GitLab’s audit logs offer a goldmine of insights into user activity, project changes, and security events. Getting that data into Graylog for centralized analysis is easier than you might think—especially with the flexibility of our Raw HTTP input and Illuminate’s GitLab Spotlight Pack. In this two-part guide, we’ll walk you through how to get it done, from wiring up GitLab’s Audit Event Streaming to visualizing enriched events in a purpose-built dashboard.
Part 1: Setting Up the Raw HTTP Input for GitLab
GitLab supports Audit Event Streaming to HTTP destinations, which means we can stream logs directly into Graylog—no custom code or forwarding agents required. All we need is a properly configured Raw HTTP input and a few settings on the GitLab side.
Prerequisites
Before diving in, make sure you have:
- A valid GitLab account with permission to configure audit streaming.
- A Graylog instance with a Raw HTTP input configured and reachable from your GitLab instance.
Note:
Want to use local install of GitLab, follow GitLab click here
Want to use Cloudflare Logpush click here
Step-by-Step: Configure GitLab to Stream Logs
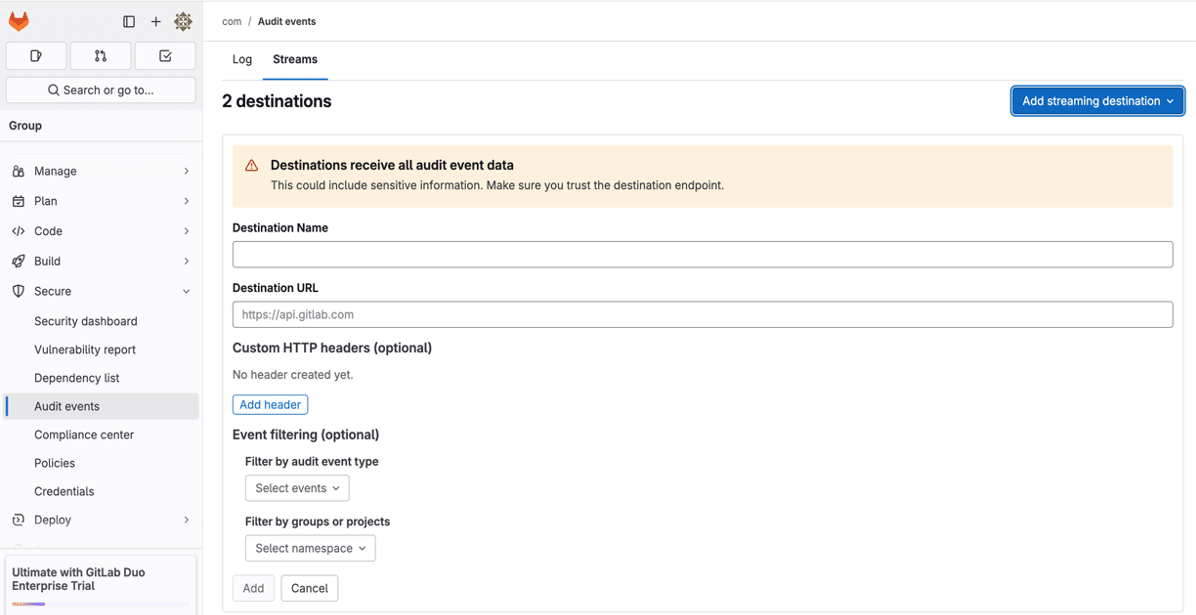
Start in GitLab:
- Destination Name: Pick something recognizable like graylog-audit-stream.
- Destination URL: Use the public-facing address for your Graylog Raw HTTP input—e.g., https://your-graylog-server.example.com/raw.
- Custom Headers: Match the header name/value pair defined in your Graylog input config to help secure the stream.
- (Optional) Event Filtering: Depending on your use case, you can control which types of audit events are sent.
Step-by-Step: Configure the Raw HTTP Input
In Graylog, head to System > Inputs and launch a new Raw HTTP input. Key settings include:
- Bind Address & Port: Ensure it’s reachable by GitLab.
- Authorization Header: This should match the custom header GitLab sends—name and value.
- TLS: GitLab requires HTTPS, so either enable TLS or route through a proxy/gateway that handles it.
- Enable Bulk Receiving: This is essential. GitLab sends log batches, so this must be checked to parse them correctly.
You can keep most other input settings at their defaults unless your environment requires something specific.
