Cyber resiliency is the new norm in cybersecurity. Nothing can be 100% secure, and you’re looking for a cost-effective solution to enhance your security posture.
At the same time, the rapidly expanding cybersecurity technology market makes it hard to find something that best fits your needs. Most people looking at Security Information and Event Management (SIEM) platforms want a tool that gives them high fidelity alerts to prevent their security analysts from drowning in false positives.
On the other hand, they’re a sizeable up-front technology investment that often comes with extra bells and whistles that you might not need. As if that wasn’t enough, they also require you to hire employees with product-specific query skills.
What if you could take a technology that you’re already using – and that your IT team already understands how to use – and make it do “double duty” as a security analytics platform?
Graylog’s Security solution solves this problem. Built with the end-users in mind, our platform requires no additional training and gives you the security analytics you need. No more, no less.
Graylog’s Security solution meets your company and team where they are. Our correlation engine generates high fidelity alerts, comes with lightning-fast speed, and requires no specialized security query training to help you level up your security effectively and cost-efficiently.
The Graylog Correlation Engine: High Fidelity Alerts for Enhanced Detection, Investigation, and Response Times
Even expensive SIEMs start with the foundation of event log data to help fire alerts. Since both log management tools and SIEMs ingest the same data, they provide many similar security functionalities. In fact, many companies use their centralized log management solution to help optimize their SIEM.
Graylog’s correlation engine allows you to skip the specialized SIEM query language and focus on what you need to quickly mature your security.
Graylog’s correlation engine gives you the high-fidelity alerts you need for early detection and rapid response. You can receive real-time alerts directly from the application and be sure that the relevant information is available when you need it. For example, you can set conditions to trigger an alert for a high rate of login failures, grouping them by user name to quickly detect a brute force attack.
If you’re a small IT team working to better secure your environment, Graylog’s high fidelity alerts can reduce alert fatigue so that your team can focus their time on threats instead of false positives.

Graylog Reporting Dashboards: Easier Documentation for a Robust Compliance Posture
Most people consider compliance a necessary “check the box” evil because it requires a lot of time-consuming manual effort.
You can use Graylog’s Parameterized Dashboards as part of your compliance reporting and documentation.
Your leadership needs to know that you have controls in place – and that they’re working. The problem is that they don’t want or need the technical details. They need things like high-level, business-focused metrics to show that your team is monitoring security.
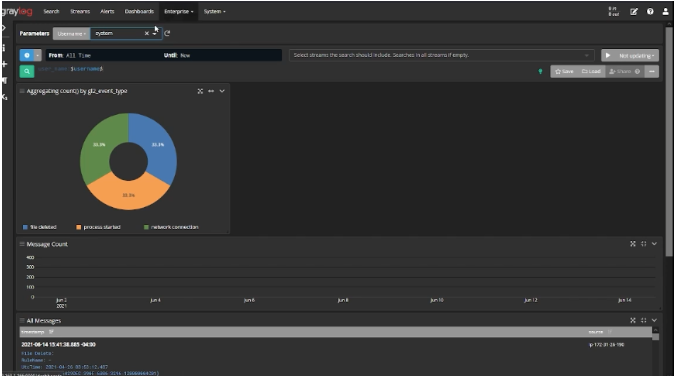
With Graylog’s Dashboards, you can bridge the language gap using visualizations, like pie charts or bar graphs. These tell the visual story your leadership needs, giving them enough detail for making decisions around future IT and human resource investments.



