In the fast-evolving landscape of digital connectivity, Application Programming Interfaces (APIs) play a pivotal role in facilitating seamless communication between diverse software systems. As organizations increasingly rely on APIs to power their applications, robust API security becomes paramount.
APIs – The Gatekeepers of Data
APIs act as the data gatekeepers, allowing applications to access, retrieve, and share information. However, this very gateway can become a vulnerability if not adequately secured. The repercussions of a breached API are severe, ranging from unauthorized access to sensitive data to service disruptions and even potential legal consequences.
Securing Your APIs
Securing your APIs is crucial for protecting both your organization and your users. A breach not only jeopardizes data integrity but also erodes customer trust. Rigorous API security measures, including encryption, authentication, and authorization protocols, serve as the first defense against cyber threats.
Furthermore, as APIs become more interconnected, the risk landscape expands. Each interconnected API creates a potential entry point for attackers. By implementing stringent security measures, organizations can ensure that their APIs are shielded from malicious intent, maintaining the integrity of their digital ecosystem.
Valuable Data at Your Fingertips
Graylog now offers a free-to-use platform to start security monitoring of your APIs. With the introduction of Graylog API Security V3.6, you have full feature parity to take advantage of the observability of your APIs. Let’s go through just some of the things you can observe with Graylog API Security:
