Imagine compliance is like a driving application. You know your location and you plug in the destination address, then it shows you the route’s overview. If you want a more specific map, you can zoom in a bit and get more details.
Similarly, the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) and it’s most recent revision provide the overview roadmap for your compliance journey. Meanwhile, NIST Special Publication (SP) 800-53 revision 5 gives you the street by street directions for how to travel from where you are to where you want to be.
By understanding how NIST 800-53 fits into your compliance program, you can build the security controls and monitoring that help you achieve your security and business objectives.
What is NIST 800-53?
NIST 800-53 sets out a series of controls that organizations can use to meet compliance requirements:
- Requirements: protection needs created by-laws, executive orders, directives, regulations, policies, standards, business needs, or risk assessments
- Controls: safeguards and protection capabilities that achieve the organization’s security and privacy objectives.
In short, an organization takes actions or deploys technologies that prove it follows the rules set forth in the requirements.
NIST 800-53 establishes 20 security and privacy control families that outline actions organizations can take to prove they followed a rule. Controls may include:
- Policies
- Oversight
- Supervision
- Manual processes
- Automated mechanisms
What are the 20 Control Families?
For each control family, NIST 800-53 defines Base Controls, Related Controls, and Control Enhancements with each step becoming more sophisticated. For each of these, the publication also provides a Discussion section with information about how to implement the control within the organization’s risk context.
The 20 Control Families are:
- Access Control (AC): Providing, limiting, and monitoring people’s access to and use of resources
- Awareness and Training (AT): Providing training about information security and privacy risks and issues
- Audit and Accountability (AU): Logging events to document activities across the IT environment, including the event type, time, location, source, outcome, and people or entities involved
- Assessment, Authorization, and Monitoring (CA): Engaging in third-party, independent control reviews, like audits and penetration tests, to determine whether controls work as intended
- Configuration Management (CM): Establishing secure baseline configurations, like disabling unnecessary functions, and creating official processes for changing, reviewing, and documenting configurations
- Contingency Planning (CP): Plans for maintaining or restoring critical business functions when systems are compromised or breached
- Identification and Authentication (IA): Creating unique user accounts and processes for ensuring that people are who they say they are when granting access to systems and resources, including considering multi-factor authentication (MFA)
- Incident Response (IR): Establishing and testing policies and procedures for handling and reporting incidents, including information spillage where sensitive information may end up in less secure systems
- Maintenance (MA): Scheduling, documenting, performing, and reviewing records of system component maintenance, repair, and replacement
- Media Protection (MP): Establishing and enforcing controls for protection digital and non-digital media, including access, marking, storage, transport, sanitization, use, and downgrading
- Physical and Environmental Protection (PE): Limiting control fo physical facilities, including for visitors, and protecting information from emergencies like power outages, fires, or natural disasters
- Planning (PL): Implementing policies, security and privacy architectures, central management operations, and baselines
- Program Management (PM): Implementing an information security program plan that assigns responsibility and sets strategies for sensitive data management, privacy management, data governance, risk management, and supply chain risk management
- Personnel Security (PS): Implementing policies and procedures for human resources risk management like screening, onboarding, and terminating personnel and third-party contractors
- Personally Identifiable Information Processing and Transparency (PT): Implementing and enforcing policies and procedures for what, how, when, and why to process personally identifiable information (PII)
- Risk Assessment (RA): Analyzing, documenting, and updating the organization’s risk tolerance and response as the foundation of its program, including privacy impact statements and threat hunting
- System and Services Acquisition (SA): Establishing, documenting, and enforcing policies and processes for allocating resources, acquiring technologies, usage, software installation, configuration management, secure development processes, and supply chain protection
- Systems and Communications Protections (SC): Enforcing low-level security controls, like separating system management and general use functionalities, implementing denial-of-service protections, protecting boundaries, data encryption, and operations security.
- System and Information Integrity (SI): Monitoring for incidents with tools like anti-virus, threat intelligence, spam protection, web application vulnerability remediation, and information handling processes
- Supply Chain Risk Management (SR): Implementing and enforcing policies and processes for reducing vendor and software component risk
What does NIST 800-53 compliance look like?
Within each of the 20 Control Families, NIST 800-53 contains anywhere from 6 to 51 Base Controls. Within those Base Controls, you then have the various Related Controls and Control Enhancements.
