Centralized Log Management for Access Monitoring
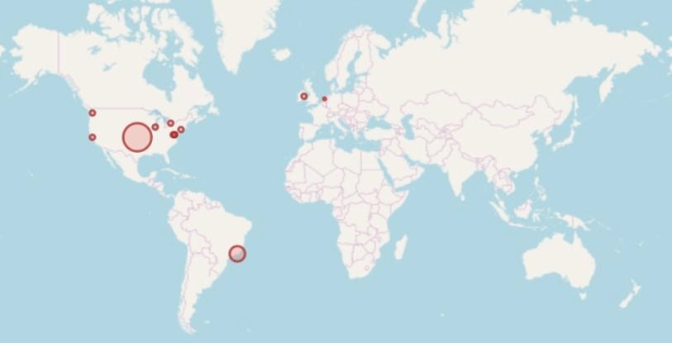
With security analytics and anomaly detection, centralized log management enables robust access monitoring.
Graylog Security – The Affordable SIEM Alternative
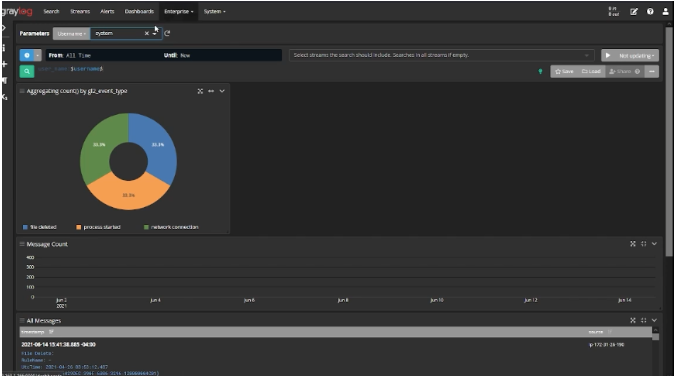
Cyber resiliency is the new norm in cybersecurity. Nothing can be 100% secure, and you’re looking for a cost-effective solution to enhance your security posture.

