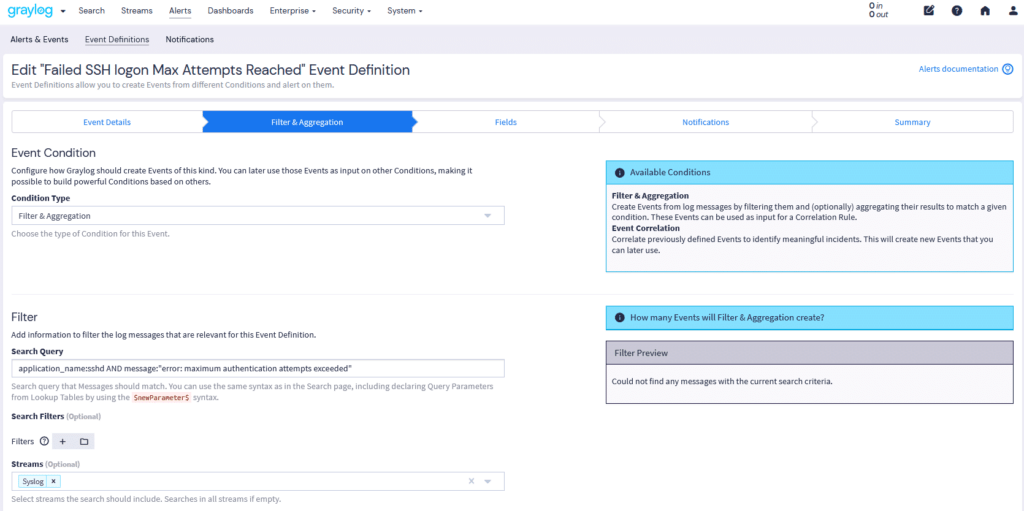
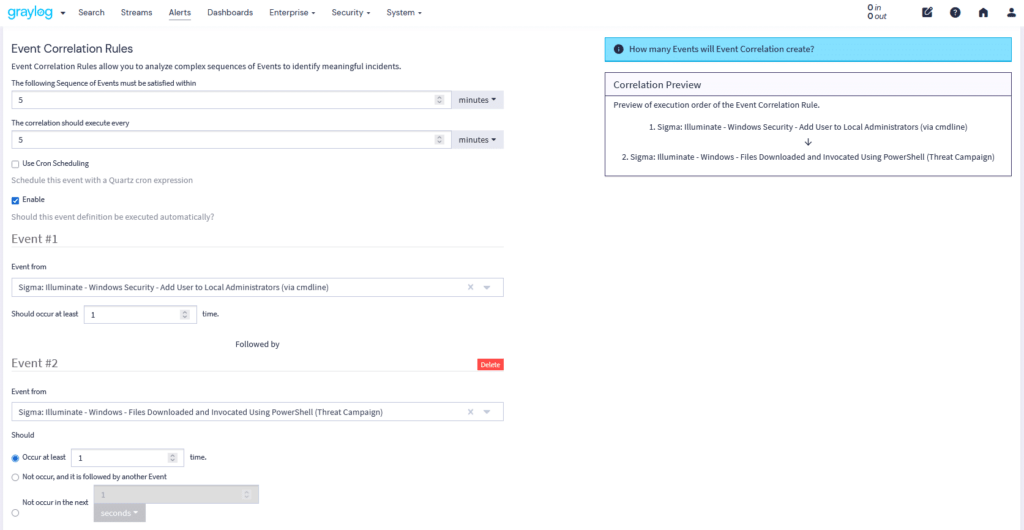
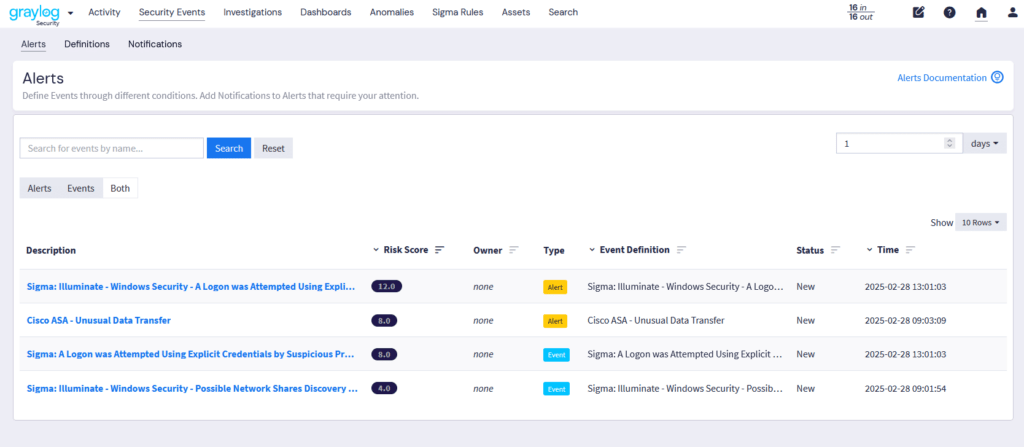
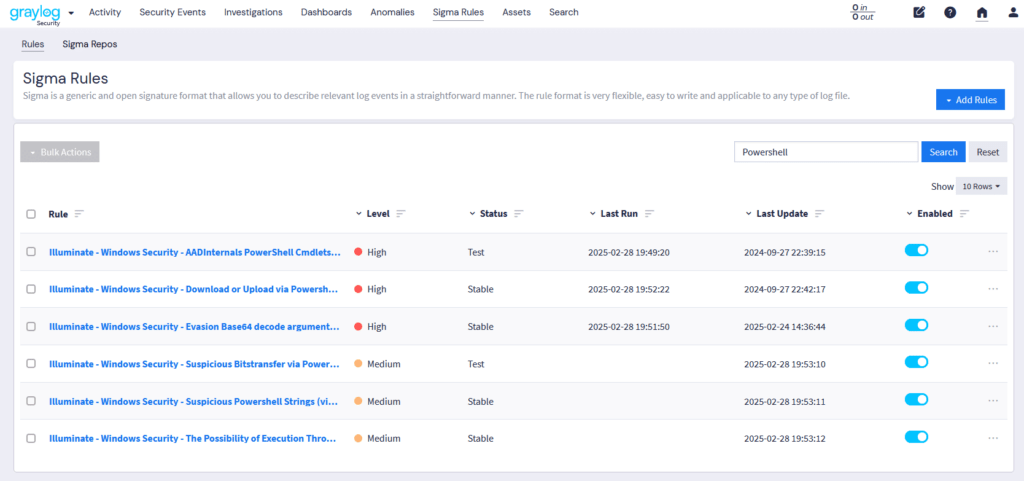
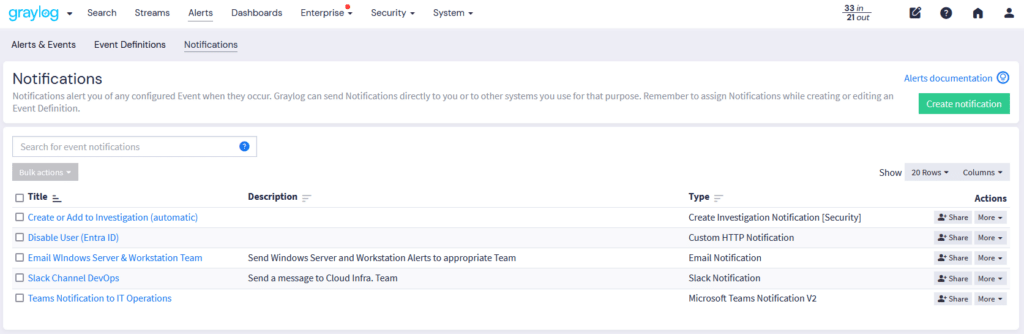
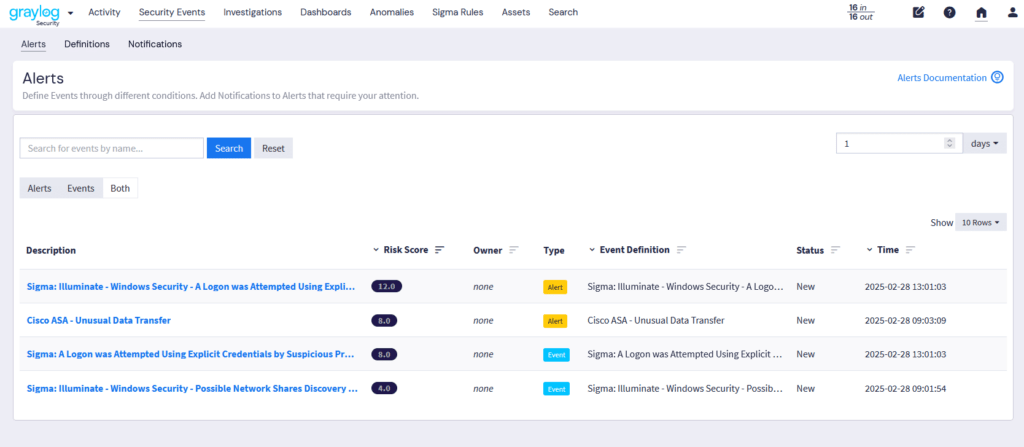
Graylog’s Events & Alerts provide granular control over threat detection and response workflows. With Illuminate and Sigma Rule integration, security teams can leverage standardized detection rules to enhance visibility and streamline incident investigation. Graylog Correlation rules refine alerts for maximum clarity. Below are the key features that make Graylog’s alerting system both powerful and intuitive: