Event Log Management for Security and Compliance
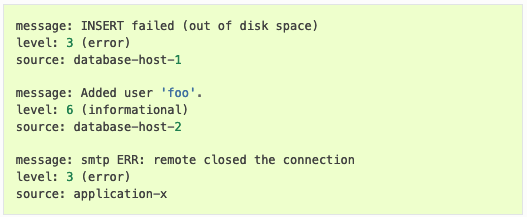
Every action in an organization’s network generates event data, including records produced by operating systems, applications, devices, and users. By following best practices for event log management, you can enhance your cybersecurity posture and enable a more robust compliance program.

