As cyber threats targeting critical infrastructure continue to evolve, the energy sector remains a prime target for malicious actors. Protecting the electric grid requires a strong regulatory framework and robust cybersecurity monitoring practices. In the United States, the Federal Energy Regulatory Commission (FERC) and the North American Electric Reliability Corporation (NERC) play key roles in safeguarding the power system against cyber risks.
Compliance with the NERC Critical Infrastructure Protection (NERC CIP) standards provides a baseline for mitigating security risk, but organizations should implement security technologies that help them streamline these processes.
Who are FERC and NERC?
The Federal Energy Regulatory Commission (FERC) is the governmental agency that oversees the power grid’s reliability. Since the Energy Policy Act of 2005 that granted FERC these powers, the rise of smart technologies across the energy industry expanded. This led to the Energy Independence and Security Act of 2007 (EISA) which led to FERC and the National Institute of Standards and Technology (NIST) to coordinate cybersecurity reliability standards that protect the industry.
However, to develop these reliability standards, FERC certified the North American Electric Reliability Corporation (NERC). Currently, NERC has thirteen published and enforceable Critical Infrastructure Protection (CIP) standards plus one more awaiting approval.
What are the NERC CIP requirements?
The cybersecurity Reliability Standards are broken out across nine documents, each detailing the different requirements and controls for compliance.
CIP-002: BES Cyber System Categorization
This CIP creates “bright-line” criteria for how to categorize BES Cyber Systems based on impact that an outage would cause. The publication separates BES Cyber Systems into three general categories:
- High Impact
- Medium Impact
- Low Impact
CIP-003-8: Security Management Controls
This publication, with its most recent iteration being enforceable in April 2026, requires Responsible Entities to create policies, procedures, and processes for high or medium impact BES Cyber Systems, including:
- Cyber security awareness: training delivered every 15 calendar months
- Physical security controls: protections for assets, locations within an asset containing low impact BES systems, and Cyber Assets
- Electronic access controls: controls that limit inbound and outbound electronic access for assets containing low impact BES Cyber Systems
