The Windows System Monitor (Sysmon) is one of the chattiest tools. With all the information coming in, it can be difficult and expensive to use it efficiently. However, the Graylog Illuminate package gives you a way to fine-tune it so that you can get better data and manage your ingestion rate better.
UNDERSTANDING THE PRIMARY SECURITY BENEFITS OF USING SYSMON
Sysmon gives you awareness of what’s going on in your endpoints. According to the 2021 Data Breach Investigations Report (DBIR), phishing remained one of the top Action varieties leading to breaches in 2020. Further, phishing increased to 36% of 2020 breaches, up from 25% in 2019.
Being aware of activities going on in your endpoints is more important than ever. You have to have visibility on your workstations to detect these breaches or attempted breaches as early as possible. Without endpoint visibility, you have a large gap in monitoring, root cause analysis, and troubleshooting.
VISIBILITY
Sysmon, if enabled appropriately, can give you a list of activities with the context necessary to respond properly. For example, Sysmon can:
- track process activity
- network activity
- DNS activity for a process
- processes being launched
- processes attempting to modify access
- modification or access to other processes
- WMI activity commonly used malware
If you’re only relying on your primary defenses and network data without including endpoint activity, you don’t have complete visibility. For example, it’s very hard to troubleshoot and understand where a PDF came from or what endpoint downloaded malware.
Using Sysmon, you can track processes running in the background. If you know that some processes running applications or in a Windows workstation’s memory indicate an attack, you can receive notifications in Sysmon.
INTEGRATION
Sysmon’s value lies in the ability to add context to other data you’re already collecting. Suppose you’re running Winlogbeat natively already on Windows. In that case, Sysmon will create an additional event log to add the configured events to and can be collected by Winlogbeat with a minor configuration change. Winlogbeat and NXLog are primary vehicles for forwarding Sysmon logs. You can install these third-party software packages on Windows and then use them to enhance the other information you’re already collecting.
3 PRIMARY CHALLENGES WITH MANAGING SYSMON
While Sysmon gives a lot of insight with its applications and services logs, it’s also challenging to get started with.
SKILL
Downloading Sysmon doesn’t require a lot of skill, but configuring your build requires a certain knowledge base.
For example, you need to make decisions about:
- Configuration: what event logs do you want and how to prevent unpredictable logs
- Installation: which machine(s) to install Sysmon on
- Deployment: what endpoints to collect logs from and run tests in advance
TIME
Even with someone who has the right skills, getting your Sysmon configuration up and running can take time. Deciding what to ingest and fine-tune the deployment can easily take a month, if not longer.
MISSED LOGS
Meanwhile, as you build out the relevant understanding of what’s coming at you and then build it, you’re losing visibility into activity happening on your endpoints. Whether this takes a month or three months, you’re going to miss a lot of events.
VOLUME
Sysmon is going to generate a lot of logs. While its value comes from its chattiness, you need to fine-tune your system so that you’re getting only the data you need. Many teams struggle with the volume of data and keeping it under control.
USING THE GRAYLOG ILLUMINATE CONTENT PACK FOR SYSMON
With Graylog Illuminate’s content pack for Sysmon, you can collect and analyze your logs in a centralized location.
DASHBOARDS
We’ve built aggregations with the Illuminate Sysmon content, including dashboards that help you get through the data. This feature lets you look at your environment, identify outliers, and immediately or rapidly understand what’s going on with all of your Windows systems, including workstations and servers.
