Like every industry, the manufacturing sector has embraced digital transformation to improve operations. Digital manufacturing uses technologies like Internet of Things (IoT) devices, data analytics, and cloud computing to improve production processes and gain efficiencies.
With businesses increasingly embracing digital transformation, they face the challenge of securing interconnected systems. Cybercriminals target the manufacturing industry for various reasons, like corporate espionage and financial gain. With many manufacturers considered part of critical infrastructure, successful attacks can have a more profound impact across the economy.
To protect against these threats, implementing robust cybersecurity for digital manufacturing means knowing the risks and having controls in place to lessen an attack’s impact.
What is Digital Manufacturing?
Digital manufacturing integrates advanced technologies into current processes, often by incorporating sensors into manufacturing machines and connecting them to networks. These sensors collect data and transmit them to connected applications, providing data-driven insights.
Traditional manufacturing facilities maintained machines that were physically separated. The modern factor relies on an integrated set of technologies that includes:
- Robotics: automating manual tasks like machine tending, welding, packaging, palletizing, and screw-driving
- Simulation: computer models that digitally test manufacturing processes and procedures
- Industrial Internet of Things (IIoT): sensors and devices connected to machines and physical assets
- Additive manufacturing: computer-controlled processes for creating three-dimensional objects
Why are Manufacturing Companies Embracing Digital Transformation?
Manufacturing companies are increasingly embracing digital transformation because the new technologies provide various benefits, including:
- Inventory management: collecting data to feed analytics models for insights that improve supply ordering, product storage, product restocking, and future forecasting processes
- Supply chain visibility: communications between manufacturers and suppliers about raw materials and finished products
- Predictive maintenance: analytics models that create alarms and alerts for reducing unplanned downtime, time spent managing maintenance, unnecessary maintenance checks
- Asset monitoring: tracking assets location, usage, and movement around the factory
Cybersecurity Challenges in Digital Manufacturing
In a traditional factory, physical security measures protected the machines because they never connected to the internet. Without network connectivity, operational technology (OT) assets could have vulnerabilities in their operating systems, software, or firmware because they remain isolated from the enterprise IT environment. However, digital manufacturing changes this.
Converged IT/OT/IoT Environments
For the connected applications to provide value, IoT and IIoT devices transmit data across the organization’s enterprise IT infrastructure. However, these devices come with inherent security risks, including:
- Lack of baseline security standards
- Infrequent security updates
- Inability to install malware or antivirus tools
Legacy Technologies
Traditional OT systems could be secured with physical and logical network segmentation. By limiting direct access to the technologies, organizations could implement robust security. Connecting these systems to the internet with IoT/IIoT means that the traditional security methods no longer work. Without maintaining secure configurations or remediating vulnerabilities, attackers can use these technologies to gain unauthorized network access.
Threat Actor Sophistication
Attackers can gain unauthorized access to a traditionally isolated network by targeting the IoT/IIoT device’s human-machine interface (HMI). Since they connect the remote systems to the manufacturing floor, attackers can get initial access to systems then move laterally to achieve objectives.
Integration Risks
To gain the full value of their IoT and IIoT deployments, manufacturers often use Application Programming Interfaces (APIs) so that the connected applications can share data with other technologies. Attackers target APIs because they are difficult to identify and secure, creating another layer of cybersecurity risk.
Best Practices for Securing Manufacturing 4.0
Manufacturers should take a comprehensive risk management approach to protecting their converged environments.
Centralize All Security Data
Every technology generates log data that manufacturers can use to monitor their security. Centralizing all security telemetry in a single location enables you to correlate and analyze events across your environment. By extending security monitoring and governance across IT, OT, and IoT/IIoT logs, you can ensure that security controls remain consistent and effective across the different network segments and technologies.
Leverage Threat Intelligence
Threat intelligence will help you understand the types of attacks occurring in the real world, including exploits to connected devices. Traditional threat intelligence sources focus on enterprise IT environments, so you may need to look for OT and IoT/IIoT threat intelligence feeds.
