Hey there, data detectives and server sleuths! Ever find yourself staring at a screen full of numbers and graphs, only to have one data point wave at you like a tourist lost in Times Square? Yup, you’ve stumbled upon the cheeky world of Anomaly Detection—where data points act more mysterious than your cat when it suddenly decides to sprint around the house at 2 AM.
So buckle up! We’re diving into the upside-down, inside-out, and occasionally ‘what-on-earth-is-going-on’ land of data anomalies.
Let’s get quirky!
1. Know Your Data: The Case of the Upside-Down Dog 🐕
Anomaly Detection is like trying to figure out why your dog suddenly slept in a weird position. Imagine if your furry friend, who typically sprawls out with his paws against the wall, suddenly starts sleeping curled up like a fox. It’s like, “Dude, what’s up? Is something wrong, you’re actually sleeping like a “normal” pup?”😂
Example: Let’s say you’re monitoring server response times. Normally, they average around 200ms. Then, out of the blue, they spike to 2 seconds! Knowing the typical behavior can help you quickly spot when something’s amiss.
2. Normalize Data: Giving Your Data a Spa Day 🧖♂️
Before you dive into anomaly detection, pamper your data a bit. Clean it, massage those missing values, and maybe even give it a facial (also known as normalizing). Let’s be real, nobody likes dirty data!
Example: Imagine you’re analyzing temperatures from sensors placed all over the world. Temperatures in Celsius mixed with Fahrenheit? That’s a recipe for chaos! Normalizing units ensures you’re not flagging a blistering day in California as an anomaly compared to a chilly one in London.
3. Structure Clear Objectives: What’s Your Endgame? 🎯
Think of this as setting your GPS before a road trip. Where are you headed? Are you trying to find a needle in a haystack, or are you monitoring traffic patterns on the freeway? Setting clear goals ensures you don’t end up on a wild goose chase.
Example: In e-commerce, are you looking for unusual purchasing patterns (maybe someone buying 100 rubber ducks at 3 AM) or sudden drops in website traffic during a sale?
4. Use the Right Tools for the Job: Not All Algorithms Wear Capes 🦸
Choosing the right algorithm is like picking the right wrench from a toolbox. Statistical methods, rules-based approaches…they all have their place. Make sure you’re not trying to hammer in a nail with a banana.
Example: Instant 🚩flag in real-time fraud detection for credit card transactions. You might opt for a rules-based approach where transactions above a certain amount or from certain high-risk locations.
5. The Never-Ending Story: Keep That Model Fresh! 🔄
If you think your job is done after setting up your anomaly detection model, think again! It’s like thinking you’re fit for life after one gym session. (Spoiler: you’re not.) Anomaly detection is an ongoing gig, and your data can throw curveballs. Over time, new types of anomalies may emerge, or what you considered “normal” might shift. Just like your music taste—remember when you were into boy bands? Yeah, let’s update that playlist.
Example: Let’s say you’ve set up an algorithm to detect fraudulent activity in an online gaming platform. Initially, the primary scam involved exploiting in-game currency. However, players found a new way to cheat via character cloning. If you’re not updating and retraining your model, you’ll miss this new trickery faster than you can say, “Game Over.”
Fantastic! The next part of the document discusses the pros and cons of customizing anomaly detection models. Let’s keep the techie quirkiness going, shall we?
To Customize or Not to Customize: That’s the Question! 🤔
So, you’ve got your anomaly detection up and running. Hold up, Sherlock! Before you consider your mission complete, let’s talk about customization. Yes, it’s like choosing toppings on a pizza—you’ve got pros and cons. (extend)

Pros of Customization: 🌈
- Laser-Sharp Accuracy 🎯: Look, you know your data better than anyone else. Customizing your model lets you tune it to a point where it can detect if a dotted “i” is missing in your data set. Yes, it’s that precise!
Example: You run an e-commerce site. A generic model might flag all big purchases as anomalies. Hey, you have a luxury section where big bucks are the norm! Customization lets you set domain-specific rules, avoiding those awkward “Did you really mean to buy this $10,000 handbag?” security checks.
