Ooops
The FireEye breach on Dec 8, 2020, was executed by a “nation with top-tier offensive capabilities.” These hackers got a hold of FireEye’s own toolkit, which they can use to mount new attacks globally.
What does this mean for you?
Mandiant is a leading Red Team/Penetration Testing company with a highly sophisticated toolkit, called the “Red Team tools.” These are digital tools that replicate some of the best hacking tools in the world. They use these tools (with permission) to find vulnerabilities in the client’s systems. Essentially, the Red Team hacks the systems to uncover weaknesses.
The Mandient Red Team tools have a unique signature. Many cybersecurity tools have the ability to use YARA rules for detection. If you have the technology to do so, your security experts can identify and classify malware incidents. However, since these recent attacks are at a level of unprecedented sophistication, the information is coming in bits. The good news is Graylog has an alert feature that can detect the signature from any log source in your organization with the signature/hash value in them.
We are going to walk you through how to take these bits of information from the YARA rules and create a rule in Graylog to alert when an IoC is detected.
NOTE: While there are many data sources for IoCs, in this article, we will focus on the countermeasures repository FireEye released after the incident. You can find this repository on GitHub and pull out the key bits of info (MD5 Hashes, IP Addresses, etc.) to alert and search in Graylog.
Creating a Graylog Alert
To create this alert, the data coming into Graylog must have the required fields (URL’s, MD5 Hashes, etc.) These URL’s, Hashes, and other IoC’s will continue to change as more is found out and known, as well as the next attack which happens. For our purposes, we use the MD5’s present in the GitHub link, but you can apply this to any IoC/Threat List. NOTE: It is important to pay attention to the way Graylog collects data to make sure it can match. If the IoC is a file name like MSIL/SharpZeroLogon, but data coming in only has SharpZeroLogon, it will not fire because it did not match.
There are many tools like Unix “grep/awk” or “Find” that you can use to extract out the IoC’s from the YARA signatures. Once you have found all of the IoC’s, you need to put them into a file, with one IoC per line. Graylog will use this file to fire alerts.
Setup
Log into your Graylog Instance, and first go to the System -> Lookup Tables -> Data Adapters, and create a MongoDB Adapter. Name it anything you like, and then Edit the adapter, and there you can add an entry. Give it a key name “MD5_Hash” in this case, and then paste in the values into the field like the picture below.
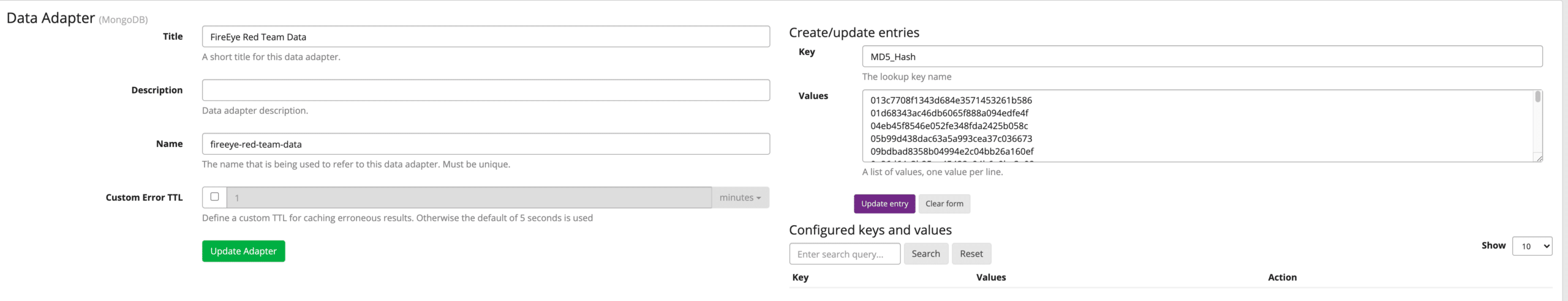
This will create the list of items to look for and alert on. Once done there, create a cache and the lookup table, as shown in the blog post on lookup tables.
