As you’re settling in with your Monday morning coffee, your email pings. The subject line reads, “Documentation Request.” With the internal sigh that only happens on a Monday morning when compliance is about to change your entire to-do list, you remember it’s that time of the year again. You need to pull together the documentation for your external auditor as part of your annual ISO 27000 and ISO 27001 audit. The good news is that centralized log management helps you meet many of the ISO 27000 and ISO 27001 requirements.
What are ISO 27000 and ISO 27001?
The International Organizations for Standardization (ISO) is an internationally recognized non-profit that sets standards across technology and manufacturing. Its two primary information security standards are ISO 27000:2018 and ISO 27001:2022. In 2022, ISO updated the 270001 standard, and and update to 27000:2018 is currently under development with no specified publication date.
What is ISO 27000:2018?
ISO 27000 is the set of fundamental principles and objectives for your security program. These include:
- Information security awareness
- Responsibility assignment
- Management commitment
- Societal value enhancement
- Risk assessment and risk tolerance review
- Incorporating security as essential to networks and systems
- Active security incident detection and prevention
- Comprehensive approach to information security management
What is ISO 27001:2022?
ISO 27001 gives you the set of practices, including policies and procedures, for establishing an Information Security Management System (ISMS), listing the following categories:
- Context of the organization: Understanding the organization, its context, and interested parties’ needs and expectations as well as determining ISMS scope
- Leadership: Leadership commitment, policy, organizational roles, responsibilities, and authorities
- Planning: Identifying actions to address risks and opportunities and defining security objectives and how to achieve them
- Support: Resources, competence, awareness, communication, and documentation
- Operation: Operational planning and control, information security risk assessment and risk treatment
- Performance evaluation: Monitoring, measurement, analysis, and evaluation, internal audit, and management review
- Improvement: Continual improvement, nonconformity, and corrective action
Bringing ISO 27000 and 27001 together
The use of the word “system” in the ISO 27001 ISMS may include having technologies, but it’s really about creating repeatable steps for:
- Understanding risk
- Establishing a risk tolerance
- Setting technical controls
- Monitoring controls’ effectiveness
- Responding to incidents
- Communicating across the organization
Basically, without the written policies and repeatable processes in ISO 27001, you won’t be able to prove that you’ve achieved the desired data security outcomes in ISO 27000.
Why comply with ISO standards?
Your organization might choose ISO as its compliance standard for many reasons. Often, these reasons are based on business objectives like industry or customer requirements.
On the other hand, ISO is a valuable standard to follow from an IT and security perspective. Some reasons to consider ISO compliance include:
- Global recognition: The “I” in “ISO” is for international recognition, and it’s a standard that you can use to provide assurance across multiple geographic regions.
- Risk-based approach: No two organizations are the same, and ISO takes a risk-based approach that allows flexibility.
- Regulatory compliance: ISO is a standard with no fines or penalties, but many regulations follow ISO best practices.
Wait, did you say regulatory compliance?
Yes, ISO 27000-series can help you meet critical regulatory compliance standards. Is it a complete program? Not always, but it does help you set the baselines. Once you set controls for ISO 27000-series, you can map those to several different regulations.
For example, the ISO 27000-series can help you comply with:
- General Data Protection Regulation (GDPR)
- Health Insurance Portability and Accountability Act (HIPAA)
- Gramm-Leach-Bliley Act (GLBA)
- Sarbanes-Oxley Act (SOX)
So, where do logs and compliance monitoring fit into ISO 27000-series compliance?
ISO compliance isn’t easy. The update to 27001 now includes technologies that weren’t specifically mentioned in the previous iterations, like cloud-based resources.
The hidden gem in ISO 27000-series is ISO 27002:2022, Information security, cybersecurity
and privacy protection — Information security controls . This document provides insight into the technical controls that you can use to meet the broader requirements.
ISO references both “audit logs” and “event logs.” This makes sense. After all, audit logs and event logs consist of the pieces of data that every user and technology generates when an action occurs. Log data and log files give you the real-time visibility and documentation needed to detect, investigate, and respond to a security event.
In ISO 27002:2013, the technical document included Logging and Monitoring within the Operations Security category, with additional mentions of audit and event logs sprinkled throughout the rest of the document. In ISO 27002:2022, the logging and monitoring requirements fall under the category “Technical controls.”
