As your security capabilities improve with centralized log management, you can create proactive threat hunting queries. Setting baselines, determining abnormal behavior, and choosing an attack framework helps you mitigate risk and respond to incidents.
Set baselines
To reduce key metrics like the mean time to investigate (MTTI) and mean time to respond (MTTR), security operations teams need to understand and create proactive queries based on their environments.
You can’t detect abnormal behavior in your environment if you don’t know what normal behavior looks like. The first step to establishing queries is to set baselines for expected behavior, like:
- Users and devices that log into systems managing sensitive data
- How often and what time of day users access data sources
- Average number of files users access per day
- Ports, protocols, or services that run on a user’s machine
- Expected CPU, memory, and disk utilization
- Expected network traffic
Choose a framework
Part of threat hunting is understanding the attack lifecycle so that you can trace threat actor behaviors. When building out queries prior to an incident, you want to decide how your organization wants to track these actions within systems and networks. Different attack models exist, including:
- Lockheed Martin Cyber Kill Chain(R)
- FireEye Attack Lifecycle
- Gartner Cyber Attack Model
- MITRE ATT&CK lifecycle
Establish a proactive threat hunting approach
Modern malware and ransomware often evade detections. As threat actors continuously update their malicious code in response to defensive strategies, you need a proactive approach to risk mitigation. Instead of waiting for systems to detect anomalous activities, you can use threat intelligence for contextual business risk and build queries around the tactics, techniques, and procedures (TTPs) that could impact your company.
Creating a schedule for going on proactive threat hunts can help you protect data and security your infrastructure. Using the threat hunting queries, baseline behaviors and attack frameworks, you can also create a schedule for proactive threat hunting that includes:
- Creating a hypothesis based on recent threat intelligence
- Aligning queries to known and emerging TTPs that can impact your organization
- Reviewing data for anomalous behavior
Focus on the Indicators
To set threat detection alerts, you need to consider the indicators of compromise (IoC). Security analysts need visibility into malicious activity to start the next stage of the investigation.
As part of your incident response plan, you should first look for some impact indicators such as:
- Has your antivirus indicated an infection?
- Are there any unusual file names?
- Did you detect a larger than usual number of bounced emails with suspicious content?
- Did you examine all alerts or suspicious log events?
- Can you correlate events with network data?
Detect and Respond
Moving from detection to response can often feel frustrating and overwhelming. However, if you collect data that points you in the right direction, you should create a targeted response. Your prebuilt queries should provide a starting off point that reduces the time the investigation takes.
If not, you should start looking at some of the highest impact response tactics including:
- Blocking unauthorized access and documenting the activity
- Blocking potential malware sources such as suspicious email and website addresses
- Closing high-risk ports or mail servers
- Changing any potentially at-risk administrative passwords or considering PAM for Admin users.
Often, you will need to report the attack to local, state, and federal authorities. When reporting the data security event, you can also leverage event log data such as:
- Location of the compromised device, service, or system
- Hostname
- Media access control (MAC) address
- IP address
- Date of incident
- Time of incident
A centralized log management system gives you not only the data that helps mitigate risk, but it also provides you with all the information necessary to respond to an attack. The more rapidly you respond to an attack, the less damage the malicious actor can cause.
GRAYLOG: PROACTIVE QUERIES WITH CENTRALIZED LOG MANAGEMENT
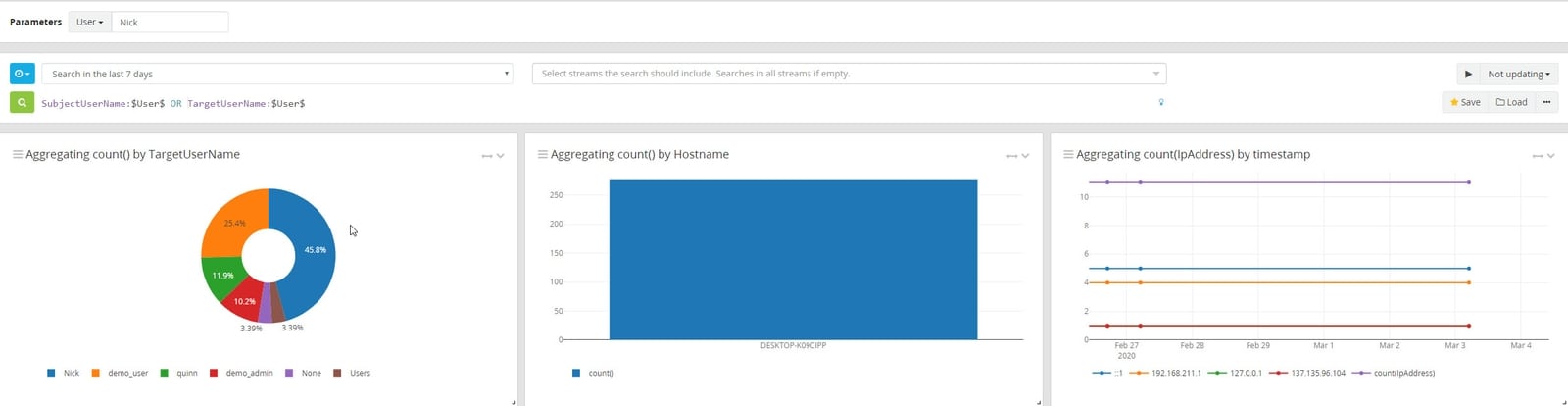
Graylog’s Search Parameters streamline threat hunting and enable more proactive risk management. Security teams can generate queries based on one or more input parameters that act as value placeholders and save them for future use.
By saving these parameterized queries, threat hunting teams can investigate or monitor values that change based on their hypothesis. For example, your team may choose to start a search with IP address, MAC address, or User ID. While the individual value may be unique, the steps in the search won’t. This means that all the threat hunters need to do is copy the value into the parameter to run the saved search.
Paring Graylog’s Search Parameters and Search Workflow capabilities gives threat hunting teams the ability to build and combine multiple searches for any type of analysis into a single action that they can review in the Dashboard.