- Knowledge Growth 🌱: As you fine-tune your model, you’re becoming the Sherlock Holmes of your data. You’ll get to the root cause of anomalies faster than you can say, “Elementary, my dear Watson.”
Example: In a content streaming service, your model might reveal that view counts dip every year during exam season. Aha, so it’s not a bug—it’s just that your audience is busy failing their exams.
- FP (False Positive) Reduction 🚫: Let’s face it, nobody likes a drama queen. Customized models reduce false alarms, so you don’t jump every time your phone buzzes.
Example: You operate a weather station. A generic model might flag a rainy day in Northern California as an anomaly (let’s be real, that IS rare). If you customize, you can set it to understand local weather patterns better.
Cons of Customization: 🌩️
- Cost: The Pricey Side of Custom 🤑: Customization sounds fun until you realize it’s like buying every topping at a frozen yogurt place. It’s expensive, and you’re probably going to regret it later.
Example: Building a custom fraud detection model for your financial services firm? You’re going to need to invest not just in the initial model creation. As well as the TLC of ongoing maintenance. Your budget might scream louder than a horror movie fan.
- In-house SME (Subject Matter Expert): The Guru Dilemma 🧙♂️: Unless you have a Yoda in your team who speaks data as fluently as he muddles syntax, you’re facing an uphill battle.
Example: You run an online education platform and want to customize the model to flag cheating during exams. If you don’t have an in-house expert in education and data science, good luck getting that model to work.
- Scalability: The Growing Pains 📈: Your model needs to adapt faster than a chameleon in a bag of Skittles. Scaling a customized model could require you to clone your SME. As far as we know, human cloning isn’t yet a thing.
Example: Imagine you start customizing your model for a small e-commerce site. Then, BOOM! Overnight success. Can your model handle the scale, or will it crash and burn like a one-hit-wonder’s music career?
There you have it, the full 411 on customizing your anomaly detection models. It’s not all sunshine and rainbows; there are storms you’ll need to weather. Let’s face it: What’s life without a little drama?
Keep your data close, & your anomalies closer! 🕵️♂️
Until next time, happy logging.
GRAYLOG SECURITY: STAYING ONE STEP AHEAD OF CYBER THREATS
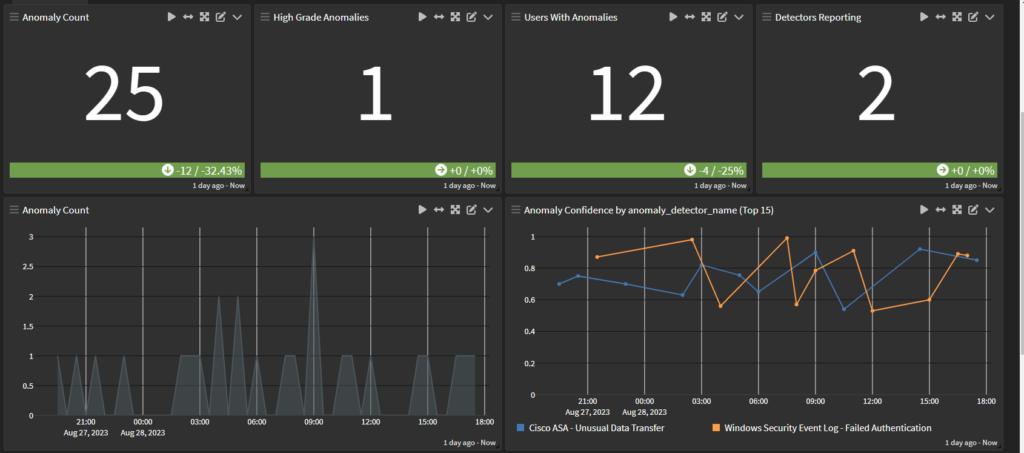
Graylog Security: Anomaly Detection, powered by Illuminate, is a game-changer in cybersecurity. Using Artificial Intelligence / Machine Learning (AI/ML), it scans your unique log data to identify anomalies and instantly alerts you to potential threats. This tool doesn’t just react to issues it enables proactive risk management. Keeping you a step ahead in the cybersecurity game.



