Email threats aren’t slowing down. From credential phishing to malware-laced attachments, email remains one of the most exploited entry points for attackers. If you’re already using Mimecast to help mitigate that risk, you’re ahead of the curve — but raw log data only gets you so far.
Starting with Graylog 6.2.3, you can pull logs directly from Mimecast using API v2.0 and view them immediately with built-in Illuminate Dashboards. This streamlines investigations, enhances visibility, enables cross-log correlation, and reduces time spent capturing critical information.
Why Integrate Mimecast with Graylog?
Mimecast logs contain a wealth of email security telemetry: blocked threats, quarantined messages, impersonation attempts, URL protections, DLP triggers — you name it. But your analysts are missing the bigger picture unless you’re pulling that data into your central logging and detection platform.
By integrating Mimecast with Graylog:
- You centralize email security insights alongside endpoint, firewall, and identity logs.
- You reduce pivoting between tools and improve incident response speed.
- You leverage ready-made dashboards and content to cut through the noise.
Prerequisites
Mimecast Setup
Before getting started, make sure the following prerequisites are covered:
- A valid Mimecast account
- A configured Mimecast API application (see Mimecast documentation for setup steps)
- API user with appropriate admin permissions based on log types
Graylog Input Configuration
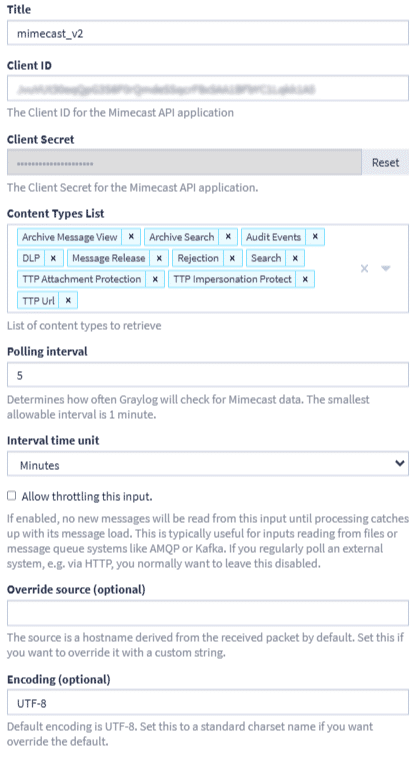
To configure the Mimecast input in Graylog:
1. Go to Graylog > Inputs
2. Select the Mimecast input and click Launch new input
You’ll be prompted to configure the following:
-
-
- Input Name
A user-defined name (e.g., “Mimecast Email Logs”) - Client ID
From your Mimecast API application - Client Secret
Also from your API application - Log Types to Collect
Select the types of logs you want to ingest (default: all). At least one is required. - Polling Interval
How frequently Graylog polls Mimecast (minimum: every 5 minutes) - Enable Throttling
When enabled, Graylog will pause new message intake from this input if the system is behind in processing
- Input Name
-
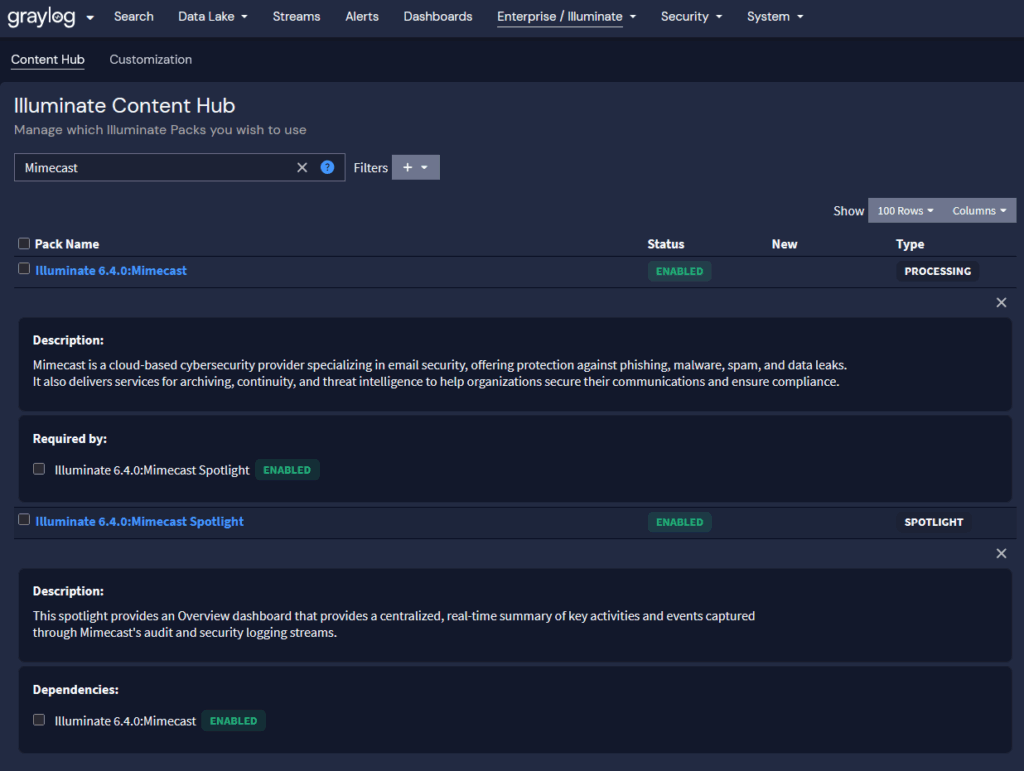
3. Enable the Graylog Illuminate Mimecast Processing Pack and Spotlight
That’s it — once saved, the input begins pulling in data and Illuminate goes to work.
