Back before live security video feeds in homes, people would walk around at night checking to make sure they locked every window and door. They took these precautions because they knew that a single open lock gave burglars an opportunity to steal from them.
For organizations, vulnerability management programs are a way to lock the doors against cybercriminals. Security vulnerabilities are weaknesses in processes and technologies that attackers can use to gain unauthorized access to systems, networks, and data. For example, the 2025 Data Breaches Investigations Report found that vulnerability exploitation was present in 20% of data breach, a 34% year-over-year increase.
As attackers increasingly focus on these security weaknesses, organizations need to have robust vulnerability management programs as a key part of their security risk management strategy.
What is a vulnerability management program?
A vulnerability management program creates standardized processes for proactively identifying, classifying, remediating, and mitigating vulnerabilities across an organization’s systems, networks, applications, and devices. The vulnerability management program may start with vulnerability scanning, but it should also include a comprehensive cycle of activities that remediate risks arising from the identified security vulnerabilities.
The key elements of a vulnerability management program include:
- Vulnerability identification: Using tools and threat intelligence to spot potential weaknesses.
- Vulnerability assessment: Evaluating the severity and potential impact of identified vulnerabilities to help prioritize next steps.
- Remediation and Mitigation: Implementing measures to fix or lessen the impact of vulnerabilities.
- Continuous monitoring and reporting: Ensuring ongoing assessment and transparency of security posture.
What Is the Vulnerability Management Lifecycle?
The vulnerability management life cycle is a continuous process that encompasses the following key phases:
- Discovery: Scanning systems to identify existing vulnerabilities within the digital infrastructure.
- Asset prioritization: Focusing on high-impact vulnerabilities and vulnerabilities affecting the assets required to maintain business operations.
- Assessment: Classifying and prioritizing remediation efforts based on the potential impact that identified vulnerabilities could have on the organization.
- Remediation: Mitigating risks by applying security patches or implementing a compensating control when the manufacturer has not provided a security update.
- Verification and monitoring: Confirming that remediation efforts addressed the vulnerability’s risk and ensuring that protective measures function as intended.
- Reporting: Communicating vulnerability management trends over time to validate processes and identify areas of improvement.
What Are the Differences Between a Vulnerability, a Risk, and a Threat?
Although the three terms are related, they each have a unique definition:
- Vulnerability: weakness in an information system, system security procedures, internal controls, or implementation that a threat source can exploit or trigger.
- Risk: a measure of the extent to which an entity is threatened by a potential circumstance or event, and typically a function of adverse impacts if the event occurs and the likelihood that the event will occur.
- Threat: a circumstance or event that can have a potential, adverse impact on operations, assets, individuals, or other organizations through unauthorized access to a system that correlates to a service outage or data destruction, disclosure, or modification.
Essentially, a vulnerability poses a risk when threat actors can use it to further their objectives, like stealing data or deploying ransomware.
What is the difference between Vulnerability Management and a Vulnerability Assessment?
A vulnerability assessment is typically an activity that is part of the organization’s larger vulnerability management practices. They differ in four ways:
- Purpose: Vulnerability management is integral to the organization’s long-term security strategy while a vulnerability assessment provides a snapshot of current vulnerabilities.
- Scope: Vulnerability management is a process across the vulnerability lifecycle while a vulnerability assessment is a single review.
- Frequency: Vulnerability management is a continuous process while a vulnerability assessment is a point-in-time review.
- Components: Vulnerability management includes identification, tracking, and remediation while a vulnerability assessment is only the identification step.
What Is the Difference Between Known and Unknown Vulnerabilities?
The term unknown vulnerabilities is a bit of a misnomer since someone, somewhere needs to know that a vulnerability exists for it to matter.
Known vulnerabilities are defined as publicly disclosed and published flaws, typically found in databases like the Common Vulnerability Enumeration (CVE) list or the Known Exploited Vulnerability (KEV) list.
Unknown vulnerabilities are really previously unknown vulnerabilities that researchers or vendors have not identified or documented, meaning no patch exists yet. Often, attackers will identify these vulnerabilities and the initial discovery occurs when threat actors exploit them.
Why Is Creating a Vulnerability Management Program a Challenge?
Many organizations struggle to implement a vulnerability management program because they need to create a well-defined framework that allows for replication.
Difficulty Gaining Executive Leadership Support
Senior leadership can view the vulnerability management program as a cost center since it acts as a proactive security control. If no data breach occurs, then the leadership can feel like it has no way to quantify the value. However, the vulnerability management program requires executive buy-in for allocating budget, approving policies, and leaders to run it.
Difficulty Assessing Risk
Vulnerability management requires understanding the organization’s attack surface and the risks that assets connected to the public internet pose. However, most of the approaches for understanding vulnerability risk fail to consider the IT environment and context. For example, the Common Vulnerability Scoring System (CVSS) helps categorize vulnerabilities by severity, likelihood of exploitation, and potential impact. Organizations need risk scores that provide context and understand the asset’s criticality to business operations.
Inability to Identify All Assets
Many organizations struggle with IT asset management because they lack a way to identify all cyber assets. Unmanaged devices, like employee-owned smartphones, may have vulnerabilities that pose a risk to the organization. Failure to identify all digital assets can lead to oversights during scanning and assessment processes.
Lack of Policies and Processes
A vulnerability management program should have repeatable, consistent steps and outcomes. However, this requires having a framework that prioritizes vulnerabilities and includes structured remediation steps. Often, organizations have time-consuming manual processes that lead to errors.
