Security hygiene is the process of reviewing your current cybersecurity posture and implementing security controls that mitigate data breach risks. As you mature your security hygiene, you create a centralized log management strategy that defines a path to a more robust posture. As part of this, you need to accommodate for the way threats evolve, including those unique to your specific industry or business.
The Key to Maturing Cyber Hygiene: Getting the Right Tools
As you mature your security program, you can’t manage everything manually. For example, you might have different cybersecurity tools for:
Reviewing these logs and reports by hand takes too much time and increases human error risk.
Process Automation
The security tool proliferation struggle is real. You can’t keep up the same pace as threat actors if you have mostly manual security processes.
As you start to move towards automation, you need to:
- Identify all the disparate tools
- Know who uses each tool
- Address which processes can be automated
- Know what processes need to remain manual
- Ensure appropriate resourcing
As your cyber hygiene evolves, you need to keep iterating these steps. As you mature your log management processes, you’ll find that you can eliminate more tools, automate more processes, and allocate resources more efficiently.
Technology to Enable People
The technology that you choose to mature your cyber hygiene should help your security team be more efficient, not hinder their ability to do their job. You need to build a technology investment foundation around your people. A Security Information and Event Management (SIEM) tool can help you mature your security posture. However, if it’s too difficult for your team to use, you won’t be able to gain all the benefits from the purchase.
For example, when a SIEM sends out an error code or other alert, the person receiving the message should know what to do. You might have a well set up environment and the best machine learning tool. If your security analyst doesn’t know what to do with the information, then you still have a cyber hygiene problem.
SIEM tools require users to have specialized skills and experience to optimize usage. You can have security analysts who know how to fix a vulnerability or investigate an incident, but they may not have experience with the tool you’re using. Without security team members who can use a tool effectively, you still lack good cyber hygiene.
Centralized log management is a way to give your team an easy-to-use solution that helps them detect, investigate, remediate, and recover from security incidents faster.
Overcoming the Obstacles to Security Hygiene Maturity
Your strategy is your cyber hygiene map, but you also need strong leadership in place to overcome some obstacles. Without a captain at the helm of your cyber hygiene ship, you might find that your boat ends up in dry dock.
Without a captain to steer your cyber hygiene boat, resistance to change can increase the cost of both tools and security.
Fear of Change
Many people are afraid of change. In security, analysts may have favorite tools that they know well. They understand how they work, and they like using them. Often, people fear new tools and automation because they worry about job security. If you can automate a task, you might not need them anymore.
For example, you might have someone running a command line to get data before putting your centralized log management tool in place to do searches. As you start to mature your cyber hygiene, automating some of these manual functions, people might be resistant because they worry that they will become obsolete.
Having strong leadership can help overcome resistance, especially when the centralized log management solution is easy to use. If your team members don’t require specialized skills, they will be less likely to worry about being replaced. Additionally, strong leadership can help them understand how the solution makes their jobs easier and overcome the fear that it eliminates their position.
By overcoming this resistance, you are able to reduce the time spent on security tasks, enhance your security hygiene, and increase your return on technology investment.
Lack of Collaboration
Another reason people might resist moving to a centralized log management solution is that they aren’t used to collaborating. Often, security teams struggling from tool sprawl find that everyone has their own “place” on the team. Instead of worrying about being replaced by the tool, team members may be worried about how others perceive them and their ability to do their jobs.
Consider the following example:
- A Red Team member gains access to a domain controller, creates an account, and gives that account domain admin privileges.
- The alarm triggers.
- The ticket goes to the Blue Team.
- The Blue Team analyzes it and recognizes that it’s a real issue.
- They sent it to the Identity and Access Management (IAM) team, explaining that someone was added to this domain admin group.
- The IAM team looks for the account
- The Red Teamer already deleted it.
- With the account deleted, the IAM team says they have no action to take.
Each team member is doing their job and doing it correctly. However, the lack of centralized visibility makes collaboration difficult. Even with centralized log management, your cyber hygiene suffers.
Shared dashboards enable collaboration because everyone has the same visibility. For example, you may not want your IAM team making changes to your security dashboard, but you can share with view-only so that everyone works from the same data.
