A recent analysis by JPMorganChase criticized the CVSS scoring process, finding missing context leads to misleading prioritization. When it comes to cybersecurity, patching vulnerabilities often feels like the Holy Grail. Get those CVEs patched, and you’re safe, right? Well, not exactly. As we know, patching isn’t as straightforward—or as effective—as we’d like to believe. Between limited resources, business interruptions, and the sheer volume of vulnerabilities, aiming for 100% patching of even critical and high severity findings can feel like chasing the wind.
Patching, while important, isn’t the ultimate answer to securing your environment.
The Obstacles to Patching Vulnerabilities
- Volume of Vulnerabilities
The number of disclosed vulnerabilities continues to skyrocket each year. The National Vulnerability Database (NVD) catalogs tens of thousands of new vulnerabilities annually. How do you decide what to patch when every scanner generates a flood of critical alerts?
- Business Continuity Concerns
Applying patches often means downtime, testing, and the risk of breaking critical systems. For organizations with legacy infrastructure, patching a production server could have unintended ripple effects that outweigh the vulnerability itself.
- Resource Constraints
Whether it’s budget, people, or tools, cybersecurity teams are stretched thin. A limited team can’t patch everything without neglecting other critical duties like incident response, user awareness training, or threat hunting.
- Exploit Context
Not every vulnerability is weaponized or even exploitable in your specific environment. Yet, traditional vulnerability management often treats all vulnerabilities as equally urgent, leading to patching fatigue.
Why 100% Patching Shouldn’t Be the Goal
Here’s the reality: patching every vulnerability isn’t just impractical; it’s unnecessary. Security isn’t about perfection; it’s about prioritization. You’re better off focusing on vulnerabilities that truly matter to your organization’s risk posture.
Why shouldn’t you aim for 100%?
- Not All Vulnerabilities Pose a Real Risk
A vulnerability in an unexposed system or one without a known exploit may not require immediate action. Over-focusing on low-risk vulnerabilities can leave high-impact risks unattended.
- Attackers Focus on Exploitable Opportunities
Attackers don’t care about your patch percentage—they care about the paths that lead to valuable assets. Patching systems indiscriminately can distract from understanding those paths.
- Runtime Context Matters More
Static vulnerability assessments tell you what could go wrong, but runtime context reveals what is happening. This is the key to distinguishing between theoretical risks and active threats.
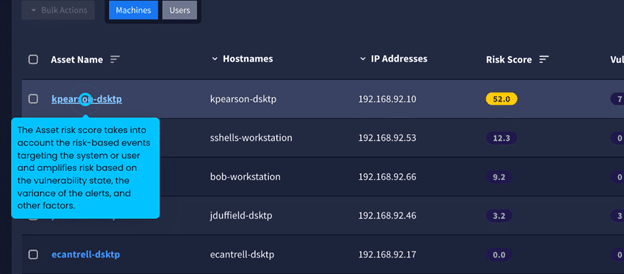
How Graylog Helps: Asset-Based Risk with Runtime Context
At Graylog, we recognize the goal isn’t 100% patching—it’s 100% understanding. That’s where our asset-based risk approach comes into play. Graylog assesses a risk score based on real-world activity along with your vulnerability data to help you focus on what truly matters.
- Runtime Activity as Necessary Context
Traditional vulnerability management is like looking at a static map—you see the terrain but not the movement. Graylog goes further by incorporating runtime activity. We help you answer questions like:
- Is the vulnerable asset being actively targeted?
- Is it communicating with known malicious IPs?
- Are unusual processes or behaviors happening on the system?
This real-time insight helps you prioritize vulnerabilities that attackers are actually exploiting.
- What’s Happening vs. What Could Happen
Patching vulnerabilities addresses what could happen, but Graylog helps you recognize what is happening. By correlating log data, threat intelligence, and asset behavior, we surface indicators of compromise (IOCs) and tactics, techniques, and procedures (TTPs) that reveal active threats.
- True Compromise Detection
Graylog’s focus isn’t just on potential risks but actual compromises. Our platform helps you identify and respond to incidents that have crossed the line from theoretical to real-world attacks. This allows you to spend less time chasing low-priority patches and more time addressing active threats.
Conclusion: Focus on What Matters
In cybersecurity, perfect can’t be the enemy of good. Chasing 100% patching is like locking every window in the house while the burglar walks in through the front door. Instead, focus on understanding your environment, prioritizing high-impact vulnerabilities, and recognizing true compromises.
With Graylog’s asset-based risk approach, you get the necessary context to separate the noise from the signal. By focusing on what’s happening, not just what could happen, you can align your resources to defend your organization effectively.
Want to see how Graylog can transform your vulnerability management process? Schedule a demo today!

VP of Product Management



