Despite implementing cybersecurity administrative and technical risk mitigation control, companies still experience cybersecurity incidents and data breaches. Not every security incident ends with data exfiltration. An organization that can contain the attacker early in the kill chain can prevent data loss and reduce the incident’s impact. As security teams work to respond to the daily barrage of alerts, they need tools that enable rapid investigations for effective and efficient incident response capabilities.
To complete a cybersecurity investigation faster, security teams need tools with lightning-fast search capabilities that enable them to collect and preserve important data.
What is a cybersecurity investigation?
A cybersecurity investigation is the process of tracking a security incident’s root cause, including the collection, preservation, and analysis of digital information that indicates data tampering. Investigations include:
- Identifying the attack vector
- Determining when the incident began
- Detailing how long attackers had access to systems
- Locating and examining hidden, deleted, or overwritten files
- Recovering file fragments or obfuscated data
- Detecting embedded malicious code
- Compiling evidence about exfiltrated sensitive data
- Generating a timeline of events
Upon completing the cybersecurity investigation, the organization should be able to answer:
- What went wrong?
- What did it do to effectively recover?
- How will it prevent the incident from happening again?
What are the 5 steps of the cybersecurity investigation process?
If you’ve ever watched an episode of Law and Order, you already know the basic steps that the investigation process follows. When investigating a cybersecurity incident, your team needs to follow these basic steps:
- Collection: gathering digital evidence to track down the incident’s root cause and impact
- Identification: recording where all evidence was found
- Preservation: making a copy of evidence for analysis
- Analysis: manipulating the evidence to answer questions about the incident
- Documentation: detailing the critical findings and conclusion based on them
- Presentation: explaining the series of events to senior leadership
5 Best Practices for Completing a Cybersecurity Investigation Faster
While you can never be completely prepared for a cybersecurity incident, you can build processes and tools that speed up the investigation.
Continuously Monitor Sources of Precursors and Indicators
