What is the Trusted Information Security Assessment Exchange (TISAX)?
The Trusted Information Security Assessment Exchange (TISAX) is the certification process for engaging in the Verband der Automobilindustrie (VDA), the German Association of the Automotive Industry, Information Security Assessment (ISA). The ENX Association, a collection of automobile manufacturers, suppliers, and four national automotive associations, established TISAX to create an overarching industry standard and make reporting more efficient.
The ENX Association provides governance for TISAX by:
- Approving audit providers
- Monitoring implementation quality
- Managing assessment results
- Maintaining a criteria framework (TISAX ACAR)
Aligned to the International Organization for Standardization (ISO) 27000-series and the General Data Protection Regulation (GDPR), the VDA ISA acts as the basis for:
- Self-assessment determining the organization’s current information security posture
- Internal audits
- External audits in accordance with TISAX
The VDA ISA establishes five maturity levels for measuring an organization’s controls:
- Level 0 (Incomplete): process not implemented or able to achieve objective
- Level 1 (Performed): process implemented and achieves objective but not documented
- Level 2 (Managed): process that achieves objective is implemented and documented
- Level 3 (Established): integrating standard process into overall systems, including documented process across dependencies with evidence proving sustainability and activity over extended period
- Level 4 (Predictable): following and monitoring an effective and established process by reporting key performance indicators (KPIs)
- Level 5 (Optimizing): Following and continuously improving a predictable process by providing dedicated resources
Who does TISAX apply to?
TISAX applies to any organization providing products and services across the automotive industry supply chain including Original Equipment Manufacturers (OEMs) and their business partners, including those who provide:
- Vehicle design
- Vehicle manufacturing
- Vehicle distribution
- Marketing services
- Sales services
- IT services
TISAX identifies the following assessment levels:
- Assessment Level 1 (AL 1): low trust level assessment where auditor checks whether an organization has a self-assessment but looks for no additional evidence
- Assessment Level 2 (AL 2): plausibility check where auditor reviews evidence supporting the self-assessment and conducting interview with the responsible party
- “Assessment Level 2.5”: full remote assessment where auditor verifies whether information security fulfills applicable requirements but doesn’t engage in on-site activities
- Assessment Level 3: comprehensive verification where auditors examines documents and evidence, conducts planned interviews with process owners, observes local conditions, observes process executions, and conducts unplanned interviews with process participants
What are the key provisions of TISAX?
The VDA ISA consists of three sections:
- Information security: basic controls based on ISO 27001 and assess according to the defined maturity levels
- Prototype protection: requirements for protecting vehicles, components, and parts that the OEM classifies as needing it
- Data protection: controls aligned to the General Data Protection Regulation (GDPR)
Information security
The information security requirements include the following categories:
- Policies: identifying information security objectives aligned to business strategy, legal compliance, and contractual obligations
- Organizational controls: establishing an information security management system (ISMS), identifying responsible parties, engaging in risk assessment when classifying projects, defining internal and external IT service provider responsibilities
- Asset management: engaging in an information asset inventory, identifying business-critical assets, completing a risk assessment when procuring external IT services
- Information security (IS) risk management: assessing risks regularly and in response to events, assigning a risk owner to each identified risk
- Assessments: engaging in internal and independent compliance audits
- Incident management: defining, detecting, investigating, and reporting security events and vulnerabilities, establishing escalation procedures, remedial actions, and communications strategies
- Human resources: conducting employee background checks, signing non-disclosure agreements, requiring compliance with information security policies, providing cyber awareness training, defining telework information security requirements
- Physical security and business continuity: establishing policies for physical access, managing visitors, owning/transporting traditional and mobile devices, business interruption, disaster recovery, and asset lifecycle management
- Identity and access management (IAM): establishing user credentials, authenticating users to systems, managing the identity lifecycle, establishing a password policy, allocating access rights on a need-to-use basis tied to a user’s role or area of responsibility
- IT Security/ Cyber Security Cryptography: encrypting data transferred via public or private networks, managing the cryptographic key lifecycle
- Operations security: formalizing change management procedures, separating development, testing, and operational systems, protecting against malware, collecting and analyzing event logs, implementing vulnerability and patch management processes, regularly auditing IT systems, regularly auditing network access and segmentation
