Industrial facilities increasingly rely on interconnected systems to improve operations. As they implement these technologies into their legacy environments, they create new cybersecurity risks within previously isolated Industrial Control Systems (ICS) and Supervisory Control and Data Acquisition (SCADA) by connecting them to public internet-facing applications.
To protect the ICS and SCADA systems from cyber threats, you should understand how these technologies fit into your environment and why cybercriminals target them. To implement appropriate cybersecurity for SCADA and ICS technologies, organizations need insights into why threat actors target these systems and best practices for implementing security controls.
What is ICS?
Industrial Control Systems (ICS) manage and control industrial processes by combining hardware and software systems that monitor industrial equipment and processes. These systems improve operational technology (OT) by supervising, controlling, and automating complex industrial environments.
As organizations work to automate these processes and use data analytics to improve operations, they create new risks as the applications that manage these technologies connect to the public internet. This convergence of the enterprise IT environment and the traditionally isolated ICS infrastructure requires organizations to implement new security controls.
What is SCADA?
Supervisory Control and Data Acquisition (SCADA) consists of the software and hardware that organizations use to control and monitor their industrial processes. While early SCADA technologies were physically and logically separated from the organization’s IT environments, they have evolved into a networked SCADA system that can include:
- Field devices: sensors that ingest data from industrial processes and actuators that control the processes
- SCADA field controllers: microcomputers that send the field device data to a human-machine interface (HMI)
- Remote telemetry units (RTUs): devices that interface with field devices and collect data about processes
- Programmable logic controllers (PLCs): small computers that monitor and control automated and repeatable processes
- SCADA supervisory computers: devices that gather data from field devices and control processes
SCADA systems typically fall into one of three types:
- Monolithic: operates from a central location
- Distributed: uses multiple controller
- Networked: remotely managed across the network
Since SCADA systems are integral to critical infrastructure, threat actors seek to disrupt them, either for financial gain or to achieve geopolitical objectives. As the enterprise IT and Operational Technology (OT) environments are increasingly interconnected, these systems pose a higher cybersecurity risk than before.
What Are the Differences Between OT, ICS, and SCADA?
OT, ICS, and SCADA technologies work together to manage industrial processes. However, their differences are the key to why you might have a hard time implementing a robust security program for them.
SCADA vs OT
OT is a broader technology category with SCADA as a subcategory. Although both monitor and manage different operational processes, OT can also include:
- Building management
- Fire control systems
- Physical access control systems
SCADA vs ICS
Like OT, ICS is a broader category of technologies for remote monitoring and process controls across industrial environments. An ICS may include SCADA as well as the following:
- Control loop: interprets signals from sensors
- Remote diagnostics and maintenance: identifies, prevents, and recovers from abnormal operations or failures
- Control server: communicates with other control devices
- Intelligent Electronic Device (IED): acquires data, communicates with other devices, and performs activities like local processing and control
ICS vs OT
ICS is a type of OT focused on controlling industrial processes and ensuring safe, reliable operation. OT security covers a wide range of control systems, while ICS has certain qualities unique to the security threats facing it.
How does a SCADA system work?
SCADA systems connect with various equipment through Distributed Control Systems and field devices. They orchestrate how information flows across the network to monitor complex industrial processes and manage their operations.
SCADA systems perform four functions:
- Data collection: gathering data, often converting analog data to a digital format for analysis
- Data communication: transmitting data across the network
- Data presentation: processing, organizing, and presenting data so system operators can make decisions about processes
- Control: making changes to operations or configurations
What types of data do SCADA systems collect?
Since SCADA systems help manage ICS processes, they collect various data necessary for maintaining operational efficiency and safety, including:
- Temperature: insuring equipment operates within safe limits
- Speed: insights into equipment speed for operational performance
- Pressure: maintaining safety and compliance when high-pressure systems are involved
- Customized metrics: tailoring data monitored to focus on the metrics relevant to an organization’s specific operational needs
How do cybercriminals attack ICS and SCADA systems?
The convergence of OT and IT gives cybercriminals the opportunity to use traditional enterprise attack methods against ICS and SCADA systems. However, unlike enterprise IT security incidents, an attack against ICS and SCADA can impact physical health and safety as well as compromise data.
Some typical attack types include:
- Spear phishing: sending fake emails to people who have access to these systems and tricking them into providing login information
- Vulnerabilities: using technical vulnerabilities in unpatched operating systems, software, and hardware to gain unauthorized, remote control of devices
- Distributed Denial of Service (DDoS) attacks: sending high volumes of requests to the system and overloading the web servers ability to respond to cause a network or service outage
- Misconfigurations: leaving internet-exposed devices at risk by allowing unnecessary functionalities
Best Practices for Securing ICS and SCADA
Securing SCADA systems is critical to safeguarding industrial processes and critical infrastructure organizations against cyber threats.
