The massive shift to remote work makes managing endpoint security more critical and challenging. Yes, people were already using their own devices for work. However, the rise in phishing attacks during the COVID pandemic shows that all endpoint devices are at a higher risk than before. Plus, more companies are moving toward zero-trust security models. For a successful implementation, you need to secure your endpoints. As a security analyst, this means you need high-fidelity endpoint log monitoring capabilities for a more robust security posture.
MALWARE, RANSOMWARE, AND PHISHING – OH MY!
Endpoint security is one of the key tenets of zero trust because devices connecting to your network can be used as part of an attack. Further, your workforce may still be entirely or primarily remote. This means that you have a lot of devices connecting to a lot of insecure networks. Any one of these devices can be compromised easily.
According to the 2021 State of the Phish report, the top five most successful phishing test themes in 2020 were:
- New Microsoft Teams request
- Coronavirus advisory alert and health warning
- Office 365 password expiration notice
- Deactivation of old OneDrive account
- OneDrive shared contract notification
Basically, users wanted to get work done and collaborate, so it was easier to “trick” them into failing the phishing test.
Additionally, more than 50% of people with work-issued devices give their friends and family access. According to the report, friends and family use these devices to:
- Check/respond to personal email
- Read news stories
- Research
- View/post to social media
- Shop online
- Stream media
It makes sense. With everyone home, sharing devices was easier. However, this puts all these company-owned devices at risk of being infected with malware or ransomware. One phishing email to a friend or family member could compromise the device.
USING LOG MANAGEMENT AS PART OF ENDPOINT SECURITY
Whether you’re feeding your logs into a SIEM or using your log management solution as the basis of your security monitoring, the good news is that you can generate high-fidelity endpoint security alerts.
USING LOG MANAGEMENT TO SUPPORT ENDPOINT SECURITY
Using your log management solution as a standalone security tool is possible. Your goal should be to collect the right logs to correlate events in a meaningful way.
You can collect, aggregate, and correlate events across devices and security solutions if you have layered protections. This gives you high fidelity alerting by enriching your data.
EXAMPLE
If you have Microsoft Endpoint Manager, you need to collect these:
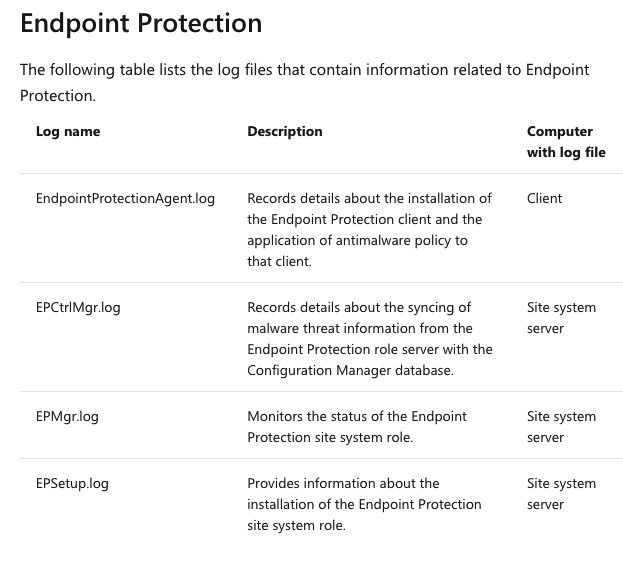
Now, you might also be supplementing your Microsoft Endpoint Manager with an antivirus agent like Symantec. To enrich your data, you also might want to collect these logs:
- Application and Device Control
- Computer Status
- Deception
- Network and Host Exploit Mitigation
- Risk
- Scan
AUGMENTING A SIEM WITH LOG MANAGEMENT
Your SIEM sends security alerts by using correlation rules. However, SIEMs send high volumes of alerts which can become overwhelming for security teams. Alert fatigue is real. Consider the following research based on responses from 2,303 IT security decision makers:
- 54% of SOC teams are drowning in alerts
- 55% are not confident in their ability to prioritize or respond
- 27% spend their time dealing with false positives
SIEMs can help you get more secure, but you need to make sure that they’re sending high-fidelity alerts.
Centralized log management can do a lot of the backend work for you. After all, SIEMs rely on logs. If you’re sending only the most important, actionable data to your SIEM, you’re fine-tuning your tool for more effective alerting. This means more effective response.
You can collect all your endpoint logs in your log management solution. Additionally, it will do the parsing and normalization for you so that you don’t need to have SIEM-specific coding knowledge.
Finally, because your log management solution does the correlation, you can optimize your SIEM by feeding it enriched data to reduce the number of false positives.
USING GRAYLOG FOR ENDPOINT SECURITY
Graylog makes it easy to use endpoint logs for monitoring security.