- Cyber security incident response: identification, classification, and response to Cyber Security incidents, including establishing role and responsibilities for testing (every 36 months) and handling incidents, including updating Cyber Security Incident response plan within 180 days of a reportable incident
- Transient cyber asset and removable media malicious code risk mitigation: Plans for implementing, maintaining, and monitoring anti-virus, application allowlists, and other methods to detect malicious code
- Vendor electronic remote access security controls: processes for remote access to mitigate risks, including ways to determine and disable remote access and detect known or suspected malicious communications from vendor remote access
CIP-004-7: Personnel & Training
Every Responsible Entity needs to have one or more documented processes and provide evidence to demonstrate implementation of:
- Security awareness training
- Personnel risk assessments prior to granting authorized electronic or unescorted physical access
- Access management programs
- Access revocation programs
- Access management, including provisioning, authorizing, and terminating access
CIP-005-7: Electronic Security Perimeter(s)
To mitigate risks, Responsible Entities need to have controls for permitting known and controlled communications need documented processes and evidence of:
- Connection to network using a routable protocol protected by an Electronic Security Perimeter (ESP)
- Permitting and documenting the reasoning for necessary communications while denying all other communications
- Limiting network accessibility to management Interfaces
- Performing authentication when allowing remove access through dial-up connectivity
- Monitoring to detect known or suspected malicious communications
- Implementation of controls, like encryption or physical access restrictions, to protect data confidentiality and integrity
- Remote access management capabilities, multi-factor authentication and multiple methods for determining active vendor remote access
- Multiple methods for disabling active vendor remote access
- One or more methods to determine authenticated vendor-initiated remote access, terminating these remote connections, and controlling ability to reconnect
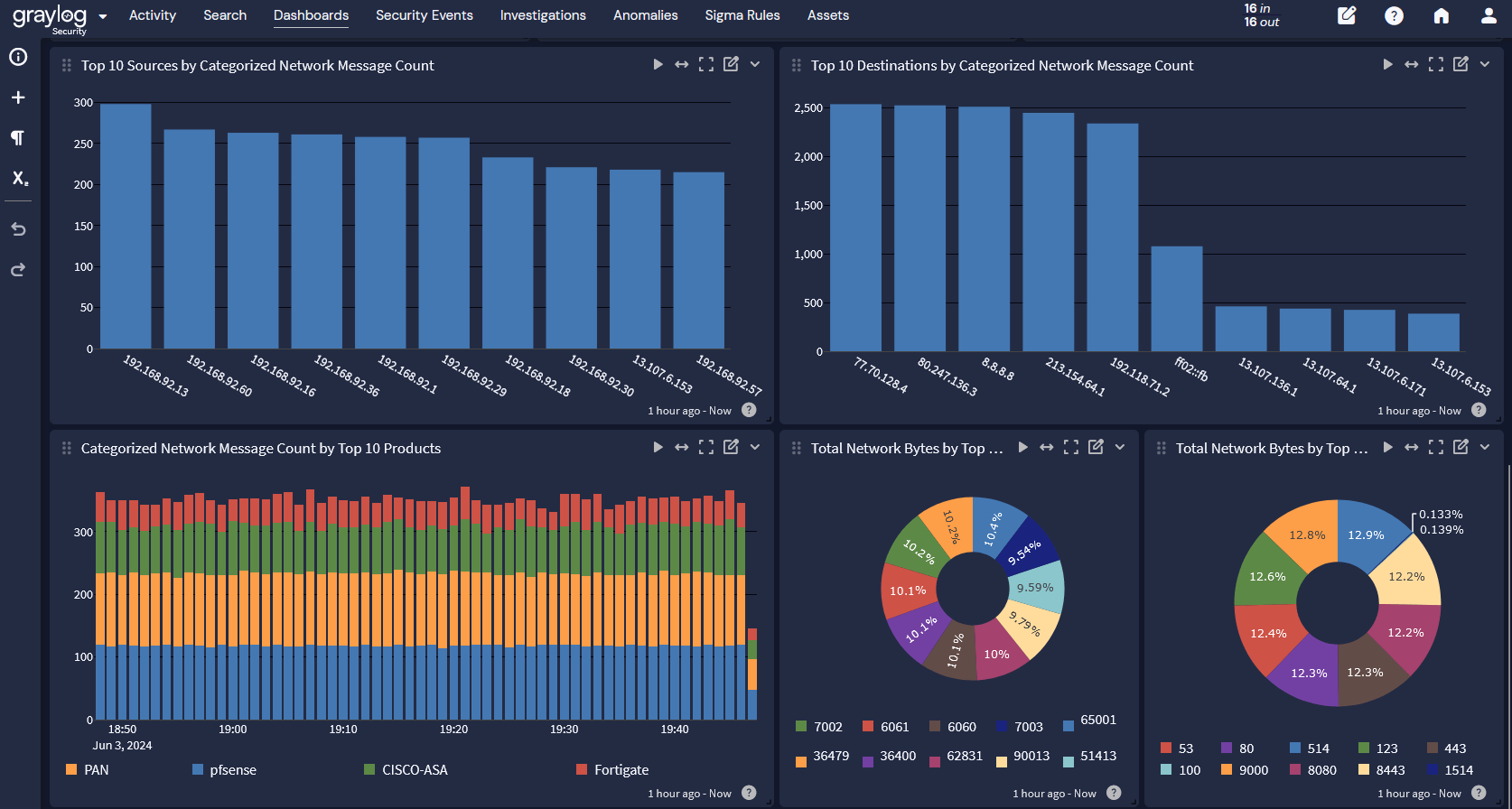
Most of these requirements fall under the umbrella of network security monitoring. For example, many organizations will implement tools like:
- Firewalls that allow or deny communications
- Intrusion detection system (IDS)/Intrusion prevention system (IPS) that monitor traffic and packets to either detect intrusions or proactively stop them
Once organizations can define baselines for normal network traffic, they can implement detections that alert their security teams to potential incidents.