Part 2: Enriching GitLab Logs with Illuminate
Now that your logs are flowing, let’s make them useful. The GitLab Content Pack—available to Enterprise and Security customers using Illuminate—helps parse GitLab’s structured log data and aligns it with the Graylog schema for analysis and correlation.
What’s Included?
This pack gives you:
- Field parsing rules for all known event_types
- Schema-compatible enrichment
- Three dashboards:
- Events Overview
- User Overview
- Web Overview
Requirements
- Graylog 6.1.3 or later
- Graylog Enterprise or Security license
- GitLab v17.9
- Raw HTTP input (dedicated to GitLab logs)
Setup Instructions
- If not already done, set up a dedicated Raw HTTP input for GitLab logs.
- In GitLab, configure Audit Event Streaming to use this input as a destination.
- In Graylog:
- Navigate to the input and click Show received messages.
- Copy the gl2_source_input value (you’ll need this in a moment).
- Go to Enterprise > Illuminate > Customization.
- Edit the lookup_adapter_input_routing
- For content_name, enter the input ID you copied.
- For input_id, enter gitlab.
That’s it! Your logs are now parsed, enriched, and routed through Graylog’s schema.
Heads-up: GitLab logs contain both standard and custom fields. Fields not defined in the schema will be prefixed with “vendor_“.
Dashboards In This Spotlight
Once the content pack is configured, you can view GitLab data across three dashboards:
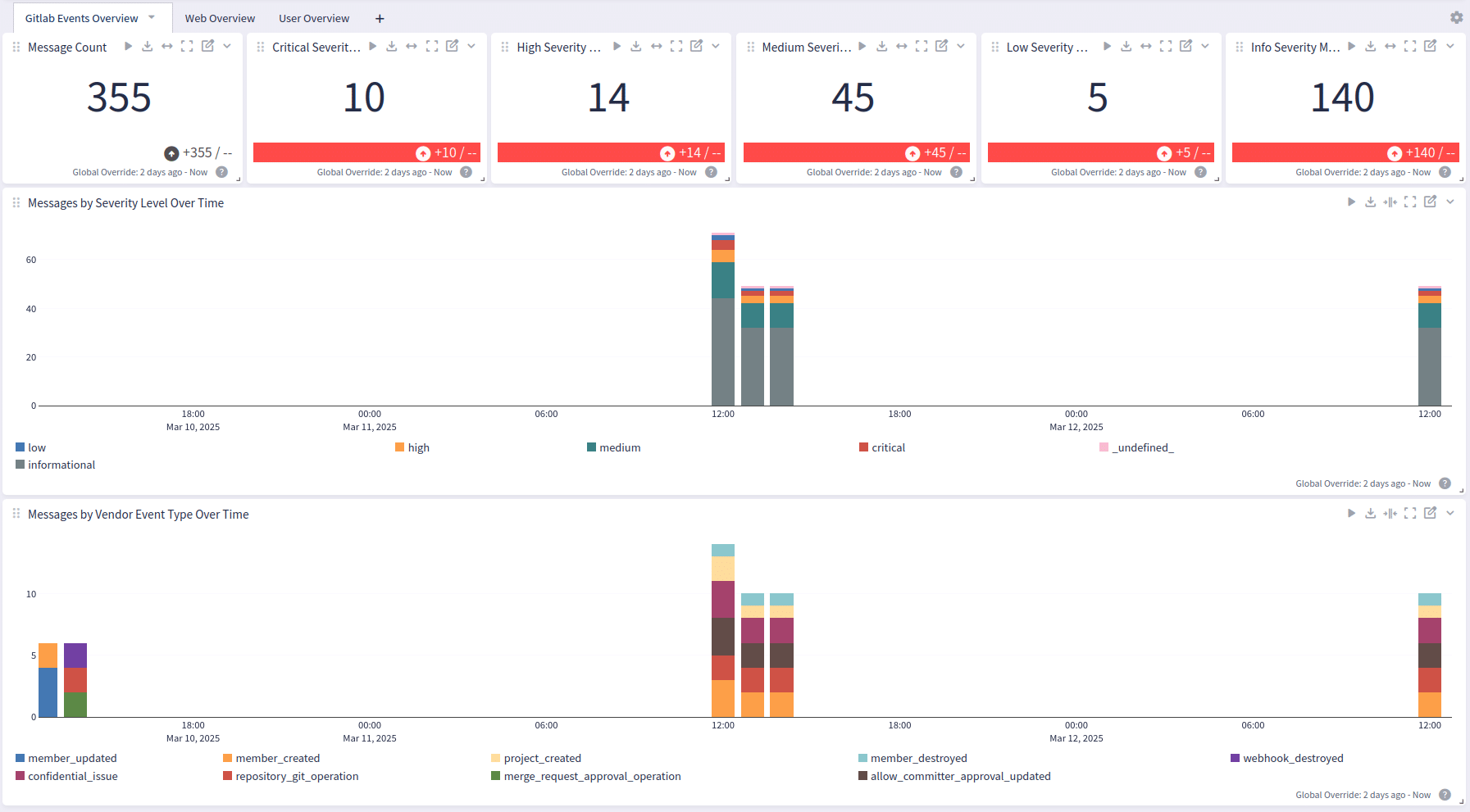
- GitLab Events Overview – Events across your environment
