Everything that makes employees’ lives easier, makes yours harder. Detecting insider threats — both employees and cybercriminals pretending to be employees — has never been more difficult or more important. The cloud technologies that make everyone else more efficient make security less efficient. They’re noisy. They send a lot of alerts. You’re tired. You’re overworked. You’re overloaded.
Graylog will help you sleep better at night, but you won’t be as exhausted because our AI/ML anomaly detection metrics give you the high-fidelity alerts necessary to mitigate insider threat risks.
Getting to “normal”
We get it. When you have a lot of remote employees all accessing cloud resources, everyone is more productive. Unfortunately for security teams, they become less productive because it’s hard to figure out what activity is “normal.” The more people share documents and download data, the harder it is to keep track of whether they should be doing these things.
Even though the Cheshire cat might argue “we’re all mad here,” there is such a thing as normal. For example, cloud application monitoring requires thousands of attributes, including:
- CPU
- Latency
- Memory
- Throughput
Since your applications alone generate this much noise, getting a sense of what normal is can be overwhelming.
Graylog brings together all the information you need from various data sources – homegrown, customized COTS, and legacy applications — so you can get the Big Picture view. Set baselines that define “normal” behavior so that you don’t go mad trying to secure your environments.
Find the diamond in the rough
Everyone is working from everywhere. Old role-based access controls don’t work in cloud-based environments. Today, the “share with a link” button and chat platforms are now your mortal enemy. You don’t know when people share information, how they share it, or where they share it.
Your logs are like a diamond cavern. You’ve got a lot of potential in there, but it’s hard to figure out the difference between the diamond and the quartz. Anomaly detection metrics help you sort out the patterns to detect an incident. They can help you sort out the difference between:
- A forgotten password and brute force attack
- A software problem or an exploited vulnerability
- A network issue or Distributed Denial of Service (DDoS) attack
Just like grains of sand polish diamonds to prove their quality, granular visibility using various attributes provide quality, high-fidelity alerts. After learning your normal, Graylog’s anomaly detection does all the polishing to give you the final diamond. Our machine learning model’s pre-built learning scenarios get you started immediately.
Graylog is a cost-effective way to polish your alerts by collecting, aggregating, and correlating more information from more data sources so you can respond faster.
Get the “stretch-fit” security solution
Just like a teenager, your company and its digital footprint keep growing. And just like the parents of a teen, you’re tired of spending money on a new security wardrobe every year. You don’t want to — or can’t — spend the money on an expensive tool. You need something that fits your team now and where they’ll be in another few years.
Graylog is the “stretch-fit” solution that gives you what you need now and grows along with you. We scale with you, including when you need to expand your computing or your application stack. Our AI/ML adapts without your team needing to fine-tune any tools, ensuring that you have the right fit every time.
Graylog Anomaly Detection: OUR DATA ANALYTICS. YOUR RELIABLE ALERTS
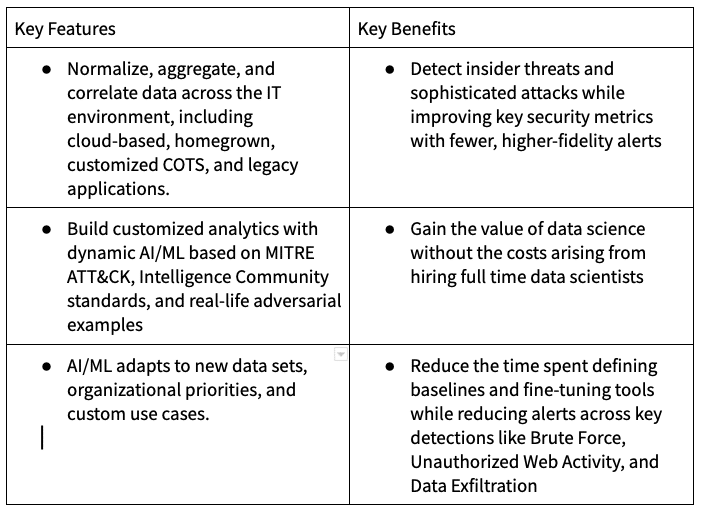
Graylog’s powerful, flexible, and seamless centralized log management solution runs Artificial Intelligence / Machine Learning (AI/ML) that identifies deviations from “normal” behavior for users and entities (UEBA). With our anomaly detection algorithms, you can create high-fidelity alerts by reducing false positives. Including UEBA into security information and event system mitigates risks caused by Insider Threats and credential-based attacks, even when malicious actors try to evade detection. Security teams benefit from our anomaly detectors with reduced alert fatigue for a proactive security posture that reduces risk, all in an easy-to-use solution that requires no specialized training.
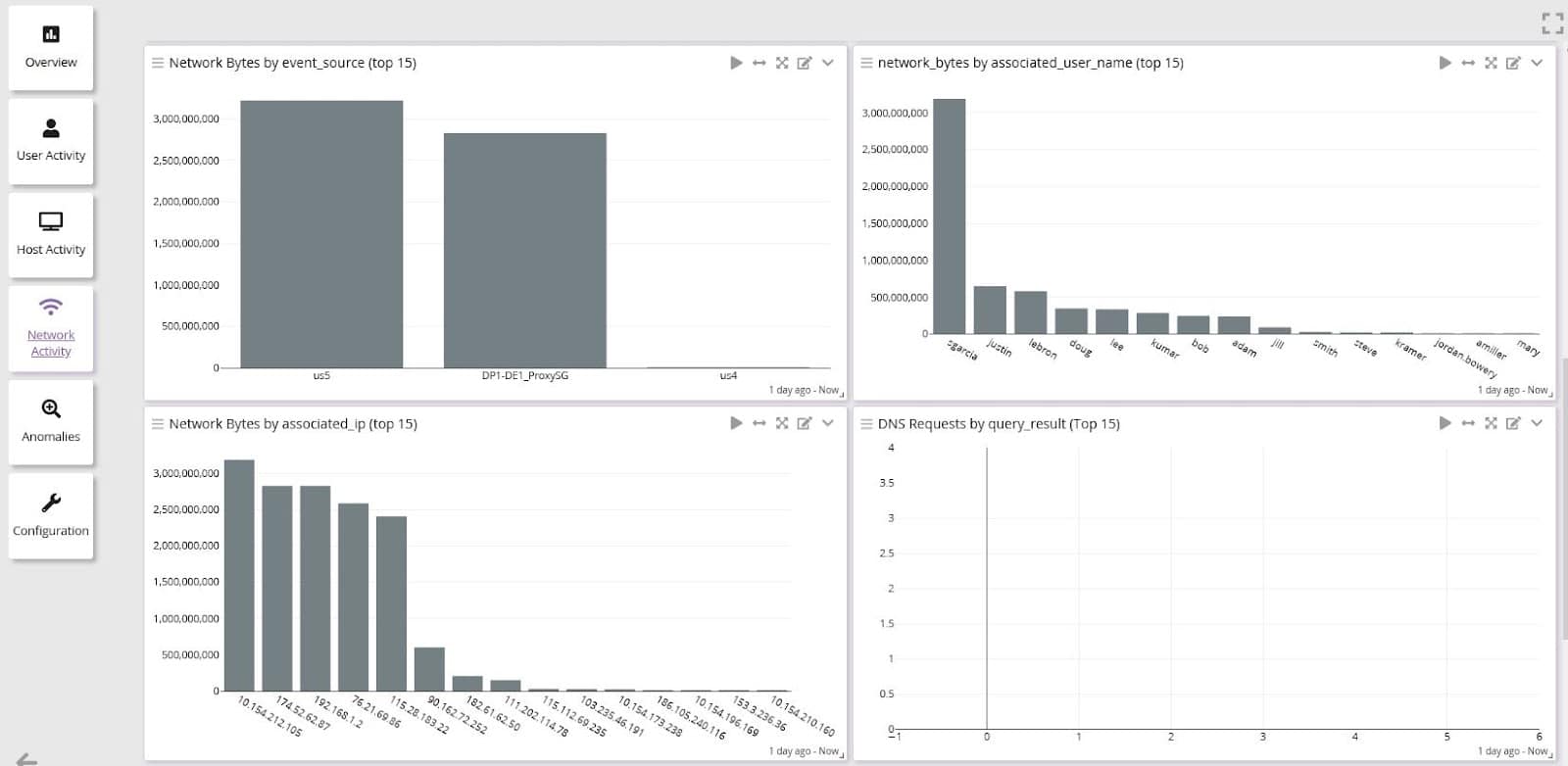
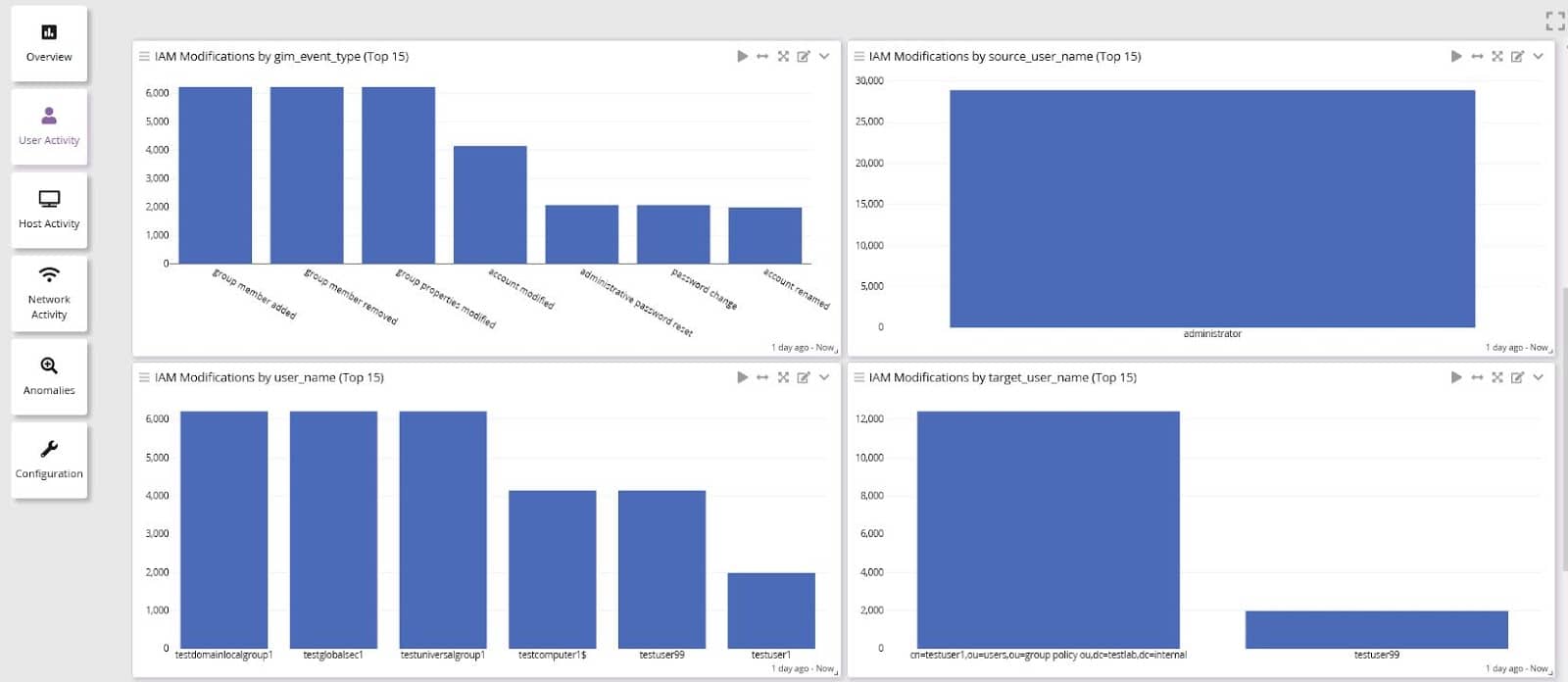
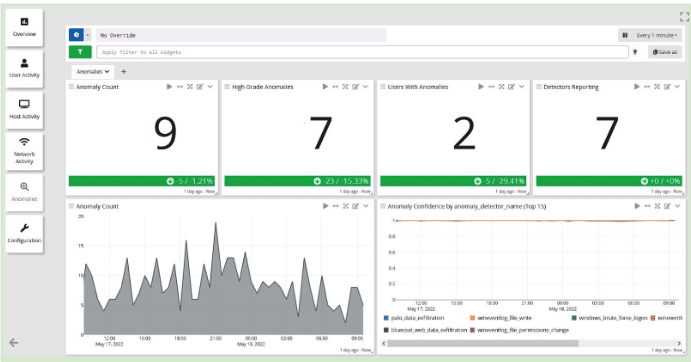