Example
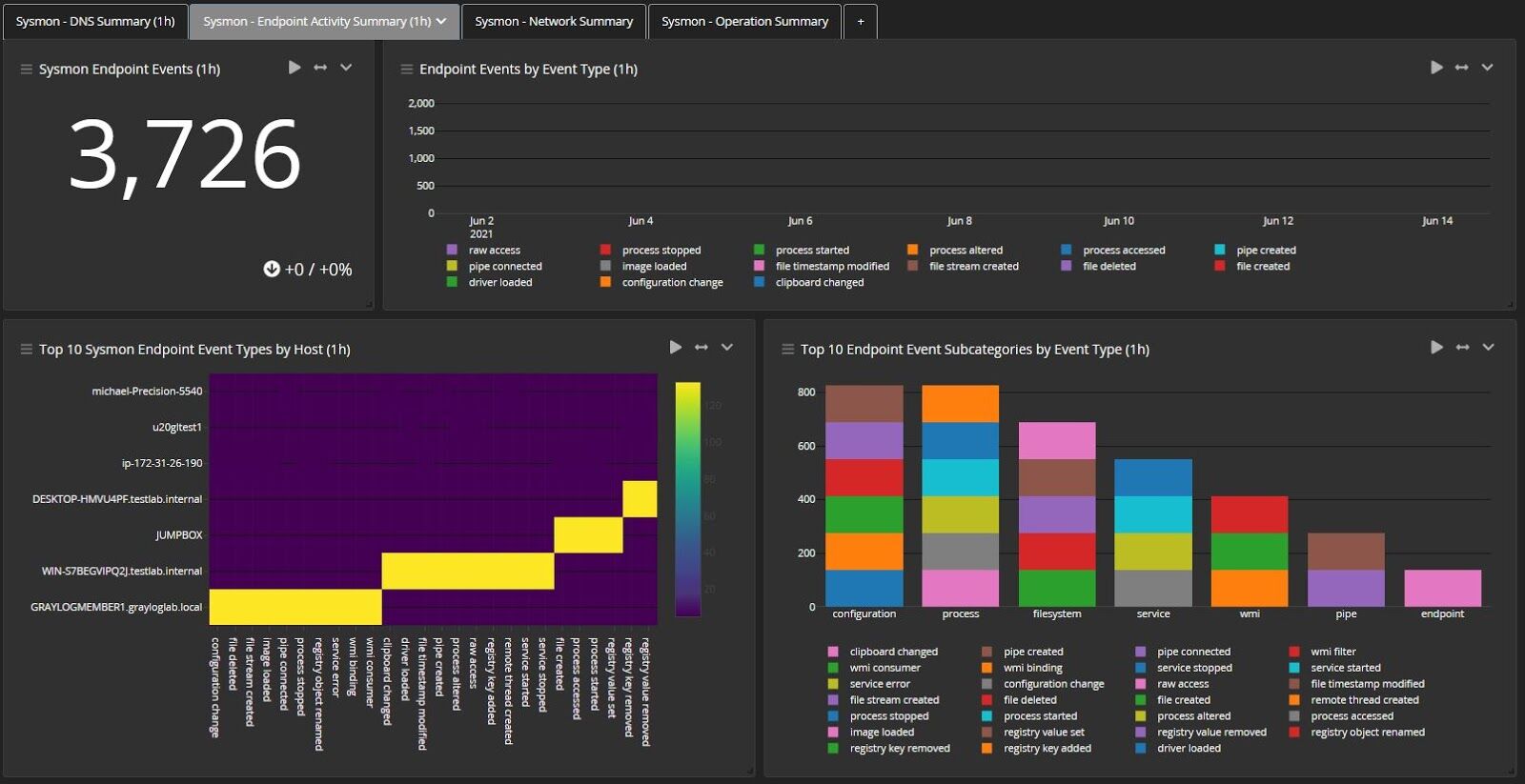
With the dashboards we’ve built, you can drill into activities on an individual workstation and whatever logs spawned due to this activity. This data gives you clear evidence in those dashboards for those individual workflows.
PARSING RULES
Our Illuminate Sysmon content pack includes almost 40 parsing rules for all the bits of information you need. These rules give you a good head start with some key identifications that provide you with visibility into the activity Sysmon tracks. With the content pack, you don’t need someone who can create the rules, and you eliminate the time it takes to configure them.
The rules cover almost everything Sysmon generates, up to the most recent version to make sure that you can process every event.