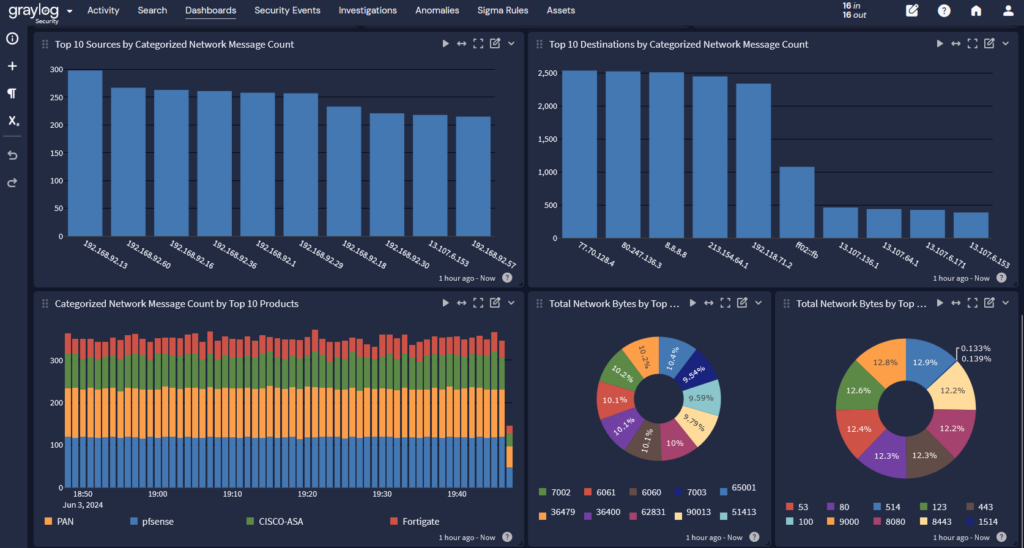
Monitor Network Activity
Monitoring network activity will tell you what your devices – including IoT and IIoT – are doing. You should be monitoring for events like:
- High-volume data transmissions
- Transmissions to abnormal locations that can indicate a command and control (C2) server
- Unusual access to sensitive data or databases
Scan for Vulnerabilities
Monitoring your environment to detect vulnerabilities enables you to implement security updates. Vulnerability scanners generate logs that you can incorporate into your security monitoring. You should consider using passive scanning technologies for your IoT deployments since active scanners often send probes or test traffic to their targets which can take IoT devices offline, ultimately impacting your network connectivity in a different way.
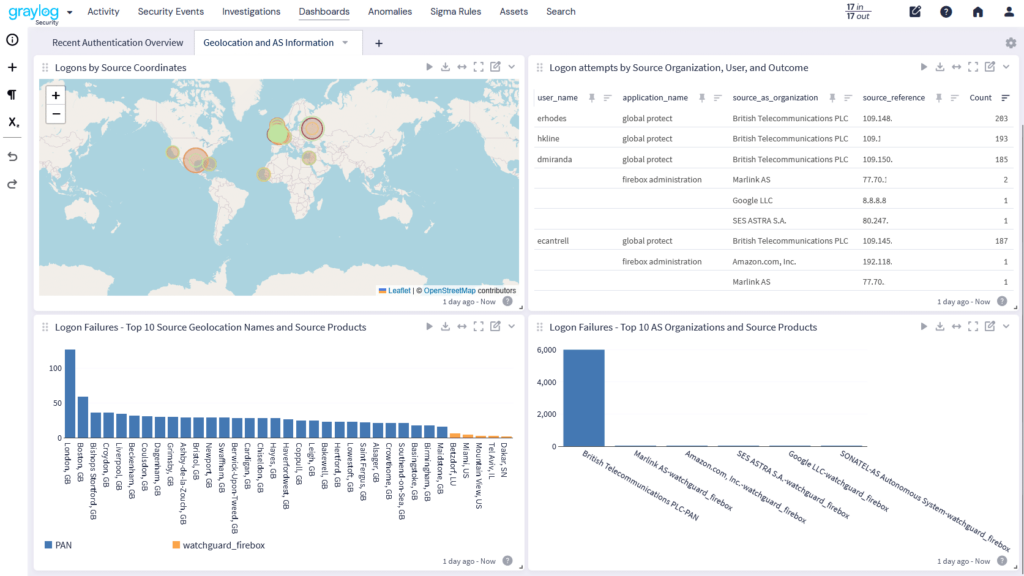
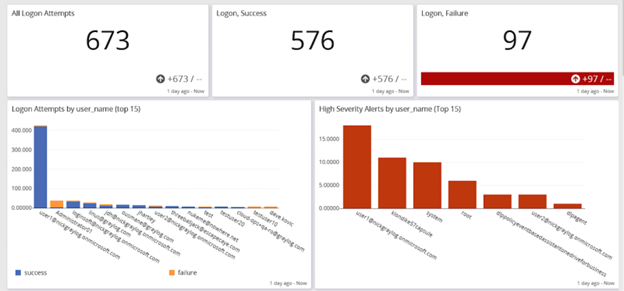
Monitor User Access
Monitoring access provides insight into human users and device access, including OT and IoT/IIoT devices. By incorporating both identities into your ongoing monitoring, you can create alerts for activities like:
- User login
- User logout
- Failed logins
- Resources accessed
- Account changes
By monitoring for these events, you can identify potential account or device takeover across the environment.