DATA COLLECTION, AGGREGATION, CORRELATION, AND STORAGE
Graylog makes it easy to ingest the logs you need, the way you need to collect them. You can use log sources or individual inputs. Since Graylog is flexible, you can adjust everything to your needs rather than changing your setting to fit Graylog.
Graylog does the normalizing and parsing for you to aggregate everything for better correlation. Our Graylog Extended Log Format (GELF) comes with optional compression, chunking, and a clearly defined structure. This does all the work to get visibility across divergent security tools and devices.
With Graylog Cloud, you can get the flexibility and scalability of the cloud to reduce costs and get more storage.
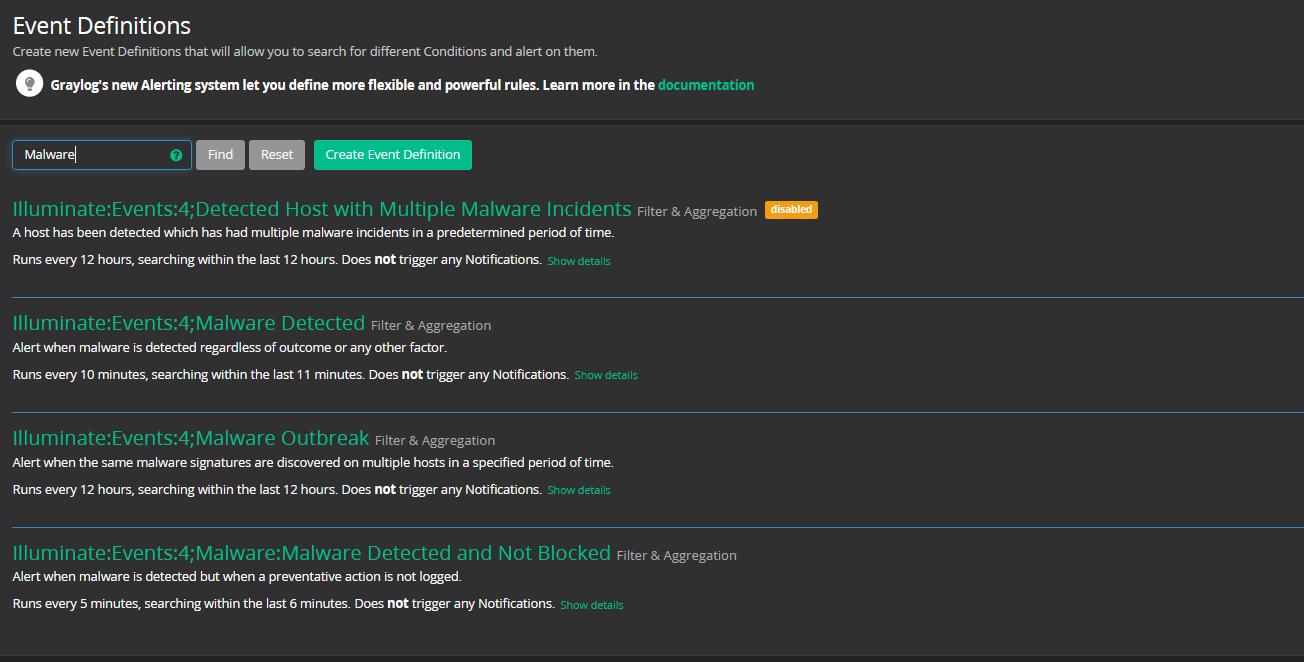
REAL-TIME ALERTS
In Graylog, an Alert is triggered when a defined Event is detected. Events are where the magic happens. When you create an Event, you set filters and aggregations that tell Graylog what to look for (or not look for) in your event logs.
