It’s time again for another meeting with senior leadership. You know that they will ask you the hard questions, like “how do you know that your detection and response times are ‘good enough’?” You think you’re doing a good job securing the organization. You haven’t had a security incident yet.
At the same time, you also know that you have no way to prove your approach to security is working. You’re reading your threat intelligence feeds. You’re looking for Indicators of Compromise (IoC) when reports indicate a potential risk from technology in your stack. Still, you don’t have the time to engage in proactive threat hunting daily. You can’t tell if you’re missing something, but you know that what you’re doing seems to be working.
You think.
Now you’re on a mission to adopt security analytics to help you make data-driven decisions. When you’re just getting started, you need to build your security analytics use cases so that you can evaluate tools and more rapidly adopt them.
What are the benefits of security analytics?
Security analytics tools collect, aggregate, and use algorithms to analyze security data so you can effectively monitor security and detect threats. They can ingest data from security tools across:
- Network traffic
- Endpoint security
- User and entity behavior
- Identity and access management
- Cloud resources
- Threat intelligence
- Applications
Security analytics tools bring in the context necessary to correlate events happening across your environment, ones that would otherwise remain disconnected.
Some of the benefits include:
- Threat intelligence usage: prioritize activities with contextual business risk
- Anomaly detection: combine user behavior and network traffic data for abnormal activities
- High fidelity alerts: reduce false positives and alert fatigue
- Forensic incident investigation: trace threats back to the compromised source
- Compliance reporting: prove continuous monitoring activities with documentation
Basic Security Analytics Use Cases
Your security analytics give you the ability to make data-driven decisions. To do this effectively, you need to know what data you want and how you plan to use it.
No two organizations are the same because their technology stacks, user profiles, and devices are different. While organizations may have similar controls, they implement and enforce them differently.
As you start researching or implementing a security analytics tool, you need to consider the basic use cases. At a high level, you want to consider:
- Network traffic analysis
- User behavior analytics
- Threat detection
- Data exfiltration
- Insider threat detection
- Incident investigation
You’re probably asking yourself right now: but what does that look like in practice?
Security Hygiene
Monitoring security hygiene with analytics can help you gain visibility into your company’s overall posture.
Under this use case, you want to aggregate data about:
- Password strength
- User location
- Endpoint security, like malware infections or anti-virus solution updates
- Threat intelligence around risky geographic regions or malware variants
Security Operations – Detection
If you’re the person receiving alerts, you’re probably suffering from alert fatigue. Since security analytics correlate and analyze data from across your environment, they allow you to build high-fidelity alerts so that you spend less time reviewing and chasing down false positives.
With more cloud resources, brute force attacks are more prevalent because user access has become the perimeter. However, it’s often difficult to determine whether a password reset is part of a brute force attack or a forgetful employee. You can create a more detailed alert to route the issue to the correct person using security analytics.
Under this use case, you could aggregate data about:
- Cloud resources
- User access
- User behavior
- IP address
- Failed login attempts
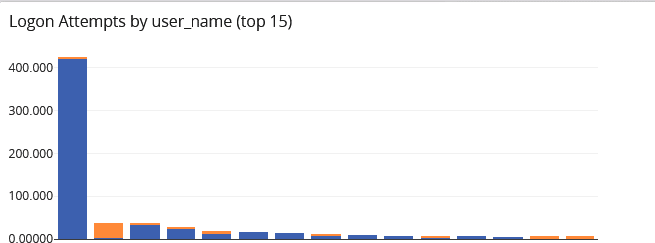
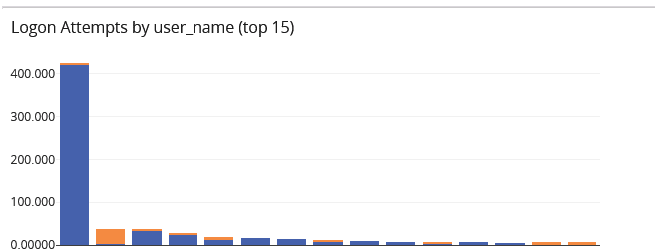
Threat Hunting/Investigation
Threat hunting and investigation capabilities go hand-in-hand. They follow similar processes but with different purposes. Investigations are a reactive process. You’ve received an alert – a high fidelity one now that you’re using security analytics – and need to investigate it.
At the same time, you want to try to move your security program from reactive to proactive, which means taking an “assumed breach” approach. Under this approach, you go threat hunting, which is investigating based on known cybercriminal attack methodologies before receiving an alert.
