Networks are the data highways upon which you build your digital transformation infrastructure. Like interstate highways transmit goods, networks transmit data. Every connected user and device is a network digital on-ramp. When malicious actors gain unauthorized access to networks, organizations must detect and contain them as quickly as possible, requiring security analysts to embark on a digital high-speed chase.
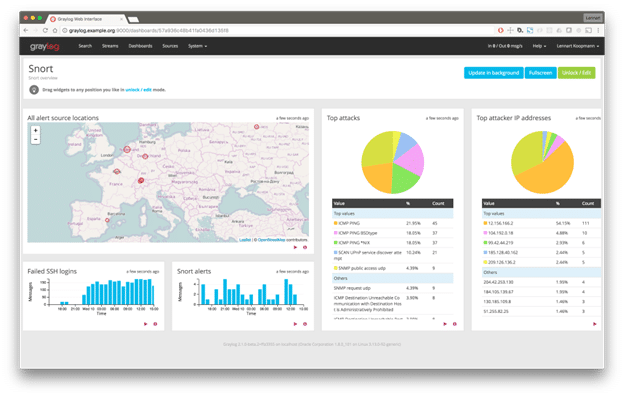
Monitoring networks with Snort IDS/IPS enables you to detect suspicious activity so that you can catch criminals before they cause irreparable harm.
What is Snort?
Snort is an open-source tool that provides real-time network traffic analysis, enabling security teams to monitor for suspicious activity. IT and security teams can use Snort in three different ways:
- Packet sniffer, like tcpdump
- Packet logger, like for traffic debugging
- Network intrusion detection system (IDS)/ intrusion prevention system (IPS)
Snort can detect a wide variety of attacks and intrusion patterns, and then it generates alerts with suggested actions to take.
Snort rules use a flexible language to combine:
- Vulnerabilities: flaws that make it easier for malicious actors to gain unauthorized access to data
- Signatures: distinctive markers associated with known attacks
- Protocols: ways that devices and systems communicate
Every rule contains the following information in the header:
- Action to take: what to do when a packet matches the rule criteria (Alert, Block, Drop, Log, Pass)
- Protocol: Type of traffic (TCP, UDP, ICMP, and IP)
- Source address
- Source port
- Destination address
- Destination port
Is Snort a sniffer?
Snort uses packet sniffing techniques to capture and analyze network traffic. However, the tool is more than just a packet sniffer. It uses protocol analysis and content matching to identify specific types of network traffic when identifying malicious activity and suspicious behavior. Snort has three basic modes.
Sniffer mode
When only reading and displaying a continuous stream of packets from the network, you can configure Snort to show:
- Only TCP/IP packet headers
- Only IP and TCP/UDP/ICMP headers
- Packet data and headers
Packet logger mode
When logging the packets to disk, you can configure Snort to show:
- Collect all packets and store them according to IP address
- Store everything in a single file that snort, tcpdump, or ethereal can read
Network Intrusion Detection System (NIDS) mode
Snort detects and alerts you to suspicious network traffic through two key capabilities:
- Content matching: matching specific strings of data within packets, like keywords and IP addresses
- Protocol analysis: examining network packets to determine content
Snort offers several different alert modes, each containing different information:
- Fast: timestamp, alert message, source IP and port, destination IP and port
- Full: fast mode data, TTL, packet headers, datagram length, service, ICMP types, window size, ACK, sequence number
- Unsock: exporting alert reports using Unix sockets
- Syslog: sending alert logs remotely
What are the benefits of using Snort?
Snort’s content matching and protocol analysis capabilities enable it to detect various network security issues.
Malicious packets
Snort’s performs real-time traffic analysis that can detect malicious payload including:
- Viruses
- Worms
- Trojans
Threats
Snort detects various threats including:
- Distributed Denial of Service (DDoS) attacks
- Port scans
- Buffer overflow
- Spoofing
Backdoor attacks
By analyzing network activity, Snort can detect attempts to exploit known vulnerabilities in operating systems (OS) and software that attackers use to install backdoors and gain unauthorized network access.
Zero-day attacks
Since Snort can detect abnormal activity on your network, it can help identify zero-day attacks that leverage new protocols or misuse existing ones by identifying deviations from expected protocol behavior. For example, Snort can detect attacks originating from potentially compromised sources, like infected devices being used as a botnet or malicious IP addresses.
