According to reporting by several cybersecurity publications the 3CX Desktop Application has been exploited in a supply chain attack. The 3CX client is a popular VOIP and messaging application used by over 600,000 companies.
From the article on Bleeping computer
This supply chain attack, dubbed ‘SmoothOperator’ by SentinelOne, starts when the MSI installer is downloaded from 3CX’s website or an update is pushed to an already installed desktop application.
“The malicious activity includes beaconing to actor-controlled infrastructure, deployment of second-stage payloads, and, in a small number of cases, hands-on-keyboard activity,” CrowdStrike’s threat intel team said.
This new malware is capable of harvesting system info and stealing data and stored credentials from Chrome, Edge, Brave, and Firefox user profiles.
Monitoring for IOCs in Graylog
Due to the fact that this malware is often seen beaconing via DNS, if you are logging DNS requests into graylog you should be able to detect this beaconing on affected machines.
Additionally if you have chosen to enhance your endpoint logging with sysmon you will also have access to process level information to further discover indicators of compromise on your endpoints.
The following instructions assume that you are running a 5.x release of Graylog Security, and have enabled Illuminate processing of your log messages to have them normalized and enriched to the Graylog information model.
To allow us to detect both new and historical IOCs, we will utilize several Sigma rules that were recently added to the Sigma HQ Github repository to detect these attacks.
If you aren’t familiar with Sigma, it is a generic and open signature format that allows you to describe relevant log events in a vendor agnostic way. Graylog Security will allow you to import these rules and have them automatically converted to Graylog alert definitions.
Installing Sigma rules into Graylog Security
For convenience, the sigma rules needed to detect this attack have all been listed below, so you can simply copy and paste them into Graylog and then enable them.
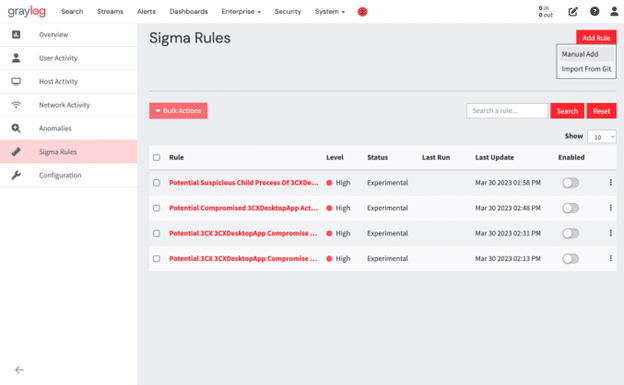
- Log into your Graylog web interface and navigate to Security > Sigma Rules
- In the top right of the screen select Add Rule > Manual Add
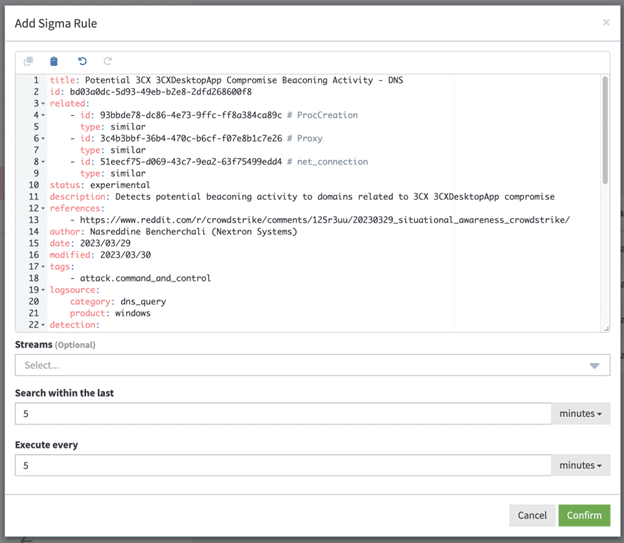
- Copy and paste the Sigma rules of your choice (listed below) into the code box.
- Keep the default search settings of 5 minutes.
- click “Confirm” to save the rule.
- Repeat the process for any other rules you would like to import.
After the rule has been added there are two actions we can take:
- Enable the alert
- Search for historical IOCs in the logs we have already ingested
Enable the Alert
- Check the enable toggle on the Sigma rule you imported to enable the event.
- If you want to receive a notification for that event definition, click the drop-down menu beside the enable toggle and choose “edit event definition”.
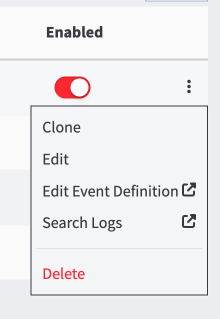
- This will take you to the standard event definition edit page.
- navigate to the “notifications” tab to setup your notification settings for the alert.
- Once your notification settings are complete and saved you will receive an alert whenever a log message matching the sigma rule is found.
