In life, you get a lot of different alerts. Your bank may send emails or texts about normal account activities, like privacy notices, product updates, or account statements. It also sends alerts when someone fraudulently makes a purchase with your credit card. You can ignore most of the normal messages, but you need to pay attention to the fraud alerts. Security is the same way. Since your systems can generate terabytes of data everyday, your security tools can fire high volumes of alerts, leaving you overwhelmed.
With risk-based alerts, you can reduce alert fatigue by incorporating additional security information, giving you a way to focus on high-value issues.
What is risk-based monitoring in cybersecurity?
In cybersecurity, a risk-based approach to monitoring means that the organization assesses the business impact and likelihood of an attack against various:
- People
- Devices
- Resources
- Networks
- Data
After identifying those people and assets who pose the highest risk, the security team often incorporates threat intelligence to help prioritize monitoring and remediation activities. For example, many security teams take a risk-based approach to vulnerability management by appling security updates to critical assets first.
What is risk-based alerting?
Risk-based alerting (RBA) means that the detection logic incorporates additional attributes to reduce the overall number of alerts generated while enhancing them with meaningful data.
When security analysts write these alerts, they may include security metadata including:
- Exploitability, like an asset’s distance from the public internet
- Impact, like users with privileged access
- Likelihood, like incorporating threat intelligence
- Asset criticality, like databases storing personally identifiable information (PII)
With RBA, security analysts can align their monitoring activities to the organization’s risk assessment more effectively. Further, when security teams have a solution that enables threat hunting, they can proactively use these enhanced rules to detect suspicious activity in their systems.
What are the benefits of risk-based alerting?
While the frontend process of building risk-based detection rules can take some time, the overall benefits you get from them are worth it.
Reduced Alert Fatigue
Alert fatigue is a real issue for anyone working in cybersecurity, and the problem has only gotten worse over the last few years. According to research, security teams are overwhelmed with inaccurate or unnecessary alerts, struggling to prioritize and review them effectively with:
- 59% of respondents saying they receive more than 500 cloud security alerts per day
- 43% saying more than 40% of their alerts are false positives
- 56% saying they spend more than 20% of their day reviewing alerts and deciding which ones should be dealt with first
- 55% saying that critical alerts are being missed
With risk-based alerting, you can correlate multiple events to generate fewer false positives. By reducing the overall number of alerts and making them more valuable, your security team can prioritize their responses better.
Faster Investigation Times
With fewer alerts and better prioritization capabilities, your security team can investigate incidents faster. With more attributes added to the alert, the security team has a way to focus their investigations. For example, consider this risk-based alert that monitors for people who recently tendered their resignation who make changes to Active Directory:
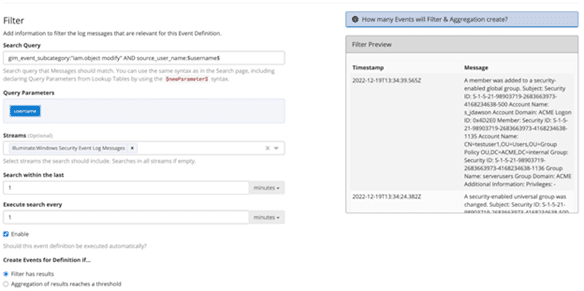
By linking the organization’s HR information to its Active Directory, the security team has a way to monitor for a specific, high-risk use case more precisely. When the system generates the alert, they also have all the information necessary to investigate the root cause.
Improved Security Metrics
Proving your security program’s effectiveness typically includes the following metrics:
- Mean Time to Detect (MTTD)
- Mean Time to Investigate (MTTI)
- Mean Time to Contain (MTTC)
- Mean Time to Recover or Mean Time to Remediate (MTTR)
With risk-based alerts, you reduce all of these times, ultimately improving the metrics. You can think of it like a chain reaction. With better detection, security teams work with better information and focus. With fewer overall alerts, analysts can investigate them faster. The faster they can find the incident’s root cause, the sooner they can contain the attacker, remediate the system, and get everything back online.
Who benefits from risk-based alerts?
Even though risk-based alerts sit under the security function, various people across your organization benefit from them.
Security Analysts
With better information, your security analysts can do their jobs more effectively and efficiently. Since they’re not spending as much time chasing down false alerts, they can focus their energy on high-impact activities like threat hunting. Further, when security analysts have the tools to do their job well, they’re more likely to stay with the company, reducing employee turnover.
IT Help Desk
When something goes wrong in your environment, the help desk is the first place users turn. Often, security issues and operational issues mimic one another. For example, a Distributed Denial of Service (DDoS) attack slows down your network, but a network device configuration issue can have the same outcome. With security teams detecting and responding to incidents faster, your IT help desk gets fewer calls.
Senior Leadership
Senior leadership is responsible for overseeing the organization’s compliance posture and making data-driven decisions about the cybersecurity program. Your risk assessment is the basis of your compliance program. With risk-based alerts, you can align your security and compliance objectives more effectively. Further, leadership needs to understand the program’s strengths and weaknesses to make meaningful decisions about security investments. When you map risk-based alerts to frameworks like MITRE ATT&CK, you gain visibility into potential tooling gaps.
Graylog Security: Risk-Based, High Fidelity Alerts to Mature Your Program
With Graylog Security, you can build risk-based, high fidelity alerts based on your organization’s unique technology stack and risk profile. Our cloud-native capabilities, intuitive UI, and out-of-the-box content enable you to build the security program you need without paying for the functionalities you don’t use. Using our prebuilt content, you gain immediate value from your logs wit search templates, dashboards, correlated alerts, dynamic lookup tables, and more.
Built with end-users in mind, Graylog’s platform empowers people of all skill levels. You don’t need special skills or engineers to build the risk-based alerts so you can uplevel your security with your current team, reducing labor costs often associated with complex SIEMs.
To learn how Graylog Security can help you improve your security posture with risk-based alerts, contact us today.



