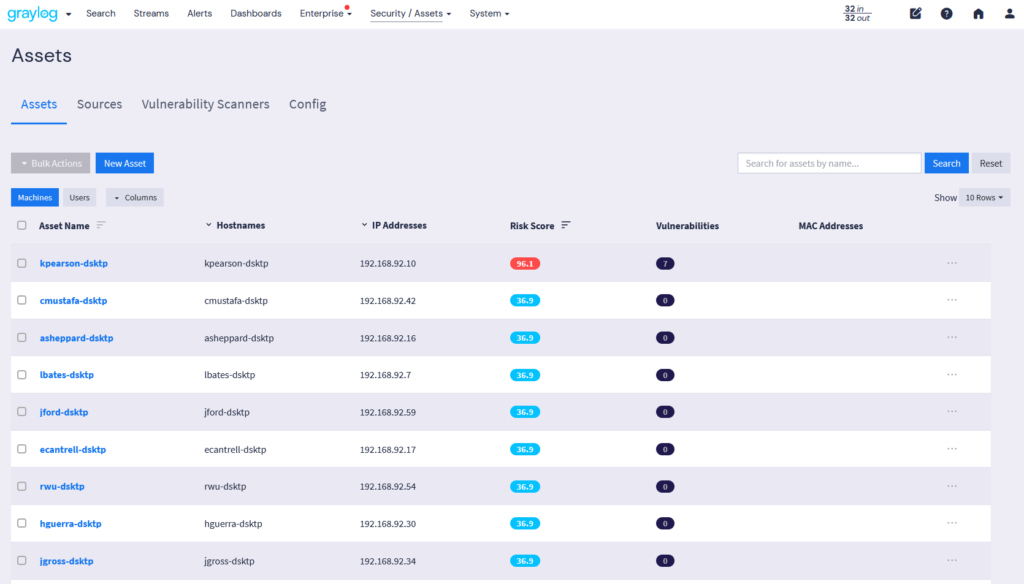
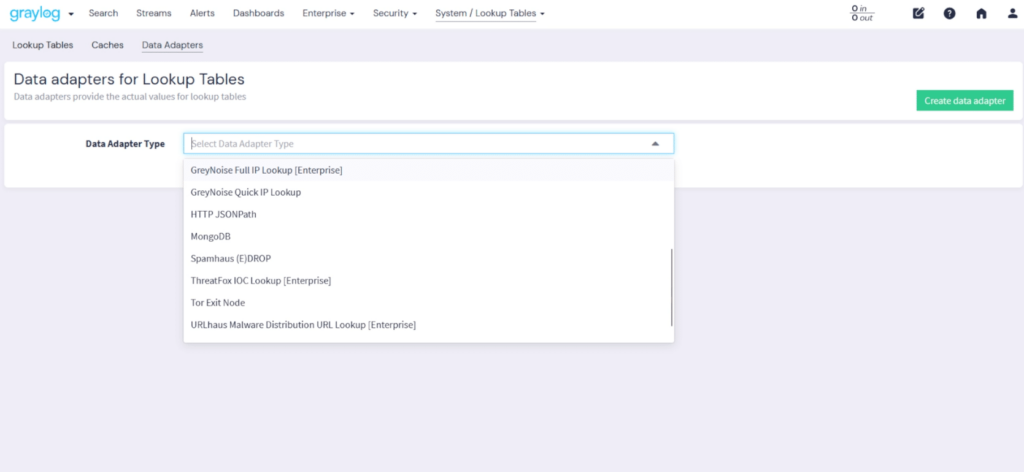
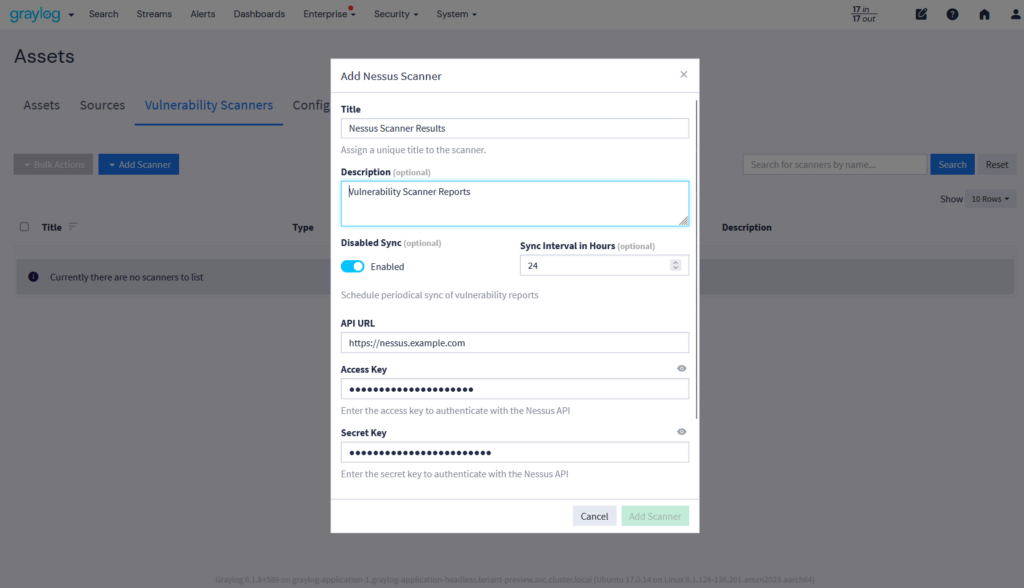
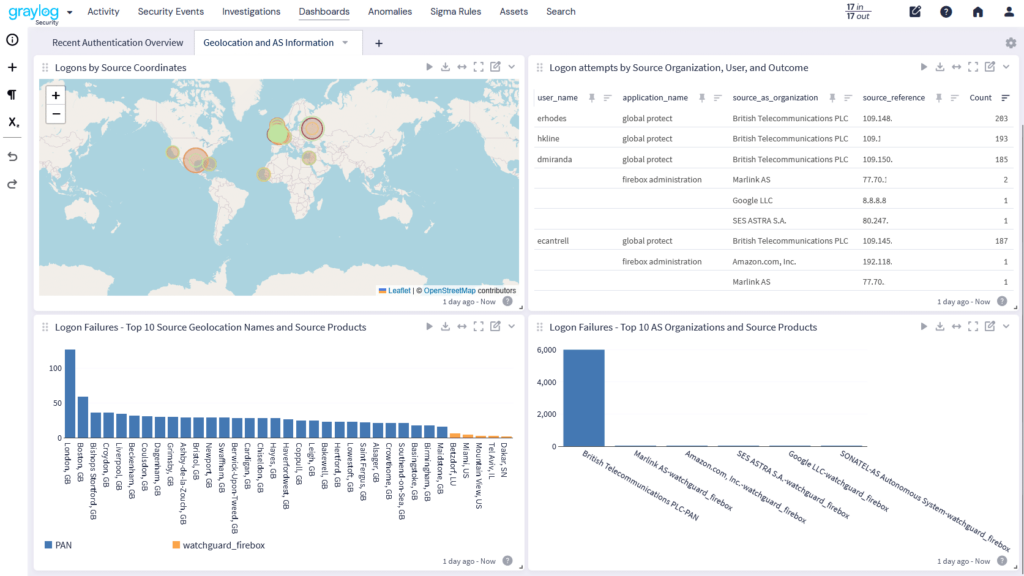
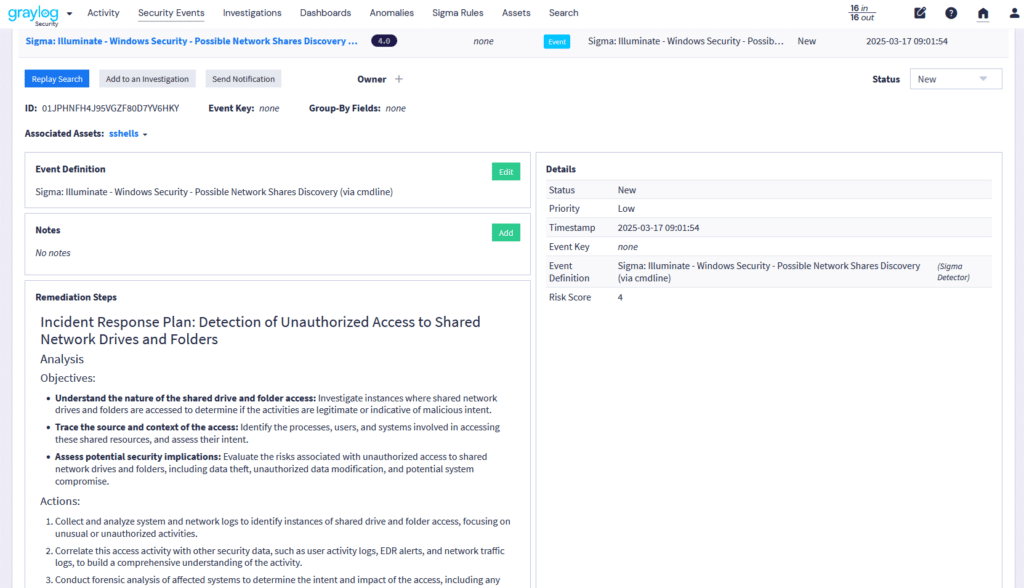
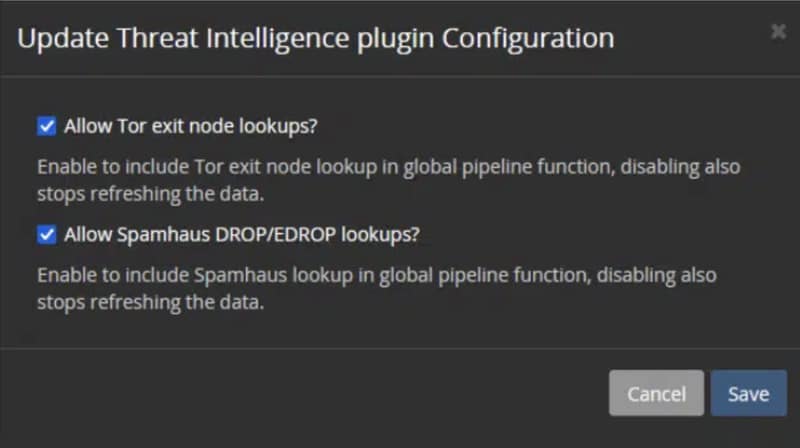
Data enrichment adds critical context to logs by integrating and normalizing data with details like user identity, location, and device data while maintaining a standardized schema. This ensures seamless aggregation, cohesive analysis, and deeper insights into system performance and security.