Under this use case, you could aggregate data that includes:
- Threat intelligence
- IP addresses
- Endpoint security posture
- Network traffic
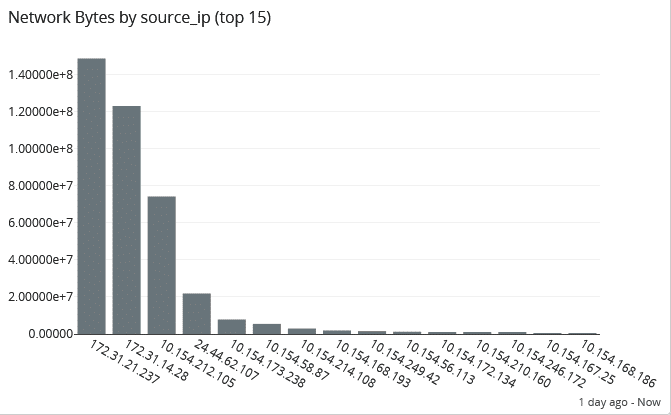
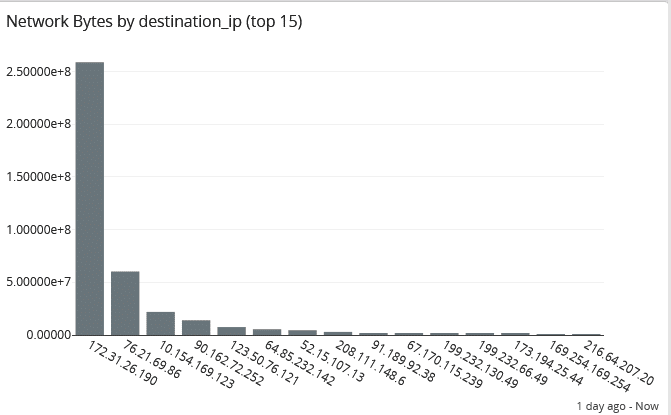
Forensics
If you do experience a security incident, you need to engage in forensic analysis. When you have a security analytics tool, you’re continuously storing and archiving the event log data that documents activities.
For example, you need information to help you determine whether data was downloaded or changed during the incident. You also need information to help you determine whether those downloads were abnormal or if the downloads occurred in a risky geographic region.
Under this use case, you could aggregate data about:
- User access to data
- Timing of access to data
- Geographic location accessing data
- Network packet data
- Threat intelligence
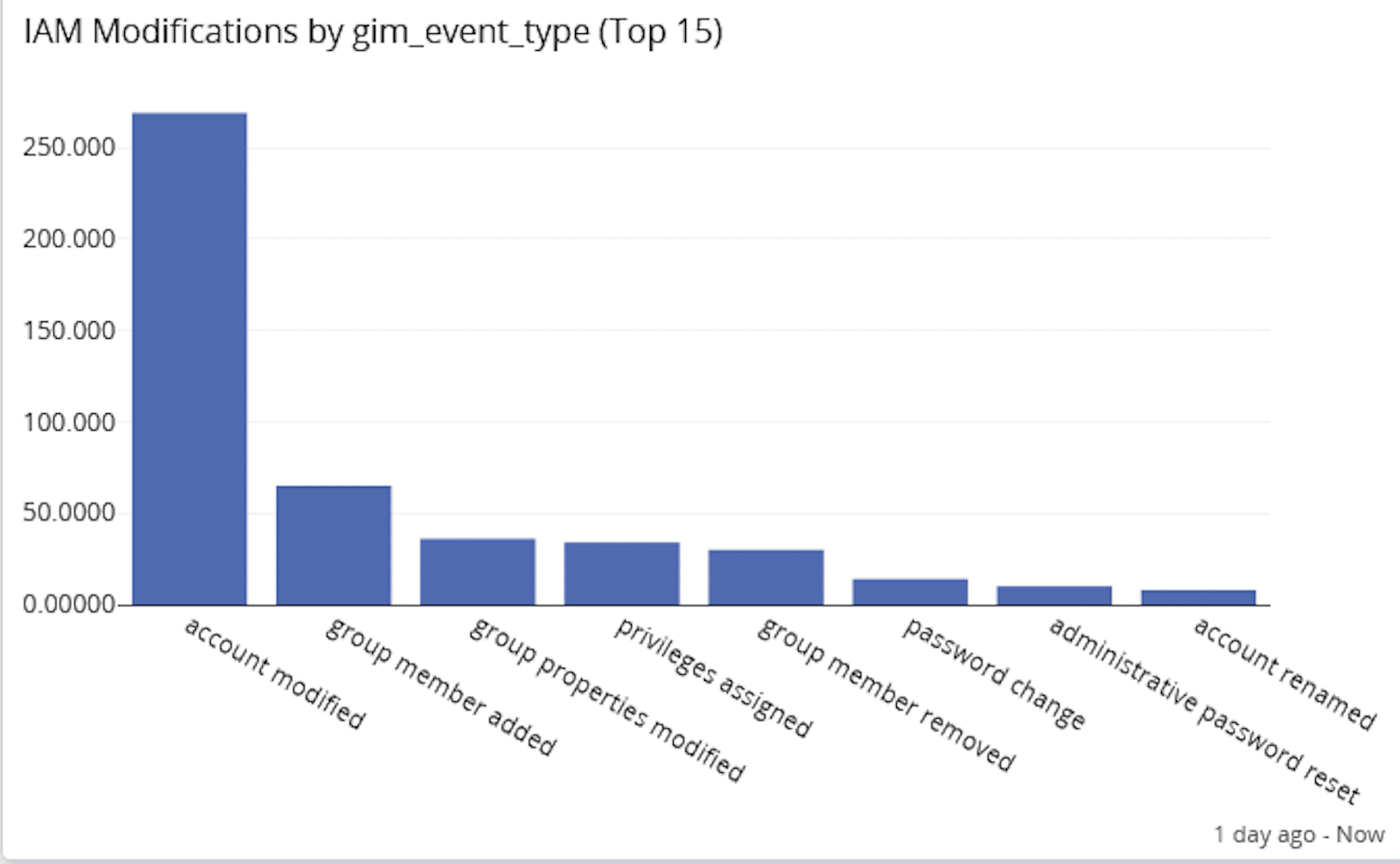
- IAM modifications

Operations
You can also use security analytics to route issues more rapidly. Your IT operations team often gets alerts that can be either a server glitch or a Distributed Denial of Service attack because they might impact an application the same way.
Under this use case, you could aggregate data that includes:
- Network metadata
- Firewall logs
- Security logs
- Intrusion Detection System (IDS)/Intrusion Prevention System (IPS) data
DevOps
Your DevOps team might be using code analysis software to help secure applications, but you still need to monitor security across development and production environments. An insecure web application run in a test environment will generate log data that you can use to help uplevel your Secure Software Development Lifecycle (SSDLC).
