Think about how your banking app connects to payment processors or how your healthcare provider’s system shares records securely – APIs have become essential for modern digital interactions, enabling applications to communicate and share data effortlessly. However, this convenience comes at a cost: APIs often handle vast amounts of Personally Identifiable Information (PII), making them prime targets for API data exfiltration.
With APIs transmitting everything from customer names and email addresses to payment details and healthcare records, cybercriminals and malicious insiders have increasingly turned to API-based attacks to steal sensitive data. Worse, many organizations lack visibility into which APIs are handling PII, creating massive security blind spots.
In this blog, we’ll explore the growing risks of PII exposure in API traffic, the methods attackers use to exfiltrate data, and what capabilities to look for in a data exfiltration prevention solution that will provide real-time protection to prevent data breaches.
The Risks of PII Exposure in APIs
APIs are designed for data exchange, making them an attractive vector for data exfiltration. Here’s why they pose such a unique risk:
- Unmanaged and Shadow APIs. Many organizations don’t even know how many APIs they have, let alone which ones handle PII. These “shadow APIs” operate without security oversight, leaving PII exposed.
- Lack of Deep Payload Inspection. Traditional security tools (WAFs, API Gateways) focus on perimeter protection and traffic filtering, but they don’t inspect the actual data being transmitted in API calls. This means sensitive information can be exfiltrated without triggering alerts.
- API Misconfigurations & Over-Permissioned Access. APIs that return too much data or lack proper access controls can expose entire datasets. Attackers exploit these weaknesses through Broken Object-Level Authorization (BOLA) attacks and token hijacking.
- Insider Threats & Compromised Credentials. Malicious insiders and attackers using stolen credentials can access APIs as legitimate users, making traditional threat detection ineffective.
- Slow, Stealthy Data Exfiltration. Attackers don’t always steal data in bulk. Many use low-and-slow exfiltration techniques, siphoning small amounts of PII over time to avoid detection.
With regulatory frameworks like GDPR, CCPA, and HIPAA enforcing strict data protection standards, organizations must take proactive measures to secure APIs and prevent unauthorized PII exposure.
How Attackers Exploit APIs for Data Exfiltration
Cybercriminals have found ways to exploit API weaknesses for PII exfiltration – as seen in high-profile breaches like the Facebook API leak and T-Mobile’s customer data exposure, where attackers siphoned off sensitive data through API flaws. Here are some common tactics:
- API Enumeration & Discovery Attacks – Attackers scan public and private APIs to find endpoints exposing sensitive data.
- Excessive Data Exposure – Poor API design can return entire datasets when only a single data point is needed.
- Broken Authentication and Token Theft – Compromised API keys or session tokens allow attackers to impersonate legitimate users and extract data.
- Man-in-the-Middle (MitM) Attacks – APIs transmitting unencrypted PII over insecure connections are vulnerable to interception.
- Automated Data Scraping – Bots exploit APIs to collect PII at scale, often without triggering security alerts.
To combat these threats, organizations need more than traditional perimeter defenses – they need deep visibility into API traffic and real-time threat detection.
What to Look for in a Data Exfiltration Prevention Solution
Not all security tools are built to handle the unique challenges of API-based data exfiltration. When evaluating a solution, organizations should look for a tool that provides deep visibility, real-time monitoring, and seamless integration with existing security frameworks. Here are the key capabilities to prioritize:
- Comprehensive API & PII Discovery
A strong data exfiltration prevention tool should automatically identify and categorize all APIs handling PII, ensuring that no sensitive data flows remain hidden.
- Full API Payload Inspection
Traditional security tools focus on metadata and traffic patterns, but a robust solution must analyze both API request and response payloads to detect unauthorized data access in real-time.
- Behavioral Threat Detection
Instead of relying on static rules, the tool should use machine learning and behavioral analytics to spot unusual data access patterns, even when attackers attempt slow, stealthy exfiltration.
- Real-Time Alerts & Response
The faster an attack is detected, the quicker it can be stopped. Look for a solution that provides immediate, actionable alerts.
- Risk-Based Prioritization
Not all security events require the same level of urgency. A good tool should prioritize threats based on data sensitivity and risk exposure, allowing security teams to focus on high-impact incidents first.
- Seamless Security Integration
Data exfiltration threats don’t exist in isolation. The right solution should work alongside existing WAFs and API gateway tools to provide a unified security posture.
- Regulatory Compliance Assurance
Organizations must meet strict data protection regulations like GDPR, CCPA, and HIPAA. A strong exfiltration prevention tool should provide clear visibility into PII exposure and automated compliance reporting to help meet regulatory requirements and avoid penalties.
With APIs continuing to expand an organization’s attack surface, investing in a dedicated data exfiltration prevention tool is no longer optional – it’s now essential. By choosing a solution with these key capabilities, businesses can ensure that sensitive data stays where it belongs – inside the walls of the business.