CIP-006-6: Physical Security of BES Cyber Systems
To prove management of physical access to these systems, Responsible Entities need documented processes and evidence that include:
- Physical security plan with defined operation or procedural controls for restricting physical access
- Controls for managing authorized unescorted access
- Monitoring for unauthorized physical access
- Alarms or alerts for responding to detected unauthorized access
- Logs that must be retained for 90 days for managing entry of individuals authorized for unescorted physical access
- Visitor control program that includes continuous escort for visitors, logging visitors, and retaining visitor logs
- Maintenance and testing programs for the physical access control system
Many organizations use technologies to help manage physical security, like badges or smart alarms. By incorporating these technologies into the overarching cybersecurity monitoring, Responsible Entities can correlate activities across the physical and digital domains.
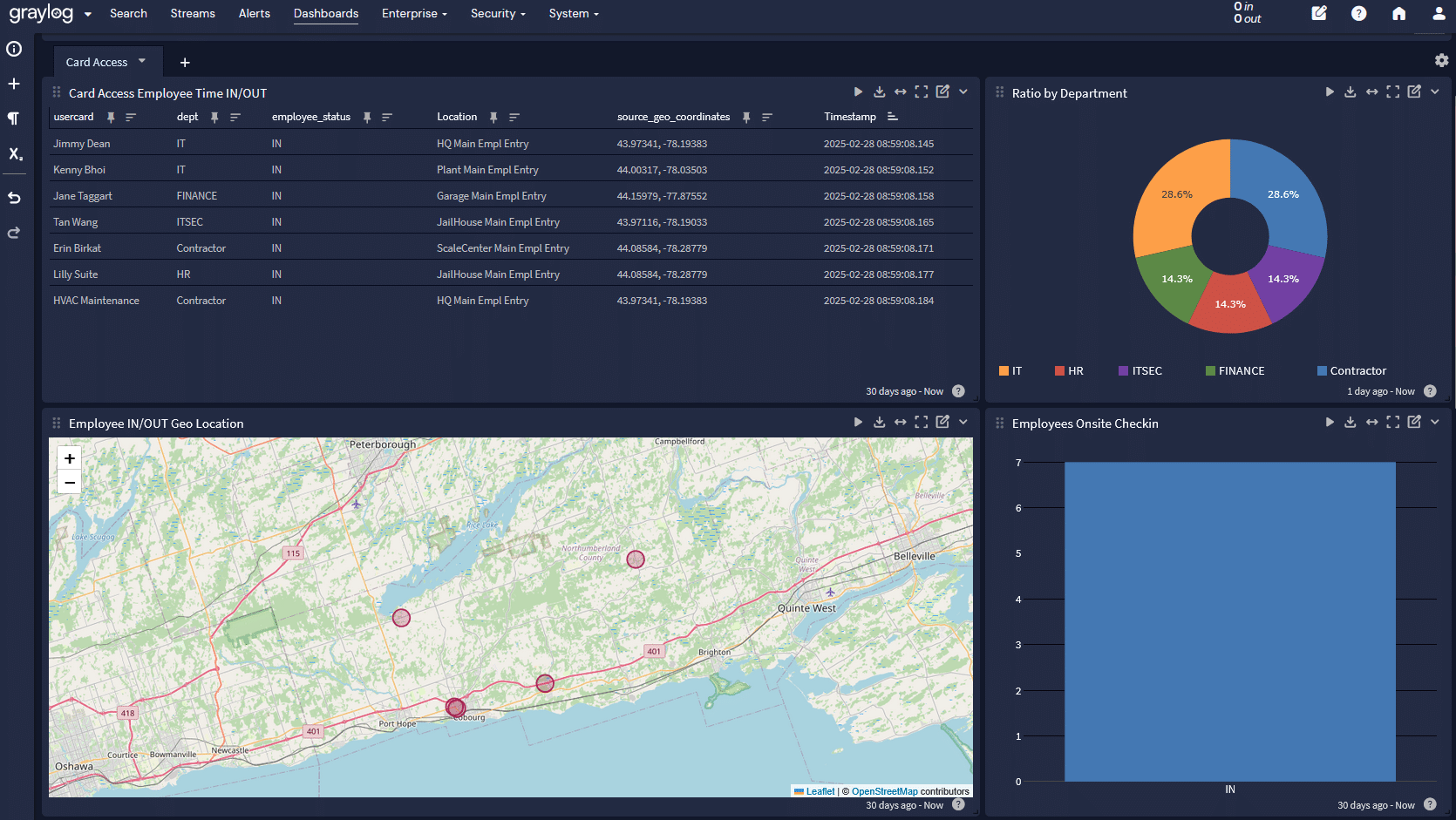
By tracking both physical access and digital access to BES Cyber Systems, Responsible Entities can improve their overarching security posture, especially given the interconnection between physical and digital access to systems.
