Writing your own Graylog Processing Pipeline functions
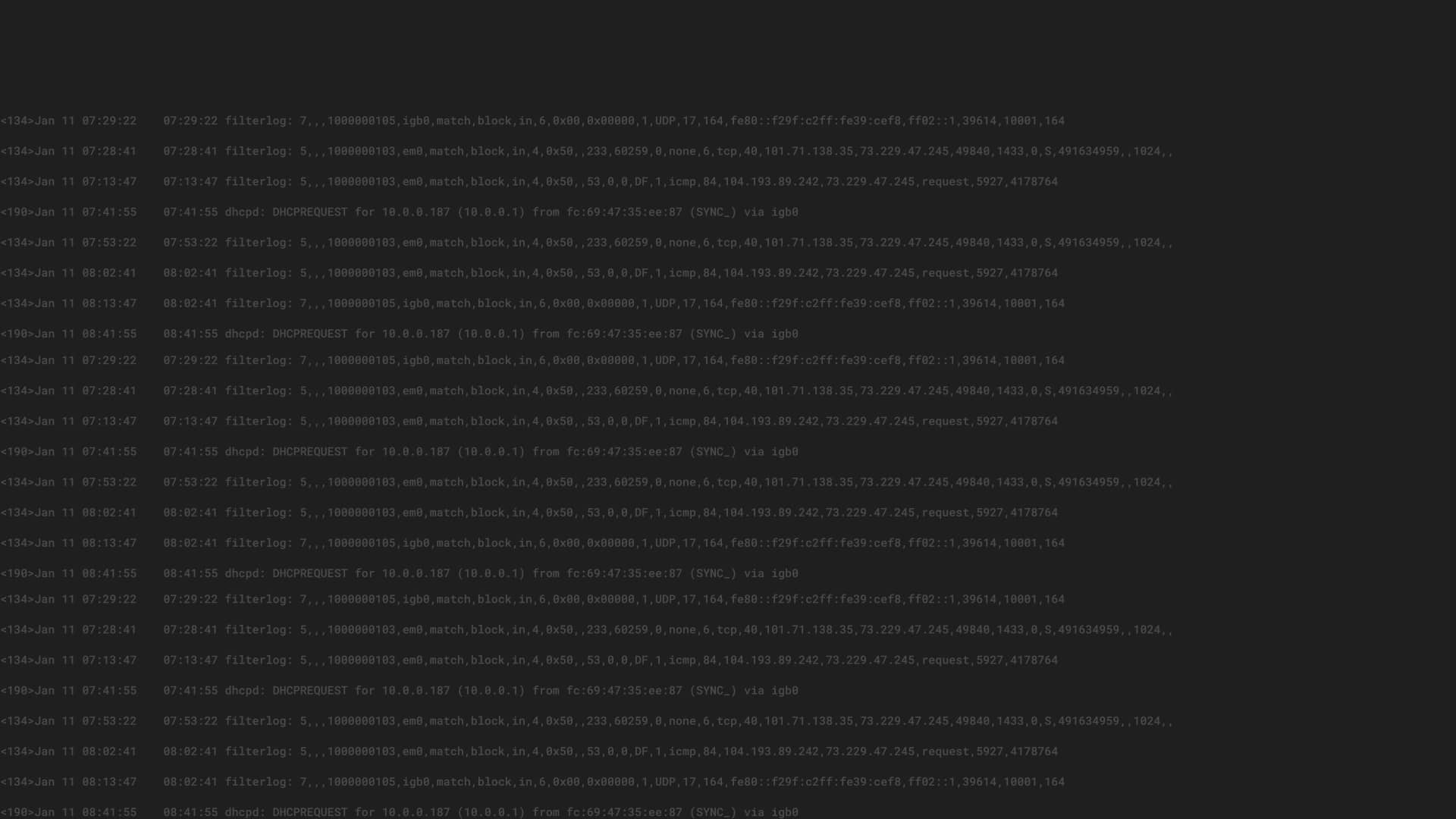
In this post, we will go through creating your own processing pipeline function. Some Java experience will be helpful, but not necessary. We will be taking it step-by-step from understanding a pipeline, to implementing and installing your function.
Why Should You Bother With Information Technology Operations Analytics?
Your organization’s IT system is a complex network of intercommunicating devices that can provide you with an abundance of useful data – if you apply the right practices to gather and filter it. See how ITOA can help.
What Are the Benefits of Monitoring Event Logs?

By monitoring event logs, you can gain deeper insight into system metrics, localize process bottlenecks, and detect security vulnerabilities.
Visualize and Correlate IDS Alerts with Open Source Tools

We will walk through integrating the IDS tool, Snort, with Graylog in order to detect and analyze suspicious activity. We will then provide examples of correlating IDS alerts with both network connection and operating system logs using Graylog.
Using Trend Analysis for Better Insights

A centralized repository of logs generated by your devices and applications stores a wealth of data. Trend analysis of that data gives you rich insight into activity in your environment.
Troubleshoot Slow MongoDB Queries In Minutes With Graylog

Database application performance troubleshooting can be time consuming and frustrating. The good news is that many of these issues can be identified and resolved using the information stored in log data.
Trend Analysis with Graylog

Trend analysis provides rich information and yields insights into the operational and security health of your network that are otherwise difficult to discern. Learn how to use Graylog to perform the types of trend analysis discussed previously.
Top Use Cases for Log Analysis

There is a wide scope of use cases for log analysis – from tackling security and performance issues head-on to enhancing the quality of your services. This post discusses these use cases in more detail.
Tips & Tricks #1: How to Quickly Debug Your Stream Rules With One Click

In the first blog post of our new Tips & Tricks series, I want to show you a quick way to debug your stream rules to test whether your targeted messages will accurately be matched by a Graylog (http://docs.graylog.org/en/latest/pages/streams.html).
The Power of Centralized Logging

Log files give you information about your IT environment. Having those logs centralized is essential to understanding your whole environment.
The Log Viewer – Your Window into Log Management

An immeasurable amount of data, in raw, unfiltered form, exists all around us. For most of us, to be able to properly categorize and “read” that data, we first must convert it into a format that we can understand – which is where the log viewer comes in.
The Data Explosion and its Effect on Security

The shift to digital business is driving a massive expansion in the volume of data that organizations produce, use, and store. It is also accelerating the velocity of data—that is, the data is changing more rapidly than ever before.