Illuminate Technology Pack
The content pack supports the following log types. Generic processing will be provided for log types not listed.
User Logged On
Unauthorized API Request
Case Action
Review Set Action
Discovery Case Adjustments
Logon Authentication Failed
Logon Requires Challenge
Completed Directory Sync
New Policy
Existing Policy Changed
Mimecast Support Login
Content Definition Adjustments
Existing Route Changed
New Delivery Route
Profile Group (Address) Log Entry
Account Updated
API Application Created
User Password Changed
User Settings Updated
User Locked
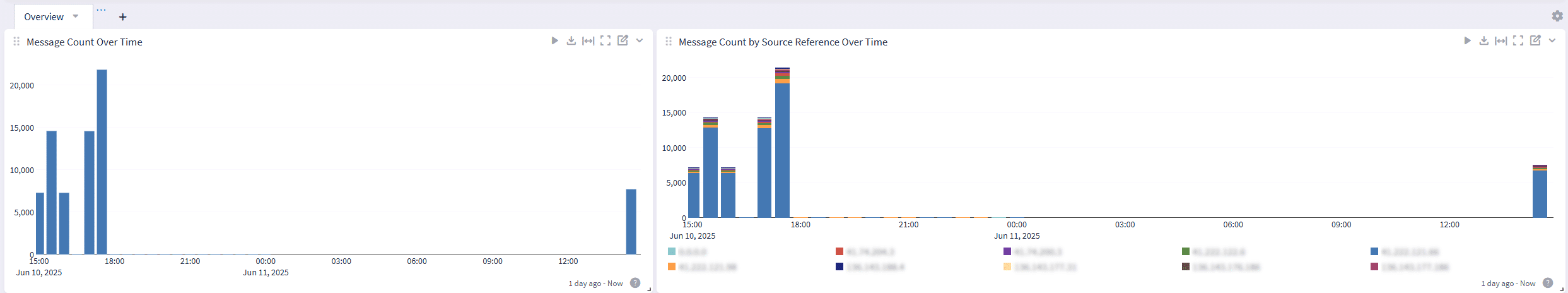
Illuminate Dashboards: Instant Insights from Day One
No need to build dashboards from scratch. With the Mimecast integration, Illuminate provides prebuilt dashboards that offer:
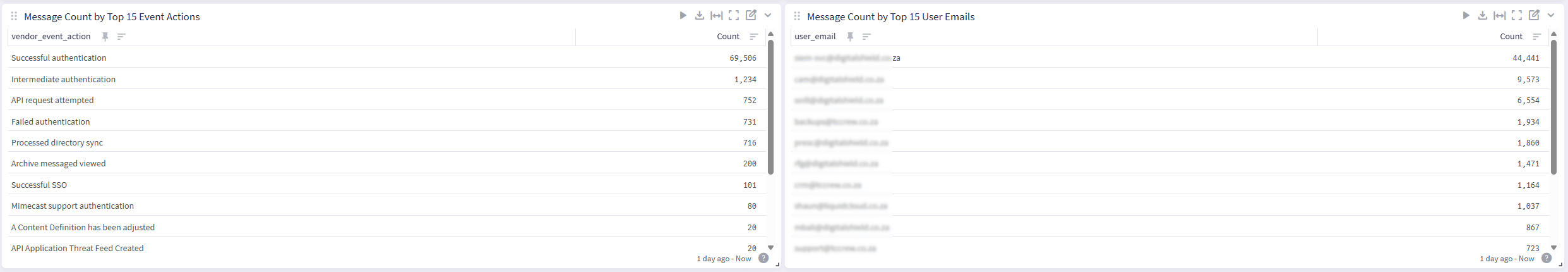
Email Threat Overview
See overall message volume, threat counts, and detection trends across time.