Under this use case, you could aggregate data that includes:
- Authorization failures
- Authorization successes
- Input validation issues
- Continuous integration (CI) server logs
- Network logs
- Data activity information
Compliance
To prove that you’re managing your security effectively, you must document all activities to pass your audits. The good news is that security analytics can help here, as well. Security analytics tools provide dashboards and visualizations that give you the documentation necessary to meet these requirements.
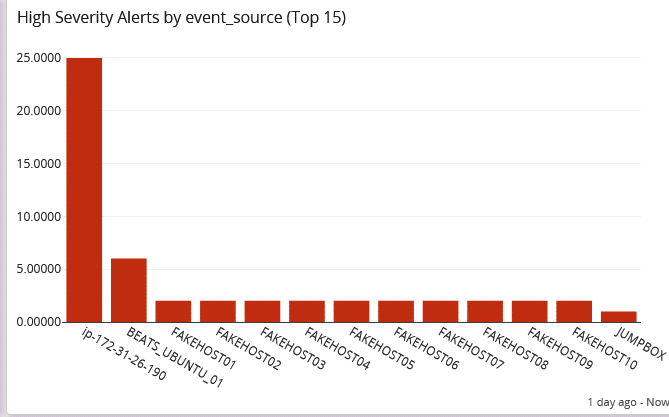
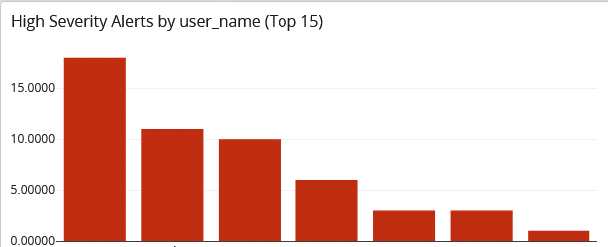
Under this use case, you could aggregate data and provide visualizations that show:
- High severity alerts by source
- High severity of alerts by alert type
- High severity of alerts by user
- High severity alerts by product

Graylog: Centralized Log Management for Security
Graylog’s centralized log management solution lets you level up your security by providing the security visibility you need. Our lightning-fast solution and parameterized searching make it easy to automate investigations to engage in threat hunting activities.
You need the right tools that help you secure your environment, collaborate with other teams, and communicate your outcomes. Graylog’s centralized log management solution is the “extra set of hands” you need without requiring specialized training for a new security tool. When you know your security analytics use cases, you can build them directly in our centralized log management solution for all the visibility, ease, and documentation necessary for a more robust security posture.