Whether you’re a developer or a security analyst, you probably already know the name Docker. Developers use Docker’s open-source platform to build, package, and distribute their applications. Since the application and all dependencies sit in the container, it runs consistently across different operating systems and environments. As with everything technology, Docker adoption is a good news/bad news story.
Good news: DevOps teams can ship applications faster.
Bad news: Attackers keep looking for new ways to compromise applications.
While Docker adoption is popular, you should create a strategy that integrates security so that you can gain the benefits and reduce the risks.
What is Docker?
The Docker platform started with containers, a standardized unit of software. A container is an isolated application version that runs on a host machine, leveraging a kernel namespaces and groups features available in Linux. Docker images contain everything necessary for an application to run, including code, runtime, libraries, and dependencies.
The suite of solutions include:
- Docker platform: cloud-native or desktop client for building, sharing, and running cloud apps
- Docker engine: container runtime that runs all application dependencies inside the container across various Linux and Windows operating systems (OS)
- Docker Hub: container image registry where community developers, open-source contributors, and independent software vendors (ISV) publicly share code
- Compose: tool that enables developers to use a YAML file to configure an application’s services then create and start them with a single command
What are the advantages of Docker?
Docker simplifies the development-to-production lifecycles, helping development teams overcome the “works on my machine” problem. By creating a development environment that resembles their production environment, developers can ensure that applications run consistently across different operating systems and environments.
Increased efficiency
Developers can create, deploy, and manage lightweight, self-contained containers to run and monitor applications in isolated environments. By preventing interference between different applications and processes, development teams can optimize resource usage, ultimately increasing overall system efficiency.
Portability
Containers are compatible with various operating systems, meaning that they can run on:
- Developer’s local laptop
- Physical machines in a data center
- Virtual machines (VM) in a data center
- Cloud
Developers can run containers on one or multiple environments, enabling them to align with business needs.
Scalability
When using an orchestration tool, developers can automate container deployment, management, scaling, and networking. Depending on user demand, cloud applications require more or less resources. With an orchestration tool like Docker Swarm or Kubernetes, developers can scale applications and resources up and down based on the organization’s needs, ensuring that the system can handle traffic without compromising performance or security.
Isolation
Although multiple containers can reside on a host, each one runs independently with its own file system, network stack, and resources. This isolation mitigates risks if attackers compromise one container because the isolation should prevent them from accessing other containers or the host.
Version control
Since Docker enables container versioning and management, security and IT operations teams can revert to previous application versions if they identify a vulnerability.
Continuous integration and deployment (CI/CD)
Since Docker containers integrate well with CI/CD pipelines, developers can seamlessly integrate them into their overall software and deployment processes.
What are the security risks associated with Docker?
Despite the great news about the benefits Docker provides, you also need to face the “bad news” about the security risks.
Some of the primary risks arising from Docker containers include:
- Vulnerabilities in container images that attackers
- Improperly configured containers or hosts
- Misconfigurations that lead to inadequate isolation
- Malicious or compromised images in open-source repositories
The fundamental security threat arising from containers lies in attackers leveraging misconfigurations, vulnerabilities, or inserted malicious code to:
- Escape the container
- Compromise other containers or the host
Why is securing Docker challenging?
Development, IT operations, and security teams share the responsibility and challenges associated with Docker security.
Security and IT Operations
IT operations and security teams struggle with Docker security be for various reasons, including:
- Continuously evolving technology: New features and updates make staying updated on best practices, vulnerabilities, and patches difficult.
- Dynamic attack surface: The attack surface changes when developers dynamically spin up or tear down containers, making it difficult to identify resources and track user access.
- Distributed nature: Deploying multi-container applications across different hosts and environments requires managing access across multiple hosts, securing network communication between containers, and ensuring consistent security configurations across the infrastructure.
- Lack of visibility and monitoring: Traditional security tools and practices fail to appropriate track and monitor security, undermining the ability to detect and respond to security incidents effectively.
- Orchestration platform complexity: Securing the orchestration platform requires ensuring secure communications between various components.
Developers
Developers struggle with Docker security be for various reasons, including:
- Container image complexity: Container images may have vulnerabilities or dependencies arising from hard-to-trace third-party components.
- Hardcoded secrets: Scanning code may not detect secrets in source-code embedded in long character strings or in hashed data.
- Default configurations: Default configurations allow processes to run as root and use the host’s user ID namesake as a default.