For example, AC-2 Account Management contains 12 control enhancements:
- Using automated system account management mechanisms
- Managing temporary or emergency accounts
- Disabling accounts for various reasons
- Automating audits of account creation, modification, enabling, disabling, and removal
- Requiring user logout
- Implementing dynamic access controls, like attribute-based access controls (ABAC)
- Managing privileged user accounts
- Using trust relationships, business rules, and mechanisms for dynamic account management
- Limiting use of shared or group accounts
- Generating alerts for least privilege violations to enforce the control
- Monitoring for abnormal user activity
- Disabling accounts for high-risk users
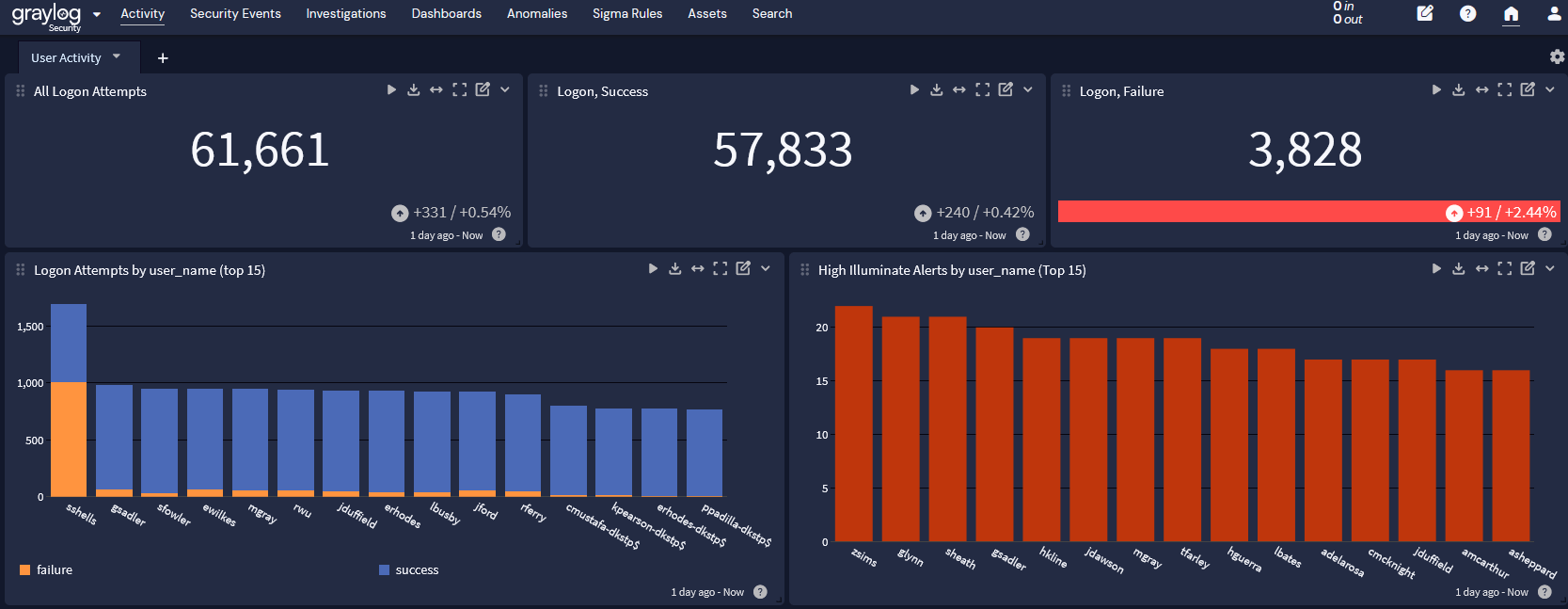
To enforce these controls and monitor their effectiveness, you likely collect data from various sources like:
- Identity and Access Management (IAM)
- Device logs
- Application logs
- User and entity behavior analytics (UEBA)
- Privileged Access Management (PAM) tools
- Network firewall logs
- Web Application Firewall (WAF) logs
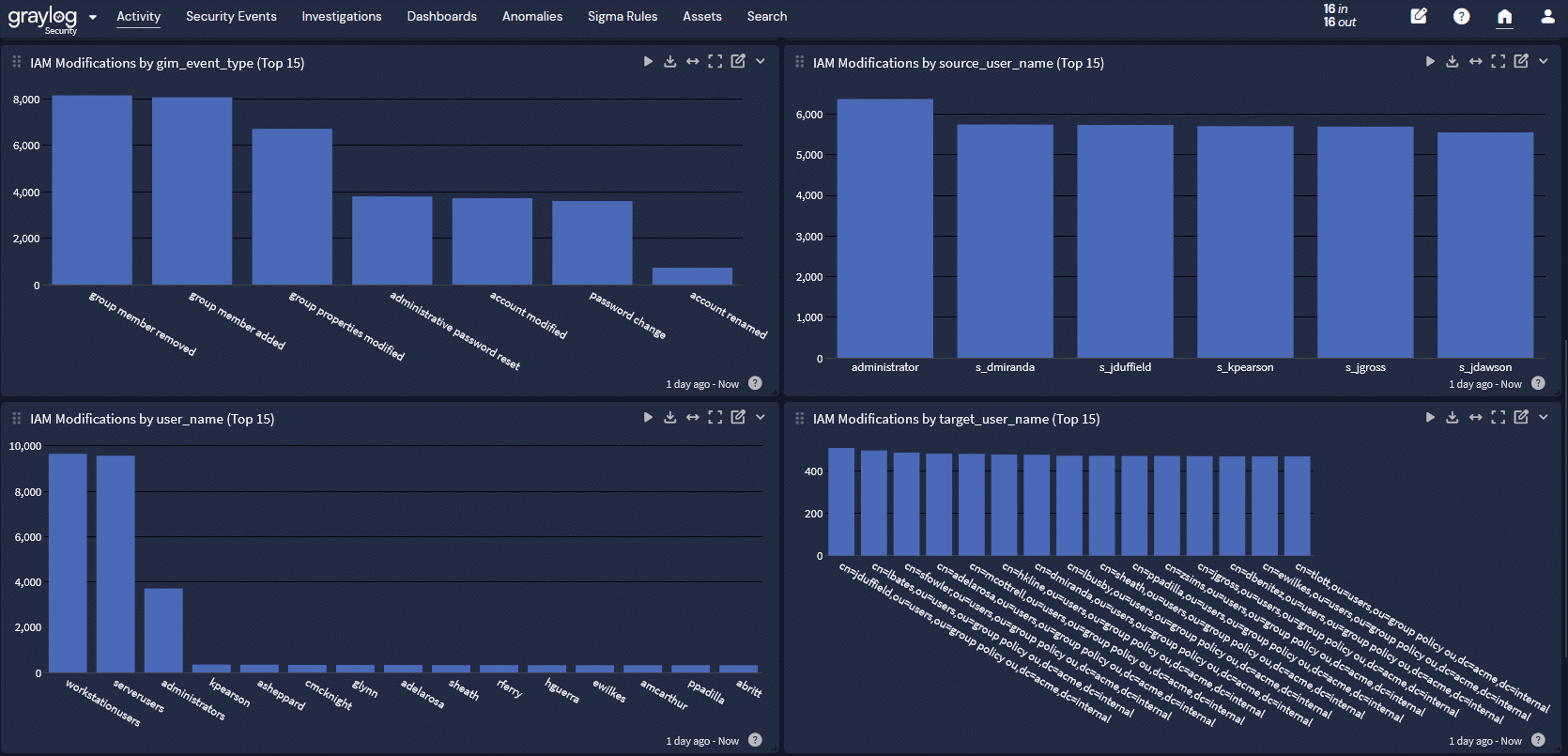
After integrating these inputs, you need to parse, normalize, and correlate the data generated which becomes time-consuming and overwhelming, especially if you have a small team with limited resources.
Despite these difficulties, a centralized threat detection and incident response (TDIR) solution provides long-term benefits. By centralizing your security and compliance monitoring data in a single location, you can create dashboards for these NIST 800-53 Control Families for continuous insights and audit documentation. Some examples of alerts that you may want to map to your NIST 800-53 compliance documentation include:
