A Syslog server allows for the collection of logs into a centralized log repository. This centralized log repository allows for quick searching of your logs across your organization through different visualization tools. The Syslog web interface will provide the easiest access to the logs, and allows for easy secured remote access.
WHAT IS A SYSLOG SERVER?
A Syslog server is, by all basic terms, a centralized logging solution. While you might have more than one Syslog server, with Graylog you can accomplish all logging in one centralized spot. Syslog servers allow you to collect logs from all types of devices and applications and put them in an easy-to-read format and timestamps. Putting all the logs into one centralized spot allows for quicker forensic investigations and easier correlation across different types of logs like a firewall log and a Unix server, to see one high-fidelity alert.
A Syslog server will keep storing your data until you run out of local disk space, so the best practices around log retention are to keep the data you need to meet any compliance needs and archive everything else for easy retrieval.
Advanced Syslog servers will enhance your security posture by providing automated alerting and reporting on the logs collected. Data segregation and filtering of logs is needed for large enterprises to ensure the Syslog GUI will only present the right data based on RBAC controls. Finally, having a Syslog server will enrich your log data at ingestion time, expanding the logs for many use cases.
WHY SHOULD YOU COLLECT SYSLOG EVENTS?
The reason to collect Syslog log files is that the Syslog protocol is supported by a vast range of devices. Additionally, you can use it to log multiple event types such as user login messages from a router or access denied events from a web server. Syslog is also supported on most network equipment including firewalls, routers, switches, web servers, and some printers. Syslog messages typically include basic information about why, where, and when the log was sent. This information could include the log message, the timestamp the message was sent, and the IP address where the message was sent from. Syslog also includes a severity field which determines how important the message is. Natively, Windows-based servers do not support Syslog but there is a wide range of third party options that allow you to easily collect event logs from Windows servers.
Since the Syslog protocol is widely utilized by so many devices, collecting these log events is very important. Not only can this information help network administrators manage large and complex networks, but it can shed light on potential security issues that can help security analysts gain a greater understanding of their environment.
HOW TO SETUP GRAYLOG AS A SYSLOG SERVER
After you have Graylog installed, you need to set it up to collect the logs. Go under System -> Inputs menu, and then Launch a new input. Under the Select Input drop-down, pick Syslog UDP, and then pick the Launch new input button.
Fill out the details by selecting the node to start the listener on, or select the Global option, then pick the port for the listener to start on. Syslog by default is UDP/514, but you would need to run Graylog as root to have the listener bind to anything below 1024. It is recommended to start it at 1514, and use the firewall to redirect the traffic from 514 to 1514.
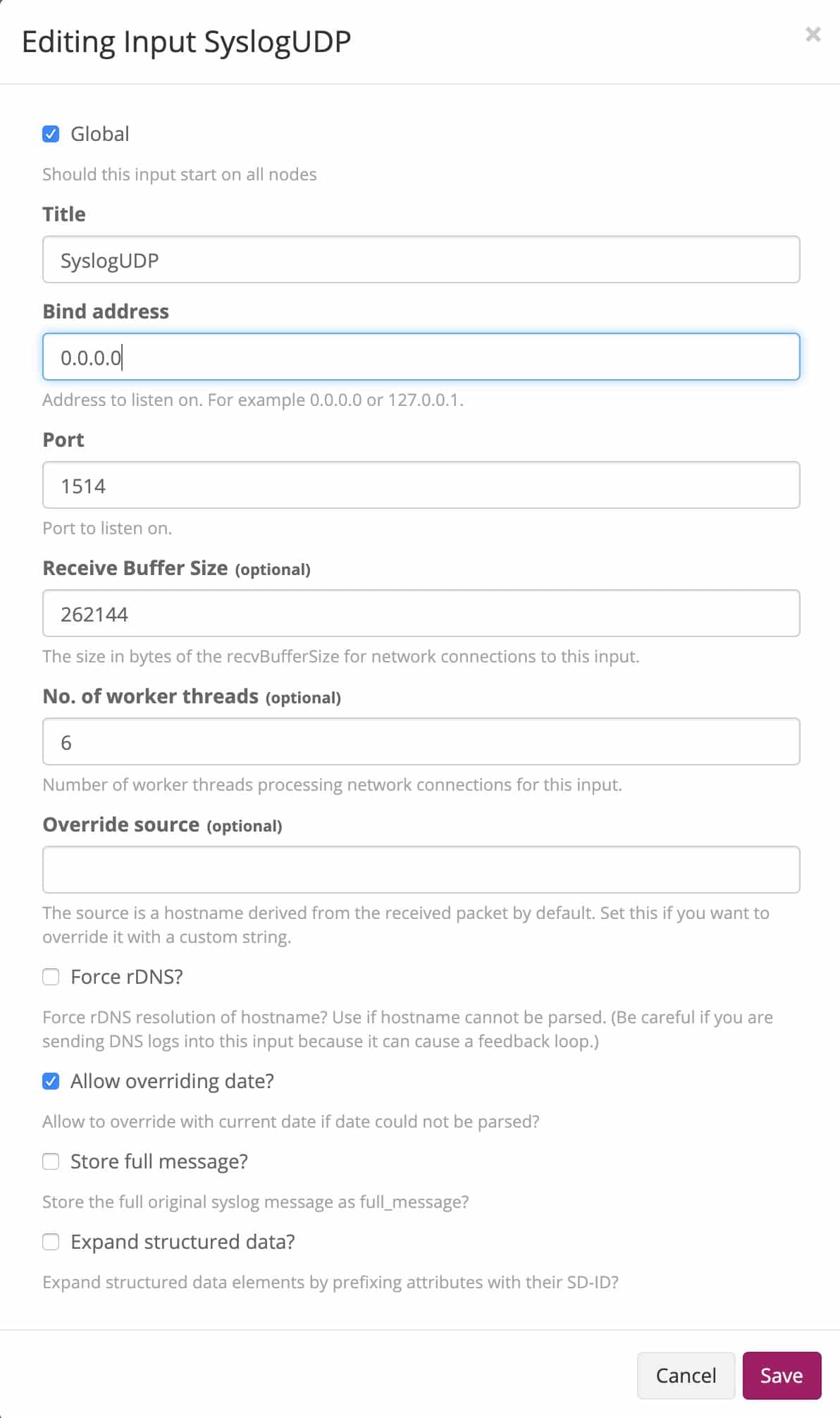
Click Save and the input should start up, noted with a green “1 RUNNING” box next to the name. Now send in Syslog data to the new port and verify it is collecting. Go to the Search tab, and now you should have data just sent in, looking similar to below.
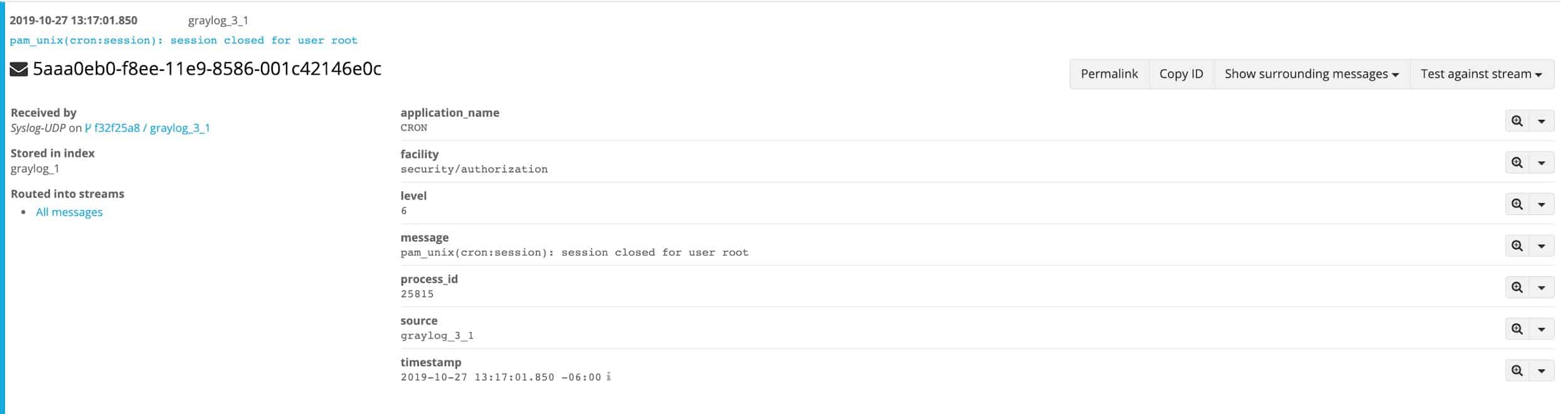
Congratulations, you have taken the first steps towards a centralized Syslog server. Keep going, and get all of your logs collected.
CONCLUSION
Keep in mind that the Syslog web interface can be pre-built to parse logs depending on the format, and different types of log sources can send in vastly different logs. Different retention times, disk space and visualizations might be needed to get the most out of all log data.