While this might seem more preventative than reactive, monitoring precursors and indicators by correlating events from across your environment means you have all the data in a single location which will make investigating and pivoting the investigation faster when it matters. Threat Detection utilizing frameworks like MITRE ATT&CK can help you narrow down where issues start.
You should start by collecting and correlating the following types of alerts in a single location:
- Intrusion Detection System (IDS)/Intrusion Prevention System (IPS)
- Antivirus software
- File integrity software
- Third-party monitoring services
Then, you can enrich this data with threat intelligence feeds and these types of logs:
- Operating system, services, and application logs
- Network device logs
- Network flows
By aggregating and correlating all your data sources in a single location, your investigation will be faster because you can trace your steps by using the data in the alert.
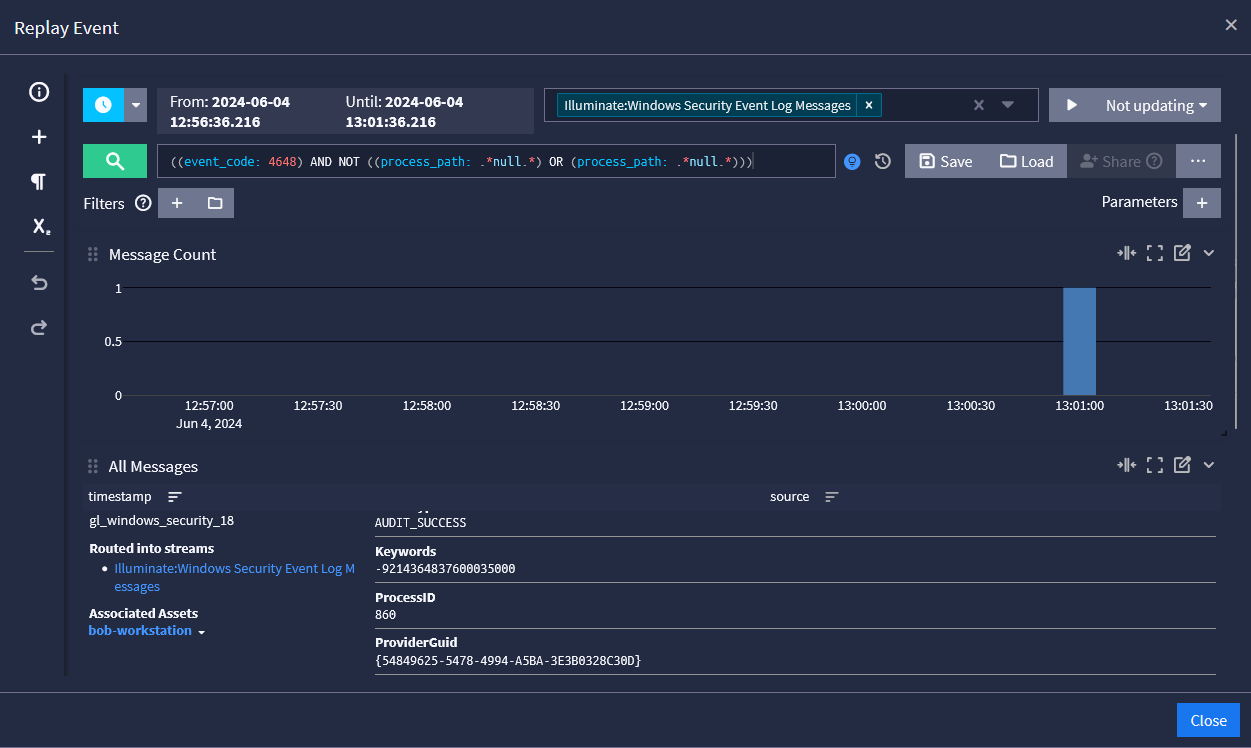
Prioritize Incidents Based on Business Impact
While all incidents are important, not all incidents will have the same impact. To streamline your investigations, you need to prioritize your research based around three key factors:
- Functional impact: current service outages and potential future functional impact if you don’t immediately contain the incident
- Information impact: effect on sensitive information’s confidentiality, integrity, and availability, including impact to partner organizations or overall mission
- Recoverability: time and resources necessary to recover weighed against the recovery effort’s overall value
- Risk Score: sorting and working on events with the highest risk score and prioritizing based on highest risk
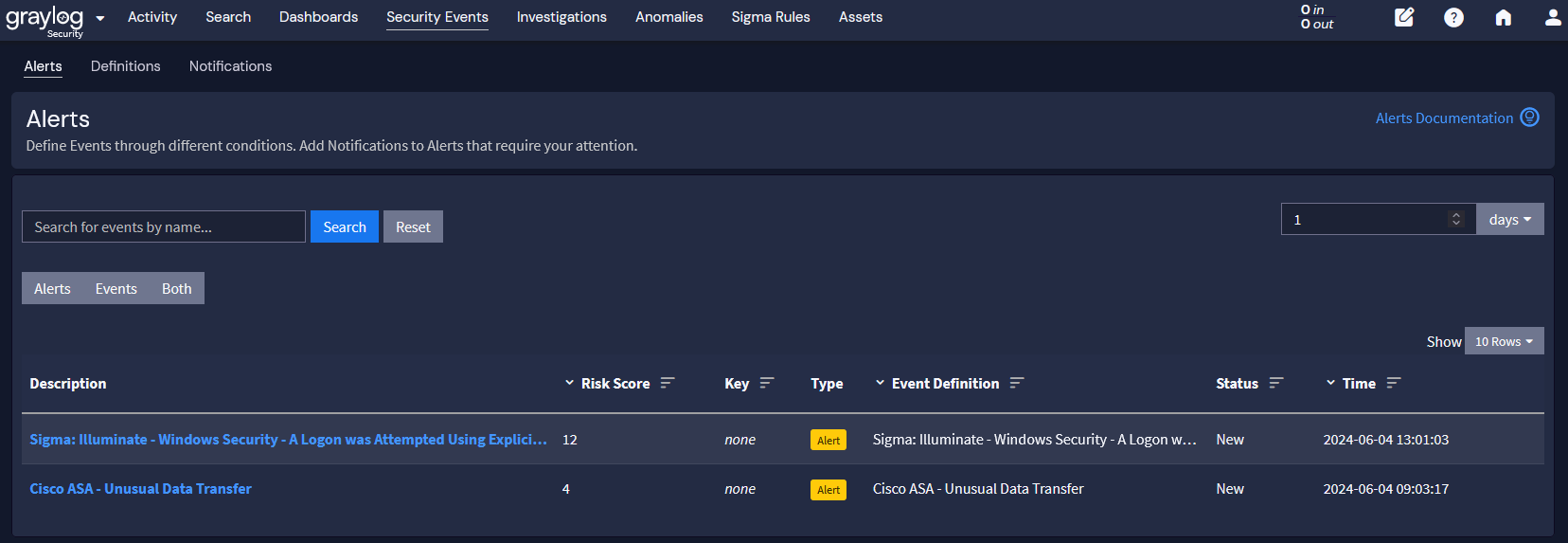
Prioritizing incidents and your response to them is critical, especially when comparing these three key factors. For example, an incident with root-level access to a server storing personally identifiable information (PII) should be a higher priority than a Distributed Denial of Service (DDoS) attack that slows down the network. On the other hand, if the PII has already been shared on the dark web, you can’t “recover” that information whereas you can recover service availability arising from the DDoS attack. In these cases, you would focus your PII event response on notification, eradicating the attacker, and preventing the incident from happening again. Meanwhile, your DDoS response would focus on restoring service.