Search Historical log files for IOCs
You can also use the Sigma Rules screen to launch a search of your historical log messages for IOCs.
- From that same dropdown menu as above choose “Search Logs”
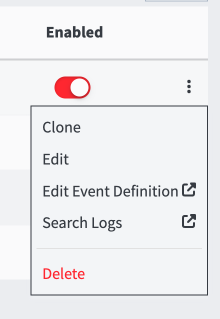
- The Graylog search page will open with your query pre-populated.
- Change the timeframe for your search and away you go!
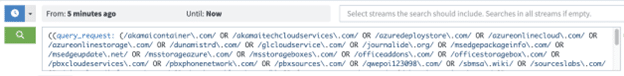
Sigma rules to import
Identify DNS requests to beaconing domains
This rule will search the “query_request” field for the IOC domains associated with this attack. For this to occur, you will need to log DNS requests to Graylog from either from the endpoint (using sysmon) or your DNS servers.
title: Potential 3CX 3CXDesktopApp Compromise Beaconing Activity - DNS
id: bd03a0dc-5d93-49eb-b2e8-2dfd268600f8
related:
- id: 93bbde78-dc86-4e73-9ffc-ff8a384ca89c # ProcCreation
type: similar
- id: 3c4b3bbf-36b4-470c-b6cf-f07e8b1c7e26 # Proxy
type: similar
- id: 51eecf75-d069-43c7-9ea2-63f75499edd4 # net_connection
type: similar
status: experimental
description: Detects potential beaconing activity to domains related to 3CX 3CXDesktopApp compromise
references:
- https://www.reddit.com/r/crowdstrike/comments/125r3uu/20230329_situational_awareness_crowdstrike/
author: Nasreddine Bencherchali (Nextron Systems)
date: 2023/03/29
modified: 2023/03/30
tags:
- attack.command_and_control
logsource:
category: dns_query
product: windows
detection:
selection:
query_request:
- 'akamaicontainer.com'
- 'akamaitechcloudservices.com'
- 'azuredeploystore.com'
- 'azureonlinecloud.com'
- 'azureonlinestorage.com'
- 'dunamistrd.com'
- 'glcloudservice.com'
- 'journalide.org'
- 'msedgepackageinfo.com'
- 'msedgeupdate.net'
- 'msstorageazure.com'
- 'msstorageboxes.com'
- 'officeaddons.com'
- 'officestoragebox.com'
- 'pbxcloudeservices.com'
- 'pbxphonenetwork.com'
- 'pbxsources.com'
- 'qwepoi123098.com'
- 'sbmsa.wiki'
- 'sourceslabs.com'
- 'visualstudiofactory.com'
- 'zacharryblogs.com'
condition: selection
falsepositives:
- Unlikely
level: high
Identify the 3CX desktop app reaching out to beaconing domains
This rule will identify messages when the 3CX app was reaching out to IOC domains. Requires sysmon logging of processes and dns requests from your endpoints into Graylog.
title: Potential 3CX 3CXDesktopApp Compromise Beaconing Activity - Windows sysmon (DNS from 3CX app))
id: 51eecf75-d069-43c7-9ea2-63f75499edd4
related:
- id: 93bbde78-dc86-4e73-9ffc-ff8a384ca89c # ProcCreation
type: similar
- id: 3c4b3bbf-36b4-470c-b6cf-f07e8b1c7e26 # Proxy
type: similar
- id: bd03a0dc-5d93-49eb-b2e8-2dfd268600f8 # dns
type: similar
status: experimental
description: Detects potential beaconing activity to domains related to 3CX 3CXDesktopApp compromise
references:
- https://www.reddit.com/r/crowdstrike/comments/125r3uu/20230329_situational_awareness_crowdstrike/
author: Nasreddine Bencherchali (Nextron Systems)
date: 2023/03/29
modified: 2023/03/30
tags:
- attack.command_and_control
logsource:
category: network_connection
product: windows
detection:
selection:
Image|endswith: '\3CXDesktopApp.exe'
query_request:
- 'akamaicontainer.com'
- 'akamaitechcloudservices.com'
- 'azuredeploystore.com'
- 'azureonlinecloud.com'
- 'azureonlinestorage.com'
- 'dunamistrd.com'
- 'glcloudservice.com'
- 'journalide.org'
- 'msedgepackageinfo.com'
- 'msedgeupdate.net'
- 'msstorageazure.com'
- 'msstorageboxes.com'
- 'officeaddons.com'
- 'officestoragebox.com'
- 'pbxcloudeservices.com'
- 'pbxphonenetwork.com'
- 'pbxsources.com'
- 'qwepoi123098.com'
- 'sbmsa.wiki'
- 'sourceslabs.com'
- 'visualstudiofactory.com'
- 'zacharryblogs.com'
condition: selection
falsepositives:
- Unlikely
level: highFind matching hashes and versions of the compromised 3CX desktop app
This rule will identify compromised versions of the application process being launched either based on file hash, or version and name. Requires sysmon logging process creation to Graylog.