How Graylog API Security Protects PII from Exfiltration
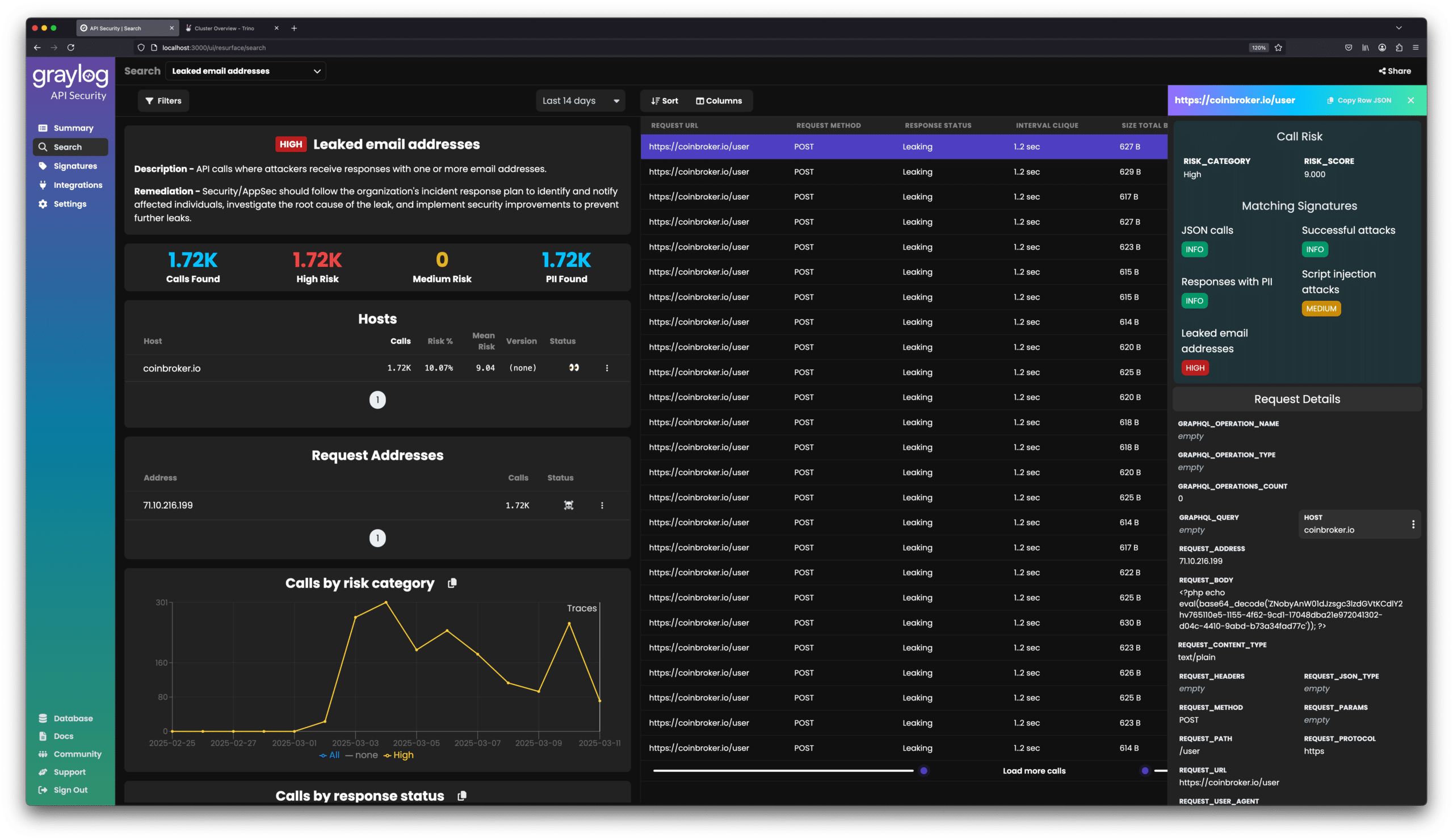
With Graylog API Security, security teams can proactively catch and stop API-based exfiltration attempts before they escalate into full-blown breaches. Unlike traditional security tools that focus on traffic control, Graylog API Security inspects API payloads in real time, identifying unauthorized data flows and stopping exfiltration at the source.
- Continuous API & PII Discovery. Graylog API Security automatically identifies and categorizes all APIs transmitting PII along with all forms of PII, providing complete visibility into sensitive data exposure.
- Real-Time Data Exfiltration Detection. Graylog API Security uses behavioral analysis & risk scoring to detect unauthorized PII access.
- Full Request & Response Inspection. Graylog API Security goes beyond header analysis to examine the actual data being exchanged.
- Threat Intelligence & Anomaly Detection. Graylog API Security identifies zero-day API attacks and stealthy exfiltration attempts.
- SIEM Integration. Graylog API Security seamlessly integrates with Graylog Security and augments centralized security operations with API-specific context.
- Built-In Compliance Support. Graylog API Security helps organizations meet GDPR, CCPA, HIPAA, and other regulatory requirements by providing detailed visibility into PII flow and tracking and securing PII across all APIs.
With Graylog API Security, organizations gain proactive protection against API-driven data exfiltration, ensuring compliance while preventing costly data breaches.