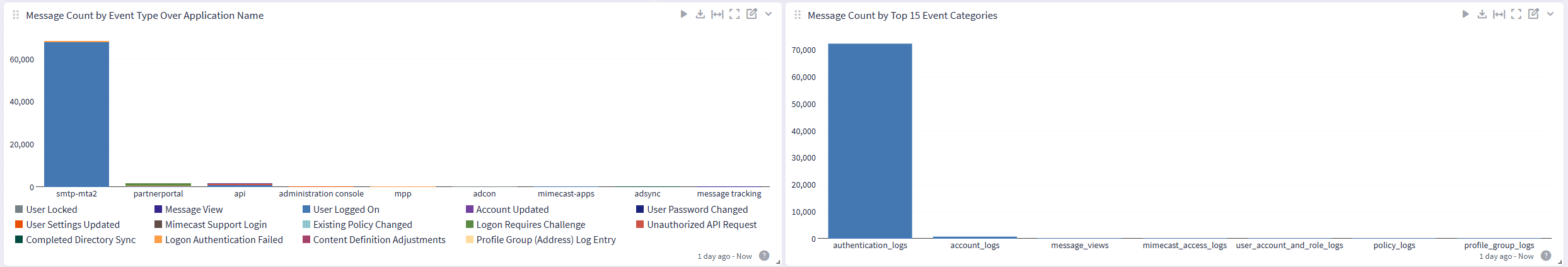
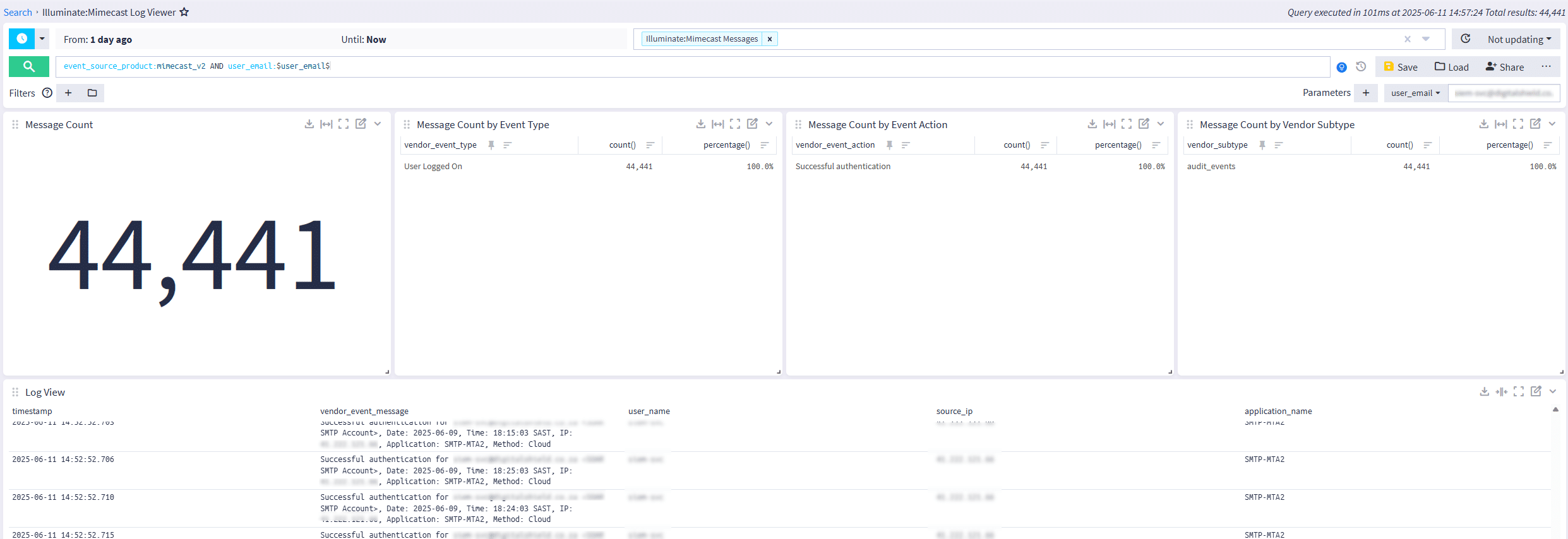
Saved Search
Quickly save searches for sharing to the team or creating an investigation using email parameters.
How This Helps Analysts
It’s not just about pretty charts. Integrating Mimecast with Graylog improves the analyst experience in several key ways:
- Centralized Investigation
Email events are side-by-side with endpoint, DNS, firewall, and user activity logs - Less Manual Correlation
No need to bounce between tools to get a full picture of an email incident - Faster Detection and Response
Dashboards highlight high-risk activity, helping analysts focus on what matters - Operational Context
Graylog’s enrichment and detection rules help connect Mimecast data to broader attack patterns
Ready to Try It?
If you’re already running Graylog Enterprise 6.2.3 or later, setting up Mimecast integration takes just a few minutes. With prebuilt dashboards and structured log inputs, you’ll go from raw data to actionable insights fast and finally get the email threat visibility your team needs.