Intrusion prevention
You can configure Snort to take prevention actions that include:
- Blocking traffic from specific IPs and ports
- Dropping packets that match rules or signatures
Correlating Snort IDS data with other events
By correlating Snort data with other events, you can create high-fidelity alerts, reducing false positives and alert fatigue. Securing and monitoring your networks is critical to your data protection program. While Snort provides real-time network traffic monitoring and analysis, you can’t gain all the data’s value unless you’re correlating it with other information from across your environment. As your organization adapts its monitoring and moves towards a zero trust architecture, using centralized log management with security analytics enables you to create a more complete view of your complex digital ecosystem.
Firewalls
By correlating your Snort and firewall data , you can gain valuable context around what’s happening in your environment. While both technologies inspect and analyze packets, firewall data can provide context about:
- Inbound and outbound traffic
- Application-level traffic
- Traffic between virtual machines
Identity and Access Management (IAM)
With people working remotely, you can correlate Snort and IAM events to mitigate risks arising from credential-based attacks. By combining data from these two technologies, you can gain visibility into the following:
- Who logged into the network
- When they logged onto the network
- Where they logged in from
Endpoints
Enriching your Snort data with endpoint security logs enables you to combine network monitoring with malware events. By correlating this data, you can more rapidly investigate the devices trying to transmit malicious packets to your networks.
Threat intelligence
You can add context to your Snort data with threat intelligence feeds. This context enables you to correlate your network activity data with things like:
- Indicators of compromise (IoCs)
- Ransomware data
- Known command and control (C2) destination IP addresses and domains
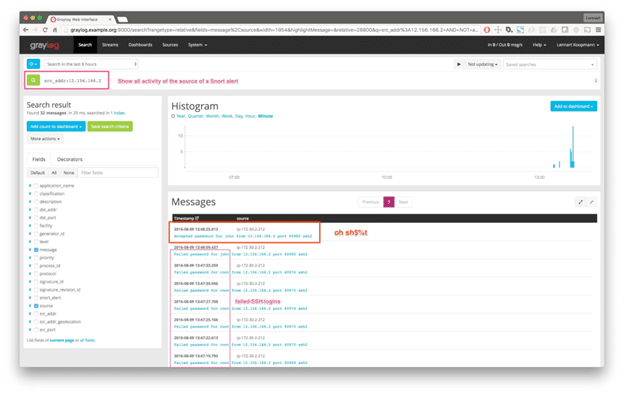
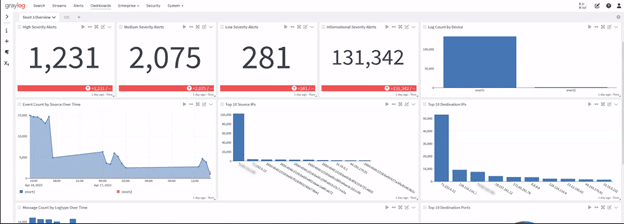
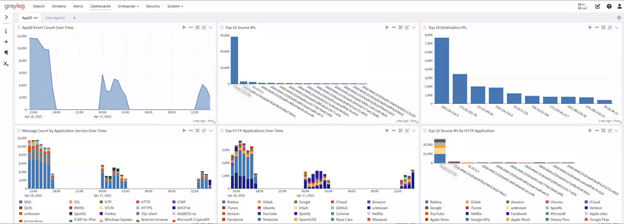
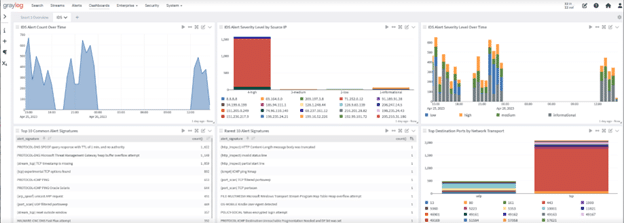
Graylog Security: Getting value from your Snort IDS/IPS
With Graylog Security, you get access to all of our pre-built content to get the search templates, dashboards, correlated alerts, reports, dynamic lookup tables, streams, and pipelines you need so that you can gain value from your logs faster. Using this pre-built content, you get alert rules, anomaly detectors, and dashboards that work across various log sources, enabling you to build high-fidelity alerts that correlate your Snort data with mission-critical log data, including those for endpoints and access. Included with your Graylog Security or Graylog Operations subscription, this content provides everything you need to ingest, sort, and process logs correctly so that you can enrich even messages and optimize your Graylog instance’s performance.