Use Sigma Rules for High Priority Incidents
Sigma rules match criteria to log events to detect incidents about known attacker exploits. Threat Detection and Incident Response (TDIR) becomes easier when you are mapping attack types into categories of attacks. Utilizing Sigma Rules enable MITRE ATT&CK techniques to be identified and categorized.
For example, a Sigma rule for the supply chain attack “SmoothOperator” that exploited the 3CX client would look like this:
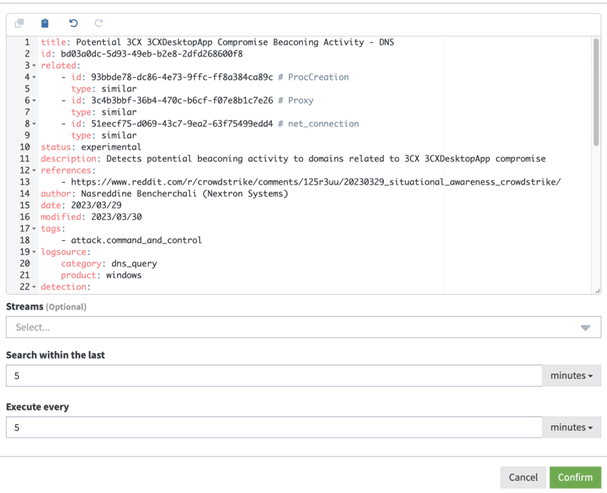
Sigma rules include many pieces of evidence that you use when engaging in a cybersecurity investigation, like:
- Technology involved
- MITRE ATT&CK mapping
- Keywords for analysis
Collect and Preserve Evidence in a Single Location
Since you may need to use evidence in the future, you must preserve it so that you maintain its integrity. Some examples of evidence that you’ll need to collect and preserve include lists of:
- Network connections
- Processes
- Login sessions
- Open files
- Network configurations
- Device memory content
If you have a centralized log management solution, you have a single location that:
- Collects, aggregates, correlates, and analyzes all log data
- Enables data storage and archiving
- Provides user access controls to preserve data integrity
Document and Share Findings in Cloud-Native Technologies
Since IT teams work remotely, handwritten logbooks are no longer effective. Incident response teams should be documenting their findings in a cloud-based location that enables them to maintain the information’s integrity and traceability.