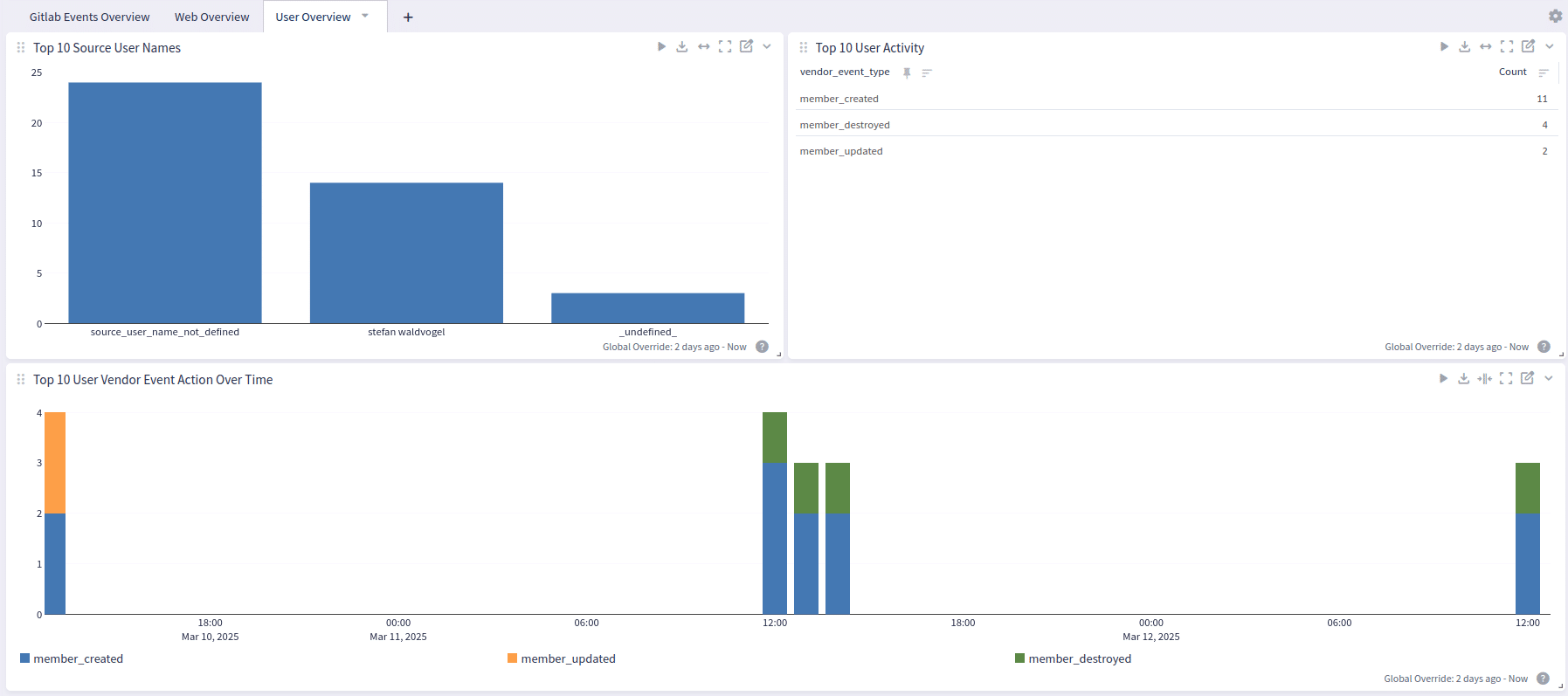
- User Overview – Activity by user
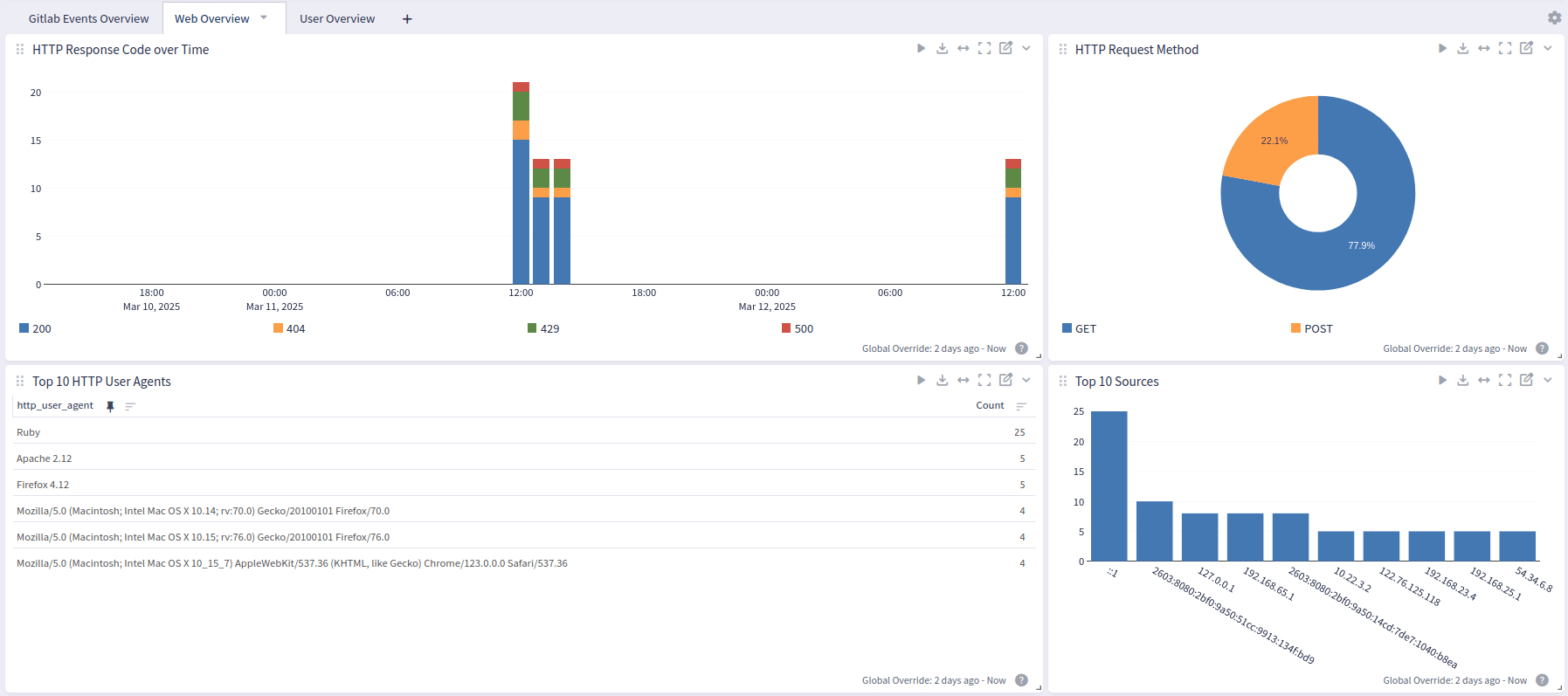
- Web Overview – Web-based audit activity
They’re plug-and-play—and fully customizable if you want to tailor them for your team.
Ready to Centralize GitLab Logs?
If you’re already using Graylog, this integration is a low-lift way to bring GitLab logs into the same workflows you use for threat detection, investigations, and compliance. And if you’re not using Illuminate yet—let’s talk. This kind of parsing power is what makes Graylog truly operational for DevSecOps teams.
What’s Next
- Need help configuring? Go to Graylog Docs → Raw HTTP Input
- Configuring Illuminate GitLab Spotlight? Go here.
- Interested in Illuminate? Contact Sales