8.15 Logging
The document notes that in general, organizations should generate evidence, ensure log information integrity, prevent unauthorized access, and identify information security events. More specifically, it states that event logs should include, for each event, the following when applicable:
- UserID
- System activities
- Dates, times, and details of relevant events
- Devicide identity, system identifier and location
- Network addresses and protocols
It further suggests the following events that a company should include in its logging:
- Successful and rejected system access attempts
- Successful and rejected data and other resource access attempt
- Changes to system configurations
- Privilege use
- Utility program and application use
- Files accessed and access type, including deletion of important data files
- Access control system alarms
- Security system activation and deactivation, like anti-virus or intrusion detection systems
- Identity creation, modification, or deletion
- User application transactions executed
Under log analysis, ISO 27002:2022 identifies the following monitoring activities that can help identify and analyze anomalous behavior:
- Successful and unsuccessful access attempts to protected resources, like domain name system (DNS) servers, web portals, or file shares
- DNS logs for outbound network connections to malicious servers
- Service provider usage reports that may contain unusual patterns of activity
- Event logs for physical monitoring, like entrance and exit badge use
- Correlating logs
8.16 Monitoring activities
The logging that you implement directly enables you to monitor networks, systems, and applications for anomalous behavior. According to ISO, the tools organizations implement to achieve continuous monitoring should have the following capabilities:
- Handling large amounts of data
- Adapting to change threat landscape
- Allowing for real-time notification
- Recognizing specific signature and data
- Recognizing data, network, or application behavior patterns
According to the document, you should consider including the following behaviors in your monitoring system:
- Outbound and inbound network, system, and application traffic
- Access to assets and services like systems, servers, networking equipment, monitoring system, and critical applications
- Critical or administrative level system and network configuration files
- Security tool logs, like antivirus, intrusion detection systems, intrusion prevention systems, web filters, firewalls, and data leak prevention tools
- System and network activity event logs
- Reviewing that executed code is authorized to run and no tampering has occurred
- Resource use and performance
As part of monitoring, organizations should identify and set baselines for abnormal activity like:
- Unplanned process or application termination
- Malicious activity or traffic from known maliciou sIP addresses or network domains
- Known attack characteristics
- Unusual system behavior, like keystroke logging or process injection
- Bottlenecks and overloads, like latency levels or network jitter
- Unauthorized access to systems or information, both actual and attempted
- Unauthorized scans of business applications, systems, and networks
- Successful and unsuccessful access attempts at protected resources
- Unusual user and system behavior
Compliance Monitoring for ISO 27000-series
As part of your security and compliance monitoring, your automated monitoring software should generate alerts based on predefine thresholds so that your security team can respond to them. Additionally, your security team needs a tool that enables them to minimize a security incident’s impact with rapid investigation capabilities.
With a threat detection and incident response (TDIR) solution, your security and compliance teams can collaborate more effectively, especially when you create reports that senior leadership can use to understand risk.
Access control
A key technical control for mitigating risk is restricting user access to resources. However, you can’t do this manually with all the different connected technologies you have. This is even more difficult when you’re looking to manage privileged access, also mentioned in ISO 27001.
Centralized log management gives you a way to track and monitor user activities. This gives you the documentation needed to prove that you have the controls in place and that they’re working.
Physical and environmental security
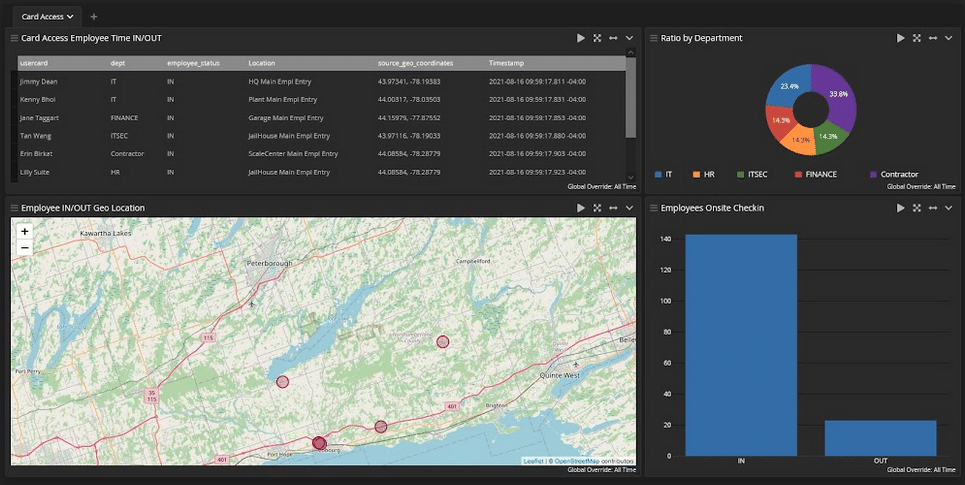
At first glance, this one may not seem to be related to centralized log management. However, when you stop and think about how you secure offices, rooms, and facilities, it makes more sense. You’re probably using card access instead of old-fashioned metal keys, especially for employees.
Centralized log management can help you track who physically accesses locations.
Information security incident management
Under this control, you need to detect, report, investigate, and respond to threats in your environment. With complex environments, this can feel overwhelming. In fact, alert fatigue is really real. The high volumes of logs generated across on-premises, multi-cloud, and hybrid environments create too many false positives for most security teams.
On the other hand, centralized log management makes this process easier. Since a log analysis solution collects, aggregates, correlates, and analyzes all actions in the environment, you can set high-fidelity alerts. With a logging system, you get better detection and response capabilities and forensic analysis functionality.
Further, you can quickly investigate these alerts while documenting your processes.

Information security reviews
Ahh, and this is what brought you to where you are today. The information security reviews – or in normal people’s terms, “audits” – mean that managers need to review compliance within their area of responsibility.
In other words, documentation.
Centralized log management helps with this as well. With the right solution, you can create dashboards that give the information people need in the way they need it. This means using things like graphs and charts.
Even better for you? You can schedule reports and forward them to those who need the information.
Graylog for ISO Compliance
Graylog gives you the centralized log management solution that helps you get compliant – and stay that way. We make it easy to visualize and explore data so that you can meet the technical requirements of ISO 27001 for audit logging. You can flag people and/or assets based on compliance requirements to not spend as much time on reporting.