Centralize all security monitoring
Like your enterprise IT technologies, your ICS and SCADA systems generate log data, providing insight into ongoing activities across the environment. By centralizing all monitoring in a single threat detection and incident response (TDIR) solution, you can gain holistic visibility into behaviors across your enterprise OT and OT environment.
Many ICS and SCADA manufacturers have systems that send logs and data to SIEM. To Send these logs, Graylog can ingest logs using NXlog log shippers from many common platforms. Some include: Schneider Electric, General Electric, Siemens, and Yokogawa.
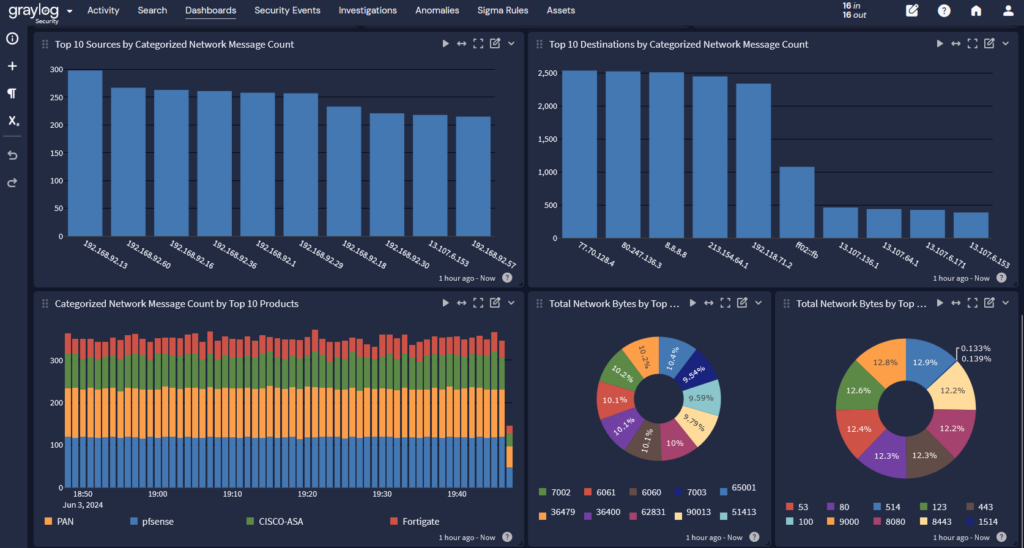
Segment networks
With network segmentation, you limit attackers’ ability to move between different network environments, like from the enterprise IT to the OT systems. Your network security tools, like firewalls, can help you implement these controls. Monitoring network traffic enables you to understand how people and devices use the different networks so you can set baselines and detect abnormal activity.
Limit access
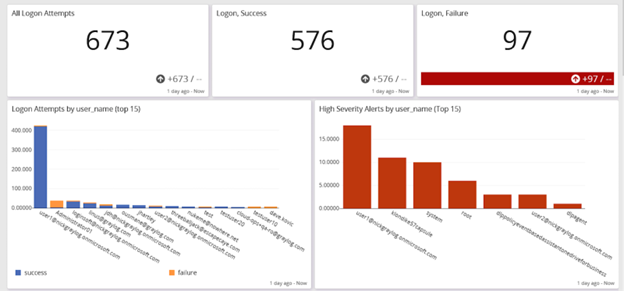
Limiting user and device access according to the principle of least privilege supports your network segmentation practices. You should implement role-based access controls (RBAC) to give only the least amount of access to networks and resources as people and devices need to complete their required activities and functions.
