If your company is like many others, it probably invested heavily in the Microsoft ecosystem. Microsoft has been around since the 1980s, focusing primarily on business technologies. It has a reputation for compatibility which gives you more purchasing options across devices and accessories. Unfortunately, this reach across corporate IT environments means that malicious actors target everything associated with Microsoft. For example, the November 2022 Patch Tuesday fixed six exploited zero-days and eleven “critical” vulnerabilities.
To protect yourself, you can collect and analyze Windows security event logs with these best practices.

What are Windows security event logs?
The Windows operating system stores detailed and in-depth records, called Windows event logs, about system, security, and application events. Windows security event logs, or security auditing logs, provide data about activities that can help you identify abnormal activity that could indicate a malicious actor gained unauthorized access to systems, networks, or devices.
To help detect security events, Microsoft build the Windows security auditing feature that you can use to:
- Monitor user activity
- Investigate incidents
- Perform forensic analysis
Two types of Windows security event logs exist:
- Success audit: security access attempt that is successful
- Failure audit: security access attempt that fails
Microsoft offers two types of security audit policies:
- Basic security audit: specified the categories of security-related events you want to audit
- Advanced security audit: similar categories as the basic security audits but recorded and applied differently
What are the categories of security audit events?
Microsoft defines nine basic security audit events. When you turn on auditing for a category, your Windows OS generates data that gives you insight into activities.
Audit account logon
These security events tell you when domain controllers or local computers authenticate a user’s access. The default setting is “success.”
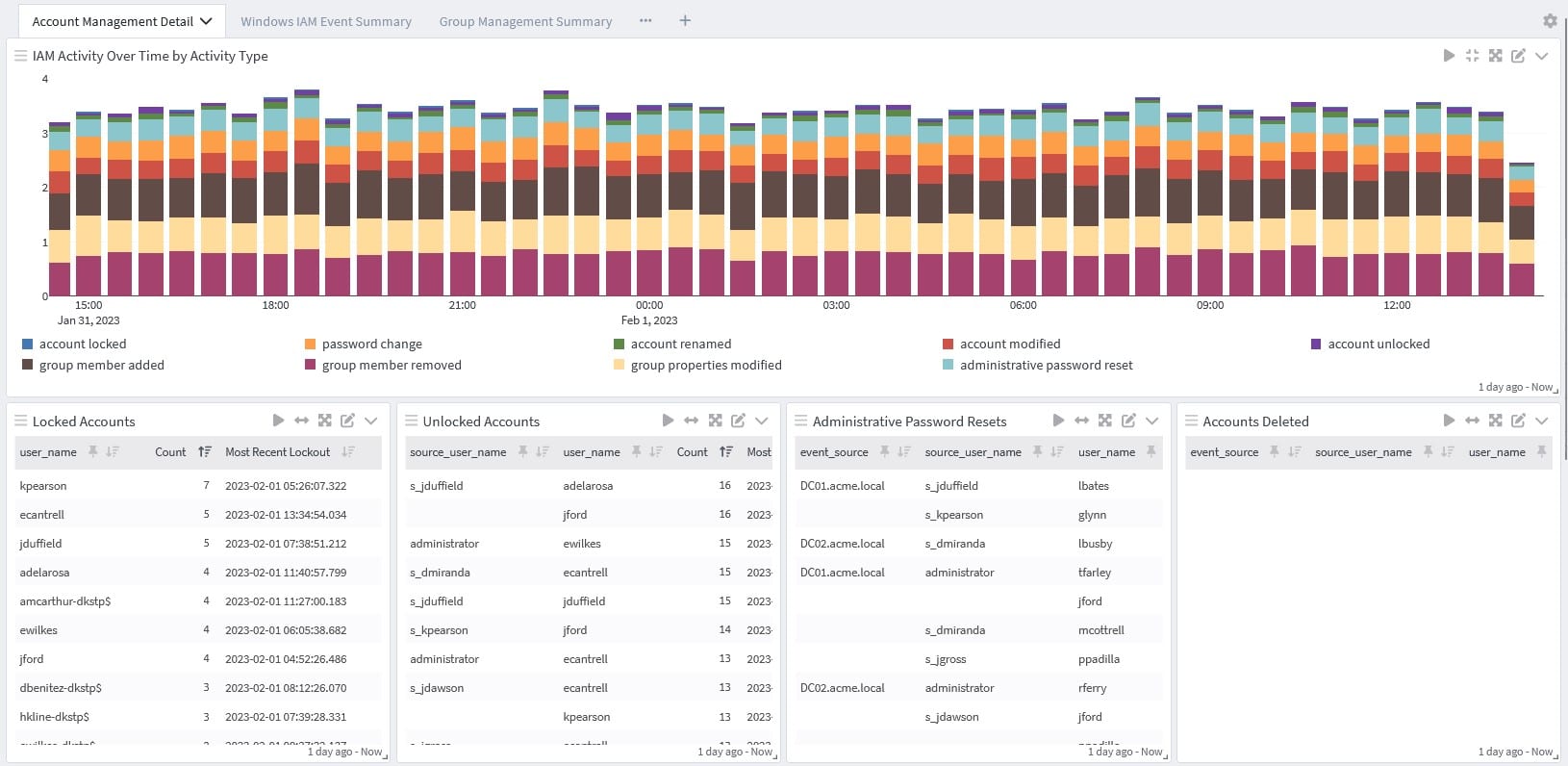
Audit account management
These audit logs tell you about account management activities for:
- User account: created, changed, deleted, renamed, disabled, or enabled
- Group: created, changed, or deleted
- Password: set or changed
The default settings are:
- Domain controller: success
- Member server: no auditing
Audit directory service access
This security audit log tells you whether a user accesses an Active Directory object with its own system access control list (SACL).
The default settings are:
- Domain controller: success
- Member server: undefined
Audit logon events
This security audit provides information about users logging on to or off from a device. Often, you will want to correlate these with account logon events.
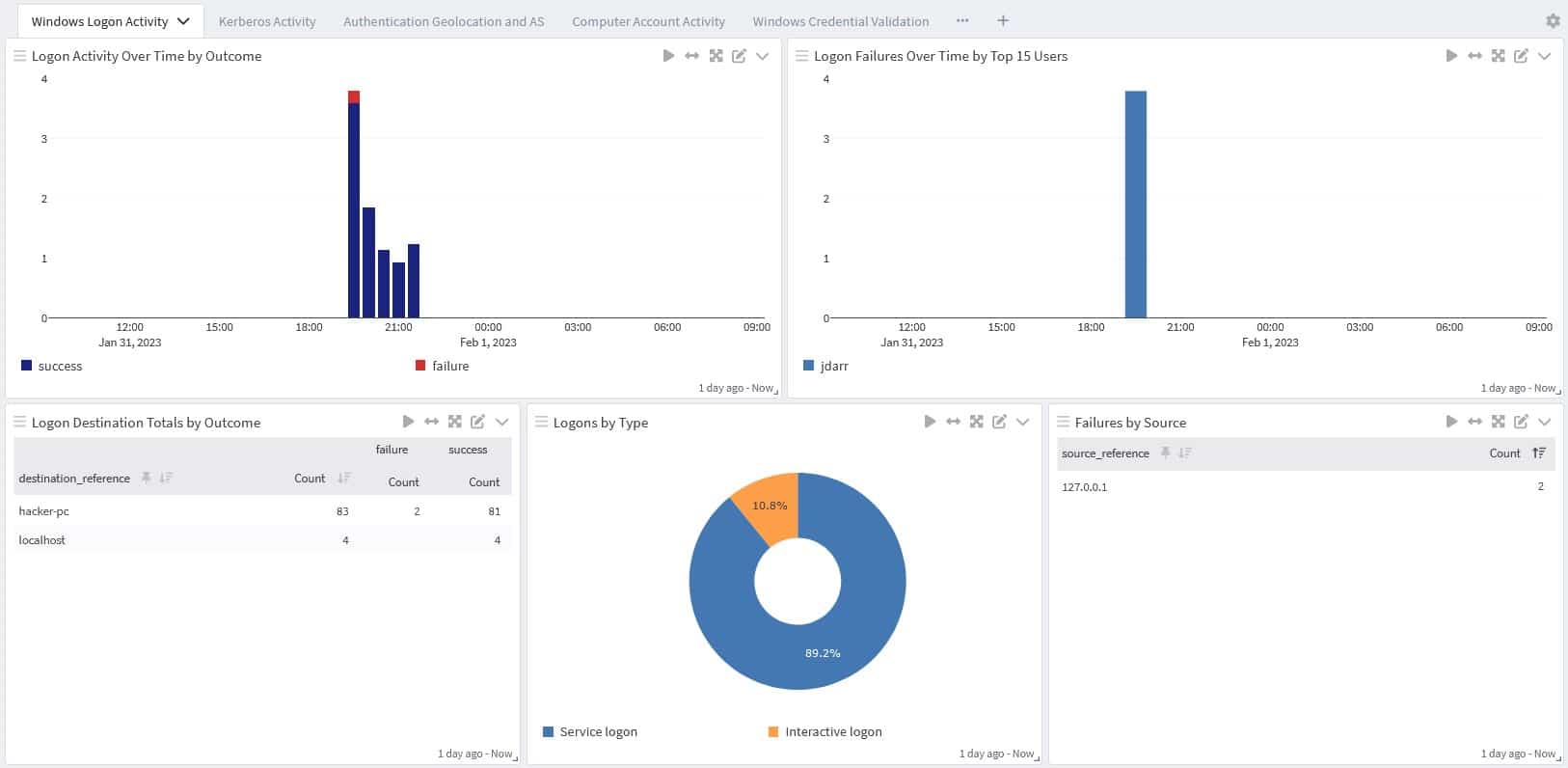
Audit object access
This security event log tells you when a user accesses objects that have their own SACL specified, like:
- Files
- Folders
- Registry keys
- Printers
The default setting is no auditing.