CIP-007-6: System Security Management
To prove that they have the technical, operational, and procedural system security management capabilities, Responsible Entities need documented processes and evidence that include:
- System hardening: disabling or preventing unnecessary remote access, protection against physical input/output ports used for network connectivity, risk mitigation to prevent CPU or memory vulnerabilities
- Patch management process: evaluating security patch applicability at least once every 35 calendar days and tracking, evaluating, and installing security patches
- Malicious code prevention: methods for deterring, detecting, or preventing malicious code and mitigating the threat of detected malicious code
- Monitoring for security events: logging security events per system capabilities, generating security event alerts, retaining security event logs, and reviewing summaries or samplings of logged security events
- System access controls: authentication enforcement methods, identification and inventory of all known default or generic accounts, identification of people with authorized access to shared accounts, changing default passwords, technical or procedural controls for password-only authentication, including forced changes at least once every 15 calendar months, limiting the number of unsuccessful authentication attempts and generating
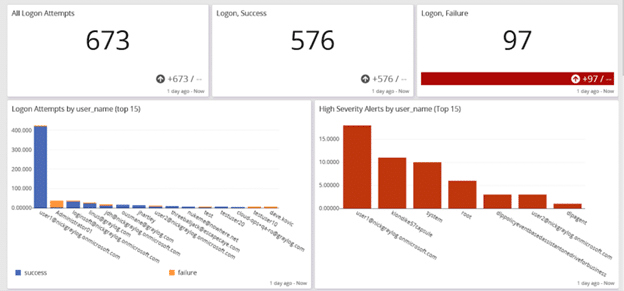
Having a robust threat detection and incident response (TDIR) solution enables Responsible Parties to leverage user and entity behavior analytics (UEBA) with the rest of their log data so they can handle security functions like:
- Privileged access management (PAM)
- Password policy compliance
- Abnormal privilege escalation
- Time spent accessing a resource
- Brute force attack detection
CIP-008-6: Incident Reporting and Response Planning
To mitigate risk to reliable operation, Responsible Entities need documented incident response plans and evidence that include:
- Processes for identifying, classifying, and responding to security incidents
- Roles and responsibility for the incident response groups or individuals
- Incident handling procedures
- Testing incident response plan at least once every 15 calendar months
- Retaining records for reportable and other security incidents
- Reviewing, updating, and communicating lessons learned, changes to the plan based on lessons learned, notifying people of changes
Security analytics enables Responsible Entities to enhance their incident detection and response capabilities. By building detections around MITRE ATT&CK tactics, techniques, and procedures (TTPs), security teams can connect the activities occurring in their environments with real-world activities to investigate an attacker’s path faster. Further, with high-fidelity Sigma rule detections aligned to the ATT&CK framework, Responsible Entities improve their incident response capabilities.