Continuous API Discovery – Automatically discover and categorize all APIs, ensuring none stay under the radar!
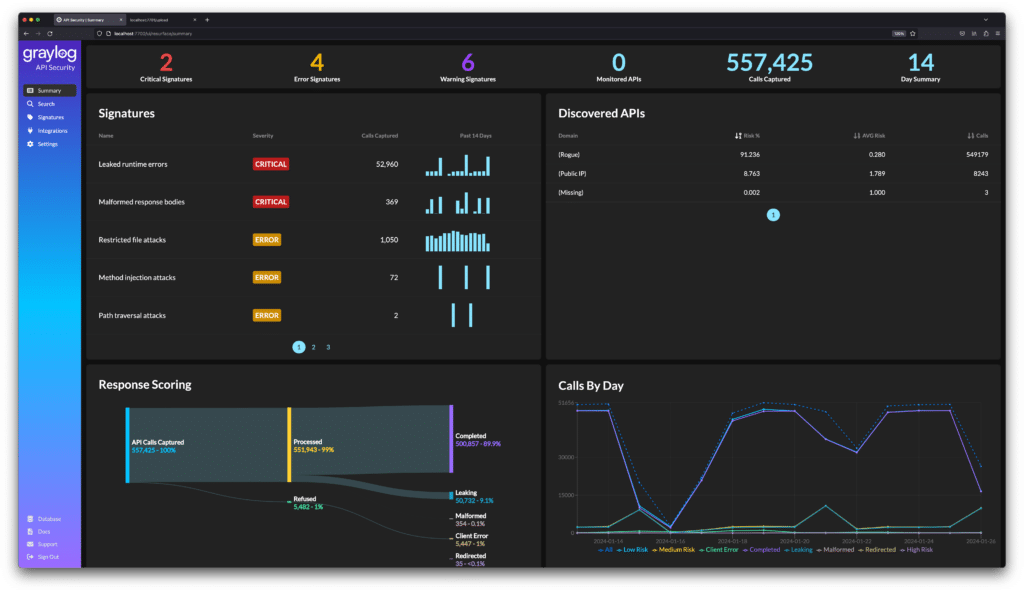
Unfiltered Request & Response Payload – Go beyond header data for precise alerts, retroactive threat hunting, and API-specific remediation.
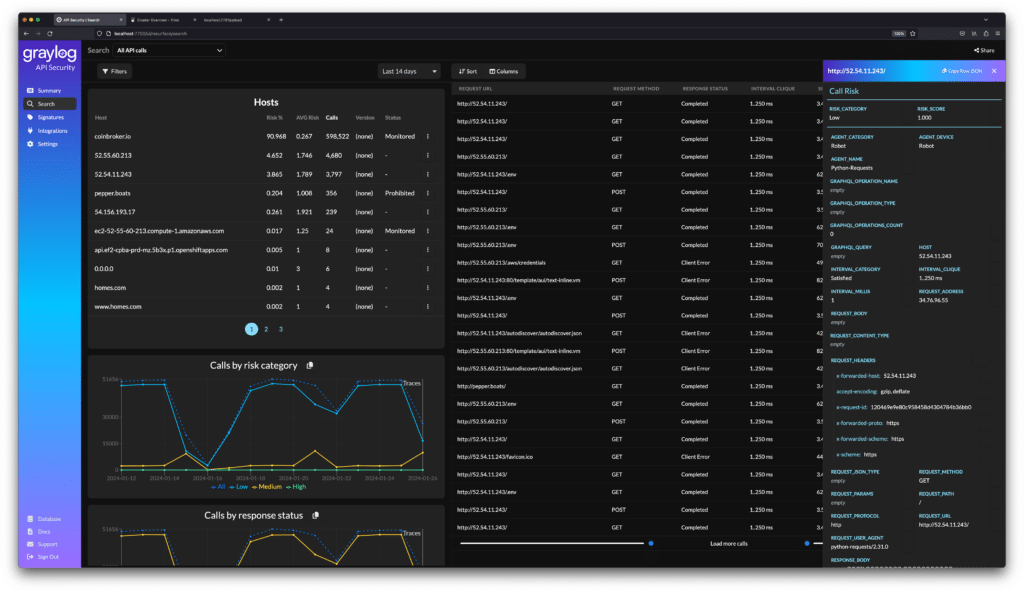
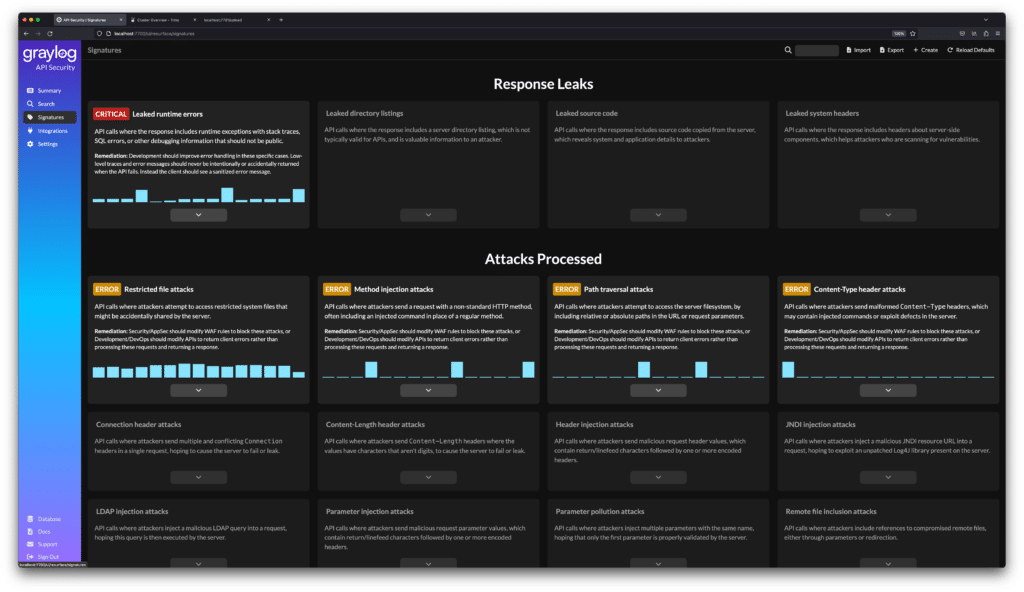
Automated Risk Scoring – Automatically highlight high-risk areas that need immediate attention based on the type of API being monitored (REST, GraphQL, JSON).
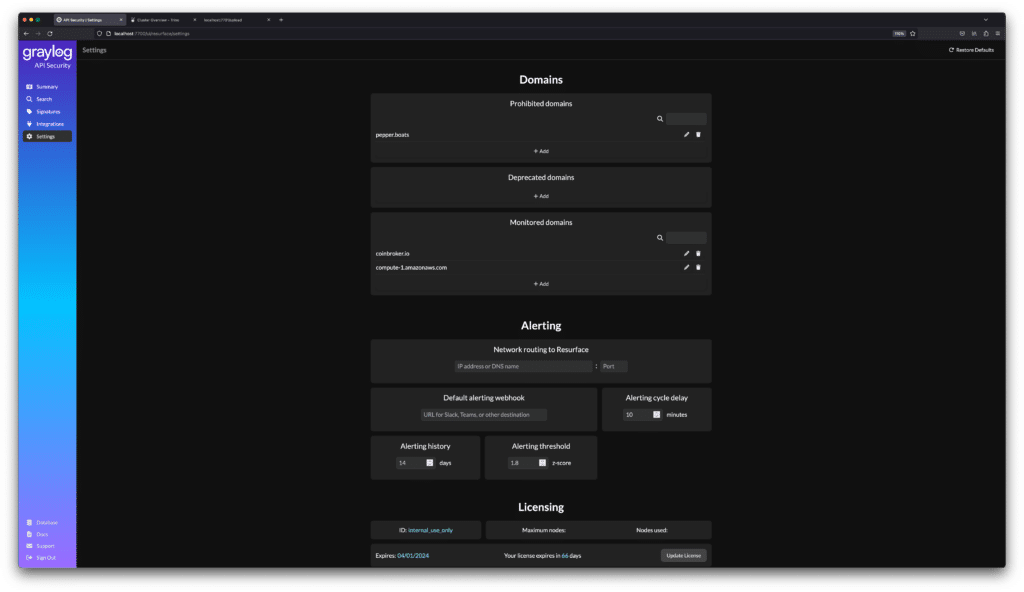
Guided Threat Detection & Response – Get alerts with clear explanations and actionable steps.Secure Self-Managed Solution – Keep sensitive data in-house, avoid third-party disruptions, PII concerns, and the red tape of SaaS security reviews.
Secure Self-Managed Solution – Avoid third-party disruptions, PII concerns, and the red tape of SaaS security reviews.
Get API Security Now
Build your micok8s or Kubernetes cluster, or deploy Graylog API Security in your favorite Cloud, and start using it. You can find more information by going to our product page. Check out our documentation for all the important things you need to deploy Graylog API Security.
Here’s what you’ll need to get started:
- A Single Node Install
- One License per organization
- Annual renewal of license
- A 6 Core CPU with 18GB of Ram