Audit policy change
This audit event tells you about changes to:
- User risks assignment policies
- Audit policies
- Trust policies
The default settings are:
- Domain controller: success
- Member server: no auditing
Audit privilege use
This security audit tells you every time a user exercises a user rights.
The default setting is “no auditing.”
Even if you turn on success audit or failure audit within this category, Microsoft makes you take additional steps to audit the following user rights because auditing them can slow down a computer:
- Bypass traverse checking
- Debug programs
- Create a token object
- Replace process level token
- Generate security audits
- Back up files and directories
- Restore files and directories
Audit process tracking
These security audits tell you about detailed tracking information for events like:
- Program activation
- Process exist
- Handle duplication
- Indirect object access
The default setting is “no auditing.”
Audit system events
These security audits tell you when users restart or shut down their computers. They also provide information about events that affect the system security or security log.
The default settings are:
- Domain controller: success
- Member server: no auditing
Windows Security Event Log Best Practices
Without planning, your Windows audit policies can generate high volumes of data that become overwhelming. To effectively use Windows security event lo gs for both security and compliance, you should follow some basic strategies.
Establish clear goals and objectives
At the highest level, you need to understand the logical grouping of resources and activiti es that require auditing.
Data and resources
Sensitive data is the foundation of your security auditing so you may want to consider how features in Microsoft SQL Server and Microsoft Server can help you monitor this information.
Some examples of resources classes and where they are stored include:
- Payroll data: Corp-Finance-1
- Patient medical records: MedRec-2
- Consumer health information: Web-Ext-1
Users
Some users require more monitoring than others. You may want to set audit policies for users with access to sensitive data, those who have privileged access, or external users.
Some examples of users might be:
- Account administrators: full privilege to change user accounts and security groups
- Finance department members: access to financial records subject to compliance requirements
- External partners: read/write access to certain project data and servers limited to only those resources
Devices
Depending on the device type, you may want to create unique audit policies to limit the amount of data generated. Your analysis and monitoring should consider:
- Device type: servers, laptops, mobile devices, and workstations
- Applications running: Microsoft Exchange Server, SQL Server, Forefront Identity Manager
- Operating system: current versus outdated version
- Data: high or low business value

Regulatory Requirements
If your company needs to comply with a regulation or industry framework, your security audit policies should align to these.
Map policy to groups of users, computers, and resources
Group Policies enable you to create defined user, computer, and resource groups to make applying security policies easier.
To get started using Group Policies you can:
- Create and edit them in the Group Policy Management Console (GPMC) then link a Group Policy Object (GPO) to Active Directory sites and domains, applying them to the users and computers you want to audit.
- Determine whether to enforce policies across the organization or only selected users and devices.
- Decide whether you want to use Advanced Audit Policies to various users, devices, networks, and systems
Choose audit settings
Once you define your requirements and start mapping your policies, you can use different audit settings to help achieve your goals.
Data and resource activity
Once you know where your company stores sensitive data, you can set audit policies like:
- Object Access\Audit File Share: Track who accessed the resource and where they accessed it from
- Object Access\Audit File System: Set OS audits to track user attempts to access file system objects, like files and folders, that have configures SACLs
- Object Access\Audit Handle Manipulation: Set OS audits to track when an object’s handle is opened or closed
- Global Object Access Auditing: Apply a global system access control SACL that cannot be overridden or circumvented to objects that must comply with data protection laws
User activity
In a world where zero trust architectures (ZTA) are increasingly important, monitoring user activity is critical.