- System acquisitions, requirement management, and development: considering information security requirements when developing, acquiring, or deploying IT systems, network services, external IT services, segregating client data when providing external IT services
- Supplier relationships: managing third-party information security risk through contractual obligations that require service and audit reports, requiring non-disclosure agreements as part of contracts
- Compliance: reviewing legal, regulatory, and contractual compliance requirements, incorporating compliance into policies, implementing processes and procedures in compliance with relevant national legislation and regulations
Prototype Protection
While many of the controls within this section focus on physical security, several also related to data and digital systems:
- Physical and environmental security: protecting against unauthorized entry and access control, like using digital cards or codes for entry
- Organizational: managing nondisclosure agreements, securely storing, deleting, disposing, transmitting, and shipping images of vehicles, components, or parts classified as requiring protection, defining secure processes for carrying mobile video and photography to protect against unauthorized image recording or access
Data Protection
While the Data Protection category references the information security category, it focuses on personally identifiable information with additional questions for organizations that act as processors under GDPR Article 28. These protections include:
- Implementation: appointing a data protection officer (DPO), determining data protection coordinators across various departments
- Organizational measures: specifying data protection principles in an internal data protection policy, implementing work processes for processing PII, contractual obligations for subcontractors, employee confidentiality agreements, and handling consumer requests that assert rights
- Quality checks: proving review and optimization of data protection management system by providing metrics for confidentiality and integrity during data transfers, access limitations, and awareness training
- Documentation: Documenting essential activities, customer support for executing data protection impact assessments, informing customer of unlawful data processing
VDA ISA Event Log Requirements
The VDA ISA incorporates specific requirements for handling and managing event logs. ISA requirement 5.2.4 states:
Event logs support the traceability of events in case of a security incident. This requires that events necessary to determine the causes are recorded and stored. In addition, the logging and analysis of activities in accordance with applicable legislation (e.g. Data Protection or Works Constitution Act) is required to determine which user account has made changes to IT systems.
According to the ISA, the “must-haves” are:
- Information security requirements around how to handle event logs
- Security-relevant requirements about logging system administrator and user activity
- Assessing the need to log IT systems
- Options for monitoring external IT services
- Regularly checking event logs for rule violations and noticeable problems
Further, the ISA identifies the following “should-haves”:
- Procedures for escalating recent events to the appropriate responsible parties, like security incident responders, data protection officers/coordinators, corporate security, IT security
- Protection event logs, including contents and metadata, against alteration
- Monitoring and recording network activity relevant to information security
Additional requirements for data that requires high protection needs include:
- Protecting the confidentiality, availability, and integrity of the event log
- Logging access during connection and disconnection of external networks
For data with very high protection needs, the ISA requires organizations to log any access to data of very high protection needs as far as technically feasible and legally permissible.
Centralized Log Management with Security Analytics for TISAX compliance
Implementing a centralized log management solution with security analytics streamlines your TISAX audit by providing visibility into:
- User access
- Network security
- Endpoint security
- Vulnerability and patch management
- Data exfiltration/data loss
Paired with user and entity behavior analytics (UEBA), you achieve further capabilities for:
- Proactive threat hunting
- High-fidelity alerts for advanced detection capabilities
- Rapid vulnerability remediation
- Lightning fast incident investigation
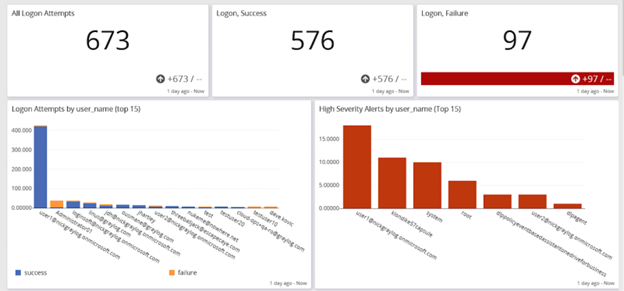
Access Monitoring
Ingesting entity and access management (IAM) tool logs into your centralized log management solution and pairing that with UEBA enables you to manage:
- Privileged access management (PAM)
- Password policy compliance
- Abnormal privilege escalation
- Time spent accessing a resource
- Brute force attack detection
Network Security
Your centralized log management solution aggregates, correlates, and analyzes data generated from various network security monitoring tools, enabling high-fidelity alerts indicating a potential security incident.
For example, you can combine firewall data with intrusion detection system (IDS)/Intrusion prevention system (IPS) for information about suspicious traffic and potential evasion techniques.
