Graylog Enterprise v3.2 is out in the world, customers are using it and loving it, and we want to share with you what we’ve learned from them.
Like most departments, IT is buried with day-to-day activities. Proverbial system and user fires that need extinguishing get in the way of that list of projects gathering dust because nobody has time to get to them.
To ease this burden and give you back much needed time to tackle it all, Graylog focused the v3.2 release on usability and productivity. Specifically, we turned most of our attention to improving Search and Alerting features that support these key activities in log management that help you work faster and more efficiently.
LET’S START WITH SEARCH
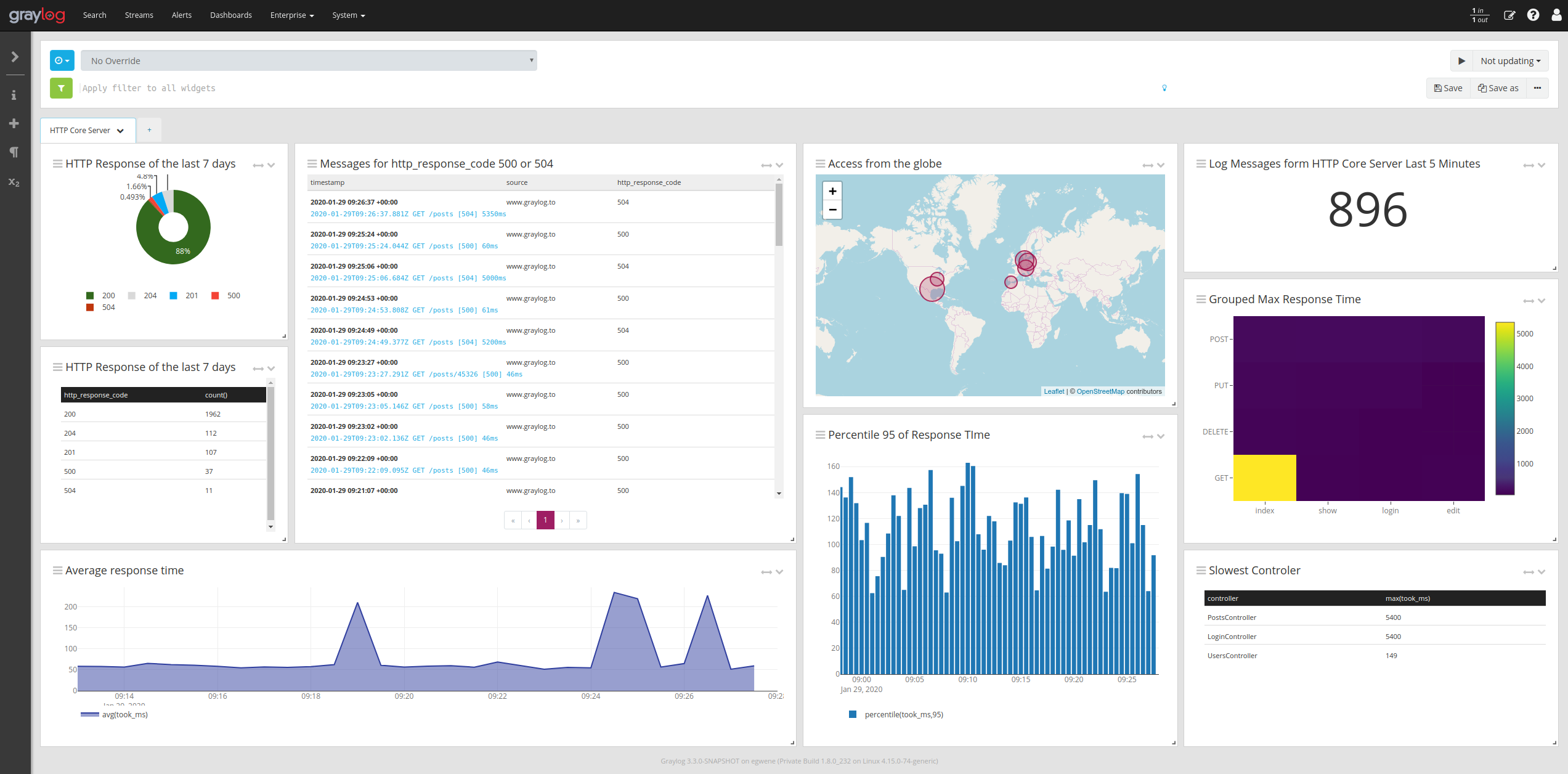
In v3.2, we unified the different search-like capabilities, Search, Extended Search, and Views, with Dashboard and Reporting widgets. On a practical level, this means everything is now presented on one screen, which makes it much easier to create sophisticated multi-search queries and view new or saved search results.
For example, a company received an alert that the server that is designated for the Finance team is showing a spike in CPU usage. To get to the root of the problem, the Analyst starts with a general search looking for all inbound connections to the server in the last 24 hours. Based on the results, it looks like it is coming from a spike in endpoint traffic, which is odd since there hasn’t been a big jump in authorized users recently. To narrow the search, the analyst creates a query that pulls back additional details on the endpoints ranked by CPU usage. The results show the problem is coming from three Mac users. It turns out that these three users updated their laptops, and are now incompatible with the kernel version on the Finance Server.
Working with 3.2, the Graylog Analyst begins in Search, sets up a query to perform the steps above, using the drop-down menus, he chooses how each query’s results should be visualized. We call this type of sequencing, “Search Workflow”. And because this is a pretty common issue investigation, the Graylog Analyst includes input parameters at the beginning, enabling the whole thing to be reused in the future by bringing up the saved search and typing in the server IP address where you are seeing a CPU utilization spike. (Maybe from a correlated alert set up in Graylog?)
Since the problem could arise again, and this is a mission-critical system, the Graylog Analyst adds the data visualization widgets to their Server Dashboard with a simple click of the down arrow next to the relevant search results.
MOVING ONTO ALERTS
Graylog Enterprise v3.2 sees two great additions to the Correlation Engine to reduce maintenance time and alert fatigue. First, you can add dynamic lists from other systems such as HR or Active Directory through Lookup Tables. This eliminates the need to manually update alerts when reference data changes. By incorporating data from other systems into your alerts, you can expand the intelligence of your alerts.
For example, if you want to make sure former employees are not accessing internal resources after their termination date, the IT team can set up a rule that references the “system of truth” for this data, matches to relevant user IDs, and sends an alert if authentication logs show activity on those user IDs. In larger companies, the list of employees who have left the company can change weekly, if not daily, and becomes a nightmare to maintain. Now, communication between HR and IT can be automated and you can rest easy that if for some reason their access credentials were not revoked, you will at least know if they ever do attempt to login to internal systems.
The second addition in v3.2 is the ability to build in multiple conditions into a single alert, creating more precise alerts to prevent alert fatigue and shrink the number of alerts that need to be created and maintained. Standard boolean logic is used here to build up alerts like “if there are 10 failed logins in a row, then a successful login, send an alert email.”
These Enterprise capabilities reduce the number of alerts you have to build, make the alerts more precise, and eliminate the need to update the alerting rules every time there is a change in the underlying comparison data.
IT’S THE LITTLE THINGS…
There are a number of other small improvements as well, all designed to create a faster, more unified, and user-friendly experience so that a wide range of users in your organization can get value from your log data using Graylog Enterprise.