Connecting Sidecar and Processing Pipelines Using Graylog
We would like to introduce a new series from our blog that takes you back to the basics of Graylog. Written by your Graylog engineers, these installments will be a deep dive into the main components of our platform.
A practical approach to Open Source network security monitoring

We will take a look at how you can analyze network traffic data in order to detect network intrusions. Every phase of intrusion will leave traces and with the correct tools in place, you can detect these early on and take countermeasures.
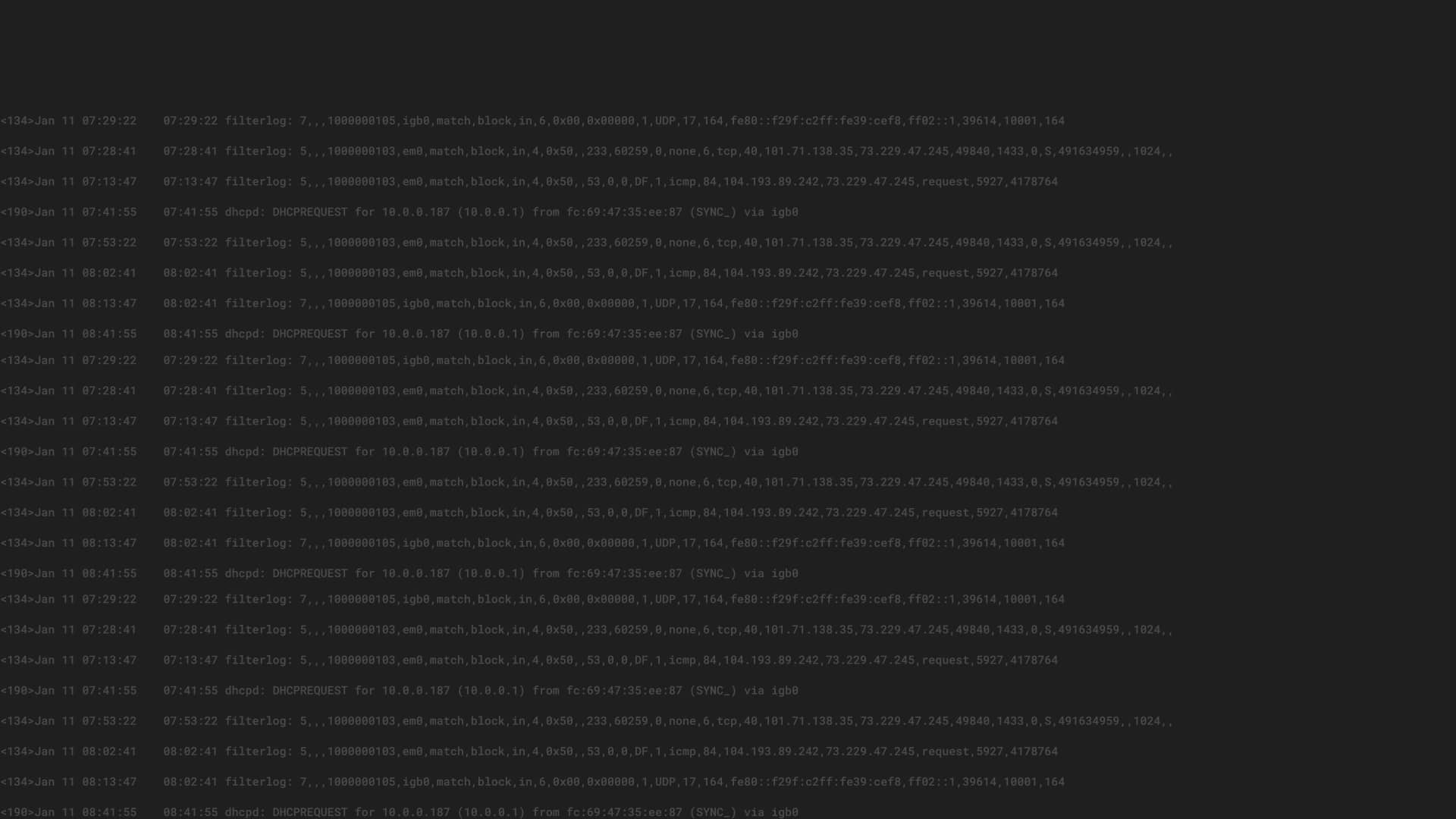
Windows Filebeat Configuration and Graylog Sidecar

Graylog sidecar can create and manage a centralized configuration for a filebeat agent, to gather logs from a local server that is not part of the Windows Event Channel and across all your infrastructure hosts.
What is IT Operations Analytics (ITOA)?