Inability to Prioritize Vulnerabilities and Remediation
The difficulties identifying assets and assessing risk combined with a lack of policies and processes typically create the larger issue that organizations have no way to prioritize their remediation activities. Without knowing what vulnerabilities to patch or remediate first, they try to work on everything at the same time which becomes overwhelming.
Difficulty Collaborating Across Teams
Vulnerability management often requires cross-functional collaboration. The vulnerability management team identifies the security weaknesses. The devops team works on the patch. The security team might have to implement a compensating control. The patch management team applies the patch across the affected assets. When the teams have no single location for storing information about vulnerabilities or their responses, the processes become overwhelming and time-consuming.
Graylog: Asset Risk Scores with Asset Prioritization
With Graylog Security, organizations can classify a machine’s or user asset’s importance to provide context that helps drive our asset risk scores. By creating categories, you can group and sort assets across different priorities, including low, medium, high, and critical.
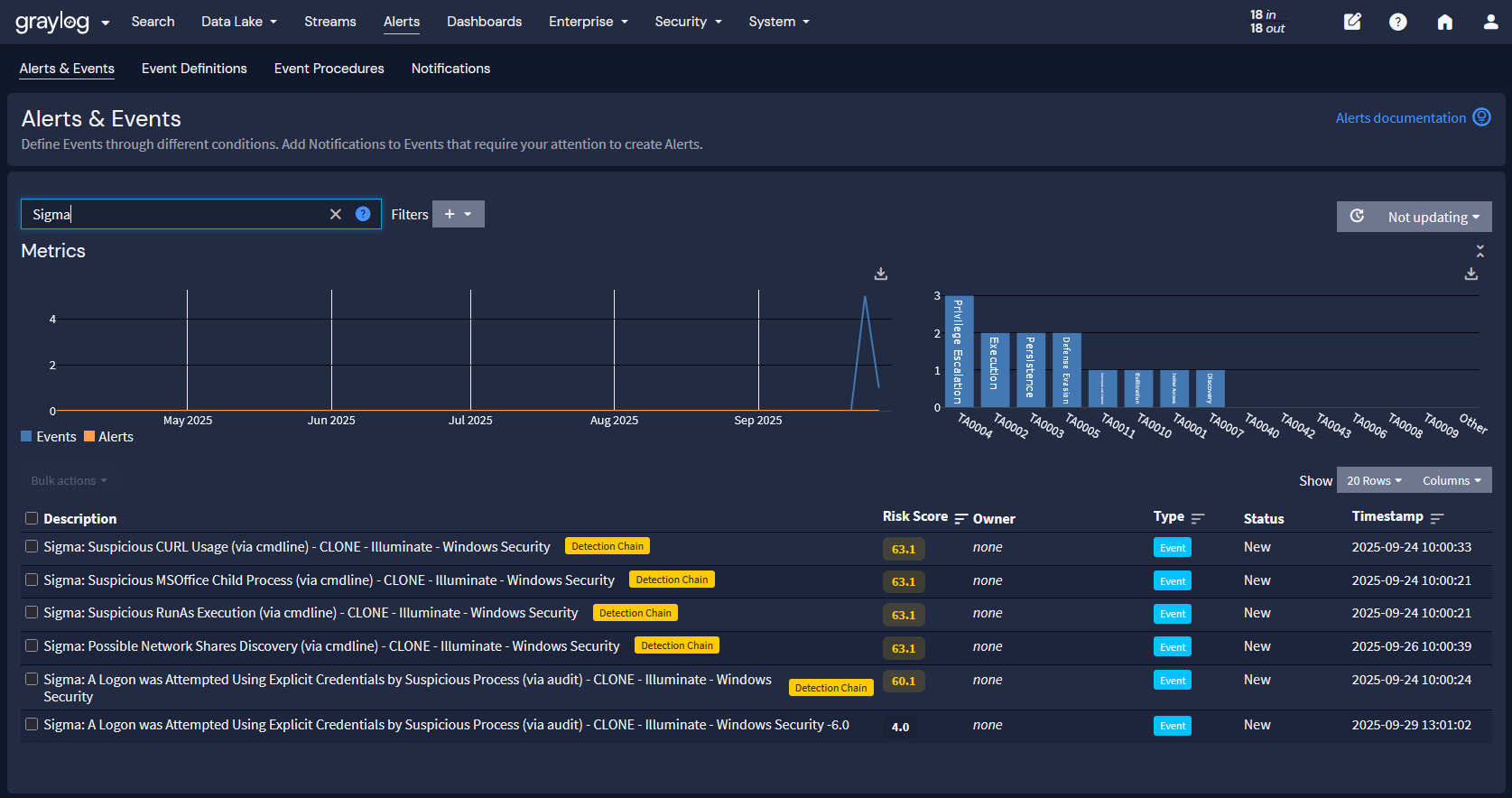
Meanwhile, our asset risk scores help your security team focus on the security events impacting assets that have vulnerabilities associated with them. Our asset risk scores combine the individual event risk score with other factors, including log data source, asset priority, and asset vulnerabilities so your security team can incorporate these insights into their response triage processes.
Built on the Graylog Platform, Graylog Security gives you the features and functionality of a SIEM while eliminating the complexity and reducing costs. With our easy to deploy and use solution, you get the combined power of centralized log management, data enrichment and normalization, correlation, threat detection, incident investigation, anomaly detection, and reporting.
With Graylog prebuilt content, you don’t have to worry about choosing the server log data you want because we do it for you. Graylog Illuminate content packs automate the visualization, management, and correlation processes for you.
To see how Graylog can help you improve your security program and help you manage APTs more effectively, contact us today.