Best Practices for Monitoring Docker Containers
To help you monitor your application environments, Docker provides various logging mechanisms. By implementing some best practices, you can evolve and mature your development, security, and IT operations processes.
Use a Centralized Log Management
To create a single source of data, you should use a centralized log management solution that can parse, normalize, aggregate, correlate, and analyze your log data across your IT and development environments.
Docker provides various log drivers so that you can easily standardize messages across your diverse environments. Once you have your data parsed and normalized, you can implement
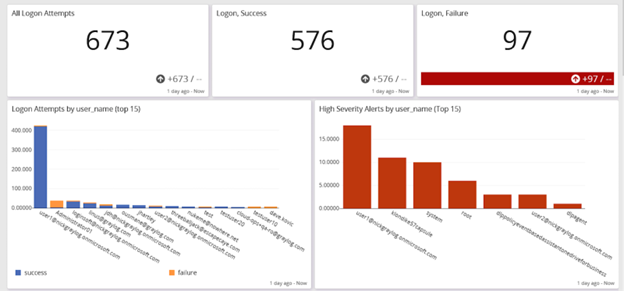
Monitor User Access
Monitoring user access to Docker containers enables your security team to ensure that only registered users with the appropriate privileges interact with your development, testing, and production environments.
When you incorporate user and entity behavior analytics (UEBA) into your access monitoring, you can implement additional security functions like:
- Privileged access management (PAM)
- Password policy compliance
- Abnormal privilege escalation
- Time spent accessing a resource
- Brute force attack detection
These additional functionalities support your ability to identify security incidents arising from:
- Unauthorized actions of authorized personnel
- Use of compromised credentials
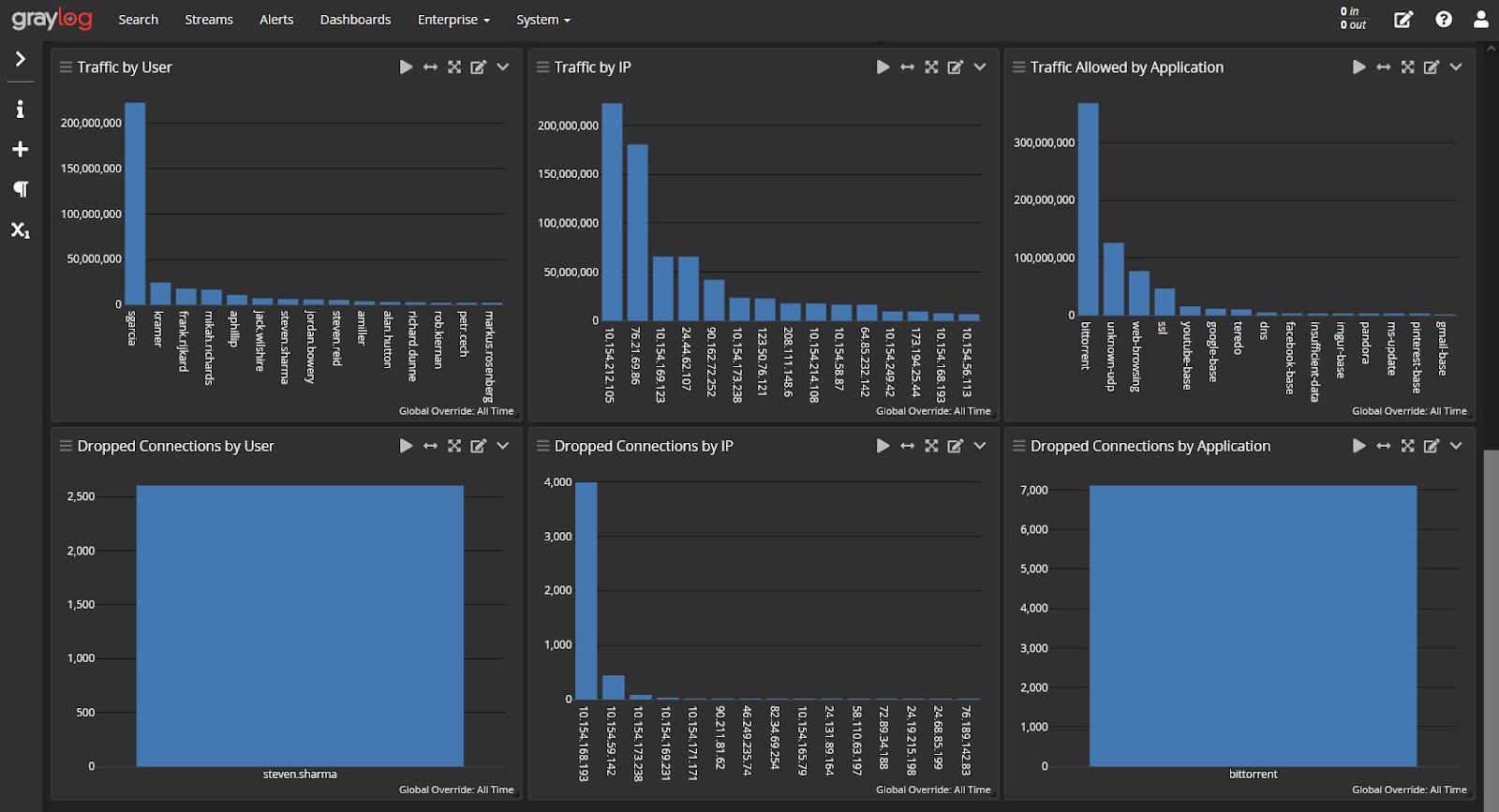
Track Network Traffic
When you monitor network security, you gain more visibility into communication between different hosts. For example, by combining firewall logs with Intrusion Detect System (IDS)/Intrusion Prevention System (IPS) logs, you gain insight into:
- Abnormal inbound and outbound traffic that could signify data traveling to a cybercriminal-controlled server
