Text editors rarely show up in threat models. Installers show up even less.
CVE-2025-49144 changes that. The issue is a local privilege escalation in the Notepad++ Windows installer that can allow a low-privileged user to gain SYSTEM-level execution by abusing insecure executable search behavior during installation. Affected versions include Notepad++ 8.8.1 and earlier, per the NVD record.
This post stays focused on what lean security teams need: signals you can actually search, plus a practical detection rule that works with common Windows telemetry.
No exploit code. No lab theatrics. Proof-first detection built on evidence.
Search Your Notepad++ File Versions in Graylog
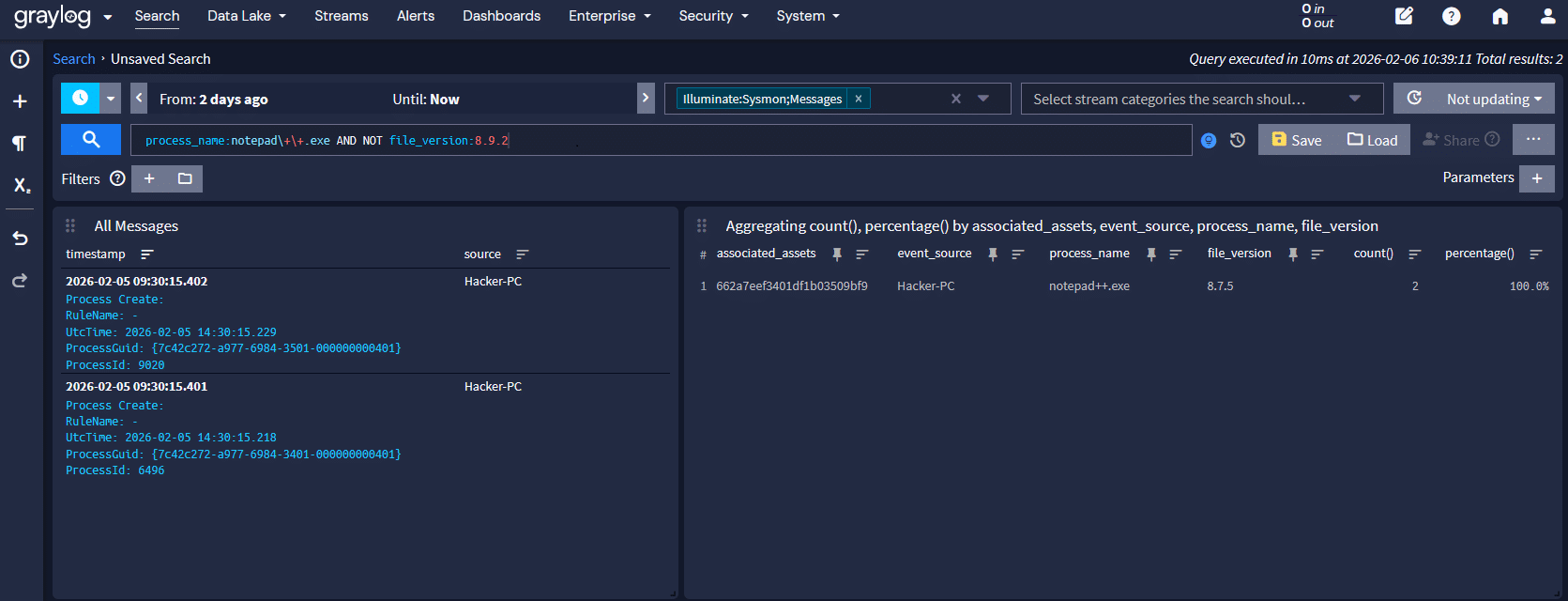
To identify potentially vulnerable endpoints, start by searching for Notepad++ versions using Sysmon process creation events.
Step 1: Find potentially vulnerable Notepad++ versions
Start by finding hosts where Notepad++ executable versions indicate exposure. If Sysmon is collecting file version metadata in process creation events, the can look like this:
process_name:notepad\+\+.exe AND NOT file_version:8.8.2Installers for Notepad++ v8.8.1 and earlier are affected. This search helps confirm where and how often the installer is executed across your environment.
That query is designed for coverage, not perfection. It helps identify endpoints where Notepad++ activity should be reviewed and confirms how often Notepad++ runs in your environment.
