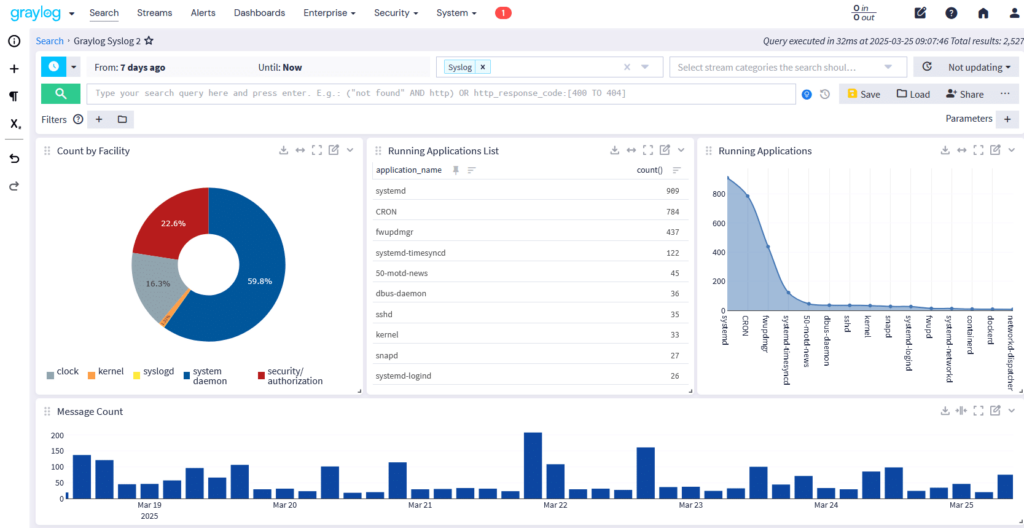
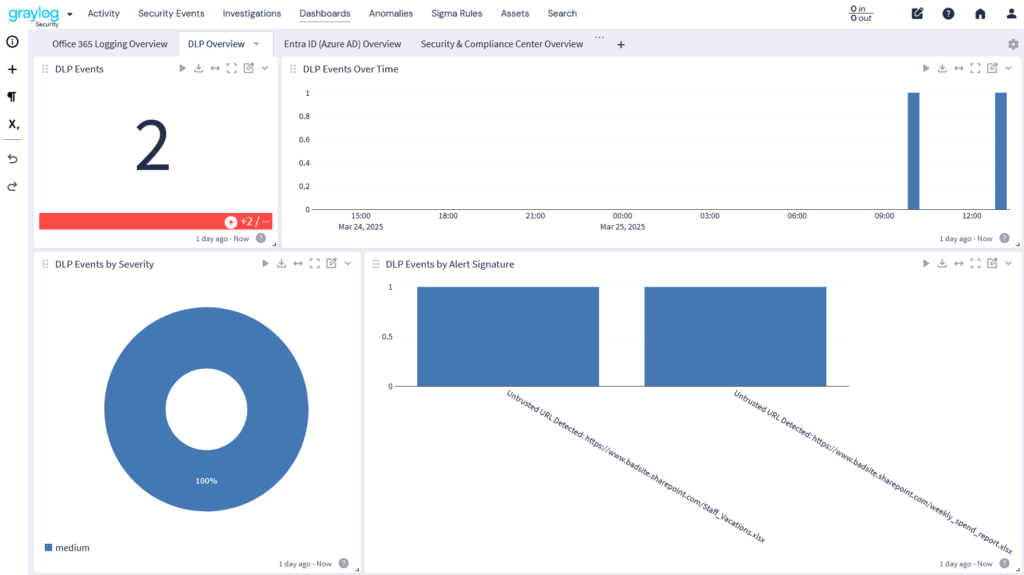
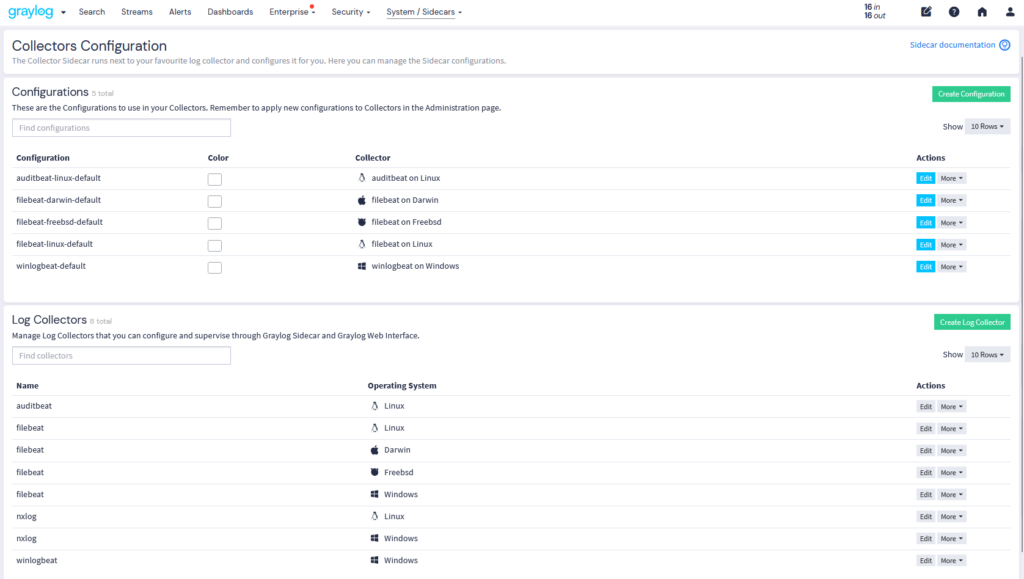
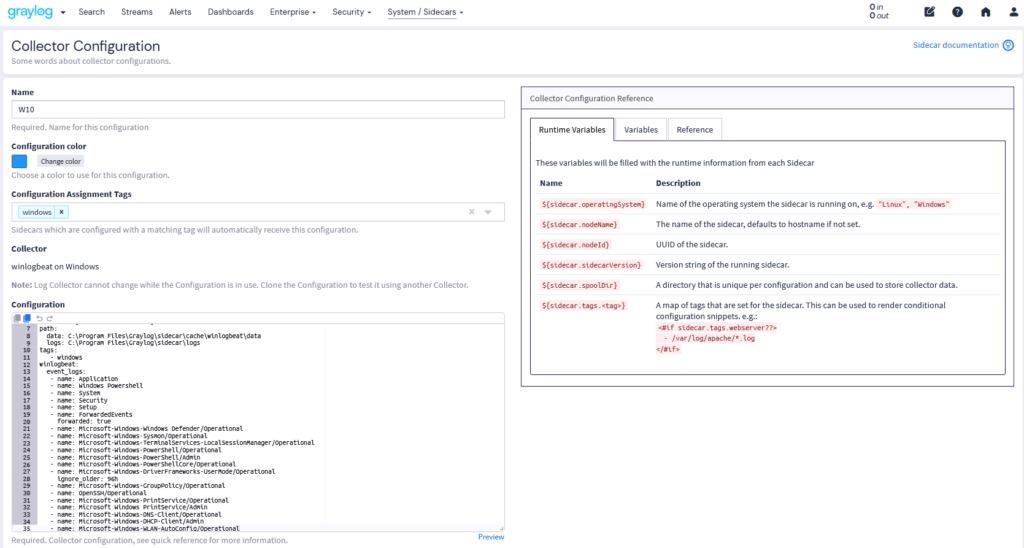
Log Collection adds critical context by normalizing logs with user identity, location, and device data—automatically applying a consistent schema. That means cleaner aggregation, smarter analysis, and clearer insights across performance and security events.