Everyone remembers that one required writing class they needed to take. If you’re like a lot of other security analysts, you assumed that your job would focus on using technology, not writing research papers. However, in today’s business environment, cyber incidents are critical business events, especially as governments and agencies create more reporting requirements.
A cyber incident report is a key element for your incident response process, especially when your organization reviews activities to identify areas of improvement during the lesson’s learned phase. When implementing a structured incident response plan, you should know what an IT security incident response report is, why you need one, and what it should contain.
What Is Cyber Incident Reporting?
Cyber incident reporting involves documenting the details of incidents like:
- Cyber attacks
- Data breaches
- Unauthorized access
The IT security report typically details an incident’s timeline, including:
- Date of incident
- Attacker activities and timing
- Accounts, resources, and/or data affected
- Remediation steps taken
Cyber reporting is a critical part of the incident response process because organizations can use the documents as part of:
- Lessons learned: Assessing incident detection and response to identify areas of improvement
- Implementing controls: Developing new controls to prevent a similar incident from occurring in the future
- Notification requirements: Communicating with affected parties or others as required by law
Why Are IT Security Reports Important?
Documenting an incident’s details and notifying relevant stakeholders promptly provides various benefits.
Maintain Compliance
Most legal and regulatory frameworks require organizations to report cybersecurity incidents to various involved parties, including:
- Law enforcement
- Cybersecurity agencies
- Affected parties, like individuals or companies whose data was compromised
Laws have varying timelines for providing notification. For example, the General Data Protection Regulation (GDPR) mandates that organizations report a data breach within 72 hours. Meanwhile, under the Health Insurance Portability and Accountability Act (HIPAA), covered entities must notify affected parties within 60 days.
Failure to comply with these notification requirements can lead to fines or other penalties.
Improve Risk and Threat Awareness
A detailed cyber security incident report provides insight into potential weaknesses. By analyzing the incident’s underlying causes, security teams can improve their risk models and close security gaps. The organization can use this information to address new threats then implement new security controls to mitigate risk.
Build Trust With Clients, Customers, and Stakeholders
Transparency during data breaches builds trust with stakeholders by demonstrating professionalism and urgency. Open communication about incidents reinforces that no organization is immune to cyber threats, showcasing commitment to data protection. While the organization will remove sensitive information related to its own security, the IT security incident report provides a timeline that can act as the foundation for these communications.
Cyber Reporting Challenges
Reporting, like compliance, is a process that can become overwhelming, especially for understaffed security teams.
Gathering Information
Under the pressure of an ongoing incident, security teams need to investigate quickly. Isolation and recovery are the critical steps. They document their activities, but they have no time to organize their documentation. Once they contain the threat and recover systems, they spend time putting the puzzle pieces together.
Creating a timeline
In a perfect world, incident investigations start with the first alert that the attackers trigger. Across complex, interconnected systems, the activity that initiates an investigation may not be that first alert. Additionally, many alerts only provide a quick glimpse into a moment in time. For example, Sigma rules provide insight that an event occurred but often lack context, like previous or follow up events.
Turning data into a narrative
Alerts and ticketing system notes are simply data points. They provide insight into discrete actions. For a cybersecurity incident report, analysts need to turn these events into a narrative. For example, the system may have sent a Windows Event alert with the ID 4625, “attempt made to logon with unknown user name or bad password and failed.” However, the security analyst needs to translate that “what happened” into the “why it matters.”
Using sensitive environment data
Although large language models (LLMs) can turn raw data into a narrative, cyber incident report data contains sensitive information, including user IDs or internal identifiers. Unfortunately, feeding data into a public LLM makes that information part of the technology’s database, creating a data leak issue.
What Needs to Be in a Cyber Security Incident Report?
Since organizations use IT security reports to document and learn from incidents, reports need to include technical and non-technical information that outlines various event details.