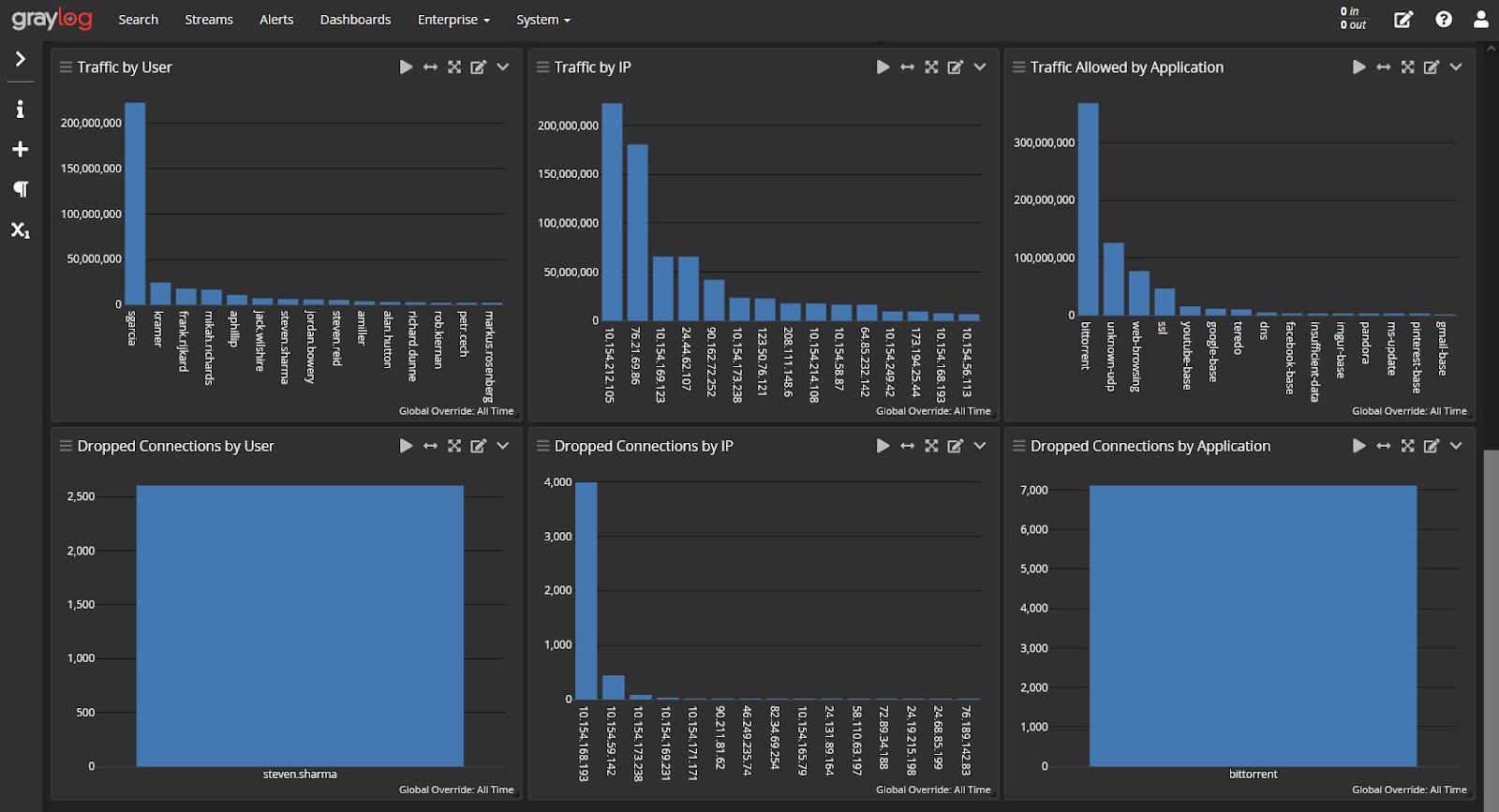
Integrating this with security analytics enables you to define baselines for normal traffic that enhance detections for abnormal activity.
Data Exfiltration
Building dashboards infused with security analytics enables you to create high-fidelity alerts that incorporate threat intelligence. With the ability to combine network monitoring, antivirus logs, and UEBA, you can create detection rules for anomalous data downloads that could mean a potential incident.