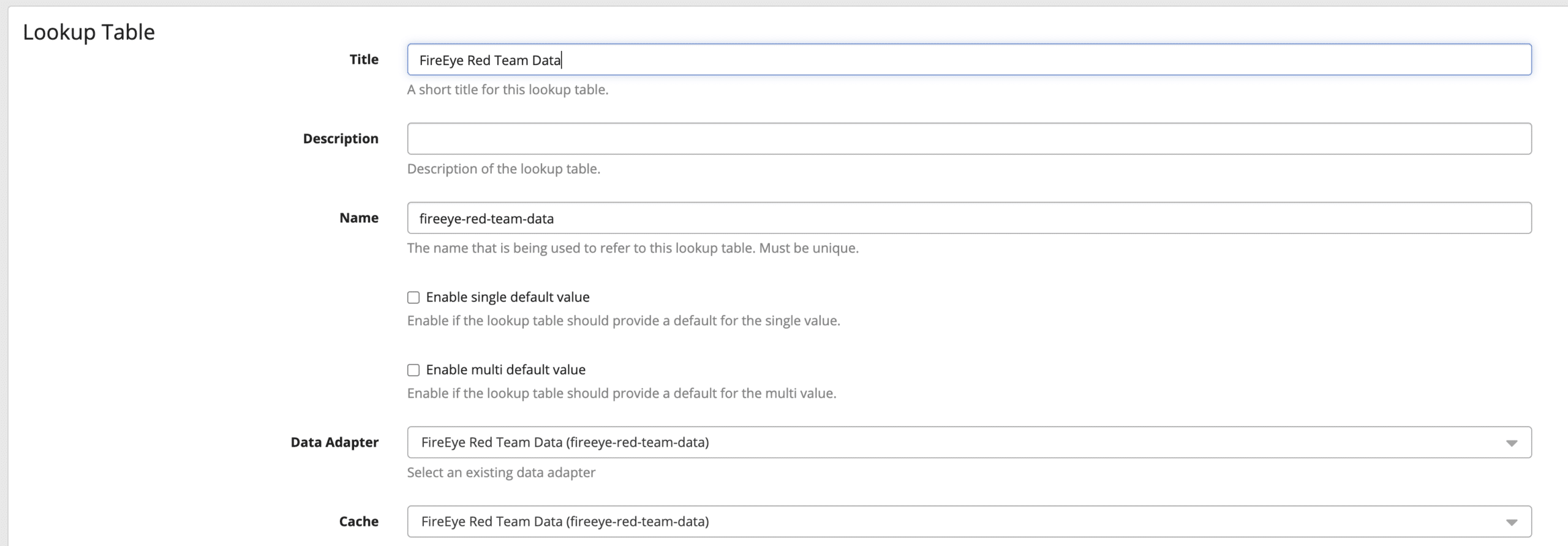
The Name does not matter, just remember what was created. Now go to Alerts -> Event Definitions and click “Create New Definition.”
On the first page, create the name and give it a priority. Here it is selected to be High.