- Potential evasion techniques
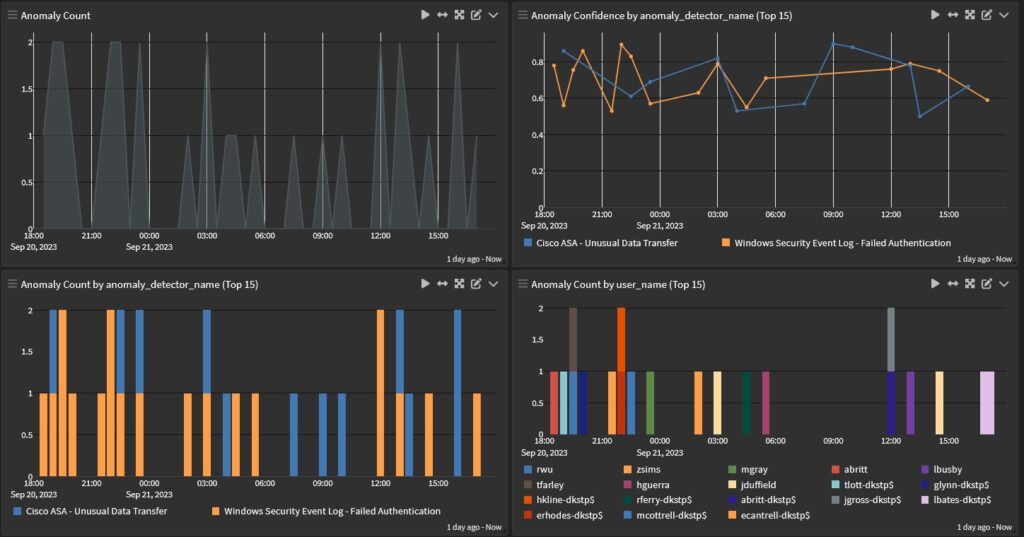
Further, with security analytics that enable you to set baselines for activity and design alerts for anomalies across all your environments, you can identify potential security incidents like:
- Use of compromised credentials
- External unauthorized access
- Compromised, authorized external parties
- Unauthorized hardware/software implemented or connected
Store Historical Data
Docker containers are ephemeral, meaning that they can be short-lived. However, by storing log data, you create a long-term record that can help you investigate a security incident. Docker containers typically publish their logs to the application’s stdout and stderr output streams. Terminating or shutting down the container erases the logs. By using a centralized log management solution, you can store them for and use them when you need.
Graylog Security: Enabling Secure Docker Container Adoption
With centralized log management, you can aggregate and analyze data from across your development, testing, and production environments to gain visibility into Docker container security.
Since Docker natively provides a Graylog Extended Log Format (GELF) driver, you can accelerate your analysis and monitoring. With all Docker and environment data normalized, you can leverage our Graylog Security analytics for the security platform functionality you need without the time-consuming complexity and costs associated with a traditional security incident and event management (SIEM) tool. Further, Graylog enables security, IT operations, and development teams to collaborate more efficiently and effectively, giving them a way to address both security issues and bugs by using a single source of data.
To see how Graylog can enable your technology teams, contact us today.