How to Proactively Plan Threat Hunting Queries
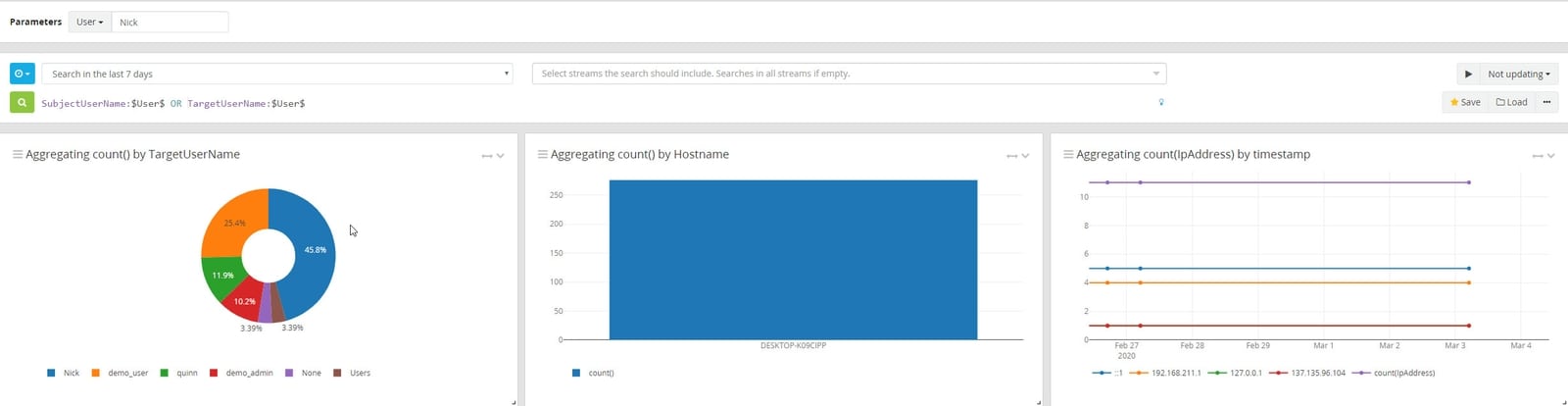
As your security capabilities improve with centralized log management, you can create proactive threat hunting queries for proactive planning. Setting baselines, determining abnormal behavior, and choosing an attack framework helps you mitigate risk and respond to incidents.

