Integrations that accelerate detection and response
Gartner identified security technology convergence as one of the key trends both in 2022 and 2023 as a necessity to remove complexity in the industry. Especially for Threat Detection and Incident Response (TDIR), simplification continues to resonate with cyber teams overwhelmed by too many tools and the continuous cutting and pasting from one tool to another.
According to Gartner, “Security technology convergence is accelerating, driven by the need to reduce complexity, reduce administration overhead and increase effectiveness. New platform approaches such as extended detection and response (XDR), security service edge (SSE) and cloud native application protection platforms (CNAPP) are accelerating the benefits of converged solutions.” Gartner has predicted that “Consolidation of security functions will lower total cost of ownership and improve operational efficiency in the long term, leading to better overall security.”
The best ways to remove complexity in your SOC are
- Identify opportunities for automation
- Streamline Logs
- Add Threat Intelligence to focus TDIR
AUTOMATION
Automation removes tedious repetitive tasks and eliminates opportunities for mistakes. A recent 2023 survey, indicated 75% of security leaders say cybersecurity automation is important, up from 68% in 2022. Teams are tackling automation in a variety of areas. The biggest rise was for alert triage to 30% compared to 18% in 2022. For vulnerability management, there was a 5% rise to 30%. Another common use case for automation in 2023 was phishing, adopted by 31% of respondents.
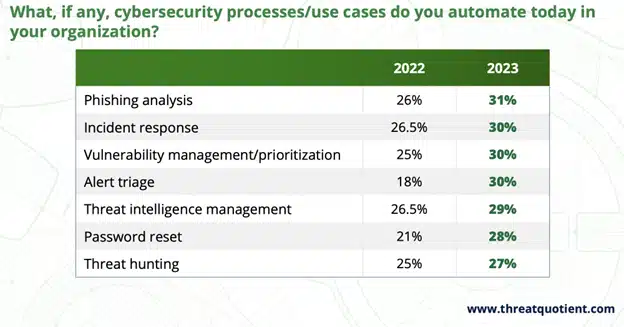
Choosing which will have the most impact on your organization may be challenging but globally all security organizations are investing in automation.
STREAMLINING LOGS
Collecting all the relevant data from various sources into a single, accessible platform like a SIEM (like Graylog) is the first step. First, one must break down silos and focus on the normalization of data from across the organization to provide a holistic view of the threat landscape. Logging strategy needs to be clearly defined to manage costs and ensure that there is clear and deep visibility to risk. For more on log management see recent blog on streamlining logs.
THREAT INTELLIGENCE
Another area where everyone can agree is that threat intelligence is important, globally, regions responded differently as to what has the biggest impact on analysts: people, process or technology. Australian respondents want more people, UK respondents want more training (process), and US respondents want smarter technology. Where to start?
TDIR is the primary function of SOC teams and it involves many moving parts including, multiple tools, threat intelligence, NDR, EDR, SIEM, SOAR, UEBA and now XDR in an ever expanding acronym nightmare. Integrations are necessary and valuable but streamlining operations is always a challenge. That is why Graylog, a leader in SIEM, Enterprise Log Management and API Security, together with SOC Prime, provider of the foremost platform for collective cyber defense, decided to do things differently. While SOC Prime has integration partnerships with a variety of SIEM vendors, they entered a technology partnership where Graylog will be packaging SOC Prime threat intelligence into off-the-shelf Illuminate curated content packs. This will simplify SOC operations for many who can’t afford additional security tools, or don’t have the skills or staff to integrate threat intelligence on their own.
Content has always been valuable for SOCs but has been reserved for more sophisticated SOCs that could write detection rules and alerts to eliminate noise and streamline detection. Graylog’s Illuminate content packs will speed threat detection and response, guided by the MITRE ATT&CK® framework. Graylog further amplifies this capability by blending SOC Prime’s intelligence with other data context, enhancing risk identification and investigative efficiency. Now available in beta, this collaboration promises to redefine the effectiveness and efficiency around how businesses identify and mitigate cyber threats.
Graylog and SOC Prime
A recent webinar demonstrated the initial integration and Andrii Bezverkhyi, CEO of SOC Prime, emphasized the collaborative benefit: “Our integration with Graylog’s platform transcends tool provisioning; we’re reshaping cybersecurity perspectives. Together, we enable security teams to swiftly tackle the most critical threats, redefining organizational defense strategies.”
Unlike other partnerships, this is a technical integration of SOC Prime capabilities into the Graylog platform. Every Graylog Security customer will have pre-curated SOC Prime content available to them via Graylog’s Illuminate packs at no additional cost or overhead. This will save both time and money for security staff that are on the front lines. Integration of SOC Prime’s technology into Graylog’s guided investigations is in beta and expected to be generally available in May. Graylog expects that enterprises seeking a SIEM that can handle the challenges of TDIR will migrate to platforms that incorporate TDIR best practices and streamline the analyst experience.
Robert Rea, Graylog’s CTO, added: “This is about making actionable intelligence a reality for every organization, drastically cutting down the time from threat detection to response. Curating SOC Prime content into Graylog alerts enables security teams to prioritize their work in a way that will make a real difference in their security posture.”
For more information about how the Graylog is transforming threat detection and response with more threat intelligence, please visit Graylog Security.
Checkout the on-demand webinar here from the Graylog and SOC Prime.