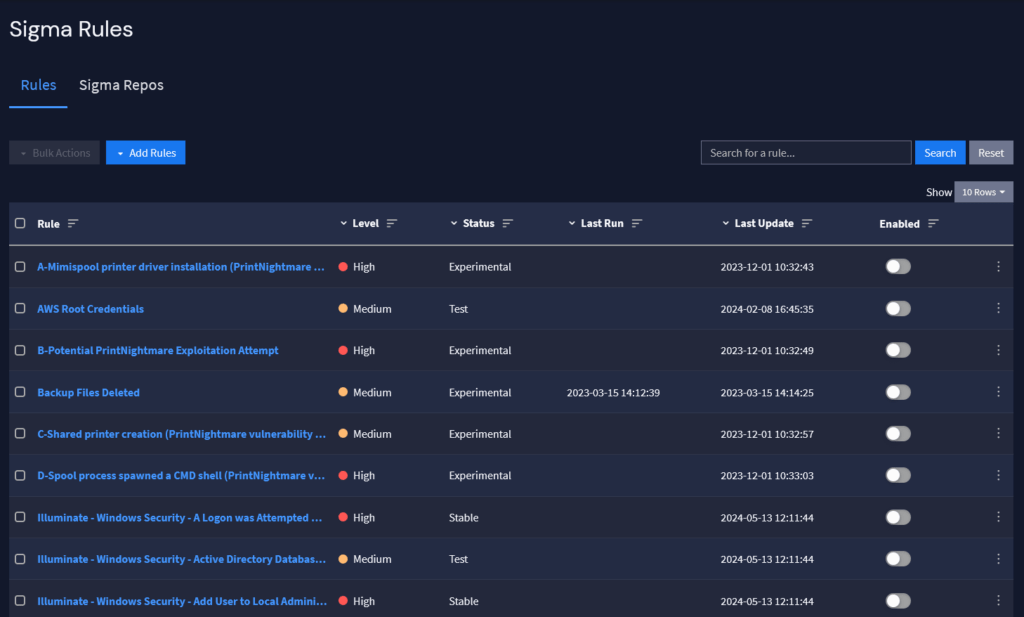
In the aftermath of an incident or incident response test, organizations need to develop reports that enable them to identify lessons learned. These include highlighting:
- Key findings
- Actions taken
- Impact on stakeholders
- Incident ID
- Incident summary that includes type, time, duration, and affected systems/data
To improve processes, Responsible Entities need to organize the different pieces of evidence into an incident response report that showcases the timeline of events.
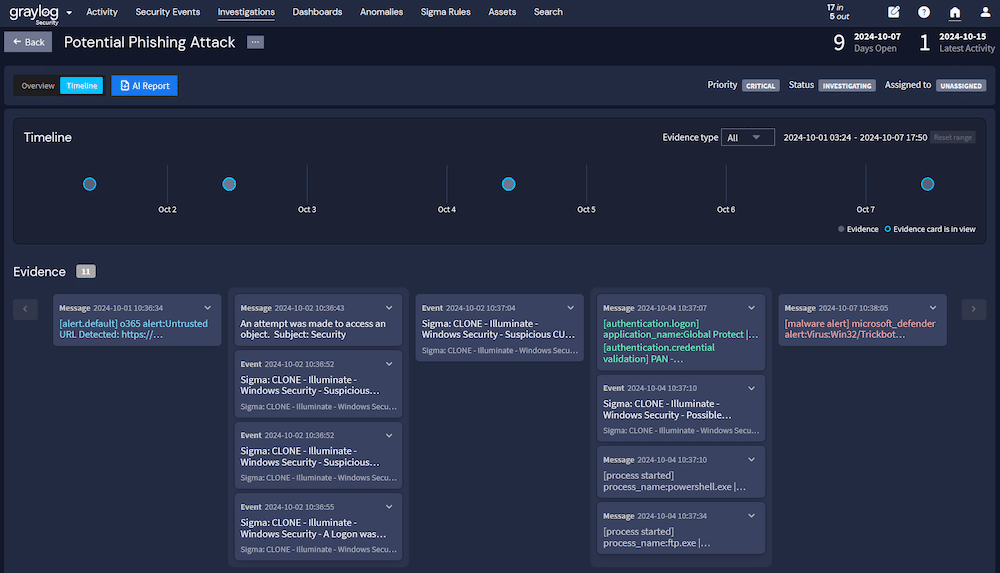
Further, they need to capture crucial information about the incident, including:
- Nature of threat
- Business impact
- Immediate actions taken
- When/how incident occurred
- Who/what was affected
- Overall scope
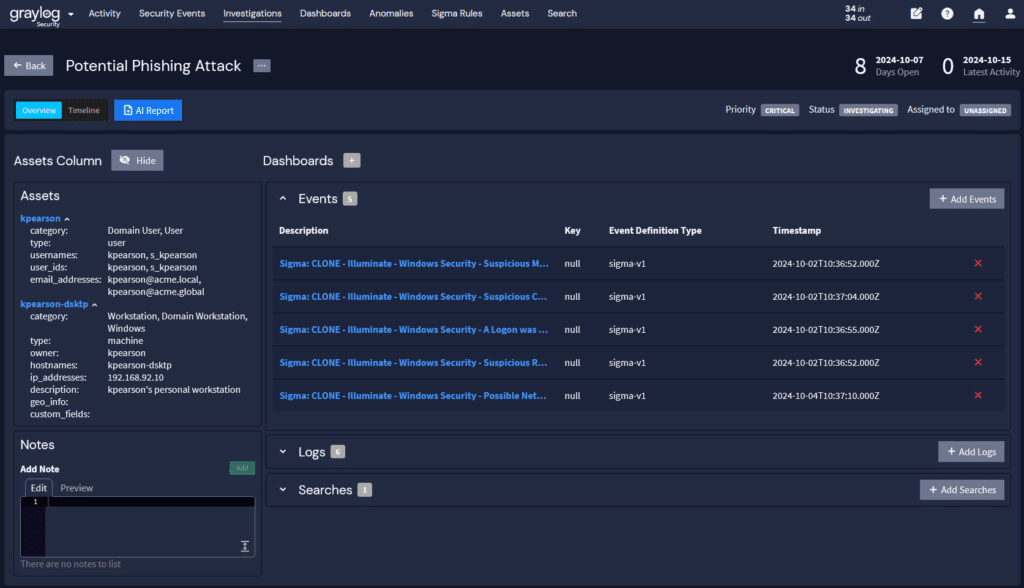
CIP-009-6: Recovery Plans for BES Cyber Systems
To support continued stability, operability, and reliability, Responsible Entities need documented recovery plans with processes and evidence for:
- Activation of recovery plan
- Responder roles and responsibilities
- Backup and storage of information required for recovery and verification of backups
- Testing recovery plan at least once every 15 calendar months
- Reviewing, updating, and communicating lessons learned, changes to the plan based on lessons learned, notifying people of changes
CIP-010-4: Configuration Change Management and Vulnerability Assessments
To prevent and detect unauthorized changes, Responsible Entities need documentation and evidence of configuration change management and vulnerability assessment that includes:
- Authorization of changes that can alter behavior of one or more cybersecurity controls
- Testing changes prior to deploying them in a production environment
- Verifying identity and integrity of operating systems, firmware, software, or software patches prior to installation
- Monitoring for unauthorized changes that can alter the behavior of one or more cybersecurity controls at least once every 35 calendar days, including at least one control for configurations affecting network accessibility, CPU and memory, installation, removal, or updates to operating systems, firmware, software, and cybersecurity patches, malicious code protection, security event logging or alerting, authentication methods, enabled or disabled account status