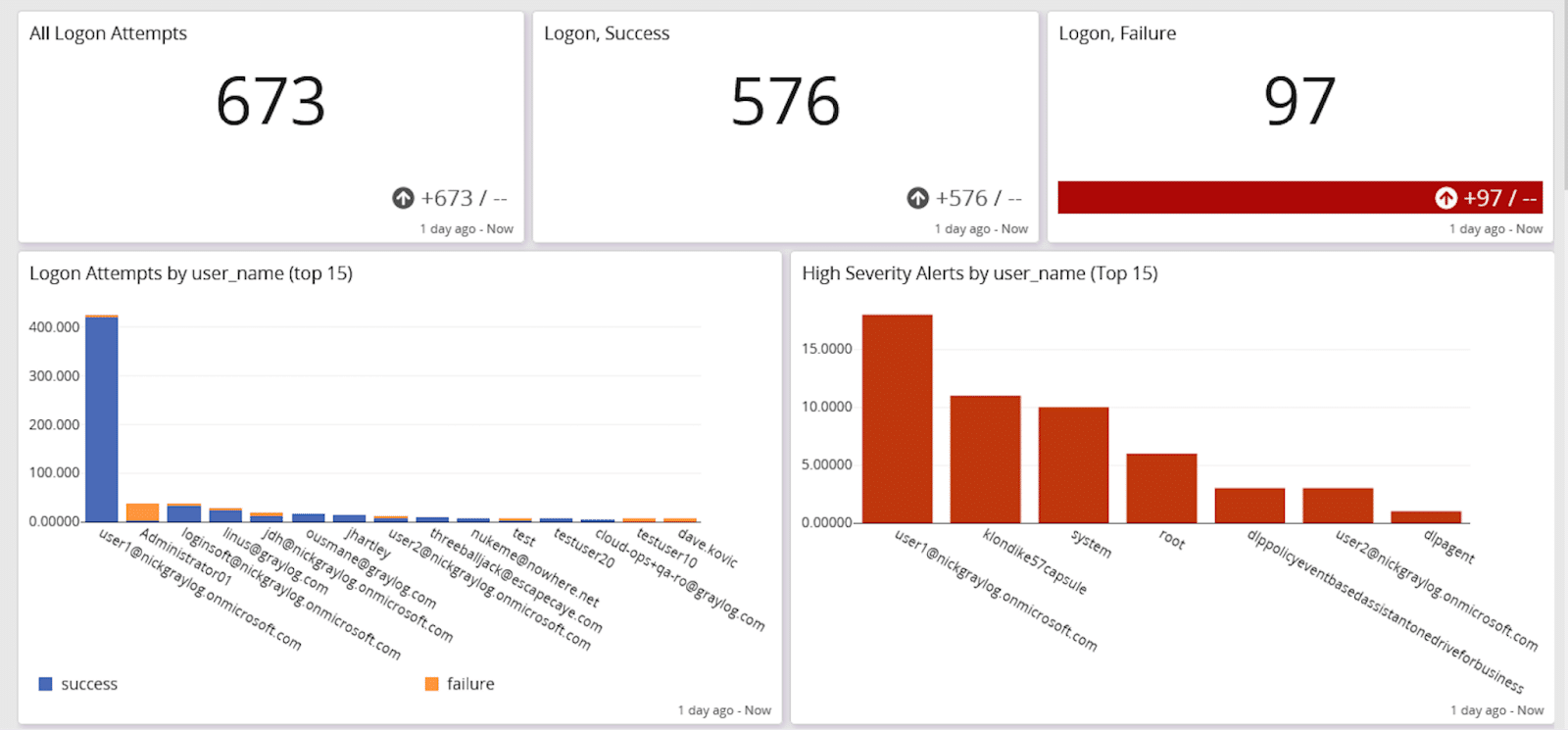
To mature your security hygiene, you need to have processes in place as well as tools. With the right processes and tools enabling collaboration, you reduce the likelihood of experiencing a security incident and optimize your IT spending.
Leading the Charge: A Top Down Approach
To overcome the resistance to change, your strategy needs to be a top-down, management decision. Engineers may understand the value of centralized log management, but they may not be able to convince other teams to join the crew.
Additionally, senior leadership can also understand how security hygiene and centralized log management fit into the overall picture. Each senior management team member has visibility into different areas.
Everyone needs to be a security champion, including:
- Chief Financial Officer: current tool spending
- Chief Information Officer: security risk evaluation
- Chief Executive Officer: overarching revenue and business vision
- Chief Compliance/Audit Officer: impact compliance violations have on revenue
By defining the use cases in advance, security hygiene becomes part of a larger corporate initiative, leadership team members can more effectively drive buy-in and overcome resistance.
Maturing Security Hygiene with Graylog Security
Graylog Security gives you the out-of-the-box security content you need in our easy-to-use centralized log management platform so that you can rapidly mature your security hygiene. You can start getting valuable data from your logs faster with a solution that enables your team.
With a single solution that works for IT operations and security teams, you get a two-for-one capability that automates processes and enhances collaboration for stronger security.