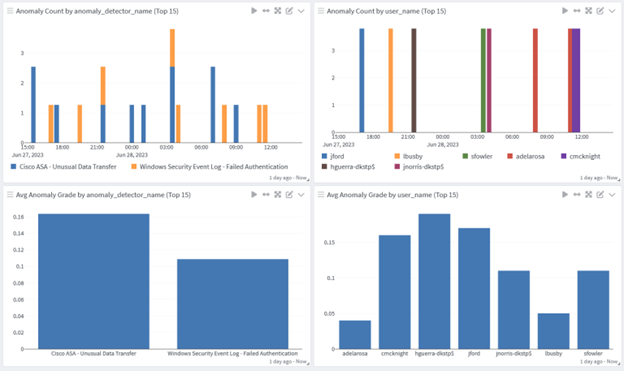
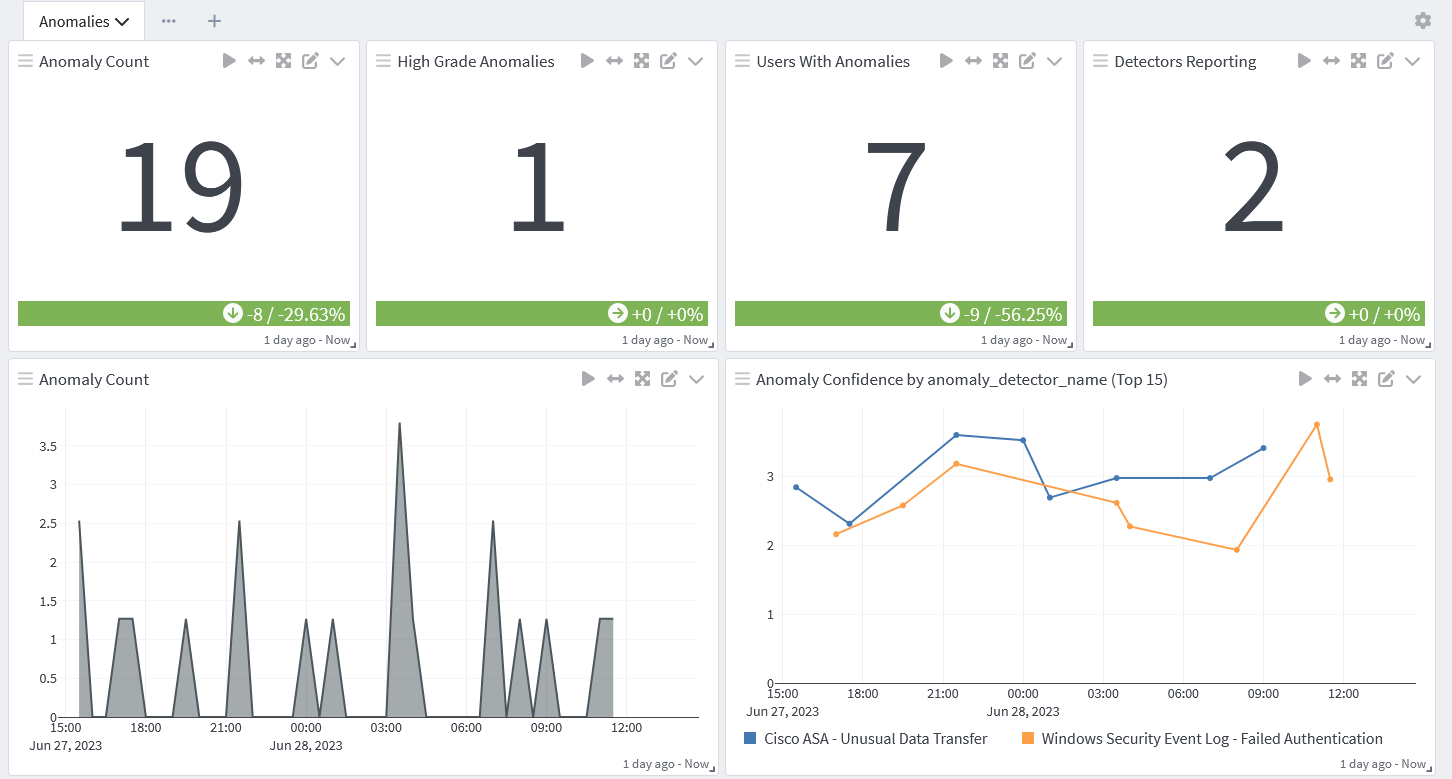
Incident Response and Automated Threat Hunting
To implement proactive monitoring, you can create queries using parameters rather than specific value, you can optimize your searches to gain real-time insights and answers. Automating these searches enables advanced threat hunting for visibility into:
- Abnormal user access to sensitive information
- Abnormal time of day and location of access
- High volumes of files accessed
- Higher than normal CPU, memory, or disk utilization
- Higher than normal network traffic
Compliance reporting
You can build dashboards that collect the information an ISA audit requires, reducing the time it takes to respond to document requests. Further, you can build reports that enable your leadership team to evaluate a security incident.
For example, a dashboard can show:
- Start of incident: when logs documented changes
- Incident activities: what types of changes the logs documented to highlight what the threat actor tried to do
- Containment/Eradication: when logs stop reporting the activities indicating the threat actor is no longer acting in the system
Graylog Security: Security analytics for TISAX compliance
Graylog Security’s intuitive user interface enables you to create the high-fidelity detections that prove your information security and data protection processes achieve their objectives. With our analytics, anomaly detection, prebuilt search templates, dashboards, correlated alerts, and dynamic look-up tables, you gain all the value of a security incident and event management (SIEM) technology without the associated costs and complexity.
To see how Graylog Security can help you achieve your TISAX certification, contact us today.