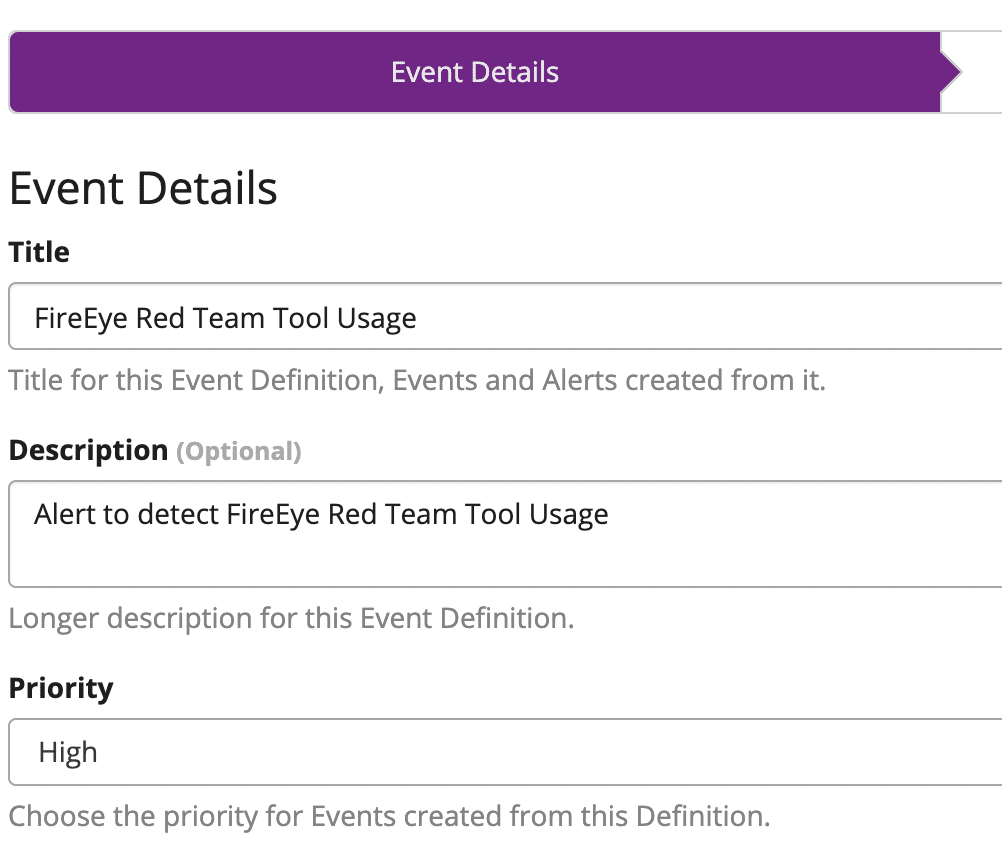
Select “Next” and on the Filter and Aggregation page, fill out the search query as shown, replacing the “MD5_Hash” before the colon with the field you will search on, so this could be a hash field or an IP address field for example.
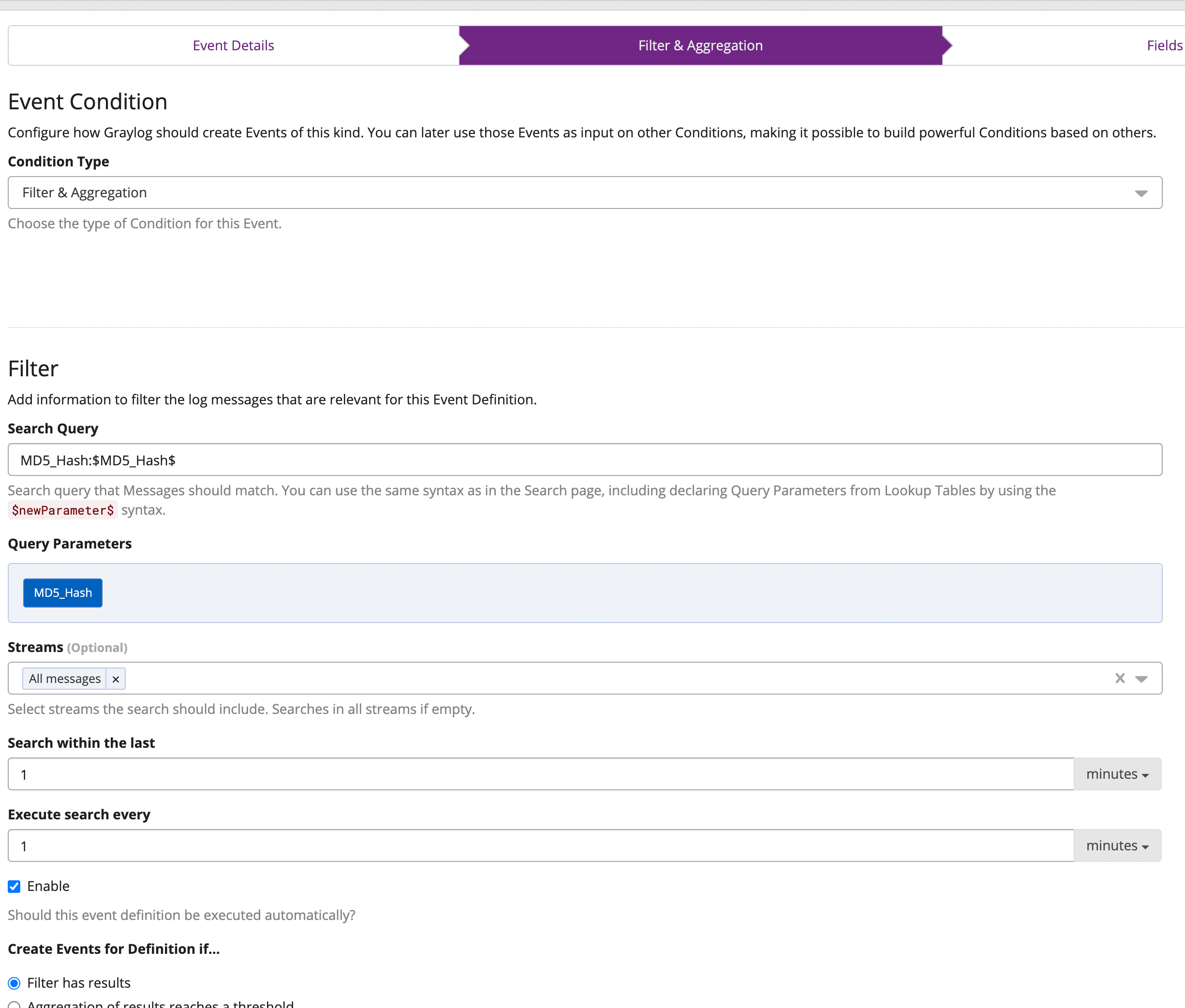
Here, the field is called MD5_Hash, and then after the colon, the parameter $MD5_Hash$, will ask you to define the parameter by clicking on the button saying undeclared.
