Anyone who’s ever misplaced their wallet knows that horrible moment where their stomach drops, the beads of perspiration begin to form on their forehead, and they start mulling over worst-case scenarios. In that worst case scenario, someone used the cash and cards in the wallet to go on a personal spending spree.
In a company’s IT environment, a missing device or shadow IT represents that missing wallet. When companies fail to appropriately manage their IT assets, they create a risk that attackers will discover a vulnerability and then go on a data-exfiltration spree.
With a robust asset management program, companies gain visibility into all hardware, software, and digital storage locations so they can implement appropriate security controls.
What is asset management?
Asset management is the set of processes, policies, and technologies that a company uses to:
- Identify its technologies, including hardware and software
- Manage the asset lifecycle
- Make data-driven provisioning decisions
By creating an asset inventory, organizations have insight into the devices, operating systems, and software within their environments.
Why Is Asset Management Important to Cybersecurity?
In a digital world, daily business operations rely on technology. When organizations lack visibility into their IT assets, they create cybersecurity blindspots, opening the door to an attack. Asset management sits as the sturdy foundation upon which a company can build a strong cybersecurity and data privacy program.
Enhance compliance
Nearly every data protection compliance mandate starts with an asset inventory that identifies all:
- User devices, like mobile devices and workstations
- Routers
- Switches
- Servers
- Load balancers
Since any one of these assets can create a security risk, you need a comprehensive listing of them so that you can engage in a risk assessment.
Mitigate risk
You can’t protect an IT asset if you don’t know you have it. With asset management, you create a comprehensive inventory that includes:
- IT assets
- Locations
- Device owners/users
- Vulnerabilities
- Configurations
By knowing and tracking all devices and software, you can implement and monitor security controls.
Control and locate hardware
With an IT asset management (ITAM) tool, you can keep track of all devices and manage their security better. ITAM enables you to track the device life cycle across:
- Location
- Ownership
- Maintenance history
In a work-from-anywhere world, IT assets are no longer tethered to a workstation. From laptops to smartphones, people bring their devices with them. By tracking an asset’s location, you can identify anomalies that indicate potential loss or theft. Wen connecting your asset inventory to a configuration data
Control software and operating system versions
Asset management includes knowing the software and operating systems running on your devices. From a cybersecurity standpoint, this information can help you identify:
- Unpatched software or operating systems
- Devices with End-of-Life (EoL)/End-of-Service (EoS) software or operating systems
- Unused software
Typically, an organization maps its asset inventory to its configuration management database (CMDB) or its vulnerability management technology. By doing this, the organization’s asset management program enables the IT and security team to monitor for potential risks or put additional controls around risky assets.
Categorize assets
When you know the assets that you have, you can associate them with specific projects or IT services to identify critical assets. Critical assets are the resources that drive the organization’s business operations and whose unavailability would lead to business disruption.
Identifying and categorizing critical assets means looking at:
- Who uses an asset
- Why people need it
- How much internal or external users rely on it
- Whether it interacts with sensitive data
By linking them to their respective owners or teams, you can prioritize and focus your security monitoring activities.
Enriching IT Asset Data with Centralized Log Management and Security Analytics
Centralized log management with security analytics enables you to correlate data from across your IT environment.
Continuously Monitor Critical Assets
Once you categorize an asset as business-critical, you need to implement the appropriate controls and monitor for abnormal activity that indicates a potential attack. When you use a centralized log management solution that includes security analytics, you can:
- Aggregate critical assets within the inventory using category tags
- Create dashboards that focus on these assets
- Use these categories and dashboards to prioritize your threat hunting activities
Track Responsible Parties to Install Security Updates
When you correlate your asset inventory with your CMDB, you can create alerts for noncompliant devices. For example, a user may not have been connected to your domain at the time a patch was released so the device remains vulnerable.
By enriching your data with the asset inventory, you can:
- Identify noncompliant devices
- Track device owners
- Work with them to install the update
Create Focused Alerts for High-Risk Assets
Often, organizations need to create compliance exceptions for unique devices. For example, a company may need to keep a device that still runs Windows 7, even though Microsoft no longer supports it.
By incorporating your asset inventory into your centralized log management solution, you can create high-fidelity alerts and monitoring dashboards for these exceptions that monitor:
- Network traffic
- Malware signatures
- User access
By correlating this data and creating specific dashboards for these risky devices, you can monitor them more closely to prevent attackers from exploiting unpatched vulnerabilities.
Investigate Incidents Faster
In security, the more data you have, the faster you can identify and investigate an incident. With the ability to create dashboards based on specific asset groups, you can investigate incidents faster.
For example, you can identify all assets associated with a server, giving you a way to narrow down potentially impacted devices. By pivoting directly within your monitoring solution, you reduce the time it takes to investigate the alert and can limit attacker dwell time.
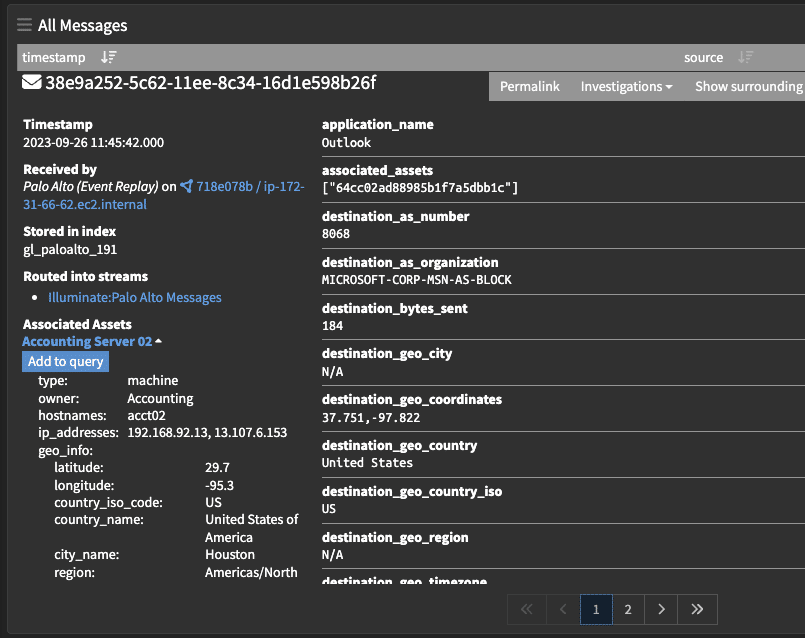
Graylog Security: Enriching Data with Asset Management
With Graylog Security’s asset management content pack, you can create the asset inventory necessary for identifying risk and monitoring cybersecurity. By leveraging Graylog Security’s out-of-the-box content and security analytics, you can build high-fidelity alerts then pivot directly into researching the log data that matters most. Our platform gives you all the functionality of a SIEM without the complexity, providing a robust technology that empowers users of all experience levels.
To see how Graylog Security makes cybersecurity investigations faster, contact us today.