Create high-fidelity alerts
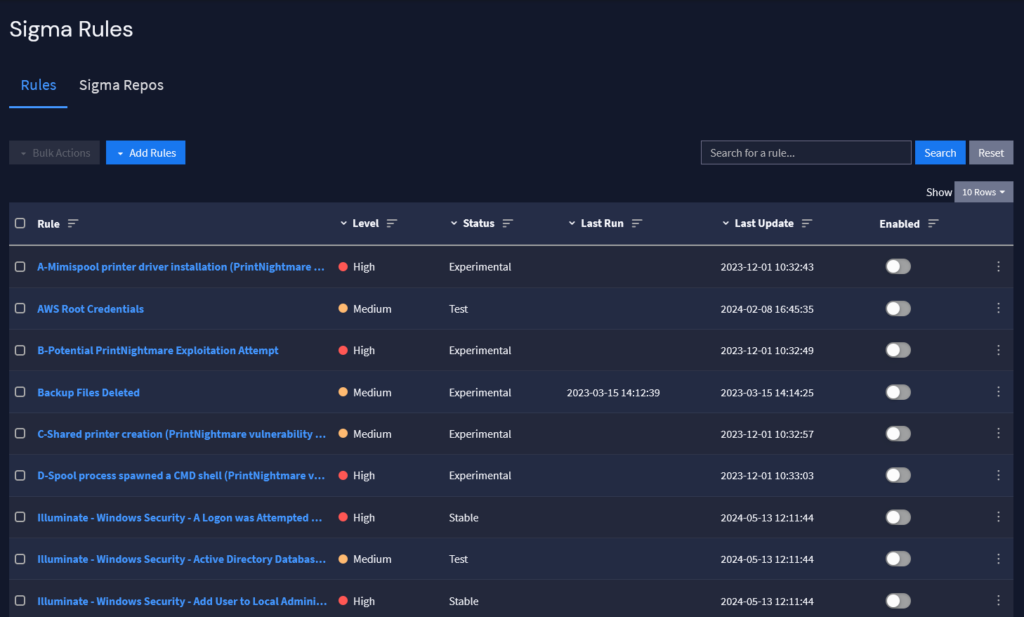
With all data and monitoring centralized in your TDIR solution, you can create high-fidelity detections to identify security issues quickly. For example, alerts that combine Sigma rules and MITRE ATT&CK framework information can help you improve key metrics like mean time to detect (MTTD) and mean time to response (MTTR).
Leverage Artificial Intelligence (AI) and Machine Learning (ML)
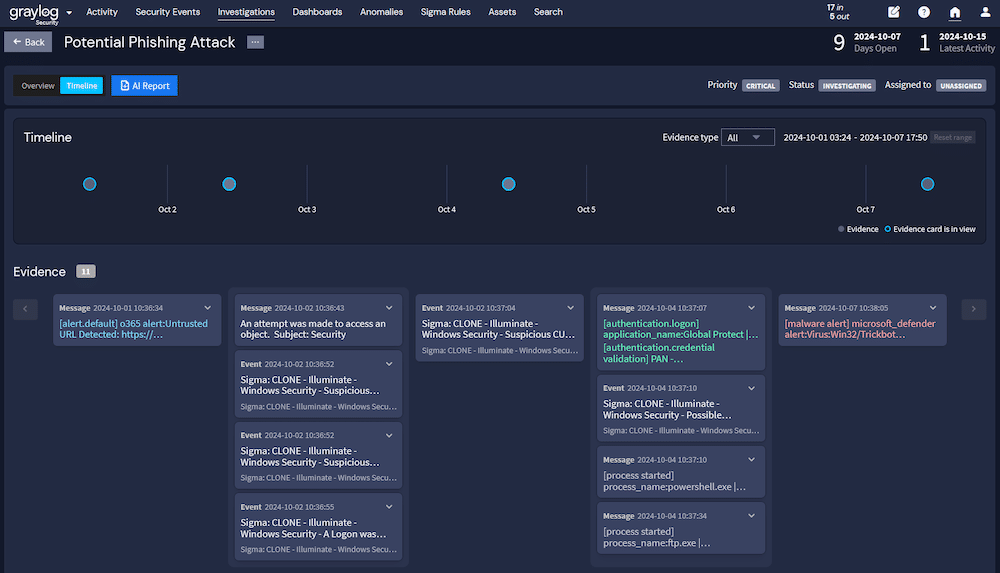
Since your environments generate high volumes of data, you can use AI and ML to improve detection and response capabilities. For example, security analytics can help you set baselines for expected user access and network traffic. Then, you can layer AI capabilities on top of ML to help track an attacker’s activity and generate incident reports.
Graylog Security: Enabling Security Monitoring for ICS and SCADA
Using Graylog Security, you can rapidly mature your threat detection and incident response capabilities. Graylog Security’s Illuminate bundles include rulesets with content that includes Sigma detections, enabling you to uplevel your monitoring by incorporating threat-hunting capabilities and correlations to ATT&CK TTPs.
By leveraging our cloud-native or premise-based capabilities and out-of-the-box content, you gain immediate value from your logs. Our anomaly detection ML improves over time without manual tuning, adapting rapidly to new data sets, organizational priorities, and custom use cases so that you can automate key user and entity access monitoring.
With our intuitive user interface, you can rapidly investigate alerts. Our lightning-fast search capabilities enable you to search terabytes of data in milliseconds, reducing dwell times and shrinking investigations by hours, days, and weeks.
To learn how Graylog Security can help you implement robust threat detection and response, contact us today.