Some security audit settings that you might want to use include:
- Account Logon\Audit Credential Validation: Track successful and unsuccessful sign-in attempts
- Detailed Tracking\Audit Process Creation and Detailed Tracking\Audit Process Termination: Monitor when users open and close applications on a computer
- DS Access\Audit Directory Service Access and DS Access\Audit Directory Service Changes: Monitors users’ attempts to access, create, modify, delete, move, or undelete Active Directory Domain Services (AD DS) objects
- Logon/Logoff\Audit Account Lockout: Identify when users attempt to sign into an account that was locked out
- Logon/Logoff\Audit Logoff and Logon/Logoff\Audit Logon: Track users logon and logoff events
- Logon/Logoff\Audit Special Logon: Track users with privileged access
- Object Access\Audit Certification Services: Monitor activities on devices that host Active Directory Certificate Services (AD CS) role services
- Object Access\Audit Registry: Track changes to registry for objects with configures SACLs based on defined access type, like write, read, or modify
- Object Access\Audit SAM: Track changes to user accounts and security descriptors in the Security Accounts Manager (SAM)
- Privilege Use\Audit Sensitive Privilege Use: Track privileged access across one or more systems
Network activity
Network activity monitoring can detect issues not covered by data or user monitoring categories.
Some security audit settings that might help you are:
- Account Management: Track attempts to make changes to user or computer accounts, security groups, or distribution groups
- Account Logon\Audit Kerberos Authentication Service and Account Logon\Audit Kerberos Service Ticket Operations: Track activities related to domain account credential use
- Account Logon\Audit Other Account Logon Events: Track network activities like Remote Desktop connections, wired network connections, and wireless connections
- DS Access: track AD S services that manage access to and modification of domain controller configurations
- Logon/Logoff\Audit IPsec Extended Mode, Logon/Logoff\Audit IPsec Main Mode, and Logon/Logoff\Audit IPsec Quick Mode: Track external and remote employee network use
- Logon/Logoff\Audit Network Policy Server: Monitor effectiveness of RADIUS (IAS) and Network Access Protection (NAP) policies
- Policy Change: Track changes to security policies on local computers or networks
- Policy Change\Audit Audit Policy Change: Track changes to audit policies
- Policy Change\Audit Filtering Platform Policy Change: Track changes to IP security policies
- Policy Change\Audit MPSSVC Rule-Level Policy Change: Track when OS generates audit events for changes to Windows Firewall policy rules
Monitor and manage security auditing
Even in a relatively small IT environment, networks generate high volumes of security event logs that you need to monitor and manage. To get the full value from your Windows security event logs, you must decide how you plan to collect, aggregate, store, correlate, and analyze the data. For example, you need to decide whether you plan to store everything on a local computer or in a central console.
When planning your storage, you need to determine how you plan to manage event log size, including whether to:
- Overwrite: Default option that only saves the newest events
- Archive: Stores historic data
- Clear logs manually: Stops collecting audit data when log files reach maximum size which can lead to important data loss if you don’t review the data regularly
Additional security event log settings that you can find in GPMC location Computer Configuration\Administrative Templates\Windows Components\Event Log Service\Security include:
- Maximum Log Size: 20 MG default with ability to customize up to 2 TB
- Log Access: Limiting user accounts and privileges
- Retain old events: Activity when log files reach their maximum size
- Backup log automatically when full: Activity when log file reaches maximum size only if choosing to retain old events
Graylog Security: Centralized Log Management for Windows Event Security Logging
Graylog Security and our Windows Event Logs Content Pack applies normalization of common event log fields to all Windows event log messages that enrich critical security event log IDs. Graylog ingests logs with both NXLog community edition or Winlogbeat from your Windows event logs into Graylog.
With Graylog, you can collect, aggregate, correlate, and analyze all your Windows security event logs in a single location to maximize your data’s value. With Graylog Extended Log Format (GELF), you can ingest log data from any source and normalize it for enhanced observability and visibility. By bringing together all your security and operations activities within Graylog, you make quantifiable gains in your operational and cybersecurity postures by making sense of your data.
To see how Graylog can help you, contact us today.