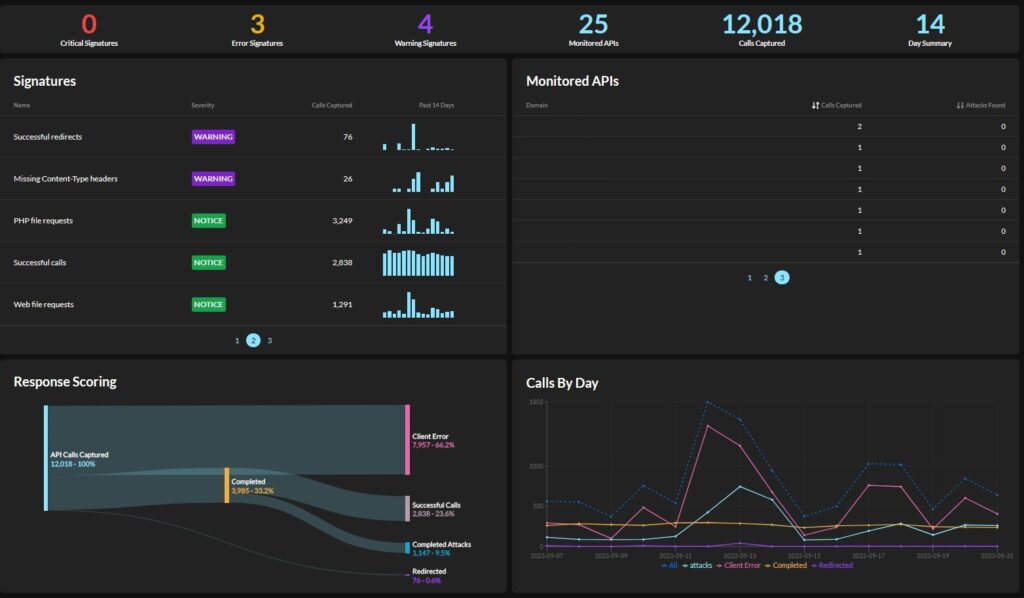
Secure APIs
Before you can secure your converged environment’s APIs, you need to know what you have. However, you may struggle with API security if all you have is a web application firewall (WAF) that helps monitor inbound and outbound traffic.
To secure the APIs that share data from your IoT devices and their applications with other resources you should be able to:
- Discover APIs, including zombie and shadow APIs
- Automatically risk score potential vulnerabilities
- Remediate underlying security issues
- Provide Correlate data with the rest of the environment
Correlate Data for High-fidelity Alerts
The more data you can correlate, the better your security alerts will be. Your threat detection and incident response (TDIR) capabilities should include high-fidelity alerts that reduce false positives. For example, if your security team can leverage Sigma rules combined with information from the MITRE ATT&CK knowledge base, you can implement automation that helps rapidly identify security incidents and speeds up investigations.
Graylog Security: Enabling Security Monitoring for Digital Manufacturing
Using Graylog Security, you can rapidly mature your threat detection and incident response capabilities. Graylog Security’s Illuminate bundles include rulesets with content that includes Sigma detections, enabling you to uplevel your monitoring by incorporating threat hunting capabilities and correlations to ATT&CK TTPs.
By leveraging our cloud-native capabilities and out-of-the-box content, you gain immediate value from your logs. Our anomaly detection ML improves over time without manual tuning, adapting rapidly to new data sets, organizational priorities, and custom use cases so that you can automate key user and entity access monitoring.
With our intuitive user interface, you can rapidly investigate alerts. Our lightning-fast search capabilities enable you to search terabytes of data in milliseconds, reducing dwell times and shrinking investigations by hours, days, and weeks.
To learn how Graylog Security can help you implement robust threat detection and response, contact us today.