- Engaging in vulnerability assessment at least once every 15 calendar months
- Performing an active vulnerability assessment in a test environment and documenting the results at least once every 36 calendar months
- Performing vulnerability assessments for new systems prior to implementation
CIP-011-3: Information Protection
To prevent unauthorized access, Responsible Entities need documented information protection processes and evidence of:
- Methods for identifying, protecting, and securely handling BES Cyber System Information (BCSI)
- Methods for preventing the unauthorized retrieval of BCSI prior to system disposal
CIP-012-1: Communications between Control Centers
To protect the confidentiality, integrity, and availability assessment monitoring data transmitted between Control Centers, Responsible Entities need documented processes for and evidence of:
- Risk mitigation for unauthorized disclosure and modification or loss of availability of data
- Identification of risk mitigation methods
- Identification of where methods are implemented
- Assignment of responsibilities when different Responsible Entities own or operate Control Centers
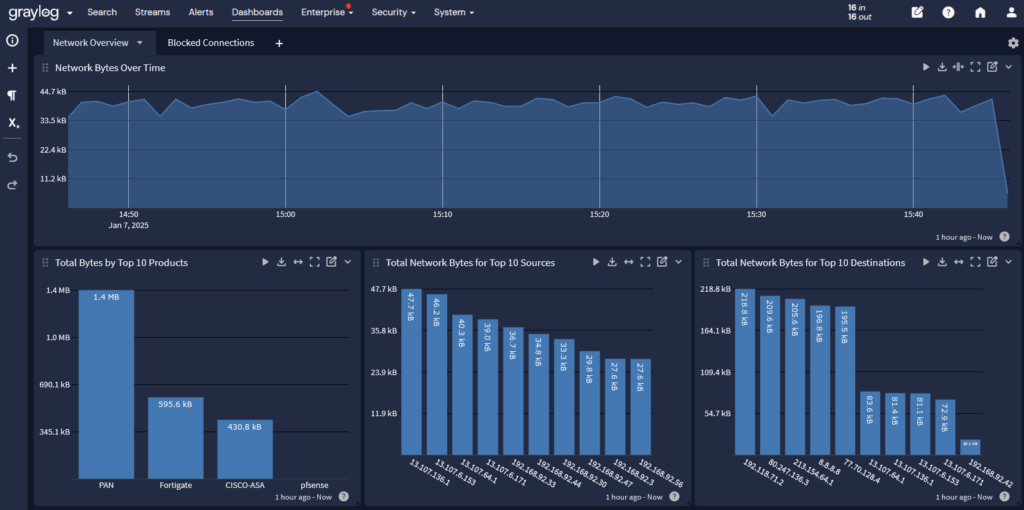
To mitigate data exfiltration risks, Responsible Parties need to aggregate, correlate, and analyze log data across:
- Network traffic logs
- Antivirus logs
- UEBA solutions
With visibility into abnormal data downloads, they can more effectively monitor communications between control centers.
CIP-013-2: Supply Chain Risk Management
To mitigate supply chain risks, Responsible Entities need documented security controls and evidence of:
- Procurement processes for identifying and assessing security risks related to installing vendor equipment and software and switching vendors
- Receiving notifications about vendor-identified incidents related to products or services
- Coordinating responses to vendor-identified incidents related to products or services