You can set your Dashboards up as reports that give leadership the answers to critical security questions. You can automate many redundant tasks that people associate with compliance by forwarding them to leadership on a set schedule.
Graylog Cloud: Rapid Deployment for Enhanced Return on Investment
Graylog Cloud is an option if you’re looking at a rapid deployment option for replacing a current security technology. Graylog Cloud gives you all the security visibility you need with all the benefits of cloud technologies, so you can overcome many of the traditional barriers that implementing a security technology creates.
With our prebuilt content, you can get started quickly. The pre-built content includes search templates, dashboards, correlated alerts, and dynamic lookup tables to meet your security needs without having to go through a long deployment process.
You need integrations across business-critical systems and real-time visibility for a robust cybersecurity posture. You can integrate all your technologies – security and business – with REST APIs and then leverage real-time data to help detect anomalies across all on-premises and cloud-based resources.
With no installation, setup, or maintenance requirements, you can go live with your Graylog Cloud deployment in less than 2 days.
Lightning Fast: Easy Exploration for Rapid Onboarding
Graylog’s rapid deployment, scalability, flexibility, and speed give you everything you need to help you mature your security posture. Whether you’re in a new role or adding new staff to your team, you need something that has a low learning curve to reduce overall costs.
CISO
When you’re moving away from something already deployed, you’re usually looking for a better overall experience. You’re looking for a vendor that offers consistency and ease of use.
With Graylog, you don’t have to worry about the million different add-ons, dropdowns, or applications. We purpose-built our platform so that you can ingest all the data you need and then easily create pipeline rules without having to worry about specialized tooling or query languages.
You need to solve your security problems, not spend time trying to figure out how to get your tools to give you the information you need. Graylog’s solution makes detecting and investigating easier for everyone.
Whether you’re an Everything CISO or a Specialized CISO, Graylog’s solution gives you visibility into all aspects of security with Dashboards. Creating Dashboards gives you visibility into the most important information to you without adding to the noise. You can even create multiple Dashboards focused on the specialized information you need.
Security Team Staff
If you’re one of the first security team members, you’re doing a lot of work. You’re trying to detect abnormal activity, respond to alerts, investigate incidents, and then go back for the forensic data supporting everything.
The first thing you need to do is reduce noise. This is where Graylog’s correlation engine and security analytics benefit you most.
Graylog’s correlation engine helps you reduce noise to get the alerts you need and want. By correlating events, you’re able to gain the high fidelity alerts necessary for detecting:
- Brute force login attacks
- Admin logins and creation of new users
- IP scanning your network after touching a high number of unique ports
Using the correlation engine, you can create complex rules that include:
- Per field correlation
- Cross event source correlation
- Negative event monitoring
- Complex correlations
You don’t need specialized query skills or knowledge. If you’re comfortable with lookup tables, you can create the grouping and visualization of security log data so you can see what’s happening. For example, you track users or devices that are bridging the Trust/Untrust gap or devices at risk of mixing auditable data with “out of scope” data.
As you’re looking to uplevel the security posture, Graylog gives you a way to investigate incidents quickly with parameterized searches that allow you to eliminate potential causes and then change the parameter.

The search parameters also help you move from reactive to proactive. Saving parameters as queries means you can investigate or monitor values based on indicators of compromise (IoCs). Pairing this with search workflows gives a way to build and combine multiple searches and then automate the process.

Whether you’re early in your security year or a long-time professional, you have an easy-to-use solution giving you everything right at your fingertips.
Graylog’s Intuitive Interface: Replace the MSSP for More Control Over Security
If you or your team is struggling to manage your MSSP, Graylog offers an intuitive solution. We built the platform to solve many of your current challenges. In other words, we offer an alternative that keeps the end-users in mind.
Our intuitive interface reduces the number of “clicks” it takes to find the information you need while providing unified visibility across your entire IT stack. Your MSSP is collecting some security event logs from your environment already. If they’re not able to collect everything across on-premises, multi-cloud, and hybrid environments, then they’re not giving you the true visibility you need. Graylog was built to integrate with all technologies, no matter where they reside.
Graylog’s high-fidelity alerts and threat hunting capabilities secure your environment themselves, even if they’re less experienced in the security space. By bringing your security capabilities back in-house, you have control over and documentation of everything you’re doing to protect your environment. You don’t need to wonder whether you’re engaging in threat hunting. You’ll know.
Using Graylog to Achieve Strategic Initiatives
With Graylog, you have the ability to truly turn cybersecurity into a revenue enabler. Using Graylog, you have a cost-efficient platform for managing security, availability, and performance.
Graylog gives you the ability to manage your IT operations and security program. With Graylog, you have a single tool for managing IT and security:
- Monitoring for abnormal activity
- High fidelity alerts
- Root cause analysis
- Proactive monitoring
Further, Graylog also has industry-leading anomaly detection with:
- Pre-built security scenarios
- Risk models that identify metrics dynamically
- Expert-built alerts and dashboards
With Graylog’s lightning-fast investigations capabilities, both security and IT teams are more productive while improving key performance metrics that apply – in different ways – to both, including:
- Mean Time to Detect
- Mean Time to Investigate
- Mean Time to Remediate
- Mean Time to Resolve
Graylog Security and Graylog Anomaly Detection: The Analytics You Need No Matter Why You Need Them
Graylog Security brings together everything you love about centralized log management and everything you need from a security platform. With Graylog Security, you get the security analytics functionalities you need without the complexity and costs associated with a SIEM.
Graylog Security is the two-in-one solution that enables IT operations and security teams to ensure robust systems performance and security in one place. Graylog Security gives you pre-built security dashboards that your team can use for monitoring and compliance reporting.
Graylog Anomaly Detection AI/ML, part of Graylog Security, gives you the visibility into user access and cloud security necessary to protect modern systems and networks. Our Anomaly Detection is User and Entity Behavior Analytics (UEBA) combines network profiling with real-life threat use cases, all mapped to the MITRE ATT&CK Framework for rapid detection, investigation, and remediation.