Devices, applications, and systems logs are needed to detect, analyze, and mitigate cybersecurity threats. Logs in a SIEM are like gold; they are both valuable. Gold is part of the economy, and logs are part of the IT ecosystem and are the foundation for cybersecurity. Here’s why they compare to liquid gold!
Raw Material: Unrefined Yet Invaluable
Looking at gold in its raw form may seem lackluster, but as soon as you process it into something beautiful, its value increases. Just like that bling you might wear, it may have been made into something you want to see. Like logs, processing raw logs from applications, systems, and hardware will show high value when the opportunity presents itself.
While raw gold has more value when refined, logs are only valuable when properly analyzed. Without processing, they are mass amounts of data. Enriching logs with additional context like asset information, IP Geolocation, threat intel, and risk scoring gives you real insights into this information. With SIEM tools, their value becomes apparent, transforming and enriching them into information crucial for threat detection.
Liquidity: Immediate Value in Critical Moments
Gold has always been an asset, easily converted into currency or goods. In cybersecurity, the flow of logs and their information is very similar. When a cyber threat occurs, security teams need quick access to specific logs to determine what the attack is and how to mitigate it. A SIEM that is refined to aggregate and correlate logs in real-time will help you capture those moments in your incident response journey.
Historical Value: Logs Accumulate Worth Over Time
Gold has always been viewed as very valuable over a long period of time. Similarly, logs store distinct information over a period of time. Within a SIEM, these logs record what’s happening in the IT ecosystem, including network events, user activity, and many others. While logs are generated, they help teams identify current problems and potential issues in the future.
As a security issue unfolds, being able to search months or years of this data gives teams the ability to see how severe an issue might be. A one-off problem might be a small flake of gold, but as you dig in and find it’s part of a larger attack, it could be part of something larger.
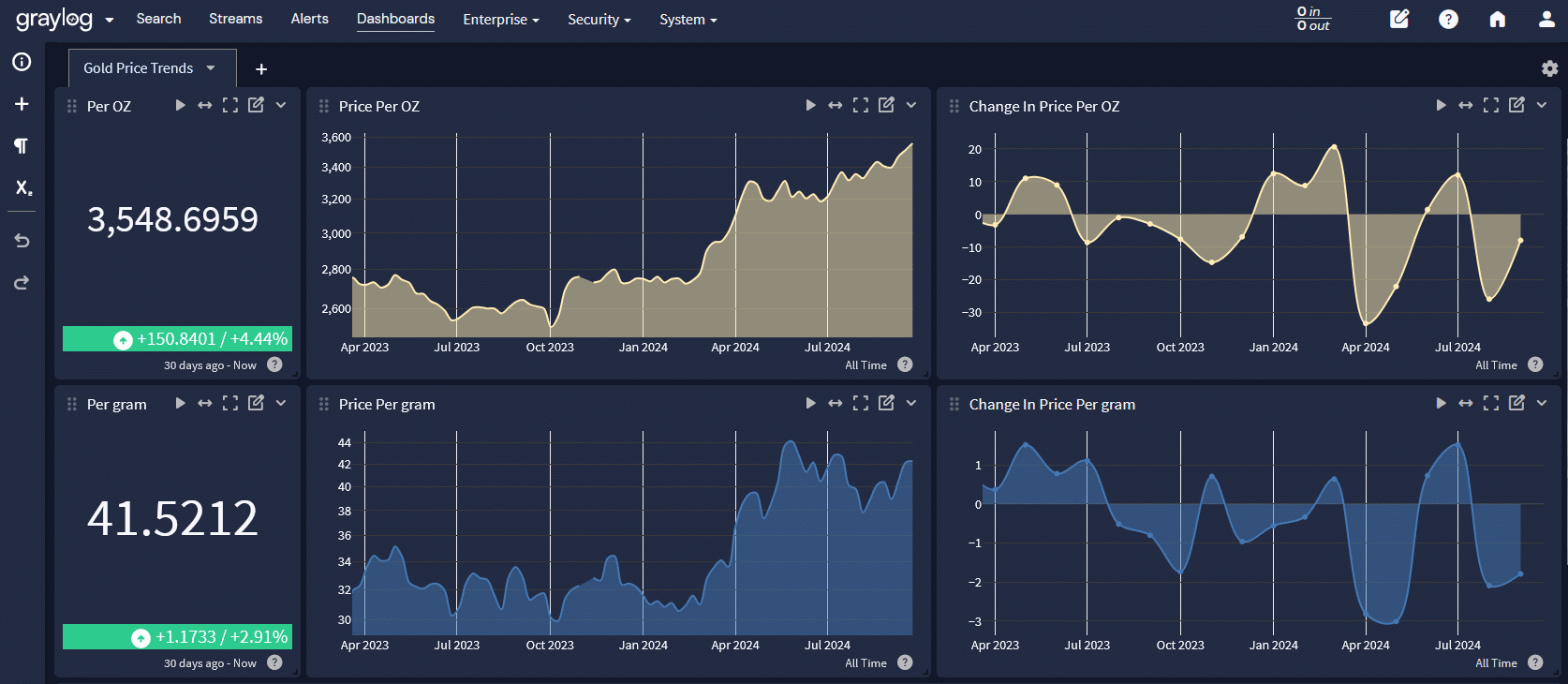
Refinement: SIEM Transforms Logs into Actionable Insights
Raw gold is not much until it’s processed and shaped. In cybersecurity, your SIEM is your refinery for your logs. A SIEM platform analyzes, correlates and normalizes data creating raw unprocessed gold into data that identifies actionable insight driving security decisions.