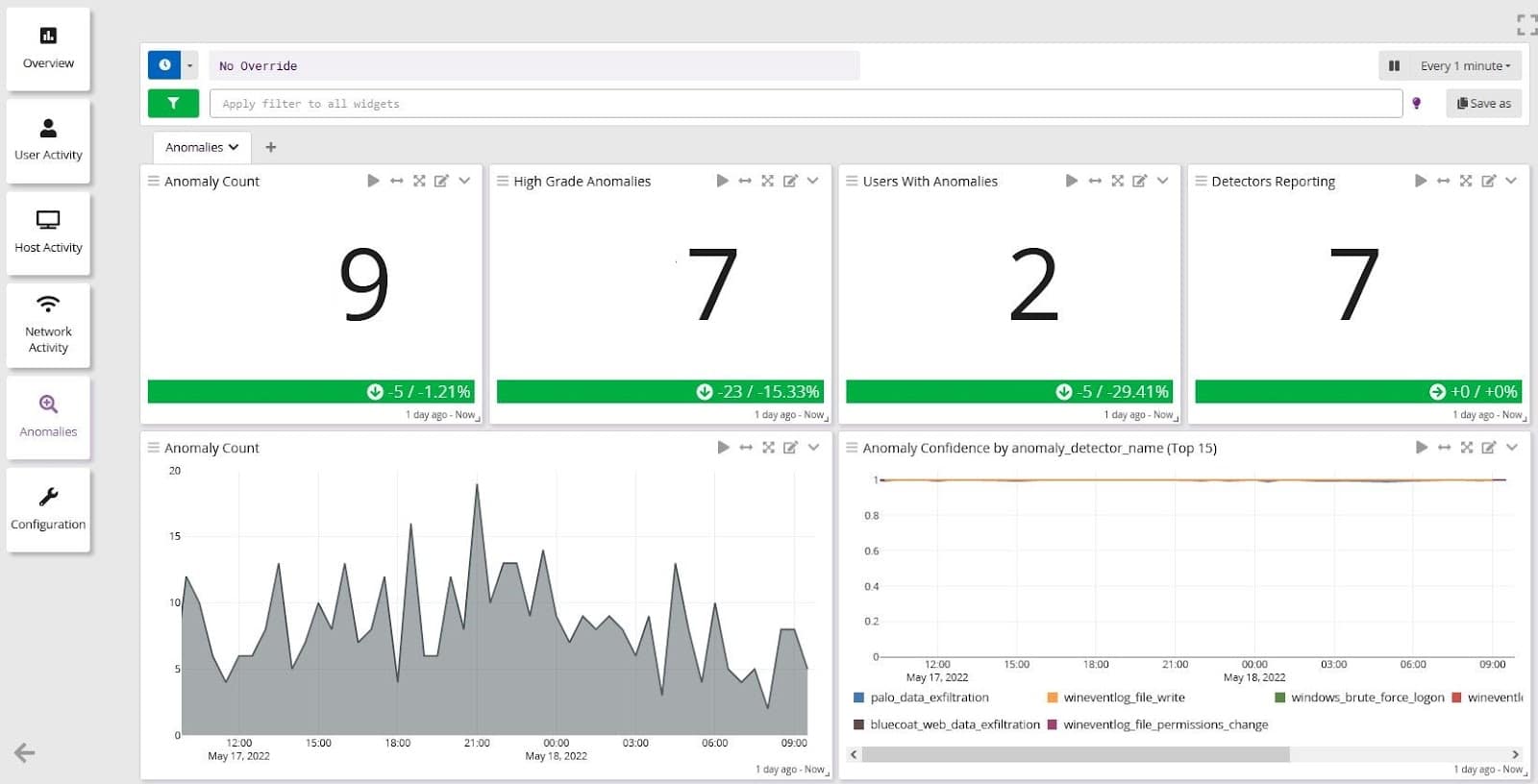
Customers with Graylog Enterprise for Security can get started quickly by using their current data with pre-built dashboards and scenarios, reducing the need for highly-skilled team members.