Cybersecurity can often seem intimidating for IT teams. After all, things like “threat hunting,” “red teaming,” and “blue teaming” are not used in IT operations. On the other hand, just because these words are terms of art doesn’t mean that they’re activities you don’t do already.
You’re probably already using log data as part of your IT operations incident response. You can apply those same analytics tools and processes to uplevel your cyber threat hunting for a more robust security posture.
What is threat hunting?
The biggest security risks facing your organization are those you don’t know. Proactive threat hunting to look for hidden risks with traditional technologies is time-consuming. Threat hunting is like exploring dark caves.
Your IT environment has these dark caves, pockets of access or data, that you need to protect. Threat hunters go into these caves, not necessarily knowing what they’re looking for but knowing that a threat actor might be hiding in the shadows.
When you’re monitoring service risks, you’re already doing a lot of this work. You’re looking for signals in the data that help you prevent system outages. Threat hunting to mitigate cyber attack risk works the same way.
The main difference is that you need information that gives you visibility into your business’s contextual risk. A situational awareness-driven threat detection process includes threat intelligence that can help your team detect potential threats already in your environment more effectively.
Threat hunting is running queries using known Indicators of Compromise (IoC) to look for suspicious system activity. This often becomes a barrier for many IT teams. They want to take a proactive look at environments, but the tools make it too resource-heavy.
Watch this video on Graylog Dashboards
A traditional security tool may need to require a query that can be multiple lines of code. A mistake in one line can return the error, so you need specialized staff that has experience with those tools to develop new queries for new use cases. Then, they need to build yet another fiddly query for each discrete action.
IT Risk Management Isn’t So Different from Threat Hunting Techniques
Since an IoC is an example of something outside your normal system, software, or hardware activity, your IT team is probably already looking for abnormal activity to prevent a service interruption. If your centralized log management tool makes it easy for your IT team to follow their instincts, then you already have a threat hunting tool.
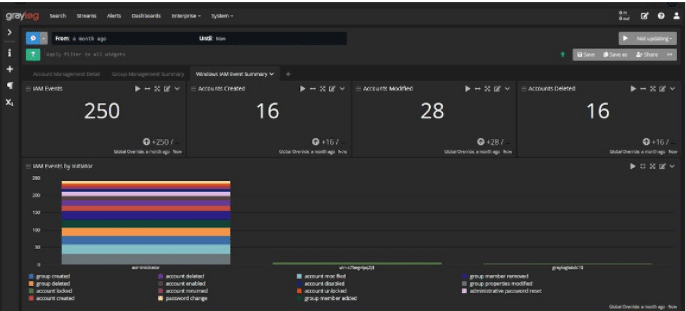
Use Case: Forgotten Password, Brute Force Attack, or Credential Theft?
Your IT team is used to getting password reset tickets. After all, people are forgetful. If they’re practicing good cyber hygiene, they may have multiple passwords. Plus, resetting passwords regularly as part of a more mature security program means they may remember an old one but not the most recent one.
If you’re using centralized log management, your IT team has better visibility into whether this is a one-shot forgotten password, a potential brute force attack, or a compromised credential arising from phishing emails. Often, multiple password resets in a short time frame are an IoC, meaning that cybercriminals are trying to find weak passwords to get into your systems and networks. This is where having real-time visibility with centralized log management helps.
Suppose your IT team uses centralized log management that makes following their gut instincts easy. In that case, they have a better chance of detecting a potential attack and possibly preventing it from being successful. If hunting down the root cause takes too long, they’re less likely to track down what’s most likely an accident that takes them away from more critical work.