- Account lockout alerts
- Total number of account management activities completed overall or during a defined audit period, like accounts created, deleted, disabled, enabled, or modified
- Percentages for each type of account management activity as part of the whole overall or during a defined audit period, like accounts created, deleted, disabled, enabled, or modified
- Data about high-risk user groups like privileged, temporary accounts, and emergency accounts
- Activities related to NIST 800-53 controls
- Total populations for audit periods
- Access activity trends over time, including the ability to adjust for the audit period
Further, you may need to implement reporting procedures that include:
- Sharing data with internal and external auditors, compliance teams, and control owners
- Sending senior leadership reports with compliance summaries in an easy-to-digest way
- Exporting findings or data to downstream compliance platforms or validating findings against ticketing systems
Graylog Security: Continuous Monitoring for NIST Compliance
With Graylog’s security analytics and anomaly detection capabilities, you get the cybersecurity platform you need without the complexity that makes your team’s job harder. With our powerful, lightning-fast features and intuitive user interface, you can lower your labor costs while reducing alert fatigue and getting the answers you need – quickly.
Our prebuilt search templates, dashboards, correlated alerts, and dynamic look-up tables enable you to get immediate value from your logs while empowering your security team.
For more information about how Graylog Security can help you achieve your NIST CSF 2.0 objectives, contact us today.