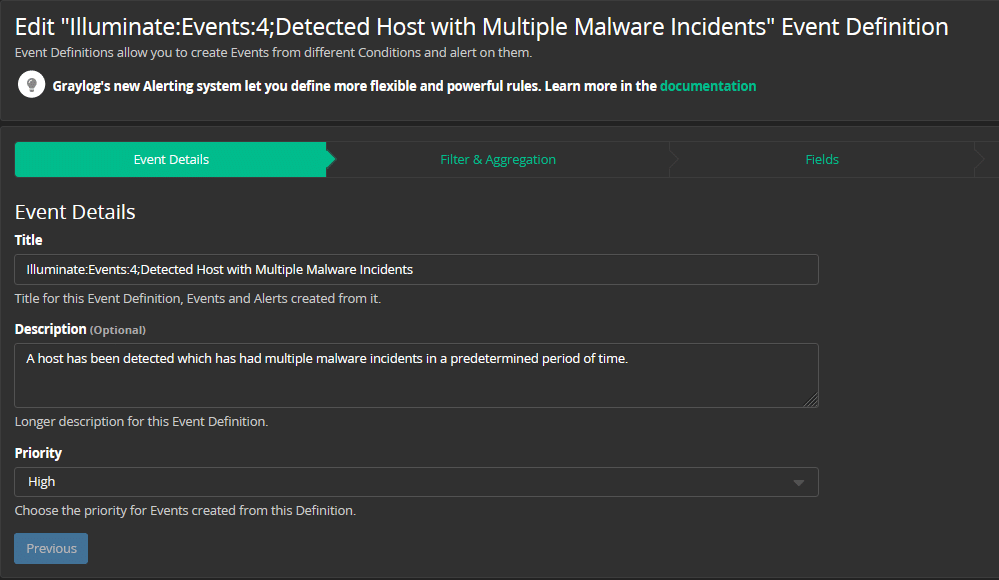
The Event that triggers an endpoint security alert could look like this:
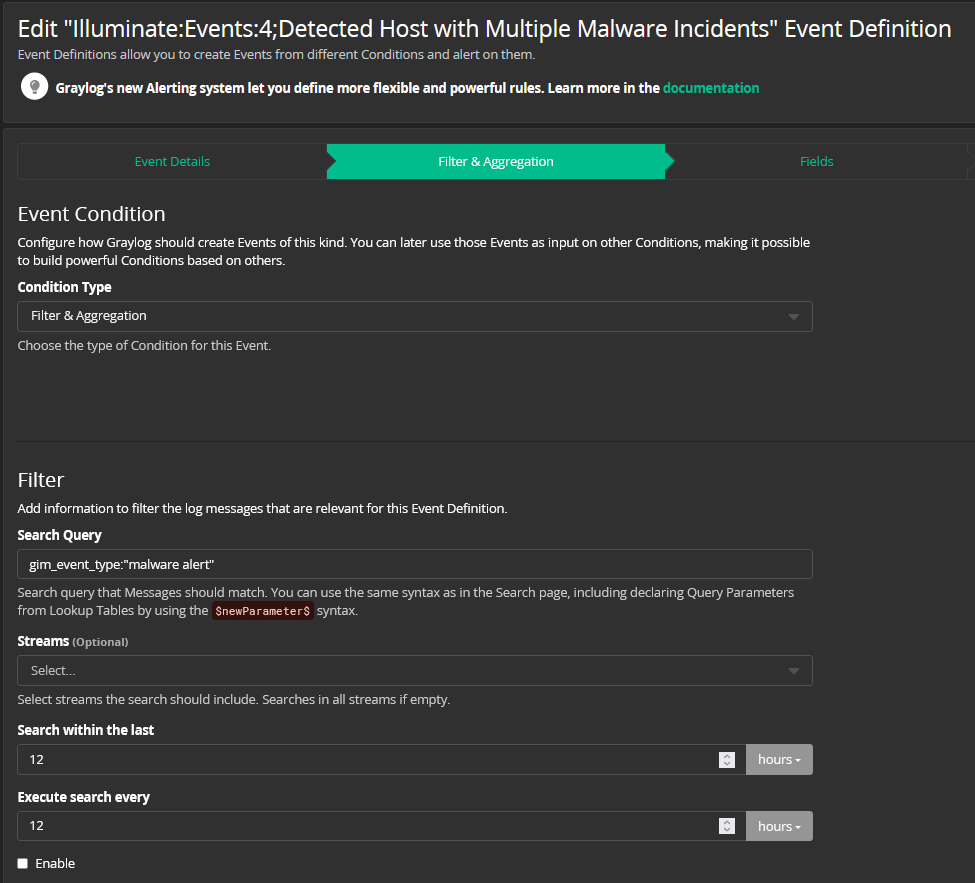
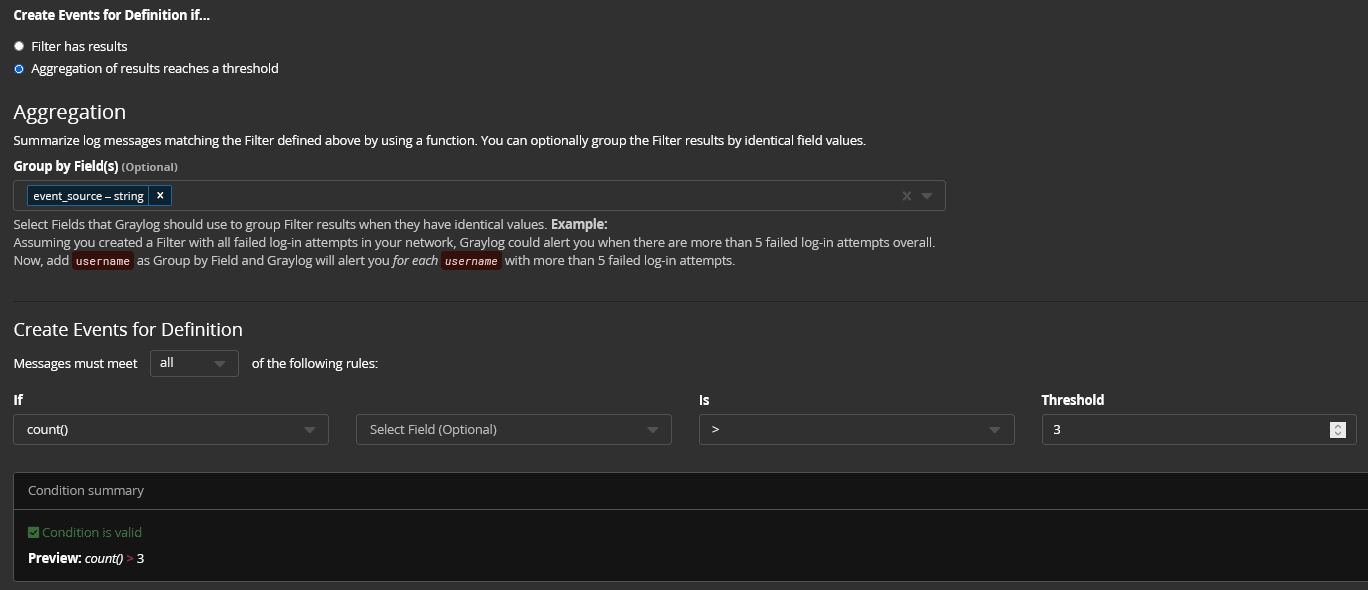
When the Event parameters are detected, the Alert fires.
ENDPOINT LOG DATA ENRICHMENT
Graylog also has threat intelligence plugins that include:
- AlienVault Open Threat Exchange
- Spamhaus DROP/EDROP lists
- ThreatFox IOC Tracker
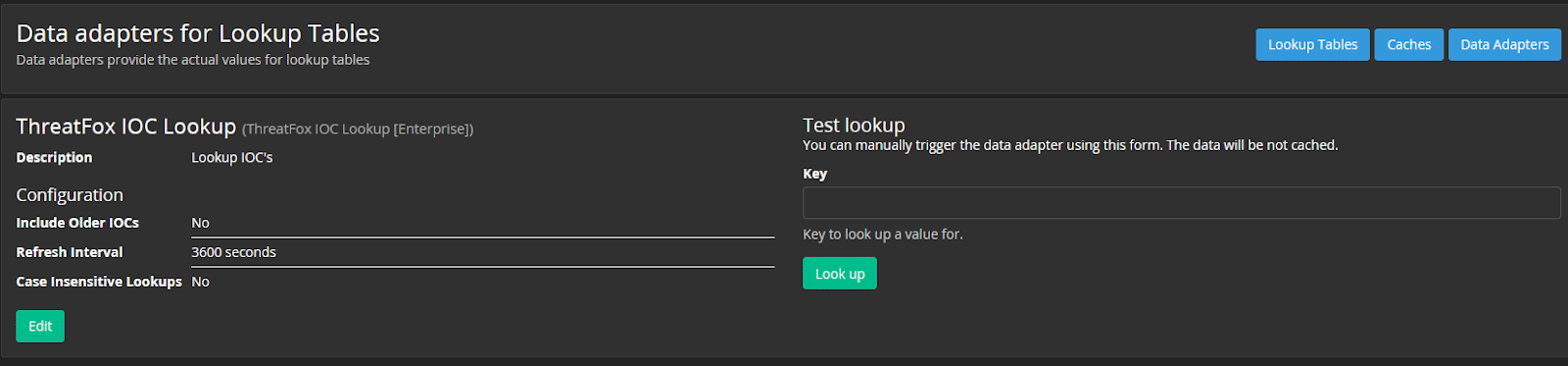
EASY AND AUTOMATED SEARCH
Most likely, you’re going to be trying to protect a lot of endpoints. Graylog’s search capabilities are easy to use. You can also save searches and run them regularly. Once you create a search and save it, you can turn it into a widget for quick visualization.
This can reduce key metrics like mean time to detect (MTTD) because you get at-a-glance visibility into trends and changes across your endpoints.
FINAL THOUGHTS
Whether using Graylog as your security monitoring solution or to optimize your SIEM, you can get better visibility into endpoint security. While cloud technologies and work-from-anywhere make it easier for most people to do their jobs, they make it more difficult for security analysts to do theirs.
Getting high fidelity alerting helps you spend more time securing and less time responding to false positives. If your company is looking to adopt a zero-trust security strategy, then Graylog can save you time and money by helping you monitor endpoint security more efficiently and effectively.