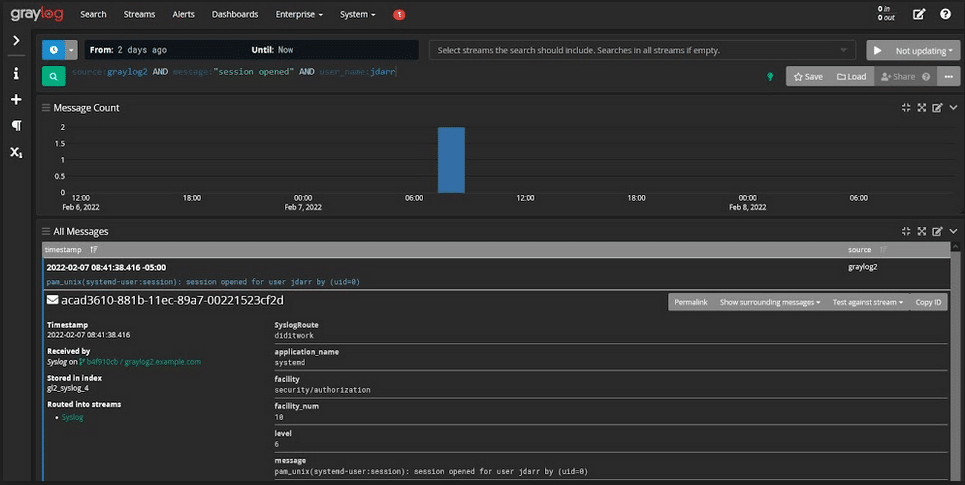
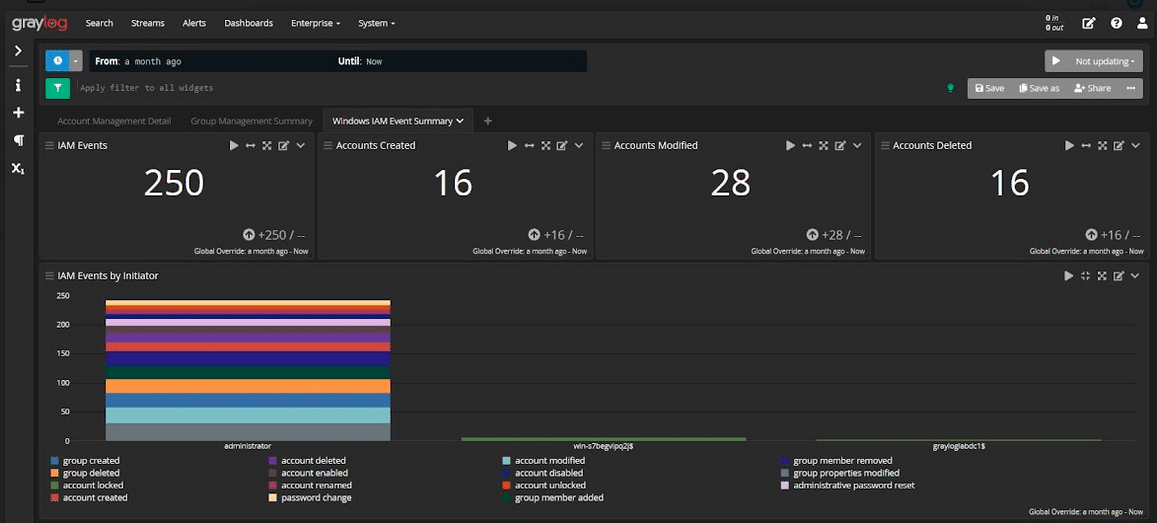
In a traditional security tool, it’s hard to do research without highly skilled staff because you need someone with experience to run the query. With centralized log management, you get the analytics-driven proactive security you need without having to retrain staff.
Use Case: Endpoint Security
As ransomware and malware attacks increase, endpoint security becomes more important. If you’re running an endpoint management tool, your IT team can see all the programs running on all employee computers.
This is where performing a specific hunt can bring value. For example, your IT team can run a query about all the programs running on all endpoints, then do a reverse sort. A reverse sort makes it easier to filter out the boring, high-usage programs like browsers, communication tools, and documents.
Instead, your team will see the programs that only a handful of people or a single person are running. While these outliers may not be risky most of the time, it’s the 1% of times when they are risky that matters. A single computer running PowerShell might end up being a threat actor using it to deploy malware or ransomware into the environment.


Graylog Empowers IT Teams to Do Threat Hunting
Sophisticated attackers can slip through alerts and predefined rules. Your IT team needs to go looking for these potential risks to find them. The problem is that this process takes too long with many tools and requires too many unique skills.
If your IT team can’t use the security tool, it’s a wasted expense. If they find nothing, then they’ve wasted their time. Having the right tools for threat hunting helps your team identify potential risks to things like network security or endpoint security.
If you’re using Graylog, your team can run simple queries and be empowered to take on information security functions as well. We built a centralized log management solution focused on the basics like field name and value. Your IT team can do all the zigging and zagging chart creations and necessary reporting without worrying about bulky code.
For example, with Graylog, your team members can add new terms easily without having to worry about increased search time. Graylog was built to enable curiosity with an interface that makes the research process – and the pivoting that can uncover security incidents – easy.
Our interface uses drop-down menus to add new search terms to their queries quickly. This increases the granularity available as they pivot, looking for potential issues.
Regardless of skill level, security analysts care about doing their jobs right and protecting a company’s data. Despite this, the cost-benefit analysis around the time a search takes and the likelihood of detecting an actual incident often means that they have a hard time prioritizing their searches.
With Graylog, IT teams can get the right balance of stability and flexibility.
Further, Graylog keeps everything easy and streamlined so your IT team can collaborate better. If a service team member needs to escalate the ticket because it’s outside their tier, they can share easily, giving everyone the ability to see everything they need.
Graylog’s centralized log management solution gives your IT team a way to do the threat hunting while eliminating the burdens normally associated with it.