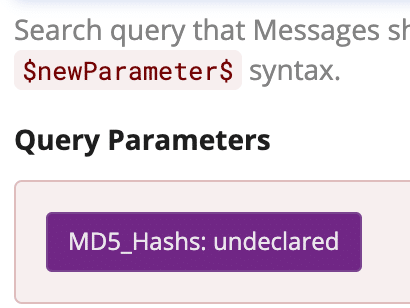
A pop out will show up, and you will have to select the lookup table from before and name the Table lookup Key field “MD5_Hash” in this example.
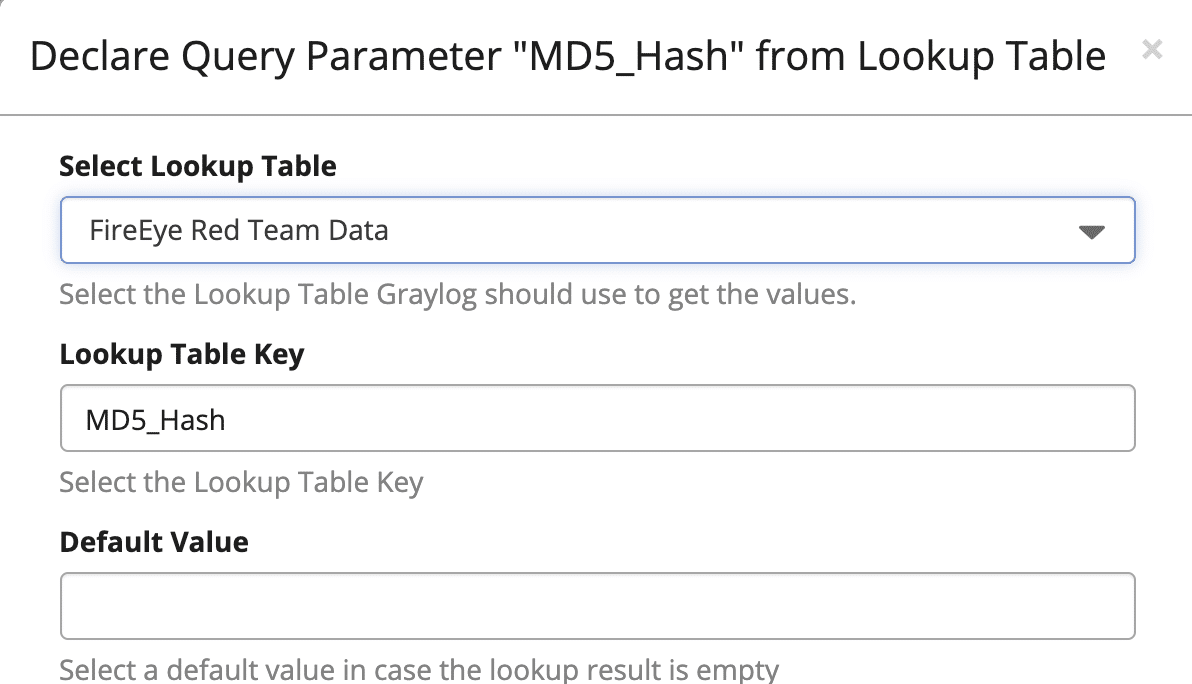
Save the pop out, and continue creating your alert to your liking, but select what streams of data to watch, the search intervals and how far back to search. If you need help with setting up alerts, refer to the alerting video.
