Centralized Log Management for the Digital Operational Resilience Act (DORA)

The financial services industry has been a threat actor target since before digital transformation was even a term. Further, the financial services organizations find themselves continuously under scrutiny. As members of a highly regulated industry, these companies need to comply with various laws to ensure that they effectively protect sensitive data. The adoption of […]
Understanding The Cyber Resilience Act (CRA)

The 2020 EU Cybersecurity Strategy, published by the European Commission and the High Representative of the Union for Foreign Affairs and Security Policy, aimed to establish safeguards against security risks arising from increased digital connectivity. As part of the strategy, the strategy included updates to Directive (EU) 2022/2555 on measures for a high common level […]
Meeting Compliance Regulations with SIEM and Logging

SIEM and log management provide security to your organization; these tools allow your security analysts to track events such as potential and successful breaches of your system and react accordingly. Usually, it doesn’t matter how you ensure your organizational safety as long as you do. However, is your organization in the health, financial, or educational […]
Centralized Log Management for TISAX Compliance

What is the Trusted Information Security Assessment Exchange (TISAX)? The Trusted Information Security Assessment Exchange (TISAX) is the certification process for engaging in the Verband der Automobilindustrie (VDA), the German Association of the Automotive Industry, Information Security Assessment (ISA). The ENX Association, a collection of automobile manufacturers, suppliers, and four national automotive associations, established TISAX […]
Centralized Log Management for SOX Compliance

Over twenty years ago, a series of corporate financial scandals set off a chain reaction, culminating in criminal convictions and new legislation. After uncovering accounting fraud across public companies like Enron, WorldCom, and Tyco, the US Congress enacted the Sarbanes-Oxley Act of 2002 (SOX). As companies have become more reliant on technology, the Securities and […]
Understanding the ISO 27000 Series Changes
David Bowie once sang, “ch-ch-ch-changes, turn and face the strange.” While the changes to ISO 27000-series may look strange, they’re primarily a configuration and modernization of the same standard you already know. The standard’s format looks entirely different, but most of your current controls will remain the same. When you understand the underlying philosophical shift, […]
Log Management for CMMC
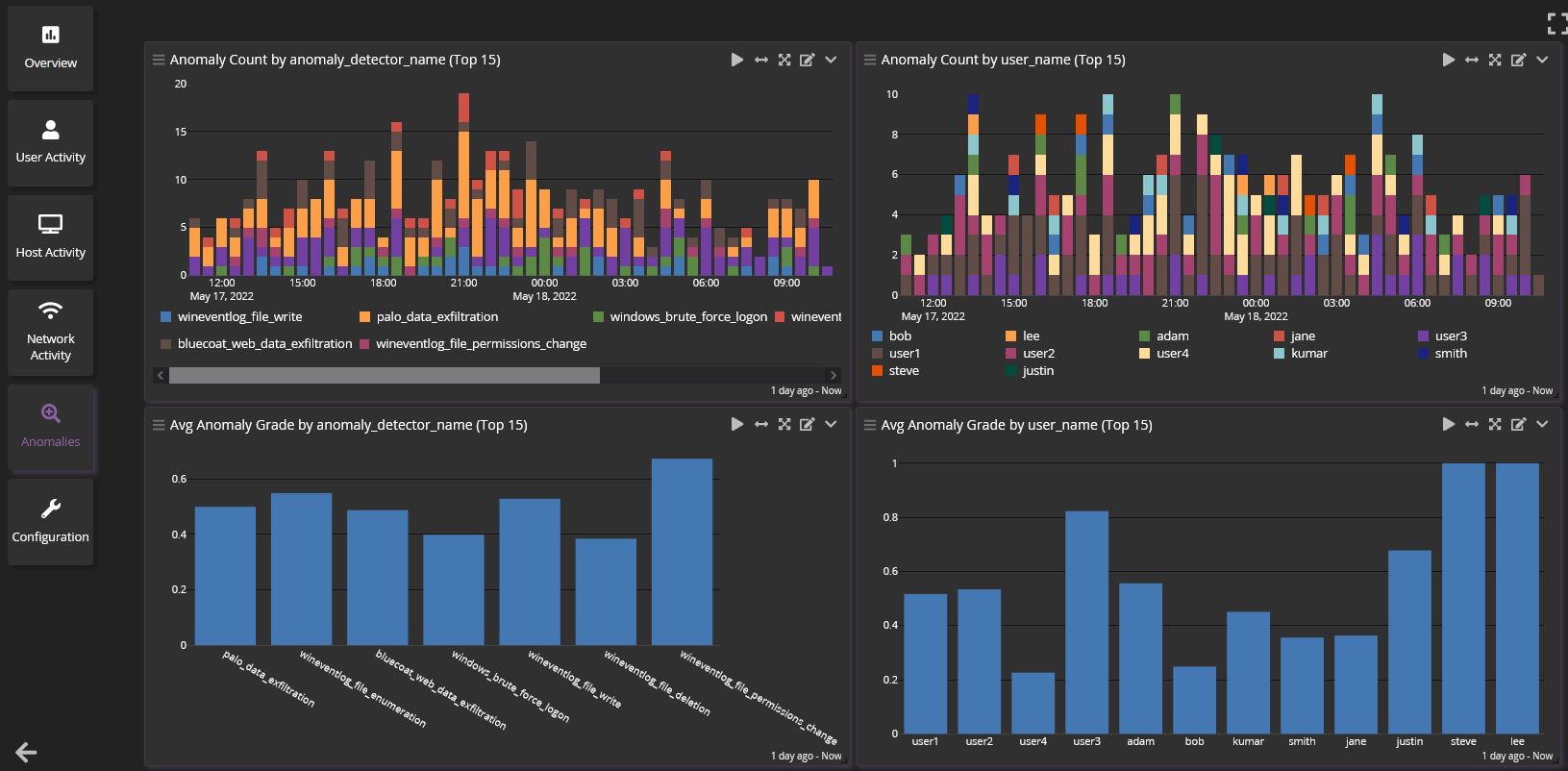
The Cybersecurity Maturity Model Certification (CMMC) seeks to help secure the Defense Industrial Base (DIB) supply chain by requiring contractors and subcontractors to standardize their security controls. With CMMC 2.0, the Office of the Under Secretary of the Defense Acquisition and Sustainment (OUSD(A&S)) designated National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171 […]
Log Management for Shared Responsibility Model Compliance
Adoption of Infrastructure-as-a-Service (IaaS), Platform-as-a-Service (PaaS), and Software-as-a-Service (SaaS) applications means navigating the Shared Responsibility Model. Under the Shared Responsibility Model, the cloud services provider takes care of the infrastructure’s security, but you need to secure what happens within that environment. According to the State of Cloud Native Security Report, 50% of companies surveyed reported […]