With a SIEM, logs are more readily available and easy to interpret. Logs are very overwhelming without one, even for experienced security teams. A well-implemented SIEM will help fuel the priority during the most critical response to security Issues. Having the ability to prioritize security issues like unusual login patterns, unauthorized access attempts, or network anomalies becomes the norm when implementing a SIEM.
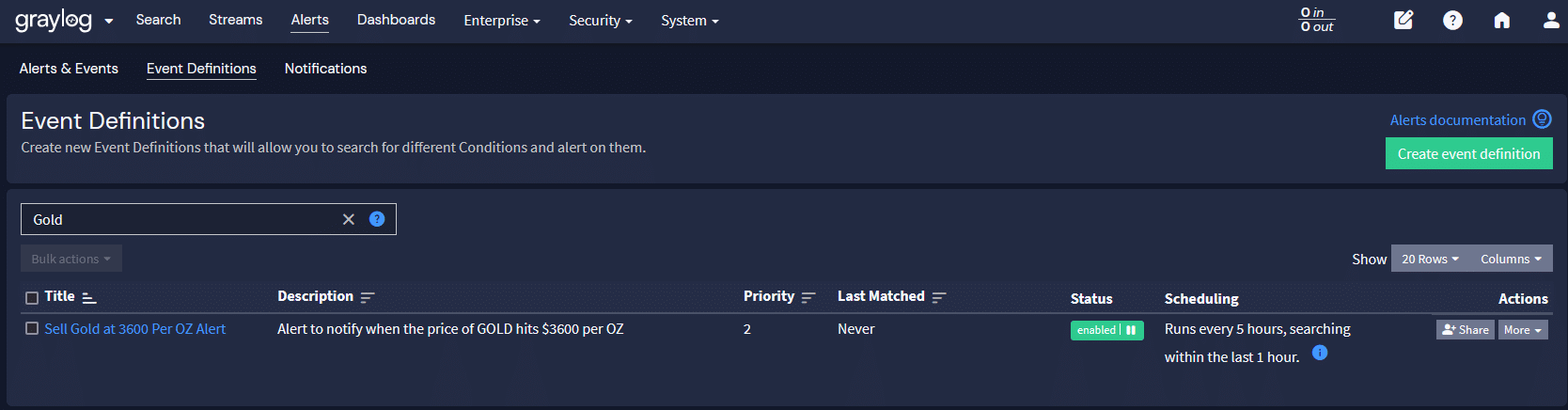
Scarcity: Not All Logs Are Created Equal
Panning for gold can bring up real gold and fool’s gold. Just like logs, they all don’t have equal value. Some logs are more critical than others. Logs from Firewalls, authentication services or even intrusion detection systems are pure gold. These logs are essential for helping to identify and prevent cybersecurity threats. Some logs might be noise, just like fool’s gold.
An efficient SIEM is like sluicing for gold, refining the valuable logs and leaving out the noise. Overburdening a SIEM with excessive logs can confuse the ability to detect threats efficiently. By refining the sources of logs, teams can extract the most valuable information, ensuring their SIEM focuses on what matters.
Regulatory Compliance: Security and Trust Built on Logs
Gold has long been an asset in many economic investment portfolios. Similarly, logs create the foundation of regulatory compliance and trust in cybersecurity. Many industries, such as finance and healthcare, are required to have their specific logs comply with GDPR, HIPAA, and PCI-DSS regulations. Organizations can be exposed to unwanted legal risks and financial penalties without these logs.
Logs are like an organization’s gold mine. Logs create trust with regulators, customers, and stakeholders. A SIEM like Graylog helps organizations to meet compliance standards, ensuring cybersecurity and transparency.
Conclusion: Smelting the Value of Logs
Just as gold is an indispensable asset, logs are the same for cybersecurity operations. Logs carry the weight you need to detect, analyze, and prevent security incidents. When processed through a SIEM, they are valuable resources. Their value in a SIEM is crucial after they have been refined, stored, and utilized correctly into value for your organization.
With Graylog Enterprise and Security, you can harness the liquid gold of logs to stay ahead of threats, streamline incident response, and reduce operational costs. Without the right logs, your view of this shiny object may have consequences during an cybersecurity event.