By using a cloud-based documentation and tracking system, investigation teams can maintain records about:
- Current incident status, like whether it’s new, forwarded for investigation, or resolved
- Incident summary
- Incident indicators
- Related incidents
- Actions taken by all incident handlers on the current incident
- Chain of custody
- Impact assessments
- Contact information for involved stakeholders, like system owners or system admins
- Evidence list
- Incident handler comments
- Next steps
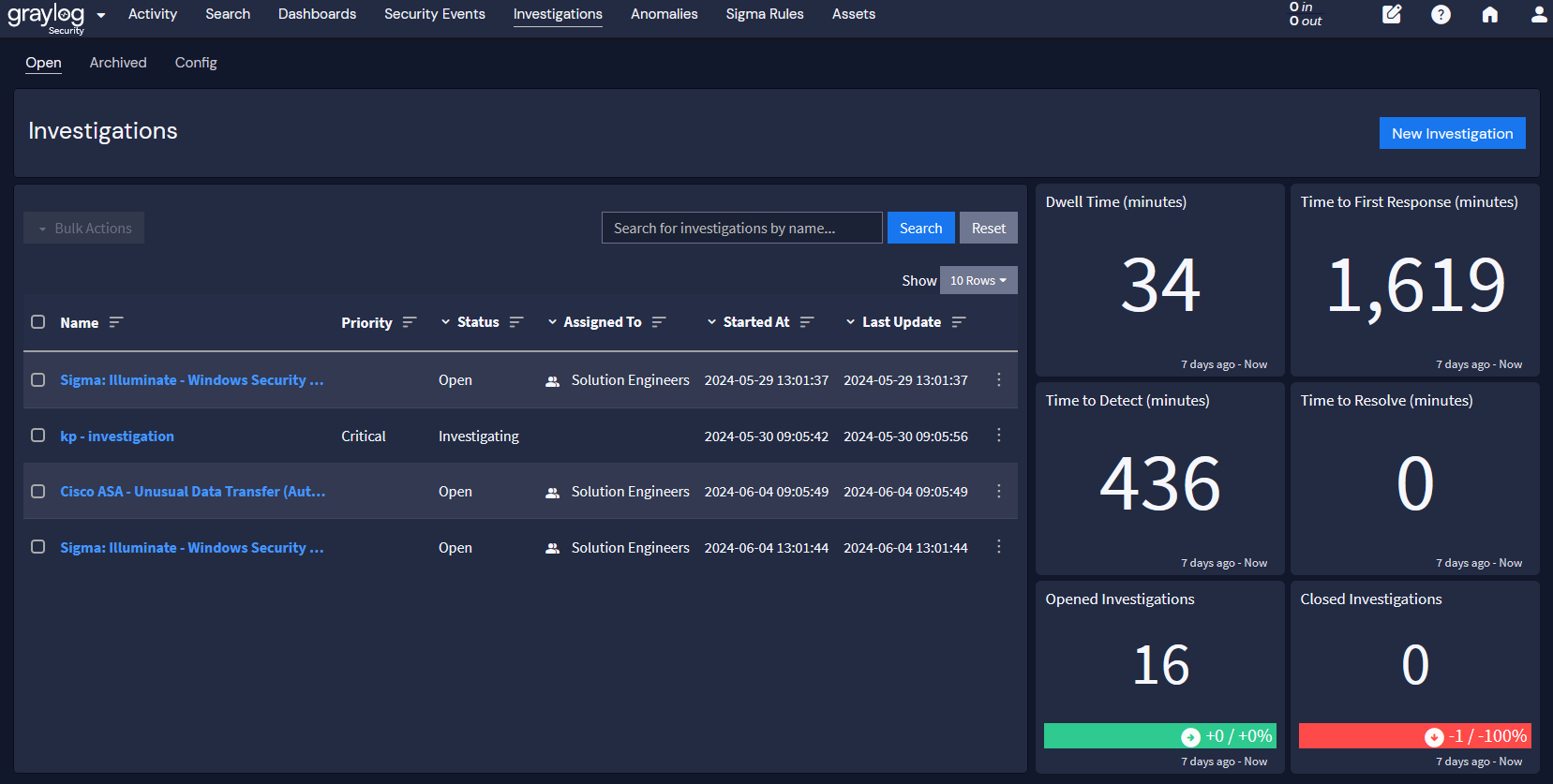
A cloud-native centralized log management solution with security investigation capabilities enables you to build a set of focused documentation that:
- Search your logs
- Prioritize incidents
- Assign responsible parties
- Collect and store evidence
- Record comments and findings
- Link to other incident investigations
Graylog Security: Cybersecurity Investigations at Lightning-Fast Speed
With Graylog Security, you get the speed, documentation, and sharing capabilities needed to complete investigations faster while storing critical incident data. With Security Investigations, you can create a new case, create custom prioritizations, document status, assign responsible incident responders, report findings, and link to log data evidence.
By leveraging Graylog Security’s out-of-the-box content and security analytics, you can build high-fidelity alerts then pivot directly into researching the log data that matters most. Our platform gives you all the functionality of a SIEM without the complexity, providing a robust technology that empowers users of all experience levels.
To see how Graylog Security makes cybersecurity investigations faster, contact us today.



