As with any other security and compliance initiative, managing log events can feel cumbersome unless you create a purposeful strategy.
1. STRATEGIZE
While some organizations want to collect all the logs possible, others choose to minimize the amount of data. Your strategy should incorporate the logs you want to collect and have a reason supporting that decision. Too much information creates noise that reduces IT staff productivity. Too little information leaves your organization adrift in the aftermath of a data security incident.
As part of your strategy, you also need to consider the format of your logs. Different systems can use different formats, so you should make sure to capture all data effectively. From the beginning, you need to consider how to aggregate data and whether your logs are exported as JSON, Key Value Pair (KVP), or syslog, or another format.
2. CENTRALIZE
Whether you use a SIEM, a log management tool, or a combination of both, you need a single location for storing all log event data. Storing all log event data in a single place streamlines correlation, analysis, and searching.
Organizations collect log event data from various sources such as applications, operating systems, and users. The underlying reason you collect this data is to gain holistic visibility into all activities occurring in your IT stack. If you have the information centralized, you can more efficiently and effectively correlate the data, particularly when engaging in real-time monitoring to detect anomalies that can indicate a security incident.
Finally, centralizing the event logs streamlines the audit document collection process, which reduces operational costs. With all the information in a single location, you reduce the time it takes to collect the data and ensure that the auditor receives all the data necessary to complete the audit.
3. CONTEXTUALIZE
To use logs effectively for security and compliance management, you need to add context that helps relate the logs to one another. Basic log messages such as “transaction failed” or “user operation failed” fail to provide the information needed for meaningful decision making.
Adding context to the log messages reduces reviewer fatigue and enables more rapid security risk detection.
Example
A log event that simply says “INSERT failed” gives no insight into what caused the failure. However, the example below incorporates the context necessary for using the log event data to trace activities.
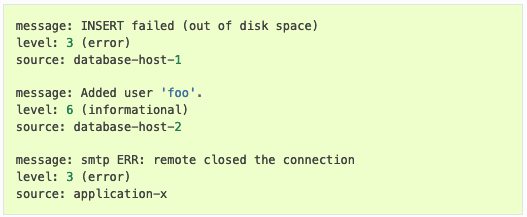
Since the message includes “out of disk space,” you know that the failure is a technical issue instead of a security concern.
4. PRIORITIZE
Log events are not all equally important. Reporting on a poll of C-Level security executives,
Infosecurity Magazine noted that 37% said they received more than 10,000 alerts each month. Of that 10,000, 52% were false positives.
You need to make sure that you set parameters around log events to reduce noise. Systems generate alerts when defined events are detected. By setting a “priority” for an event classification, your security analysts can more efficiently review the alerts and respond to high priority notifications first, ultimately enhancing your security posture.
5. ANALYZE
All the strategizing, centralizing, contextualizing, and prioritizing leads up to using log event data for analyzing events. Your logs provide real-time information about the events occurring across your IT infrastructure that reduce the time it takes to analyze the impact the event is having or will have. With real-time search functionality, your security team can more effectively monitor the events and correlate data more rapidly.
Additionally, you can use logs to analyze trends across your ecosystem. Researching trends gives you a way to set baselines for “acceptable” and “anomalous” activities.
Example
If your Windows operating system always updates on a Tuesday night at 11:59 pm, a log event that notifies your security of a 9 am Wednesday operating system update can signify a security incident. However, if you’re collecting and correlating logs but not analyzing the data, you may not be effectively securing your infrastructure or may find yourself violating a compliance requirement.
ESTABLISHING BEST PRACTICES FOR EVENT LOG MANAGEMENT WITH GRAYLOG
Log management enhances your cybersecurity posture and enables a more robust compliance program. By following best practices for event log management, you reduce the operational costs associated with security monitoring and audit documentation gathering.
Graylog’s flexible and comprehensive approach to detecting, responding, and searching for log event data makes it easier for security teams to prevent data breaches or investigate security incidents.