- Notifying vendors when no longer granting remote or onsite access
- Vendor disclosure of known vulnerabilities related to products or services
- Verifying software and patch integrity and authenticity
- Coordination controls for vendor-initiated remote access
- Review and obtain approval for the supply chain risk management plan
CIP-015-1: Internal Network Security Monitoring
While this standard is currently awaiting approval by the NERC Board of Trustees, Responsible Entities should consider preparing for publication and enforcement with documented processes and evidence of monitoring internal networks’ security, including the implementation of:
- Network data feeds using a risk-based rationale for monitoring network activity, including connections, devices, and network communications
- Detections for anomalous network activity
- Evaluating anomalous network activity
- Retaining internal network security monitoring data
- Protecting internal network security monitoring data
Graylog Security: Enabling the Energy Sector to Comply with NERC CIP
Using Graylog Security, you can rapidly mature your TDIR capabilities without the complexity and cost of traditional Security Information and Event Management (SIEM) technology. Graylog Security’s Illuminate bundles include detection rulesets so that you have content, like Sigma detections, enabling you to uplevel your security alert, incident response, and threat hunting capabilities with correlations to ATT&CK tactic, techniques, and procedures (TTPs).
By leveraging our cloud-native capabilities and out-of-the-box content, you gain immediate value from your logs. Our anomaly detection ML improves over time without manual tuning, adapting rapidly to new data sets, organizational priorities, and custom use cases so that you can automate key user and entity access monitoring.
With our intuitive user interface, you can rapidly investigate alerts. Our lightning-fast search capabilities enable you to search terabytes of data in milliseconds, reducing dwell times and shrinking investigations by hours, days, and weeks.
To learn how Graylog Security can help you implement robust threat detection and response, contact us today.