MANAGE DATA AND REDUCE NOISE
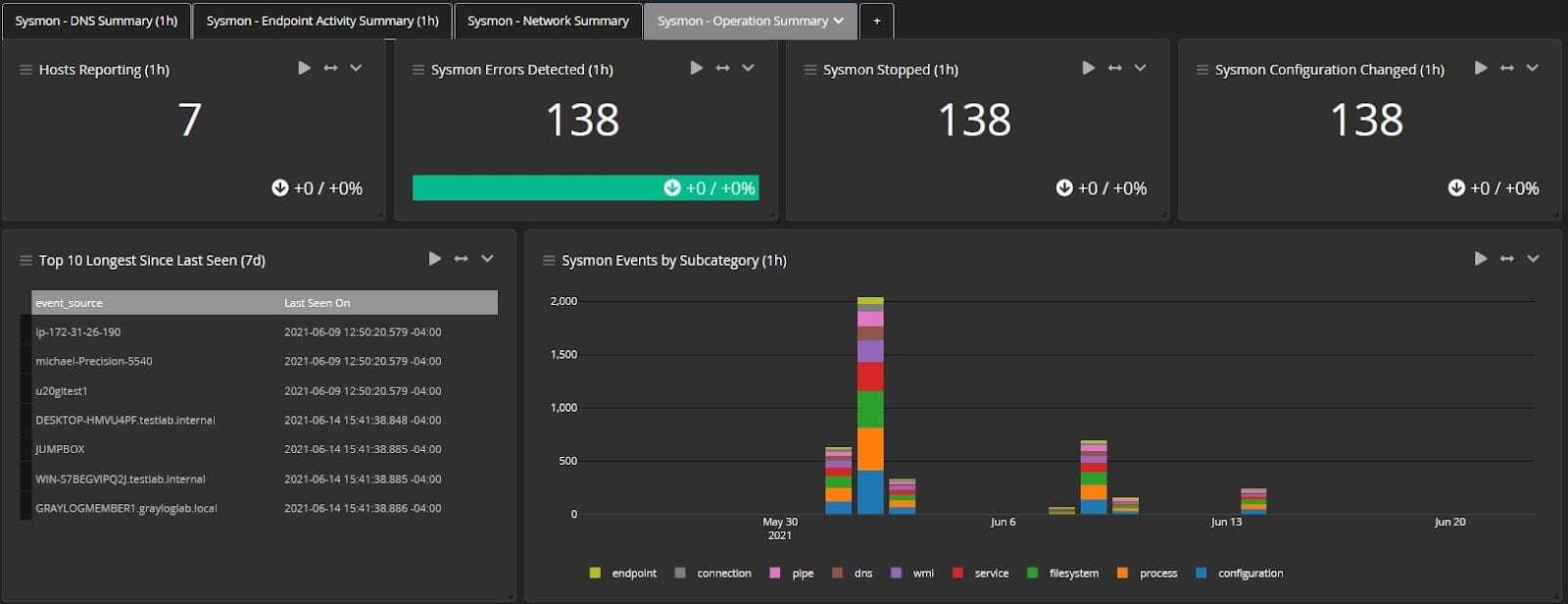
One of the things our dashboards will do is help you tune Sysmon. We built aggregations that reduce the time it takes to tune Sysmon and the excess “noise” and traffic. These aggregations mean you can configure it properly to accelerate the amount of high-value data/
Example
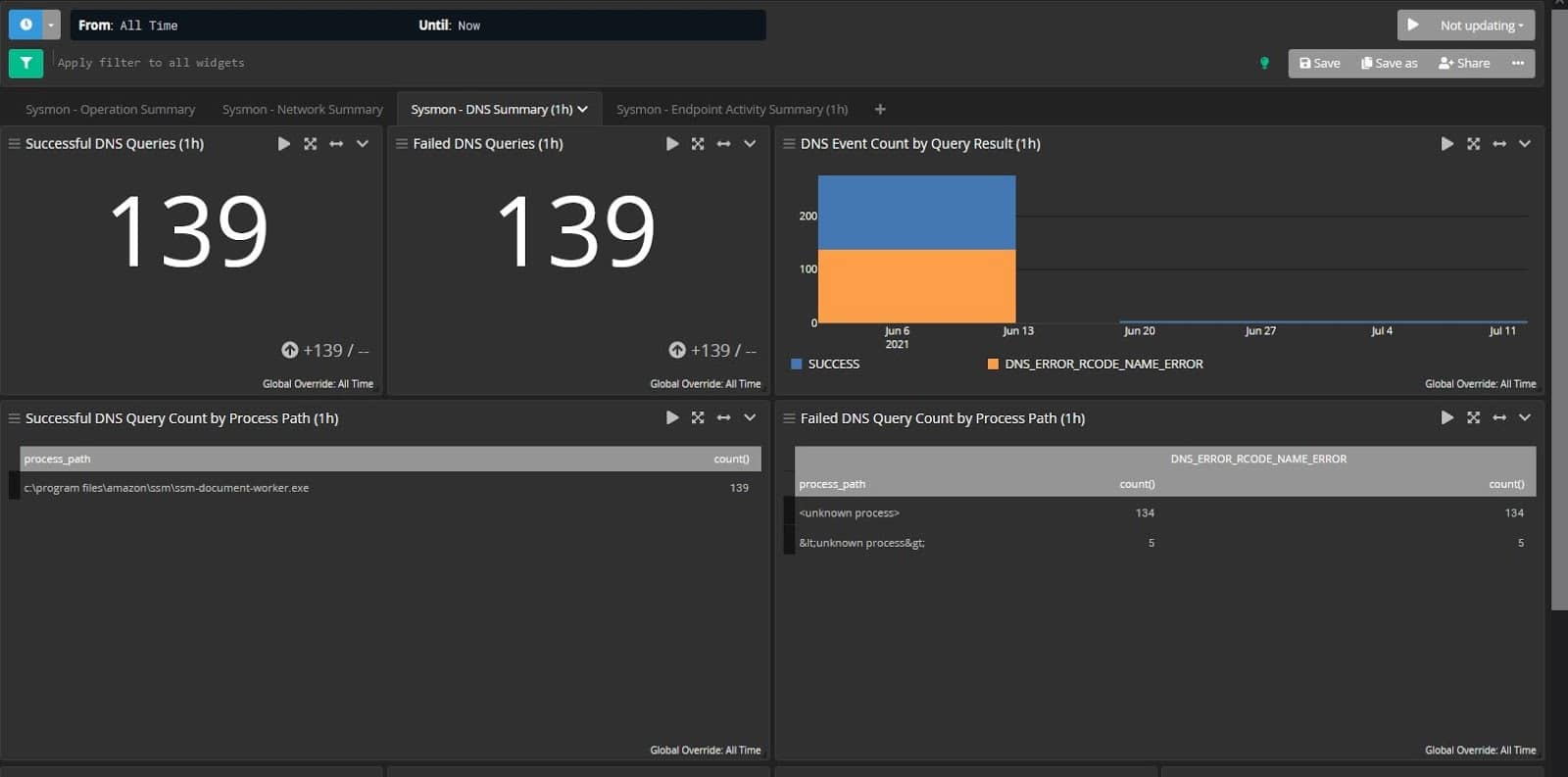
The new content pack means you can utilize lookup tables. To help detect track potential fallout from the SolarWinds hack, we built lookup tables that include hash values and DNS destinations for visibility into the bad DNS locations or IP addresses. Then, you can schedule and set the timing for when the search executes.
GRAYLOG ILLUMINATE CONTENT PACK FOR SYSMON
With Graylog Illuminate, you can eliminate many of the challenges organizations face when trying to get started with Sysmon. Sysmon events give you the data necessary to track the activity on endpoints. Graylog’s Illuminate content pack for Sysmon helps you maximize the return on investment by removing many of the primary pain points.
Graylog’s Illuminate for Sysmon content pack reduces the amount of time it takes to get started tracking important data and makes it easier to tune your deployment. By bringing together all of your Sysmon data and your other event logs, you can have full visibility to help protect your Windows systems.