IT Operations Analytics (ITOA) is a vital asset to extract those valuable insights buried in piles of highly articulated data, and a powerful asset to sift through all the complexities of the Big Data.
Troubleshooting with Log Management – Best Practices

Troubleshooting is centered on first identifying and then rectifying problems within the system. Since logs record all kinds of event data, proper log management is a crucial step to figuring out exactly what went wrong – as well as when and how.
Threat Intelligence And Log Management: Security Through Automation

A well-integrated and fully-automated threat intelligence requires a proper centralized log management tool to attain a strong cybersecurity posture.
Parsing Log Files in Graylog – Overview
Want to know all about parsing log files? The experts here at Graylog prepared a useful guide for you.
Log Indexing and Rotation for Optimized Archival in Graylog

How do I rotate around my logs and configure them in Graylog? Let’s talk about the best practices around log retention and how to configure them in Graylog.
Keeping Graylog Secure

After you are up and running on Graylog, there are a few different areas where you can limit the attack surface. This a plan which includes best practices. CIA Triad has published some industry best practices which is a good starting framework.
ITOps vs. DevOps: What Is the Difference?

ITOps vs. DevOps: where does one end and the other begin? What does each role encompass and how can you tell the difference between them?
How to Use Graylog Lookup Tables
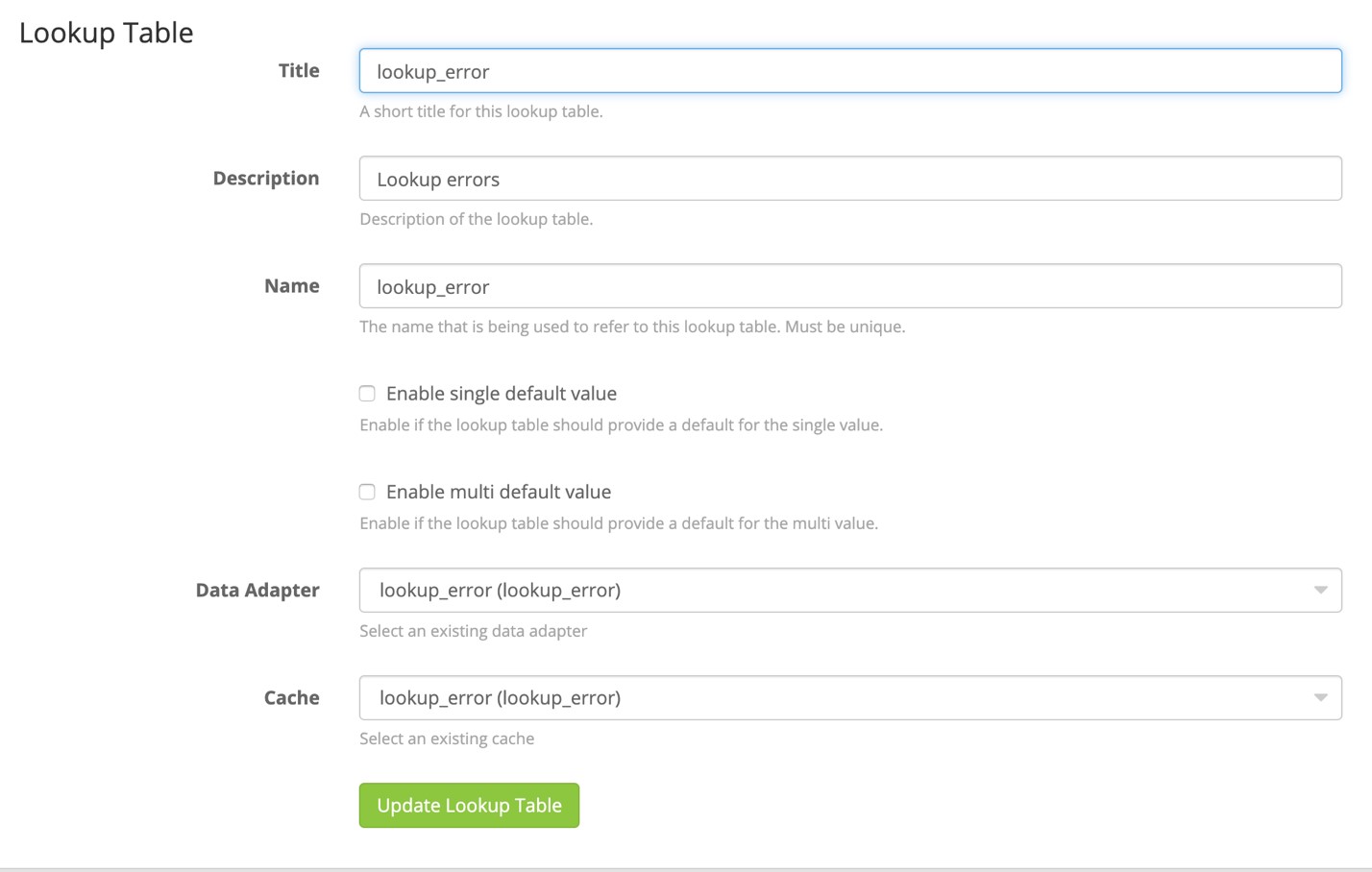
Graylog has a few built-in lookup tables and common adapters to read in the data from various locations. In this article, we’ll go over the steps needed to configure your lookup table.
How to use Graylog as a Syslog Server

A Syslog server is, by all basic terms, a centralized logging solution. While you might have more than one Syslog server, with Graylog you can accomplish all logging in one centralized spot.