What the Vulnerability Looks Like Operationally
CVE-2025-49144 is a local privilege escalation vulnerability in Notepad++ installers (≤ 8.8.1). The exploit uses the plugins folder to place and load DLLs. This means any DLL placed there can run. During installation, the installer attempts to register NppShell.dll by calling regsvr32.exe without a fully qualified path.
An attacker can exploit this by placing a malicious regsvr32.exe in the same directory as the installer. When invoked, the malicious binary executes with SYSTEM privileges.
Operationally, this produces a strong signal:
- exe runs as SYSTEM
- Executed from a non-standard directory
- Spawned by the Notepad++ installer
Why Sysmon Is Ideal for Detecting It
Sysmon captures the core mechanics this exploitation path relies on:
- Process creation with full command line details
- Parent-child relationships
- Executable paths
- High-fidelity context for investigations and correlation
Microsoft describes Sysmon as logging detailed process creation activity and other system behaviors to the Windows event log once installed.
For this CVE, Sysmon Event ID 1 is the workhorse: it gives enough detail to separate legitimate regsvr32.exe usage from a hijacked binary executed outside System32 or SysWOW64.
Step 2: Hunt for the high-signal behavior
The high-signal indicator for this scenario is regsvr32.exe running from a non-standard directory with a Notepad++ shell registration context.
Use a general search that focuses on three elements:
- exe execution
- evidence of the Notepad++ shell DLL path
- exclusion of known legitimate Windows paths
A General Search to Find the Exploit on Hosts
Search for Hijacked regsvr32.exe Execution
(((process_command_line: /.*[\\]contextMenu[\\]NppShell\.dll.*/)
AND (process_path: /.*[\\]regsvr32\.exe/)
AND (process_command_line: /regsvr32 \/s.*/))
AND NOT (process_path: (/C:[\\]Windows[\\]System32[\\]regsvr32\.exe/ OR /C:[\\]Windows[\\]SysWOW64[\\]regsvr32\.exe/)))This is proof-first hunting: It looks for the execution behavior that should almost never occur during standard software installation practices.
A Sigma Rule for Potential Detection and Action
Step 3: Add a Sigma rule for detection and response
Below is a Sigma rule aligned to the published logic used by the Sigma community for this CVE. The rule flags regsvr32.exe executions that match the suspicious command-line patterns while excluding the normal Windows binary locations.
title: Potential Notepad++ CVE-2025-49144 Exploitation
id: 933f0bb5-0681-4fe7-8a17-4e6cccbaac44
status: experimental
description: |
Detects potential exploitation of CVE-2025-49144, a local privilege escalation vulnerability in Notepad++ installers (v8.8.1 and prior) where the installer calls regsvr32.exe without specifying the full path.
This allows an attacker to execute arbitrary code with elevated privileges by placing a malicious regsvr32.exe alongside this Legitimate Notepad++ installer.
The vulnerability is triggered when the installer attempts to register the NppShell.dll file, which is a component of Notepad++.
references:
- https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2025-49144
- https://x.com/NullSecurityX/status/1937444064867029179
author: Swachchhanda Shrawan Poudel (Nextron Systems)
date: 2025-06-26
tags:
- attack.persistence
- attack.privilege-escalation
- attack.defense-evasion
- attack.t1574.008
- cve.2025-49144
- detection.emerging-threats
logsource:
product: windows
category: process_creation
detection:
selection:
Image|endswith: '\regsvr32.exe'
CommandLine|startswith: 'regsvr32 /s'
CommandLine|contains: '\contextMenu\NppShell.dll'
filter_main_legit_regsvr32:
Image:
- 'C:\Windows\System32\regsvr32.exe'
- 'C:\Windows\SysWOW64\regsvr32.exe'
condition: selection and not 1 of filter_main_*
falsepositives:
- Unknown
level: high
Final Takeaway
CVE-2025-49144 is a reminder that privilege escalation often arrives through ordinary workflows. The fastest teams do not wait for noisy indicators. They set proof-first detections around behaviors that are rare, high-signal, and easy to validate.
If regsvr32.exe runs as SYSTEM outside System32 or SysWOW64, that should become a known event in minutes, not a surprise discovered after persistence is established. If you are not logging Sysmon, getting started with Sysmon is an important step in your detection capabilities.
Learn more about using Graylog Illuminate content packs for Sysmon to normalize Sysmon data and surface signals fast.