title: Potential Compromised 3CXDesktopApp Activity - Windows Sysmon (file hash)
id: 93bbde78-dc86-4e73-9ffc-ff8a384ca89c
related:
- id: 3c4b3bbf-36b4-470c-b6cf-f07e8b1c7e26 # Proxy
type: similar
- id: bd03a0dc-5d93-49eb-b2e8-2dfd268600f8 # dns
type: similar
- id: 51eecf75-d069-43c7-9ea2-63f75499edd4 # net_connection
type: similar
status: experimental
description: Detects execution of known compromised version of 3CXDesktopApp
references:
- https://www.reddit.com/r/crowdstrike/comments/125r3uu/20230329_situational_awareness_crowdstrike/
author: Nasreddine Bencherchali (Nextron Systems)
date: 2023/03/29
tags:
- attack.defense_evasion
- attack.t1218
- attack.execution
logsource:
category: process_creation
product: windows
detection:
selection_hashes_1:
- hash_sha256:
- 'DDE03348075512796241389DFEA5560C20A3D2A2EAC95C894E7BBED5E85A0ACC'
- 'FAD482DED2E25CE9E1DD3D3ECC3227AF714BDFBBDE04347DBC1B21D6A3670405'
- 'AA124A4B4DF12B34E74EE7F6C683B2EBEC4CE9A8EDCF9BE345823B4FDCF5D868'
- '59E1EDF4D82FAE4978E97512B0331B7EB21DD4B838B850BA46794D9C7A2C0983'
- sha1:
- '6285FFB5F98D35CD98E78D48B63A05AF6E4E4DEA'
- '8433A94AEDB6380AC8D4610AF643FB0E5220C5CB'
- 'BEA77D1E59CF18DCE22AD9A2FAD52948FD7A9EFA'
- 'BFECB8CE89A312D2EF4AFC64A63847AE11C6F69E'
selection_pe_1:
- OriginalFileName: '3CXDesktopApp.exe'
- Image|endswith: '\3CXDesktopApp.exe'
- Product: '3CX Desktop App'
selection_pe_2:
file_version|contains:
- '18.12.407'
- '18.12.416'
condition: all of selection_pe_* or 1 of selection_hashes_*
falsepositives:
- Legitimate usage of 3CXDesktopApp
level: high3CX desktop application starting suspicious child processes
This rule will identify potentially suspicious child processes being launched by the compromised application process. Requires sysmon logging process creation to Graylog.
title: Potential Suspicious Child Process Of 3CXDesktopApp - Windows Sysmon
id: 63f3605b-979f-48c2-b7cc-7f90523fed88
related:
- id: 3c4b3bbf-36b4-470c-b6cf-f07e8b1c7e26 # Proxy
type: similar
- id: bd03a0dc-5d93-49eb-b2e8-2dfd268600f8 # dns
type: similar
- id: 51eecf75-d069-43c7-9ea2-63f75499edd4 # net_connection
type: similar
- id: 93bbde78-dc86-4e73-9ffc-ff8a384ca89c
type: similar
status: experimental
description: Detects potential suspicious child processes of "3CXDesktopApp.exe". Which could be related to the 3CXDesktopApp supply chain compromise
references:
- https://www.reddit.com/r/crowdstrike/comments/125r3uu/20230329_situational_awareness_crowdstrike/
- https://www.crowdstrike.com/blog/crowdstrike-detects-and-prevents-active-intrusion-campaign-targeting-3cxdesktopapp-customers/
author: Nasreddine Bencherchali (Nextron Systems)
date: 2023/03/29
tags:
- attack.command_and_control
- attack.execution
- attack.t1218
logsource:
category: process_creation
product: windows
detection:
selection:
ParentImage|endswith: '\3CXDesktopApp.exe'
Image|endswith:
- '\cmd.exe'
- '\cscript.exe'
- '\mshta.exe'
- '\powershell.exe'
- '\pwsh.exe'
- '\regsvr32.exe'
- '\rundll32.exe'
- '\wscript.exe'
condition: selection
falsepositives:
- Unknown
level: highGraylog Security: Sigma Rule Event Processor for Advanced Detection Capabilities
With Graylog Security, you get the security functionality of SIEM and the intuitive user interface that makes managing security faster. With our Sigma Rule Event Processor, you can import rules you want to use directly from GitHub, and we automatically associate it with an event definition or customize the definition, giving you a way to rapidly mature your detection capabilities. Follow this video for more 3CX content.