Executive summary
The executive summary provides a clear, concise overview of the cybersecurity incident for a broad audience, highlighting:
- Key finding
- Actions taken
- Impact on stakeholder
- Incident ID
- Incident summary, with type, time, duration, and affected systems/data
Incident details
This section captures critical information about the incident, including:
- Nature of threat
- Business impact
- Immediate actions taken
- When/how incident occurred
- Who/what was affected
- Overall scope
Attack vector details
Attack vector details identify the specific vulnerabilities that attackers exploited, including technical details like:
- Open ports
- Weak credentials
- Phishing URLS
- Source IP addresses for Distributed Denial of Service (DDoS) attacks
Systems and assets affected
This section outlines the technology assets impact, including:
- Servers
- Storage
- Network device
- User devices
Additionally, it details the damage that the incident causes, like data corruption, to evaluate the impact on business operations.
Business impact assessment
A business impact assessment evaluates the operational disruptions and data compromises resulting from the cyber incident. It reviews any
- Financial losses
- Regulatory implications
- Long-term consequences
Incident response actions
Incident response actions highlight the steps taken from detection to remediation, including
- Preparation
- Containment
- Recovery
Detailing these activities can identify areas of improvement that enable the organization to update controls.
Communication and notification logs
Communication and notification logs show how the organization shared information about the incident for compliance and accountability purposes. These logs detail communications with all affected parties informed, including
- Internal teams
- External stakeholders
- Regulatory authorities
Conclusions
In the conclusions, the cybersecurity incident report provides a comprehensive overview of the event, its impact, and insights for future prevention.
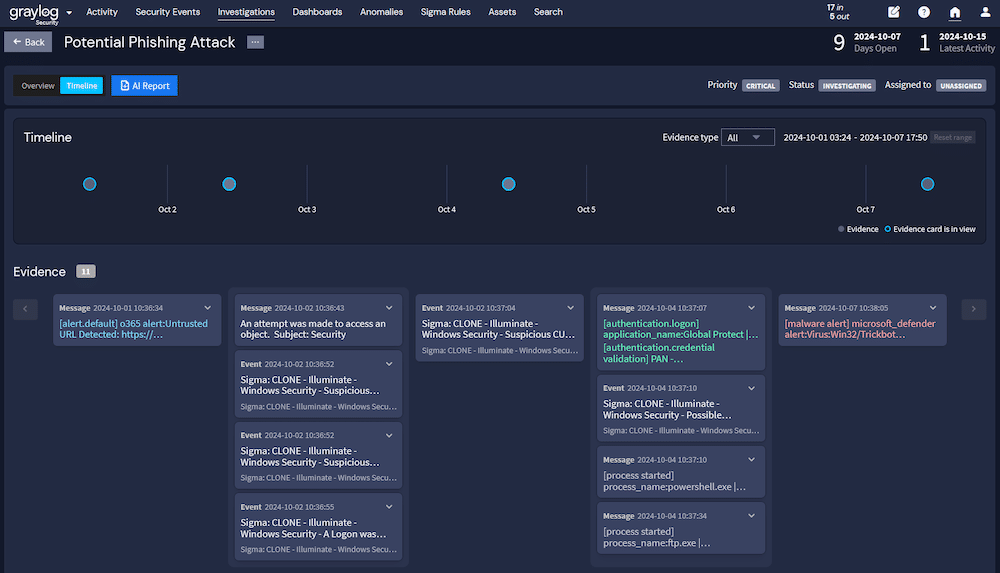
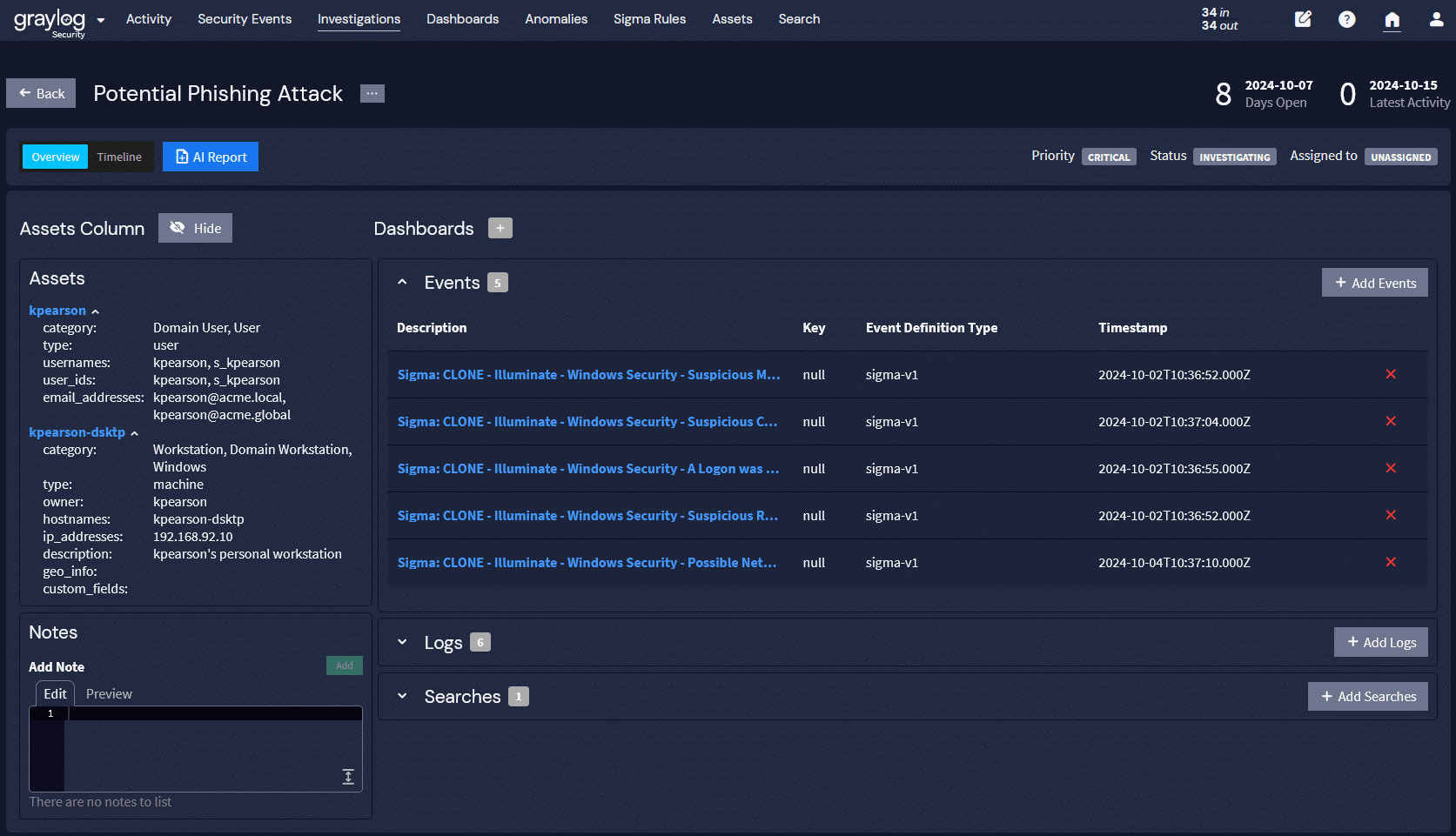
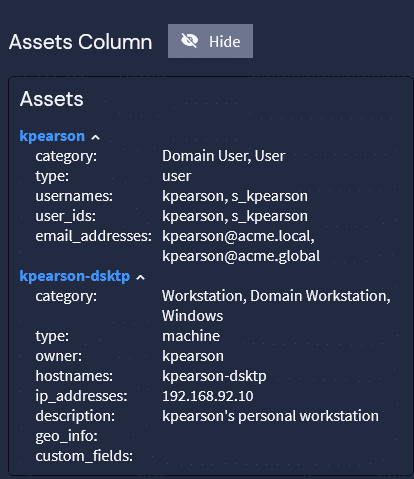
Graylog Security: Responsible AI for Automating IT Security Incident Reporting
Reading every log generated during a security incident is overwhelming, but the individual logs are only limited pieces of discrete information. To gain full visibility into an incident, you need to aggregate the data and understand the timeline.
With Graylog Security, you can create AI-generated incident reports using your organization’s log data while maintaining control and security over the information in the logs. At the click of a button, our AI interface analyzes all the logs and provides a report based on what it found, what it sees happening based on the data, and recommendations for mitigating the issue. Since all data you need remains in your Graylog deployment or in Data Warehouse, you maintain control, security, and privacy over your most sensitive environment data.
To learn how Graylog Security can improve your cyber incident reporting capabilities, contact us for a demo today.



