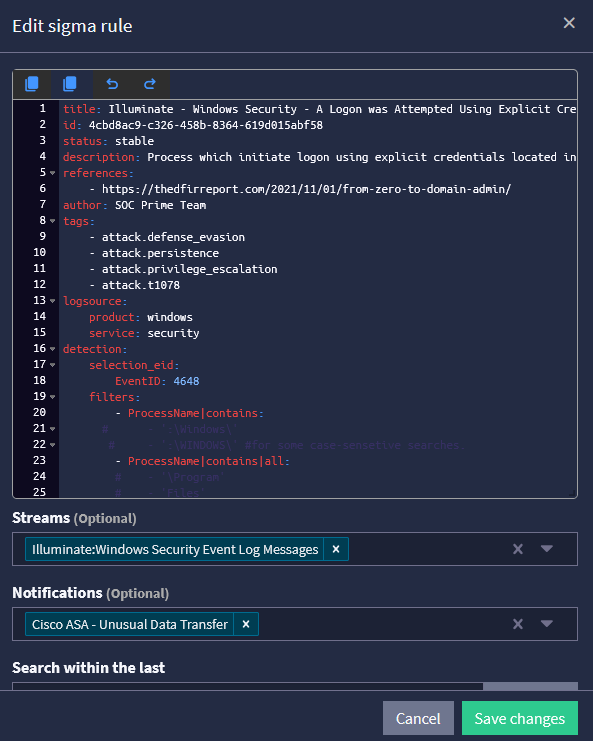
Graylog Security: Threat Detection and Incident Response (TDIR) with ATT&CK
With Graylog Security, you can use prebuilt content to map security events to MITRE ATT&CK. By combining Sigma rules and MITRE ATT&CK, you can create high-fidelity alerting rules that enable robust threat detection, lightning-fast investigations, and streamlined threat hunting. For example, with Graylog’s security analytics, you can monitor user activity for anomalous behavior indicating a potential security incident. By mapping this activity to the MITRE ATT&CK Framework, you can detect and investigate adversary attempts at using Valid Accounts to gain Initial Access, mitigating risk by isolating compromised accounts earlier in the attack path and reducing impact.

Graylog’s risk scoring capabilities enable you to streamline your TDIR by aggregating and correlating the severity of the log message and event definitions with the associated asset, reducing alert fatigue and allowing security teams to focus on high-value, high-risk issues.