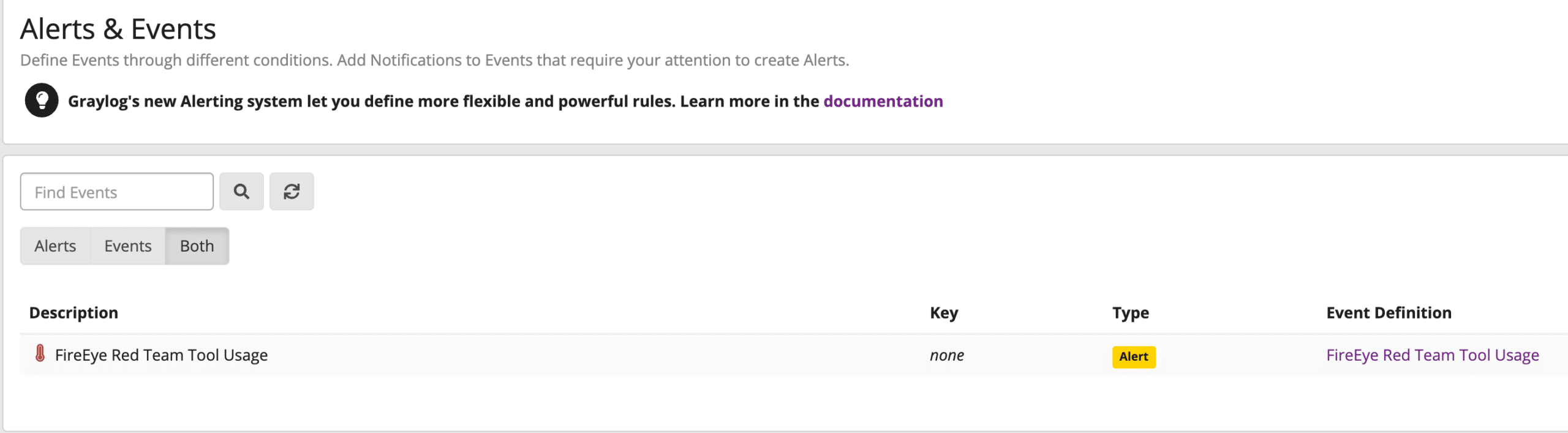
Once you’ve set up and enabled your alert, the next time you detect one of the IoC’s, you will see it show up on the “Alerts & Events” page:
Wrap Up
Breaches happen. Graylog can help you detect them when they’re happening will give you more time to respond. Also, keep an eye out for new IoCs and configure them using the method above.
While in this case, theIoC’s were made public. If you do not have an exact IoC to look for, you can start at a more generic level and create searches, for find broader topics in your environment–e.g.,
vendor_name:<companyName>
This is the best way to monitor whether you are the software discussed in this blog, in various industry publications, and/or in your Twitter feed.
Happy Logging!